First published on CloudBlogs on Sep, 19 2017
Howdy folks, A common request we get from our customers is to reduce the number of times users are prompted to sign into Azure AD. One way to reduce the frequency of prompts is to check the "Keep me signed in" checkbox on the sign-in flow, but our telemetry shows that usage of that checkbox is very low. But we know from talking to customers, that cutting down on the number of signin prompts is REALLY important. Nobody wants to have to signin to an app multiple times! So today I'm happy to share that we're improving how "Keep me signed in" option is shown to users. We're also adding intelligence to ensure users are prompted to remain signed in only when it's safe to do so. First, as a quick refresher, here's what the existing "Keep me signed in" experience is like. As you might guess, most users cruise right past the check box and never think twice.
Howdy folks, A common request we get from our customers is to reduce the number of times users are prompted to sign into Azure AD. One way to reduce the frequency of prompts is to check the "Keep me signed in" checkbox on the sign-in flow, but our telemetry shows that usage of that checkbox is very low. But we know from talking to customers, that cutting down on the number of signin prompts is REALLY important. Nobody wants to have to signin to an app multiple times! So today I'm happy to share that we're improving how "Keep me signed in" option is shown to users. We're also adding intelligence to ensure users are prompted to remain signed in only when it's safe to do so. First, as a quick refresher, here's what the existing "Keep me signed in" experience is like. As you might guess, most users cruise right past the check box and never think twice.

What's changing
We're replacing the "Keep me signed in" checkbox with a prompt that displays after the user successfully signs in. This prompt asks the user if they'd like to remain signed in. If a user responds "Yes" to this prompt, the service gives them a persistent refresh token. This is the same behavior that currently occurs when a user checks the "Keep me signed in" checkbox. For federated tenants, this prompt will show after the user successfully authenticates with the federated identity service.
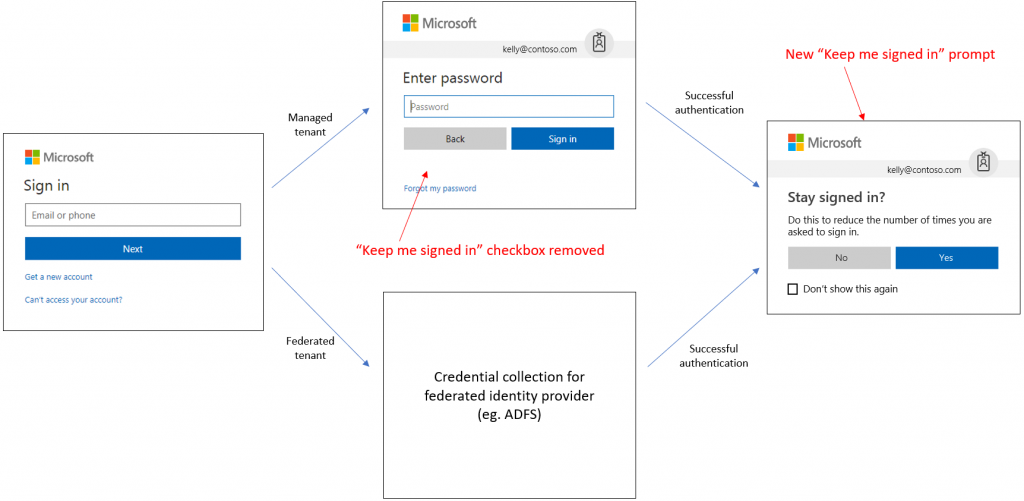
Some things to know
- During the public preview period of the new sign-in experience , the updated "Keep me signed in" prompt will only show when users opt into the new sign-in experience. Users using the old experience will continue to see the checkbox and will not get the prompt.
-
Admins can choose to hide this new prompt for users by using the "Show option to remain signed in" setting in
company branding
.
(Note: Existing configurations of this setting will carry forward, so if you previously chose to hide the "Keep me signed in" checkbox in your tenant, we won't show the new prompt to users in your tenant.)
- This change won't affect any token lifetime settings you have configured.
An additional note about security
Because "Keep me signed in" drops a persistent refresh token, some members of the IT community have asked if this might alter the security posture of their organization. We've done a significant amount of analysis on this topic and have concluded that increasing refresh token lifetime improves the user experience without reducing security posture. For more on that topic, please see our recent blog post on changes to default refresh token lifetimes .Let us know what you think!
Look for this new "Keep me signed in" prompt to start rolling out on the new sign-in experience in early October. Let us know if you have any questions, and head on over to the Azure Active Directory community to share your feedback and suggestions with us – we look forward to hearing from you! Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity DivisionUpdated Jul 28, 2020
Version 6.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.