Howdy Folks,
Today's blog is about Microsoft Passport, a new set of features in Windows 10, Microsoft Account, Azure AD and (soon!) Windows Server AD aimed at eliminating passwords once and for all. Microsoft Passport has been submitted to the Fast Identity Online (FIDO) Alliance (specifically the FIDO 2.0 working group) for consideration in the upcoming 2.0 specification.
We're going to focus on how Microsoft Passport with Azure AD eliminate the need for using a password to login to your PC and to the cloud services Azure AD manages for you.
This post is written by Hari Samrat on my team. Hari will walk you through Microsoft Passport, the new credential system in Windows 10, and how it works with Azure AD.
And as always, we'd love to hear your feedback on this so please fire away in the comments section.
Best Regards,
Alex Simons (Twitter: @Alex_A_Simons )
Director of Program Management
Microsoft Identity and Security Division
---------------------------------------------- Hi there, I am Hari Samrat - one of the Program Managers working on Azure AD support in Windows 10. Continuing the coverage of Azure AD and Windows 10, I want to talk about how a new credential in Windows 10 - Microsoft Passport – works with Azure AD to reduce reliance on passwords in your organization.Why?
Passwords are ubiquitous - they are simple to use, but they are also insecure, hard to manage and prone to breaches and phishing attacks. To protect users from the risks of passwords, the industry has created a panoply of methods - password complexity policies, changing passwords on a set frequency, One-Time Passwords (OTPs), and multi-factor authentication (MFA). These all help, but at the cost of usability. Smartcards, the other major credential method used in enterprises, are more secure than passwords while also providing a physical second factor. The downside is that they require considerable infrastructure to deploy and maintain. And there is very limited support for smartcard authentication on mobile devices. Our goal with Microsoft Passport and Azure AD is to eliminate the need for passwords by blending the simplicity of passwords with the higher security of smartcards.What is Microsoft Passport?
Microsoft Passport is a key based authentication system built into Windows 10. To use Microsoft Passport users create a gesture that they use to login to their Windows 10 device. The user gesture unlocks the device and it's TPM. The TPM protects a private key that is used to sign authentication requests to Azure AD, eliminating the need to authenticate using a password.How does it work?
Let's start with a high level view of the flow:

Creating and using Passport
Creating Passport: Upon first login to their device the user is prompted to create a gesture. After they create the gesture, Windows creates a private-public key pair and registers the user's public key with Azure AD while the private key is protected by the device's TPM or encrypted with a locally derived secret. A signed attestation blob, that is used to validate the TPM, is sent to Azure AD along with the public key to complete the registration. Using Passport: The authentication flow is initiated by the Windows client. The user is asked to provide their gesture that unlocks the TPM and then an authentication request is sent to Azure AD. Azure AD responds by sending a nonce to the Windows client, which is then signed using the user's private key and sent back to Azure AD. When Azure AD gets the signed nonce, it looks up the public key and uses it to verify the signature. If the signature is verified, Azure AD returns an authentication token.
First run experience
When you first sign-in to a Windows 10 device that is joined to Azure AD, you will be asked to setup your Microsoft Passport, in this case with a PIN:

Signing into the PC.

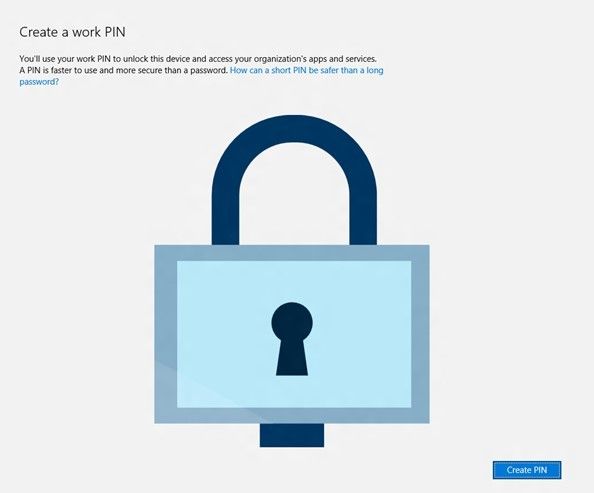
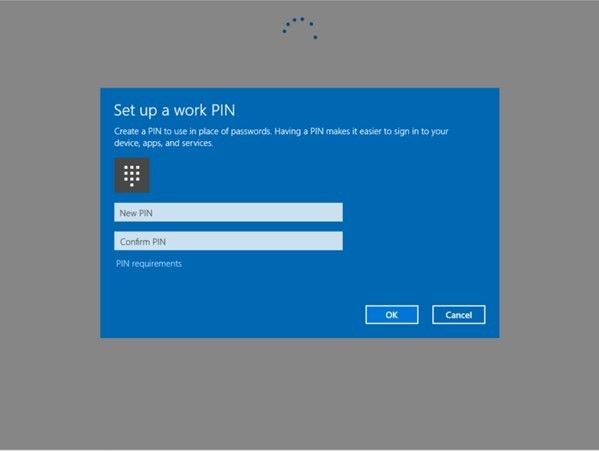

Detailed flow of Passport Setup
Using Passport
Now let's take a look at how to sign in using a Microsoft Passport – it's no different than a password. You simply sign in with the PIN that you set up earlier.

Sign in screen after Passport is setup

Detailed flow of the auth using Passport
After sign-in, Windows sends an auth request Azure AD that does not contain either a username or secret. Azure AD responds with a nonce. Windows asks the TPM to sign the nonce and sends it back to Azure AD along with the key ID that was sent by Azure AD during setup. Azure AD looks up the key using the key ID and verifies the signed nonce using the key.Passport for work
Azure AD Admins can manage Microsoft Passport configuration by tweaking a few settings:| Policy | Commentary |
| Microsoft Passport enabled | Passport is enabled by default. If for some reason you need to disable Passport on some devices you can use this setting to turn it off. |
| Hardware TPM required | The default behavior during setup is to try to create Passport using a hardware TPM. If this fails or if the TPM is not available, then software encryption is used. If you wish to restrict the use of Microsoft Passport to devices with a hardware TPM only, then turn this on. |
| Pin complexity | The default gesture for Microsoft Passport is a 4-digit numeric PIN. Use this policy if you require a more complex PIN. |
| Enable biometrics | You can turn off biometrics using this, by default this is ON. |
In closing
Microsoft Passport with Azure AD opens an easy path towards eliminating passwords in your organization. Microsoft Passport will see industry wide adoption across platforms and devices as part of FIDO 2.0. All you need to start is Window 10 and Azure AD Join. We hope you give it a try and let us know what you think! Hari Samrat, PM grunt Microsoft Identity and Security Services Division Microsoft
Microsoft