Howdy folks,
Yesterday the Office team announced the availability of Multi-Factor Authentication for Office 365. If you missed their announcement, you can read it here .
The AD team has been working on MFA for Office 365 for over 6 months now and we are excited to be able to make this security capability available to the broad set of Office 365 users. At the same time, we've been working on Multi-Factor Authentication for Azure Administrators which is also now available. These capabilities are both available for no extra charge to Office 365 & Azure customers.
And of course we continue to improve and advance our Windows Azure Multi-Authentication Service, our paid service that offers organizations the ability to protect all their cloud apps and on premise servers in a highly customizable and configurable way.
To give you a clear idea of each offer and what it does, I asked Shawn Bishop who is one of the MFA Program Managers here in the Active Directory team to write up a quick post which I've included below.
As always, any feedback or suggestions you have here would be great!
Best regards,
Alex Simons (@Alex_A_Simons)
Director of PM
Active Directory
-----------------------------------------------------------------------------------------------
Hi everyone!
I'm Shawn Bishop, PM on the Windows Azure MFA team. We have been very excited to announce the availability of
Multi-Factor Authentication for Office 365
and hope that many of our customers will take advantage of the additional security it provides for their access to Office.
At the same time, we are formally announcing the availability of
Multi-Factor Authentication for Azure Administrators
. Technically, this has been around for a number of months and allows Azure administrators to use MFA for their accounts when accessing the Windows Azure Management Portal. Both Multi-Factor Authentication for Office 365 and Multi-Factor Authentication for Azure Administrators, which are included at no additional charge in Office and Azure subscriptions respectively, offer a subset of features contained in the full-blown
Windows Azure Multi-Factor Authentication
.

Now that multi-factor authentication is included with Office 365 user licenses as well as administrator access to Azure, we thought there might be some questions about the additional features you can get with Windows Azure Multi-Factor Authentication. Here is a chart that shows the feature comparison.

Windows Azure Multi-Factor Authentication Feature Comparison
The primary features that Windows Azure Multi-Factor Authentication unlocks are those that are found within the Multi-Factor Authentication Management Portal, which can only be accessed after creating a Multi-Factor Auth Provider in the Azure Management Portal. Creation of that provider and linking it to an Office 365 directory is what upgrades an Office 365 tenant from having Multi-Factor Authentication for Office 365, containing a subset of features, to having Windows Azure Multi-Factor Authentication which contains all of the available features. There is a previous blog post
here
that describes how to get started.

To create a Multi-Factor Auth Provider sign into the
Windows Azure Management Portal
and go to
Active Directory
à
Multi-Factor Auth Providers
. Create a new provider by providing a name, usage model for billing and link it to your directory unless being used for on-premises applications only.
Let's go over some of the things you can do in the MFA Management Portal to take advantage of these additional features. The features are accessed by managing your Multi-Factor Auth Provider.

To access the MFA Management Portal, select a Multi-Factor Auth Provider and click
Manage
.
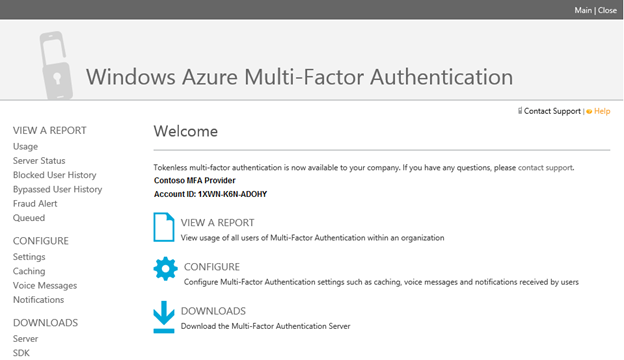
The Multi-Factor Authentication Management Portal provides access to advanced features.
Customizable Voice Greetings
– Do you have professional voice talent, access to a celebrity or maybe just someone on the IT team that wants everyone to listen to them for a change? You can create your own .mp3 or .wav files and upload them to the MFA Management Portal. Once uploaded, you can map them to the voice greetings that are available. Your users will then hear your custom greetings instead of the default Microsoft greetings when they answer authentication phone calls.
If you would like me to be your voice talent, I would be happy to moonlight for the right price (after normal business hours of course – don't tell my boss)
. To get started, click
Voice Messages
in the left navigation, click
New Voice Message
and then click
Manage Sound Files
. After your custom sound files have been uploaded, select the language for the greeting and the message type that you want to map your sound file to. You can even play different greetings for different applications be entering an application name. If the name matches an application name configured in the on-premises MFA Server (see more on this feature below) or the "SAS Login" or "SAS Verification" application names we use from Azure AD, that greeting will play.

