First published on CloudBlogs on Jun, 22 2018
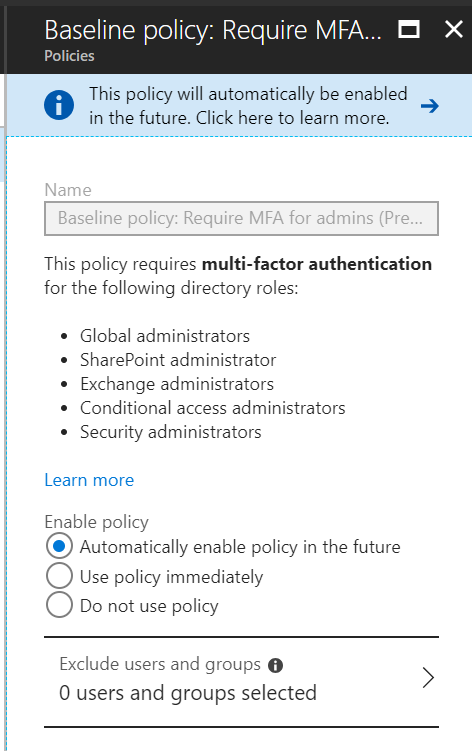
Howdy folks, Identity attacks have increased by 300% in the last year. To protect our customers from these ever-increasing attacks, Microsoft is embarking on a journey to rollout baseline protection. To that end, I'm excited to announce today the public preview of the first baseline policy to protect privileged Azure AD accounts. This baseline policy will be available by default to all Azure AD tenants and will require MFA for privileged Azure AD accounts. Attackers who get control of privileged accounts can do tremendous damage, so it's critical to protect these accounts first. The following Azure AD roles are covered by this policy:
Howdy folks, Identity attacks have increased by 300% in the last year. To protect our customers from these ever-increasing attacks, Microsoft is embarking on a journey to rollout baseline protection. To that end, I'm excited to announce today the public preview of the first baseline policy to protect privileged Azure AD accounts. This baseline policy will be available by default to all Azure AD tenants and will require MFA for privileged Azure AD accounts. Attackers who get control of privileged accounts can do tremendous damage, so it's critical to protect these accounts first. The following Azure AD roles are covered by this policy:
- Global administrator
- SharePoint administrator
- Exchange administrator
- Conditional access administrator
- Security administrator
Get started today
To enable baseline policy, follow the steps below:- Sign-in to the Azure portal with a global administrator, security administrator, or conditional access administrator account
-
Navigate to the Conditional access blade. You'll see the baseline policy to require MFA for admins
- Click on the baseline policy
-
To enable the policy immediately, select "Use policy immediately"
- Exclude users or groups as appropriate ( Recommendation: Exclude one " emergency-access administrative account " to ensure you are not locked out of the tenant)
- Save the policy
Tell us what you think
As always, we want to hear your feedback! Please let us know what you think of this new policy and how it's working for you. We're listening! Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity DivisionUpdated Jul 24, 2020
Version 11.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.