- Home
- Exchange
- Exchange Team Blog
- Basic Auth and Exchange Online – February 2020 Update
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update: The full timeline for retirement of Basic Authentication in Exchange Online is now published in Basic Authentication Deprecation in Exchange Online – September 2022 Update.
It’s been a few months since we announced changes we will be making to Exchange Online to improve security.
We’re pleased to provide an update today and to try and answer some of the questions we’ve received since that post. We do understand a change like this can be disruptive.
Azure AD Sign-In Report
The first piece of news is that the improved Azure Sign-In report which can help you understand Basic Auth usage in your tenant is available. We still have work to do on it, but we decided we’d rather get the word out now as we continue to work on it than wait until it’s all complete. The report has recently been extended to include data you’ll find helpful for identifying clients and apps still using Basic Auth, and we have more updates coming soon.
Take a look at a blog the Identity team posted that will help you use some of the more advanced features available within the report.
The report is part of the Azure Active Directory admin center, called Sign-ins. It’s typically available in the side menu under Azure Active Directory, and you can always search if you can’t find it.
On this overview page you’ll see the sign-in activity in your tenant, dates, times, user IP address and so on. You can add columns, and we’d suggest you add Client app if it’s not already there.
Now you can add a filter, Client app (then apply), and then a new dialog will allow you to pick the client app(s) to view. To view Basic Auth connections today you should select everything except Browser and Mobile Apps and Desktop Clients. When non-browser clients are using Modern Auth they will be placed into the Mobile Apps and Desktop Clients group.
If you have custom apps you’ll see them here, the screenshot below shows only the defaults provided.
Once you have your filter in place, you’ll see only those connections that meet the filter criteria (i.e. using Basic Auth). If you click on any of the lines, you’ll see more information in the pane below.
The User agent field can be handy for identifying app versions, if the app sends the string that is, many apps don’t (and User agents can be modified).
An easier way to view the data is to export it and use something like Excel to filter/group – as you likely will have a LOT of data. Today if you choose to download the report as a csv, the User agent data will be missing. But, if you download as JSON, and then convert it to csv so Excel can read it – the User agent string will be available. (We’re adding User agent to the CSV download dataset soon).
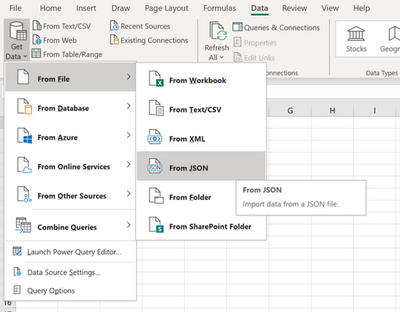
The simplest way to do this is to open a new Excel workbook, go to the Data menu, Get Data, From JSON – and import the file you downloaded from the Azure Sign-in report page.
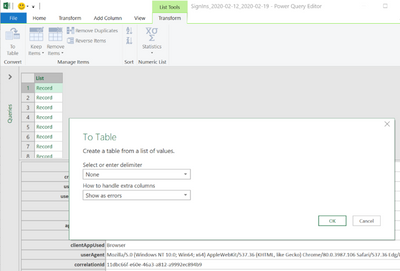
Excel analyzes the file and then opens the Power Query Editor. Each Record is an entry from the Sign-in Log report. If you select any item in that list you’ll see the details in the window below.
Click on Transform / To Table and accept the defaults of no delimiter and extra columns as errors, then click OK.
The last step is to click on the small double-headed arrow shown in the red circle below and uncheck Use original column name as prefix (shown in the blue circle below) – then click OK.
Finally, Close & Load to turn that JSON into an Excel workbook you can use to filter and sort your connections and start to identify the changes you need to make.
Outlook and Basic Authentication
Switching to Outlook, we want to try and answer a few questions we received after our last post. We didn’t explicitly mention Outlook for Windows or for Mac in our previous post – and we’re sorry for any confusion that might have caused.
Both Outlook for Windows and for Mac are impacted by our turning off Basic Auth in Exchange Online. Both clients rely upon Exchange Web Services (EWS) and so if they are still using Basic Auth, they will be affected. Both clients need to be switched to use Modern Auth before October 2020.
