- Home
- Security, Compliance, and Identity
- Core Infrastructure and Security Blog
- Using Azure Security Center and Log Analytics to Audit Use of NTLM
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The purpose of this post is to show how you can collect and query security events of interest from Windows servers. To do this we will use:
- Azure Security Center to collect events
- Log Analytics Workspace to store events
- Kusto query language to query stored events
As an example, we are going to collect 4624 (An account was successfully logged on) events from multiple machines. This event is generated on the destination machine when a logon session is created and can be used to audit for NTLM authentication. See the link below for more details:
How to audit use of NTLMv1 on a Windows Server-based domain controller - https://support.microsoft.com/en-ca/help/4090105
What is Kusto?
Kusto is a big-data engine for log and telemetry search and analytics, and powers Azure Log Analytics along with many other Microsoft products, such as Azure Application Insights, Azure Time Series Insights, Azure Security Center, and more. Use this link to learn more about the query language.
Why audit for NTLMv1?
The fact that the NTLMv1 response generation uses the relatively weak DES encryption algorithm and a fixed-length 16-byte random number makes it highly susceptible to brute-force attacks. In comparison, the NTLMv2 response uses the stronger HMAC-MD5 algorithm and a challenge of variable length.
To put it into perspective, NTLMv2 was introduced in Windows NT 4.0 SP4
See links at the bottom of the page for more information.
Decisions, decisions!
Azure Security Center Tiering
For Azure Security Center to collect the data we need, you will need to configure Standard tiering. This can be done in one of three different ways:
- At the subscription alone – choose this option if you want to store the events in the workspace created by Security Center, and not in an existing workspace
- At the Log Analytics Workspace alone - choose this option if the subscription contains multiple VMs and you only want Security Center to manage a subset of them
- Both; the recommended option
Monitoring Agent Installation
Data collection from the source machines is done using the Microsoft Monitoring Agent (MMA), the installation of which can be done in several different ways:
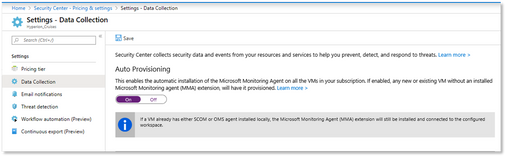
- You can enable Auto Provision on Security Center to automatically deploy the agent for your Azure VMs. This option ensures any new VMs are automatically onboarded
- Enable the Log Analytics VM Extension; this is the method shown below. See https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm#enable-the-log-anal... for more details.
- Manually install the agent and configure it to report to the Log Analytics workspace; see https://docs.microsoft.com/en-ca/azure/azure-monitor/platform/agent-windows
Costs
- Storing data in log analytics might incur additional charges for data storage.
- Depending on the number of resources being monitored, enabling Standard tiering in Security Center can lead to additional costs.
Use the Pricing calculator (https://azure.microsoft.com/en-ca/pricing/calculator/) to configure and estimate costs.
Connect Azure VMs to Log Analytics Workspace
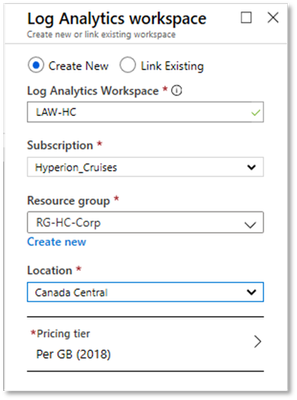
- Create a Log Analytics Workspace if you do not already have one.
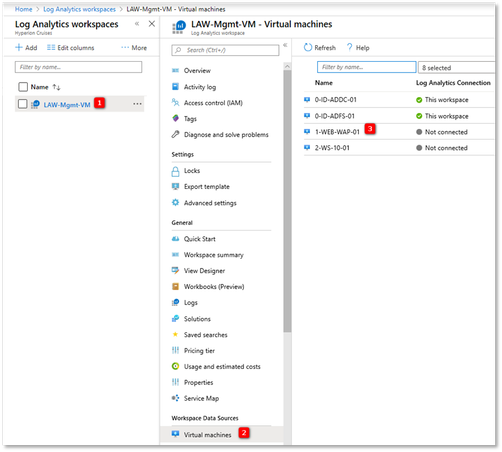
- In your list of Log Analytics workspaces, select the workspace created earlier.
