Anas Hadidi and Shruti Ailani bring this blog to you to help you leverage Security Copilot automations to understand your cyber exposure via Microsoft Security Exposure Management (MSEM) which can be an aggregator for your Microsoft or non-Microsoft exposure sources.
Introduction
Microsoft Security Exposure Management (MSEM) provides the Cyber Defense team with a unified, continuously updated awareness of assets exposure, relevant attack paths and provides classifications to these findings. While MSEM continuously creates and updates these finding, the Security Operations Center (SOC) Engineering team needs to reach to this data and interact with it as a part of their proactive discovery exercises.
Microsoft Security Copilot (SCP) on the other hand, acts as an always-ready AI-powered copilot to the SOC Engineering team. When combined, the situational awareness from MSEM and the quick and consistent retrieval capabilities of SCP, MSEM and SCP empower the SOC Engineers with a natural-language front door into exposure insights and attack paths, this combination also opens the door to include MSEM content, and the reasoning over this content in Security Copilot prompts, in prompt books and allows the use of this content in automation scenarios that leverage security copilot.
Traditionally, a SOC person needs to navigate to Microsoft Security Advanced Hunting, retrieve data related to assets with a certain level of exposure, and then start building plans for each asset to reduce its exposure, a plan that needs to take into consideration the nature of the exposure, the location the asset is hosted and the characteristics of the asset and requires working knowledge of each impacted system. This approach:
- Is a time-consuming process, especially when taking into consideration the learning curve associated with learning about each exposure before deciding on the best course of exposure reduction; and
- Can result in some undesired habits like adapting a reactive approach, rather than a proactive approach; Prioritizing assets with a certain exposure risk level; or attending to exposures that are already familiar to the person reviewing the list of exposures and attack paths.
Overview of Exposure Management
Microsoft Security Exposure Management is a security solution that provides a unified view of security posture across company assets and workloads. Security Exposure Management enriches asset information with security context that helps you to proactively manage attack surfaces, protect critical assets, and explore and mitigate exposure risk.
Who uses Security Exposure Management?
Security Exposure Management is aimed at:
- Security and compliance admins responsible for maintaining and improving organizational security posture.
- Security operations (SecOps) and partner teams who need visibility into data and workloads across organizational silos to effectively detect, investigate, and mitigate security threats.
- Security architects responsible for solving systematic issues in overall security posture.
- Chief Information Security Officers (CISOs) and security decision makers who need insights into organizational attack surfaces and exposure in order to understand security risk within organizational risk frameworks.
What can I do with Security Exposure Management?
With Security Exposure Management, you can:
- Get a unified view across the organization
- Manage and investigate attack surfaces
- Discover and safeguard critical assets
- Manage exposure
- Connect your data
Reference links:
|
Overview Get started Concept |
How-To Guide
|
Overview of Security Copilot plugins and skills
Microsoft Security Copilot is a generative AI-powered assistant designed to augment security operations by accelerating detection, investigation, and response. Its extensibility through plugins and skills enables organizations to tailor the platform to their unique environments, integrate diverse data sources, and automate complex workflows.
Plugin Architecture and Categories:
Security Copilot supports a growing ecosystem of plugins categorized into:
- First-party plugins: Native integrations with Microsoft services such as Microsoft Sentinel, Defender XDR, Intune, Entra, Purview, and Defender for Cloud.
- Third-party plugins: Integrations with external security platforms and ISVs, enabling broader telemetry and contextual enrichment.
- Custom plugins: User-developed extensions using KQL, GPT, or API-based logic to address specific use cases or data sources.
Plugins act as grounding sources—providing context, verifying responses, and enabling Copilot to operate across embedded experiences or standalone sessions. Users can toggle plugins on/off, prioritize sources, and personalize settings (e.g., default Sentinel workspace) to streamline investigations.
Skills and Promptbooks
Skills in Security Copilot are modular capabilities that guide the AI in executing tasks such as incident triage, threat hunting, or policy analysis. These are often bundled into promptbooks, which are reusable, scenario-driven workflows that combine plugins, prompts, and logic to automate investigations or compliance checks.
