First published on CloudBlogs on Aug 26, 2016
This post was authored by Chris Green, Senior Program Manager, Microsoft Intune. On August 25th, 2016 Lookout released research , conducted in partnership with The Citizen Lab (Munk School of Global Affairs, University of Toronto), about a sophisticated, targeted, and persistent mobile attack on iOS that uses three zero-day vulnerabilities called “Trident.” When exploited, these vulnerabilities can form an attack chain that subverts even Apple’s strong security. According to Lookout’s research, Trident is used in a mobile spyware product called Pegasus, attributed to an organization called NSO Group , to attack high-value targets. The Pegasus attack starts with SMS phishing using spoofed sender numbers and anonymized domains to deliver malware to the target’s iPhone. The target’s phone is remotely jailbroken and immediately starts compromising the target’s digital life. Further, Pegasus has a built-in self-destruct capability. Lookout’s research reveals that the system is always monitoring to see if it’s been discovered. If it detects tampering, it has the ability to wipe itself out. Lookout is reporting that their products detect and alert customers to this threat. Lookout has published extensive information on this threat in this blog post and this associated white paper . Microsoft and Lookout have been working together on a partnership for mobile security that can help you insure that your corporate assets are always protected. In addition to the use of mobile security technology, Microsoft Intune, part of the Enterprise Mobility + Security (EMS) suite, provides capabilities to help reduce the risk of data loss due to compromised devices by helping ensure that devices are up to date and fully patched. Given that OS updates take time to roll out across all devices in your organization, you can run the Intune Mobile Device Inventory report to view which devices are still vulnerable. This report shows all devices that are enrolled in Intune MDM, plus devices connected to Exchange through Exchange ActiveSync (the latter requires the Exchange connector to be deployed). The report will enable you to identify who you should follow up with to ensure they plan to install the latest updates.
You can start enforcing an update by setting the minimum OS version setting in an Intune compliance policy and using Conditional Access to restrict access to services like Exchange Online and SharePoint Online.
The report will enable you to identify who you should follow up with to ensure they plan to install the latest updates.
You can start enforcing an update by setting the minimum OS version setting in an Intune compliance policy and using Conditional Access to restrict access to services like Exchange Online and SharePoint Online.
 You can also specify a patch version for Android devices.
You can also specify a patch version for Android devices.
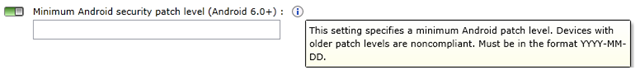 Users who attempt to connect to these services from an unpatched device will be blocked until they are at the required version. It is recommended that organizations provide early notification to users before this policy goes into effect.
Users who attempt to connect to these services from an unpatched device will be blocked until they are at the required version. It is recommended that organizations provide early notification to users before this policy goes into effect.

 You can use these methods to help ensure that iOS, Android, Windows, and Windows Phone devices are patched and up to date.
You can use these methods to help ensure that iOS, Android, Windows, and Windows Phone devices are patched and up to date.
This post was authored by Chris Green, Senior Program Manager, Microsoft Intune. On August 25th, 2016 Lookout released research , conducted in partnership with The Citizen Lab (Munk School of Global Affairs, University of Toronto), about a sophisticated, targeted, and persistent mobile attack on iOS that uses three zero-day vulnerabilities called “Trident.” When exploited, these vulnerabilities can form an attack chain that subverts even Apple’s strong security. According to Lookout’s research, Trident is used in a mobile spyware product called Pegasus, attributed to an organization called NSO Group , to attack high-value targets. The Pegasus attack starts with SMS phishing using spoofed sender numbers and anonymized domains to deliver malware to the target’s iPhone. The target’s phone is remotely jailbroken and immediately starts compromising the target’s digital life. Further, Pegasus has a built-in self-destruct capability. Lookout’s research reveals that the system is always monitoring to see if it’s been discovered. If it detects tampering, it has the ability to wipe itself out. Lookout is reporting that their products detect and alert customers to this threat. Lookout has published extensive information on this threat in this blog post and this associated white paper . Microsoft and Lookout have been working together on a partnership for mobile security that can help you insure that your corporate assets are always protected. In addition to the use of mobile security technology, Microsoft Intune, part of the Enterprise Mobility + Security (EMS) suite, provides capabilities to help reduce the risk of data loss due to compromised devices by helping ensure that devices are up to date and fully patched. Given that OS updates take time to roll out across all devices in your organization, you can run the Intune Mobile Device Inventory report to view which devices are still vulnerable. This report shows all devices that are enrolled in Intune MDM, plus devices connected to Exchange through Exchange ActiveSync (the latter requires the Exchange connector to be deployed).
 The report will enable you to identify who you should follow up with to ensure they plan to install the latest updates.
You can start enforcing an update by setting the minimum OS version setting in an Intune compliance policy and using Conditional Access to restrict access to services like Exchange Online and SharePoint Online.
The report will enable you to identify who you should follow up with to ensure they plan to install the latest updates.
You can start enforcing an update by setting the minimum OS version setting in an Intune compliance policy and using Conditional Access to restrict access to services like Exchange Online and SharePoint Online.
 You can also specify a patch version for Android devices.
You can also specify a patch version for Android devices.
 Users who attempt to connect to these services from an unpatched device will be blocked until they are at the required version. It is recommended that organizations provide early notification to users before this policy goes into effect.
Users who attempt to connect to these services from an unpatched device will be blocked until they are at the required version. It is recommended that organizations provide early notification to users before this policy goes into effect.

 You can use these methods to help ensure that iOS, Android, Windows, and Windows Phone devices are patched and up to date.
You can use these methods to help ensure that iOS, Android, Windows, and Windows Phone devices are patched and up to date.
Published Sep 08, 2018
Version 1.0Intune Team Microsoft
Microsoft
 Microsoft
MicrosoftJoined September 05, 2018
Security, Compliance, and Identity Blog
Follow this blog board to get notified when there's new activity