- On the left-hand menu, under Workspace Data Sources, select Virtual machines.
- In the list of Virtual machines, select a virtual machine you want to install the agent on. Notice that the Log Analytics connection status for the VM indicates that it is Not connected.
- In the details for your virtual machine, select Connect. The agent is automatically installed and configured for your Log Analytics workspace. This process takes a few minutes, during which time the Status shows Connecting.
- After you install and connect the agent, the Log Analytics connection status will be updated with This workspace.
Connect Physical Servers to Log Analytics Workspace
The steps in https://docs.microsoft.com/en-us/azure/azure-monitor/platform/agent-windows show how to install and configure the Microsoft Monitoring agent manually.
Configure Auditing on Servers
Use Group Policy Objects to enable subcategory-level auditing on the machines:
- Computer Configuration \ Policies \ Windows Settings \ Security Settings \ Local Policies \ Security Options
- Audit: Shut down system immediately if unable to log security audits - Disabled
- Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings – Enabled
- Computer Configuration \ Policies \ Windows Settings \ Security Settings \ Advanced Audit Configuration
|
Policy |
Setting |
|
|
Domain Controllers |
non-Domain Controllers |
|
|
Account Logon |
||
|
Audit Credential Validation |
Success, Failure |
Success, Failure |
|
Audit Kerberos Authentication Service |
Failure |
|
|
Audit Kerberos Service Ticket Operations |
Failure |
|
|
Account Management |
||
|
Audit Computer Account Management |
Success, Failure |
Success |
|
Audit Other Account Management Events |
Success, Failure |
Success, Failure |
|
Audit Security Group Management |
Success, Failure |
Success, Failure |
|
Audit User Account Management |
Success, Failure |
Success, Failure |
|
Detailed Tracking |
||
|
Audit Process Creation |
Success |
Success |
|
DS Access |
||
|
Audit Directory Service Access |
Success, Failure |
|
|
Audit Directory Service Changes |
Success, Failure |
|
|
Logon/Logoff |
||
|
Audit Account Lockout |
Success |
Success |
|
Audit Logoff |
Success |
Success |
|
Audit Logon |
Success, Failure |
Success, Failure |
|
Audit Special Logon |
Success |
Success |
|
Policy Change |
||
|
Audit Audit Policy Change |
Success, Failure |
Success, Failure |
|
Audit Authentication Policy Change |
Success |
Success |
|
Privilege Use |
||
|
Audit Sensitive Privilege Use |
Success, Failure |
Success, Failure |
|
System |
||
|
Audit IPsec Driver |
Success, Failure |
Success, Failure |
|
Audit Other System Events |
Success, Failure |
Success, Failure |
|
Audit Security State Change |
Success, Failure |
Success, Failure |
|
Audit Security System Extension |
Success, Failure |
Success, Failure |
|
Audit System Integrity |
Success, Failure |
Success, Failure |
Note:
- Ensure the event logs on your servers are sized correctly so that they are not rolled over too quickly by enabling additional audit logging.
- Use the command AuditPol /get /category:* locally on a server to verify that the right audit policy is being applied.
Data collection in Azure Security Center
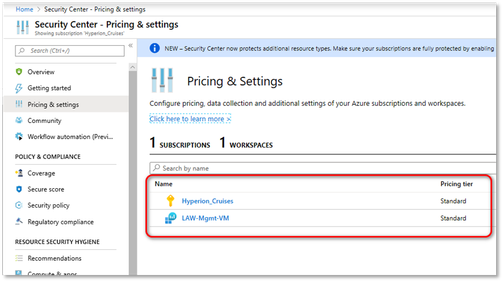
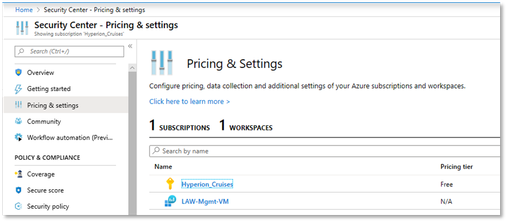
- Under the Security Center main menu, select Pricing & settings.