Configure custom voice greetings in the MFA Management Portal after uploading custom sound files.
Customizable Caller ID
– Instead of receiving authentication phone calls from Microsoft's default 855 phone number, you can specify the phone number that should appear on caller ID. Only North American phone numbers are currently supported.
Fraud Alert
– This is a great security feature! If your users receive a multi-factor authentication request when they aren't expecting it (maybe they are golfing, shopping, having their nails done, attending night classes or watching the Seattle Seahawks win the Super Bowl!), they can ignore the call or answer and hang up without pressing # to deny access to the person attempting to use their credentials. However, the fraud alert feature takes it a step further and allows your user to be more proactive about attempted attacks. They can answer the phone and enter your configured fraud alert code (0# by default, but customizable) to report the attempted access. Not only will it deny the authentication taking place, but will put a block on that user's account so that additional authentication attempts are automatically denied without continuing to bother the user. It can also send an email notification to any configured email addresses such as the security team and IT admins so that they can take action, investigate and change the user's password. Once they have taken appropriate action, they can unblock the user's account in the MFA Management Portal.

Configure the caller ID phone number, fraud alert, account lockout and other settings in the MFA Management Portal by clicking
Configure
on the welcome screen or
Settings
in the left navigation
Reporting/Auditing
– In the MFA Management Portal, you can run reports to see all of the multi-factor authentications that have been performed for your organization. The Summary report shows the total number of authentications, successful auths and denials during the timeframe you specify. The User Summary report shows the total number of authentications, successful auths and denials by user. The User Details report shows the details of each authentication including the date/time, method of authentication (phone call, text, mobile app, OATH token), access type (RADIUS, LDAP, IIS, cloud, Terminal Services), phone number called/texted, application accessed, success/denial and reason for any denials (phone unreachable, incorrect PIN entered, user reported fraud, user abducted by aliens, etc.). The reports can be run anytime for the date range you choose and can be downloaded in csv format. There are also reports to see all fraud alerts, blocked users, users who have used a one-time bypass (see below for more info on this feature) and the status of any MFA Servers installed on-premises (see below for that feature too!).

The MFA Management Portal has a number of reports that can be run, including usage reports. Each usage report have a variety of filters that can determine which authentications appear in the report. Select a date range and any other desired criteria to run the report.
One-Time Bypass
– Uh oh! You have a user that needs to access SharePoint Online to access a document for an important meeting that starts in 20 minutes, but they accidentally dropped their phone that they use for MFA in the toilet. What do you do? If they have an office phone number configured in the directory account, they can authenticate on that number. You could also change the phone number on their user account to another one they have access to. Otherwise, you can issue them a one-time bypass. The bypass lasts for a period of time (5 minutes by default) during which the user can get into an MFA-protected application one time without performing multi-factor authentication. Yeah! Day saved.

A one-time bypass can be granted to users through the MFA Management Portal. You may have to select the "Azure Default", "MFA Server Default" group or another group created for MFA Server replication first. The on-premises User Portal can also be used by helpdesk administrators or end users to initiate a one-time bypass if needed and admins have enabled the feature.
Block/Unblock Users
– Have a rogue user? See something suspicious in your authentication logs? Want to play a trick on the CTO and deny them access to your applications (I hereby do not sanction such action)? You can put a block on any of your users so that their multi-factor authentications are automatically denied. Oh, and you can unblock them when they threaten to fire you for locking them out or if they entered their PIN incorrectly too many times and accidentally locked themselves out.

Administrators can put a block on a user in the MFA Management Portal or through the on-premises User Portal
MFA Server
– Do you want to use multi-factor authentication with other things besides Office 365 and the Azure Management Portal? When you procure Windows Azure Multi-Factor Authentication, you can use the Windows Azure Multi-Factor Authentication Server on-premises to secure things like VPN, AD FS, UAG, TMG, RD Gateway, on-premises OWA/Exchange, Citrix, IIS web applications and Terminal Services (are there enough 3-letter acronyms in that list?). The MFA Server can run in a master/slave configuration to provide redundancy and high availability. Your user data stays on-premises but performs authentications through the MFA cloud service, just like Office 365 and Azure Active Directory do. The MFA Server comes with a User Portal that allows users to perform self-enrollment, MFA account self-management, perform help desk functions or just log into when they feel lonely and want an automated multi-factor authentication system to call them on the phone to say hello. The MFA Server also comes with a Web Services SDK that could be used to integrate MFA into custom applications.

The MFA Server can be downloaded and installed on-premises to secure many systems using standard protocols. It integrates with Active Directory for easy user management and comes with web tools used for enrollment, account management and helpdesk functions.
MFA SDK
– The SDK can be downloaded and integrated into a custom application to perform multi-factor authentication. It is easy to use and give you a lot of flexibility in how and when to perform MFA. It is available in C#, VB.NET, Java, Perl, PHP and Ruby. There is a previous blog post about using the SDK
here
.
Event Confirmation
– This feature allows you to perform multi-factor authentication for specific events or transactions. It is typically used through an SDK to play templates that have been configured in your account to play custom greetings and perform text-to-speech on parameters that you pass in such as dollar amounts and account numbers.
Are we done? Of course not! We will continue to add new and exciting features to our multi-factor authentication products. Some of those features will be included in MFA for Office 365 and MFA for Azure Administrators, but some will only be available through Windows Azure Multi-Factor Authentication. We hope you take advantage of these features to make your organization more secure and find value in the additional features available in Windows Azure Multi-Factor Authentication!
 Microsoft
Microsoft