The good news is that up to date versions of both of those clients fully support Modern Auth and have for several years. Outlook for Windows added support for Modern Auth with the release of Outlook 2013 (though it required a registry key to be enabled) and Outlook 2016 onwards have Modern Auth enabled by default. Outlook for Mac has supported Modern Auth since Outlook for Mac 2016.
So it’s very likely you are already using a Modern Auth capable version of Outlook. How can you tell if you are using Modern Auth?
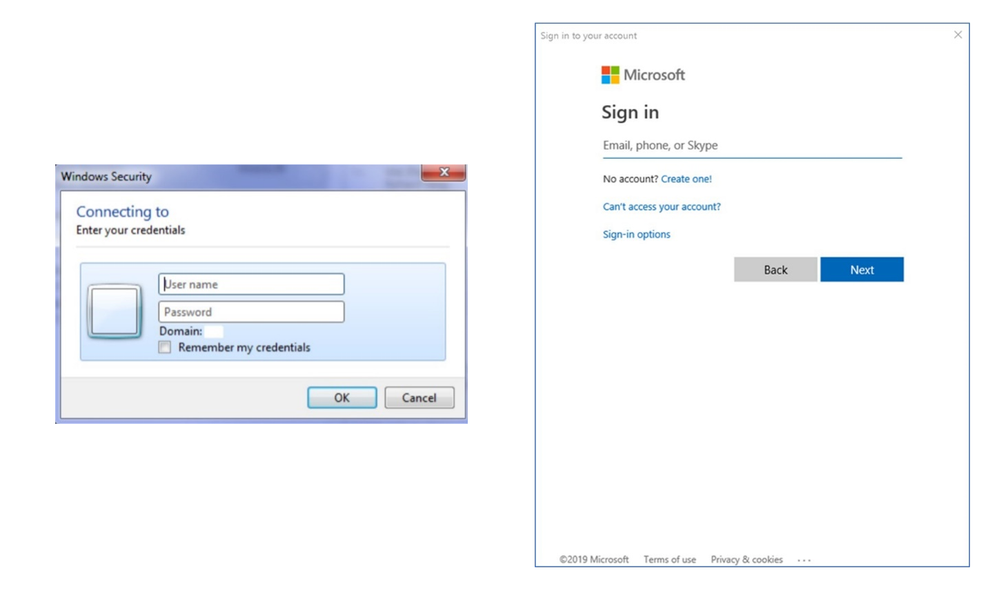
The simplest way to tell when using the Windows version is the very different authentication dialog each use. On the left below is the classic Basic Auth dialog, on the right in the mini web-like page Modern Auth dialog:
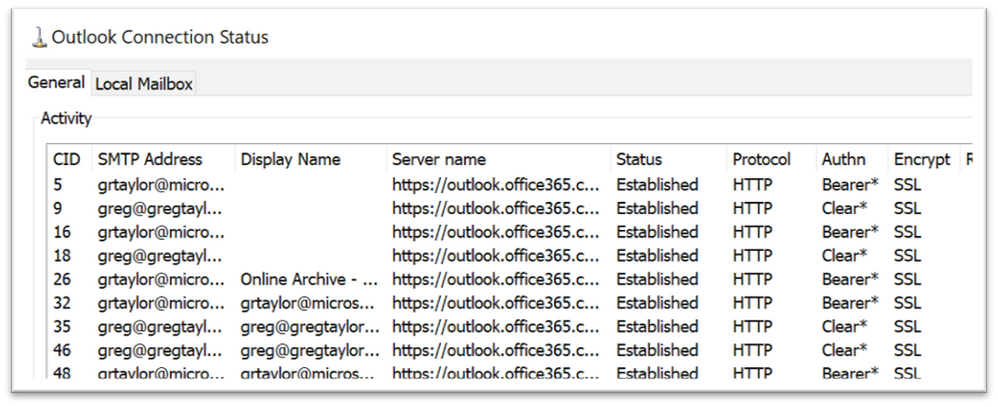
There’s another way to check too (and again this is Outlook for Windows) hold CTRL and right click the Outlook tray icon, choose Connection Status and you’ll see all the connections Outlook has to Office 365. ‘Bearer*’ means Modern Auth – ‘Clear*’ means Basic Auth. As you can see from the image below, our test guinea pig’s corporate email is using Modern Auth – his personal email (also hosted in Exchange Online as you can tell from the Server name in use) is not. Oops.
If you see Basic Auth being used by the client, it might be because Modern Auth is disabled in your tenant.