As mentioned earlier, the recommended option is to enable Standard tiering for both the subscription and for the workspace. This ensures you receive recommendations on resources other than just virtual machines. The subsections below show both.
Workspace Configuration
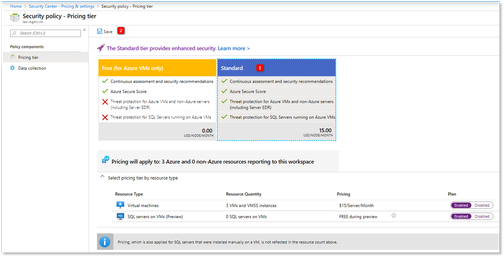
- Select the desired Workspace in which you intend to connect the agent and select Standard pricing tier. Click Save.
You will be billed (Number of VMs) * $15 per month (or, more correctly, (Number of VMs) * $0.02 per hour. Only powered-on VMs are billed, and billing is hourly.
- Select the appropriate data collection tier. Common provides a full user audit trail in this set.
Note:
These security events sets are available only on Security Center’s Standard tier.
To see a list of events collected see Data collection in Azure Security Center - https://docs.microsoft.com/en-us/azure/security-center/security-center-enable-data-collection#data-c...
Subscription configuration
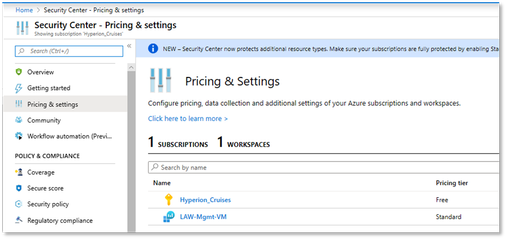
- Select the applicable Subscription and select Standard pricing tier.
Disable any resource types that you do not want to collect data for, and then click Save.
- If you did not want to manually connect the VMs to the workspace, enable auto-provisioning on Security Center to automatically deploy the agent for your Azure VMs. This is done under the Data Collection node
Verify Data Collection
- Click on the Log Analytics Workspace -> Logs
- In the query pane, expand Security, click on the icon to the right of SecurityEvent to show sample records from the table
- Click Run
- This is a common way to take a glance at a table and understand its structure and content.
Log Query
Under the Log Analytics Workspace -> Logs, type the queries and click Run.
Summarizing list of events
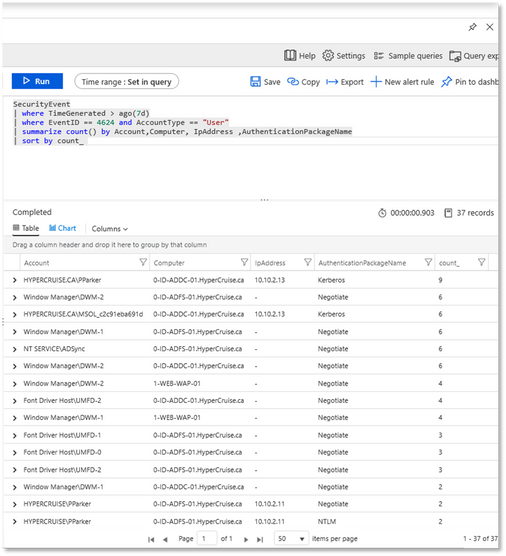
The following query:
- returns all events logged over the past 7 days
- with ID 4624 and by a user account
- groups them by the Account,Computer, IpAddress and AuthenticationPackageName fields
- and sorts them by decreasing order of the number of results in each group.