Security analysts can create, manage, and share promptbooks across tenants, enabling consistent execution of best practices. Promptbooks can be customized to include plugin-specific logic, such as querying Microsoft Graph API or running KQL-based detections.
Role-Based Access and Governance
Security Copilot enforces role-based access through Entra ID security groups:
- Copilot Owners: Full access to manage plugins, promptbooks, and tenant-wide settings.
- Copilot Contributors: Can create sessions and use promptbooks but have limited plugin publishing rights.
Each embedded experience may require additional service-specific roles (e.g., Sentinel Reader, Endpoint Security Manager) to access relevant data. Governance files and onboarding templates help teams align plugin usage with organizational policies.
Connecting Exposure Management with Security Copilot
There are multiple benefits of connecting MSEM with Security Copilot (as explained in section 1 [Introduction] of this paper). We wrote a plugin with two skills to harness the Exposure Management insights within Security Copilot and to eventually understand the exposure of assets hosted in a particular cloud platform by your organization and of assets belonging to a specific user.
A high-level architecture of the connectivity looks like this:
The two skills of the plugins correspond to the following two use cases:
- Obtain exposure of an asset hosted on a particular cloud platform by your organization
- Obtain exposure of an asset belonging to a specific user
As a user you could also specify the exposure level for which you want to extract the data, in each of the above use cases.
Plugin Code (YAML)
GitHub - Microsoft Security Exposure Management plugin for Security Copilot - YAML
Proof of Concept (screen video)
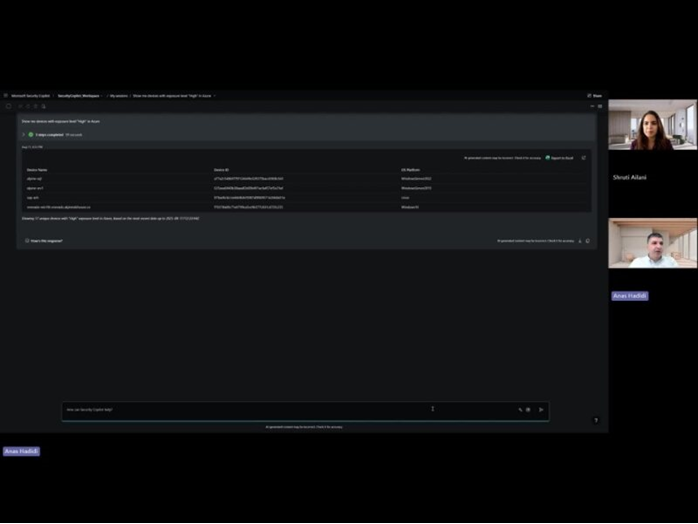
Conclusion
Here, we proposed an alternative approach that drives up the SOC’s efficiency and helps the organization reduce the time from exposure discovery to exposure reduction. The alternative approach proposed allows the SOC person to retrieve assets that fit a certain profile, i.e. prompt Security Copilot to “List all assets hosted on Azure with Low Exposure Level” and after all affected assets are retrieved, the user can then prompt Security Copilot to “For each asset, help me create a 7-days plan to reduce these exposures” and can then finally conclude with the prompt “Create an Executive Report, start by explaining to none-technical audience the risks associated with the identified exposures, then list all affected assets, along with a summary of the steps needed to reduce the exposures identified”. These prompts can also be organized in a promptbook, further reducing the burden on the SOC person, and can also be made using Automation on regular intervals, where the automation can later email the report to intended audience or can be further extended to create relevant tickets in the IT Service Management System.
An additional approach to risk management is to keep an eye on highly targeted personas within the organization, with the proposed integration a SOC person can prompt Security Copilot to find “What are the exposure risks associated with the devices owned by the Contoso person john.doe@contoso.com”. This helps the SOC person identify and remediate attack paths targeting devices used by highly targeted persons, where the SOC person can, within the same session, start digging deeper into finding any potential exploitation of these exposures, get recommendations on how to reduce these exposures, and draft an action plan.
 Microsoft
MicrosoftMicrosoft Security Copilot is a generative AI-powered assistant for daily operations in security and IT that empowers teams to manage and protect at the speed and scale of AI.
