First published on CloudBlogs on Aug, 06 2018
Howdy folks, Today, I am excited to share some really cool improvements to Multi-Factor Authentication (MFA) and self-service password reset (SSPR) that are now in public preview! We’ve heard from our customers that having two different registration experiences causes confusion and frustration. Now, users can register once and get the benefits of both MFA and SSPR—eliminating having to register their security info for these features twice. This allows administrators to create and maintain a single set of documentation for their users and greatly simplifies the helpdesk scenarios. We received a lot of positive feedback from customers who have been using the private preview of these improvements and now we're excited to share them with all of you. Keep reading to learn more about these improvements!




Howdy folks, Today, I am excited to share some really cool improvements to Multi-Factor Authentication (MFA) and self-service password reset (SSPR) that are now in public preview! We’ve heard from our customers that having two different registration experiences causes confusion and frustration. Now, users can register once and get the benefits of both MFA and SSPR—eliminating having to register their security info for these features twice. This allows administrators to create and maintain a single set of documentation for their users and greatly simplifies the helpdesk scenarios. We received a lot of positive feedback from customers who have been using the private preview of these improvements and now we're excited to share them with all of you. Keep reading to learn more about these improvements!
Register for MFA and SSPR in a single experience
In the current Azure AD experience, users who are enabled for both MFA and SSPR must register their security info in separate experiences. We've heard from you that this causes confusion and frustration for users, especially if they have to register the same info, such as phone number, twice.
Before: MFA registration experience.

Before: SSPR registration experience.
With the new combined experience users can register their security info for both MFA and SSPR in a single, combined flow. This means users get to register once and benefit from both features!
A single, updated security info registration experience.
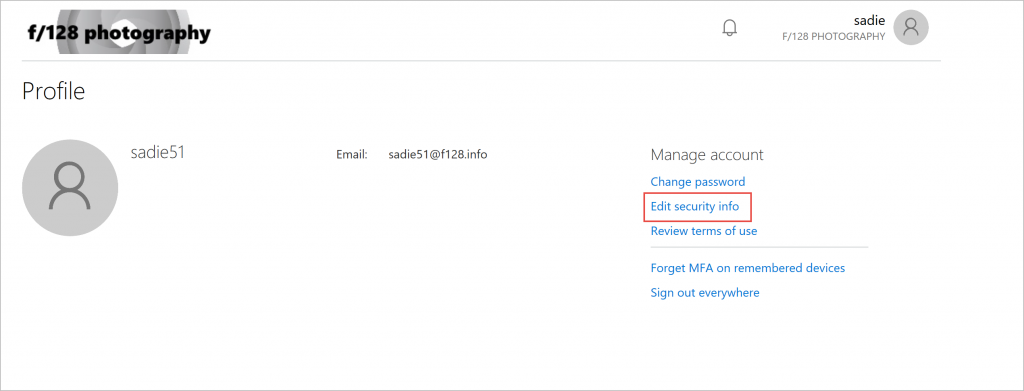
After registering, users can manage their security info from their profile or by going to security info registration .
Profile page with Edit security info link to manage security info.
Here users can add more security info, change or delete previously registered info, and choose their default methods for MFA.
Security info management page.
Users who previously registered for MFA or SSPR through the separate experiences can manage their registered info through this new experience. We have created new documentation for this experience that shows users how to register and manage their security info. We recommend that you review this documentation and use it to prepare your users for the new experience. In particular, users who are familiar with the previous app password registration experience should follow the steps listed in our apps passwords tutorial to register app passwords in the new experience. You can enable this experience for a group of users or all users in your organization today by following these steps . You can also let us know about your experience with this preview by filling out our survey .Improved registration experience for the Microsoft Authenticator app
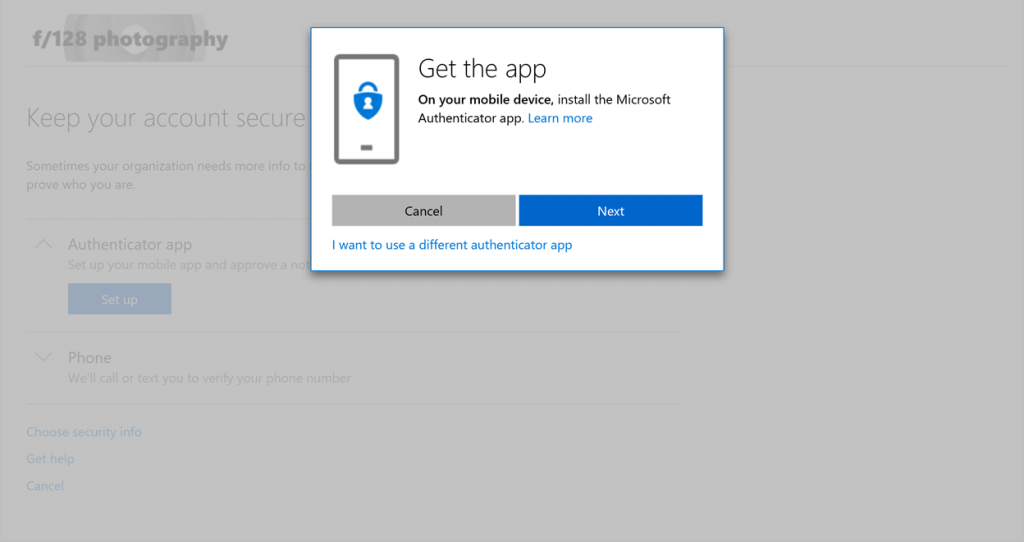
Not only does this new experience give users the ability to register for two features at once, but we also made each step in the registration process more intuitive. In particular, we improved the registration experience for the Microsoft Authenticator app (or any other authenticator app). Clear instructions and illustrations walk users through each step of registering their authenticator app. In addition, users who register from their mobile device can setup their account in the Microsoft Authenticator app with a single tap.
First step in the Microsoft Authenticator app registration experience.
To learn more about registering the Microsoft Authenticator app, check out our user guide .Reset passwords using Microsoft Authenticator
Users who register the Microsoft Authenticator app (or another authenticator app) through the new security info registration experience or the current MFA registration experience can use an authenticator app to prove who they are to reset their password.
Mobile app options in Password reset settings.
You can quickly enable this feature from the Azure AD portal under Password reset settings—simply check the Mobile app notification and Mobile app code options. To learn more about how to enable your users to reset their password using the Microsoft Authenticator app, check out our documentation .Tell us what you think
As always, we want to hear any feedback or suggestions you have. Please let us know what you think in the comments below or send us an email at ssprfeedback@microsoft.com . Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity DivisionUpdated Jul 24, 2020
Version 8.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.