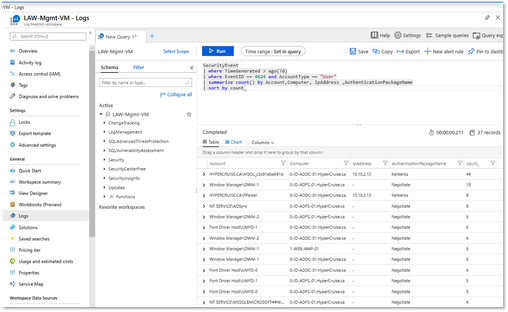
SecurityEvent
| where TimeGenerated > ago(7d)
| where EventID == 4624 and AccountType == "User"
| summarize count() by Account, Computer, IpAddress, AuthenticationPackageName
| sort by count_
Selecting specific columns
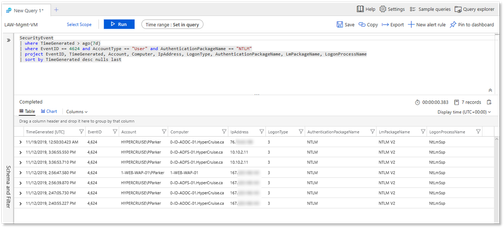
The following query:
- returns all events logged over the past 7 days
- with ID 4624, by a user account and NTLM is used for authentication
- specifies that the following columns be included in the result: EventID, TimeGenerated, Account, Computer, IpAddress, LogonType, AuthenticationPackageName, LmPackageName, LogonProcessName
- and sorts them by decreasing order of TimeGenerated column, with null values placed at the end.
SecurityEvent
| where TimeGenerated > ago(7d)
| where EventID == 4624 and AccountType == "User" and AuthenticationPackageName == "NTLM"
| project EventID, TimeGenerated, Account, Computer, IpAddress, LogonType, AuthenticationPackageName, LmPackageName, LogonProcessName
| sort by TimeGenerated desc nulls last
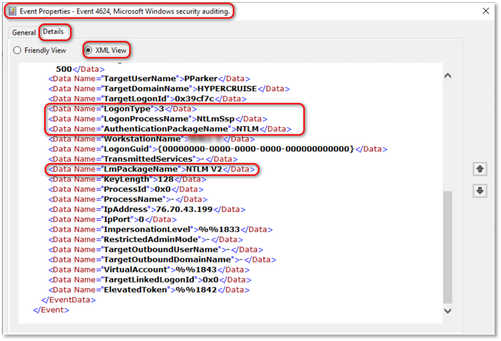
The columns in the query correspond to the XML data fields in the event as shown below.
Remember, you can ignore the event for security protocol usage information when the event is logged for "ANONYMOUS LOGON".
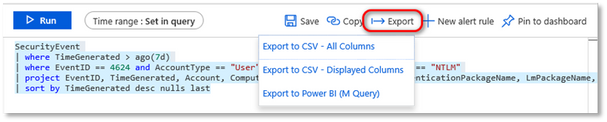
Exporting query data
Log Analytics supports several exporting methods:
- Excel: Save the results as a CSV file.
- Power BI: Export the results to Power BI.
- Share a link: The query itself can be shared as a link which can then be sent and executed by other users that have access to the same workspace.
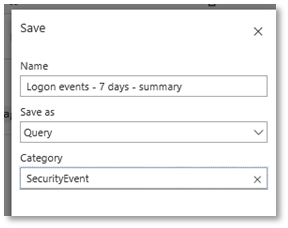
Saving queries
Once you have created a useful query, you might want to save it or share with others. The Save icon is on the top bar.
Loading saved queries
The Query Explorer icon is at the top-right area. This lists all saved queries by category. It also enables you to mark specific queries as Favorites to quickly find them in the future. Double-click a saved query to add it to the current window.
There you have it – we configured Azure Security Center to collect events from windows servers, store them on a Log Analytics Workspace and used KQL to query the saved logs for audit for NTLM authentication.
You can extend this to cover a wide range of auditable events. See https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/appendix-l--events-to-monitor for one such list.
References
- Azure Security Center frequently asked questions (FAQ) - https://docs.microsoft.com/en-us/azure/security-center/security-center-faq
- Overview of log queries in Azure Monitor - https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/log-query-overview
- Azure Monitor log query examples - https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/examples
- Security Watch: The Most Misunderstood Windows Security Setting of All Time - https://docs.microsoft.com/en-us/previous-versions/technet-magazine/cc160954(v=msdn.10)?redirectedfr...
- Stop using LAN Manager and NTLMv1 - https://blogs.technet.microsoft.com/miriamxyra/2017/11/07/stop-using-lan-manager-and-ntlmv1/ (Content may be archived; if so, search TechNet and MSDN blog archive)
- Auditing and restricting NTLM usage guide - https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/jj...
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.