If your tenant was created before August 1, 2017, that’s most likely it (and that’s precisely why this member of the Exchange Team’s own O365 tenant is forcing him to connect with Basic – so he needs to fix that - sharpish).
So if you need to enable Modern Auth on your tenant, go read about that here. But before you just flip the switch, we do want to point out that this change affects your entire tenant. Just make sure you understand how such things as Conditional Access might impact the authentication flow. So be thoughtful, use the new report to see usage and when you are ready, make the change. Also, if your organization is in Hybrid, know that turning on Modern Auth on the tenant doesn’t impact your mailboxes on-premises. But you can enable Modern Auth there too. Read more about Hybrid Modern Authentication here.
How do you know if you are using Basic or Modern Auth with Outlook for Mac? You almost certainly are using Modern Auth – the number of connections we see using Basic is miniscule. If you are not, the Sign-in report would show it too.
POP, IMAP and SMTP
The next piece of news we want to share is an update on the status of adding Modern Auth support to POP and IMAP for O365 commercial customers (we’ve had Modern Auth for IMAP in consumer Outlook.com for years).
We’ve completed our development work and are rolling out Modern Auth support for POP and IMAP in Exchange Online now. Documentation for developers is being finalized and we’ll link to it in this blog post when it is available.
Now if you are using POP or IMAP for your day to day email access, and if your current email client vendor has added support for Modern Auth, then great. But to be honest, using POP or IMAP for day to day access to your mailbox means you are really missing out. Even if you are using Outlook with those protocols you don’t get the complete calendar or contacts experience, and so switching to Outlook and using the default connectivity protocols, either for Windows/Mac, is going to make your use of email more functional and productive. And you might want to check out Outlook on the Web (OWA) – it’s changed enormously over the past few years and is a very capable and feature-filled client used by millions of people every day.
What if you are using POP and IMAP for various devices in your office? Chances are these devices are sending mail (things you have scanned for example) using SMTP email submission, so this change to POP and IMAP won’t impact them – but if you do have devices polling for mail, and the vendor has long gone or can’t update the devices to support Modern Auth for POP and IMAP, then we’re sorry… but they will hit issues.
It has to be said too that these devices are often a weak link in your security chain anyway. They have credentials stored on them, no-one ever changes the password – and if an attacker can get just one username and password in your tenant, they can see the entire tenant directory and from there go on to do far worse things.
What about 3rd party apps that integrate with your email, and use POP or IMAP to access a mailbox you have in Exchange Online? First port of call should be to speak to that vendor and ask what their plans are. As you might have seen, we’re not the only major cloud provider securing applications by removing Basic Auth, so if that application vendor wants to help their customers stay secure, they need to move to Modern Auth.
Finally, SMTP. We’re pleased to announce that we’re nearly done with the engineering work for Modern Auth for SMTP and hope we will soon be able to start the process of deploying that to the service. We’ll provide another update with some guidance on configuration and general usage as soon as we have it available.
PowerShell and Automation
PowerShell, scripts and automation – we are absolutely committed to supporting non-interactive scripts via Remote PowerShell using Certificate Based Authentication. We’re still working hard on the code, have some customers working on this with us already, and will have more to say on this in the next couple of months. Please be patient, we know many of you are desperate to get your hands on something that works, we’re working really hard to deliver that to you.
We do hope though that you are using the new PowerShell V2 Module already, and know all about Azure Cloud Shell which we provide details about here.
Exchange ActiveSync
Finally, we’ll address Exchange ActiveSync. As we have said previously, many up to date versions of mobile device email clients support Modern Auth already. Take a look at the usage report for your tenant and you’ll find the users on devices not using Modern Auth. The User Agent string will hopefully tell you the version of the device they are using. If they are using a device that should support Modern Auth, but isn’t using Modern Auth – users might need to reset or reconfigure their account.
As we said in the last post, we’re strongly recommending you switch to Outlook for iOS and Android in favor of the native apps. There are many security and business benefits over native apps when connecting to Exchange Online. We also just published details of a Total Economic Impact™ study Forrester which details the security, productivity and cost benefits a switch to Outlook mobile can provide. You can find that here.
Summary
That pretty much sums up the update for now. We do plan on making updates more regularly now the report is available, and as we close in on October 2020. Look out for more information in due course.
The Exchange Team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.