First published on CloudBlogs on Apr 11, 2016
Do you remember what it was like when everyone had desktop computers and data security focused on the best way to physically lock computers to heavy desks? In this article, we’ll review the ways security and access control have changed over the years, highlighting how Enterprise Mobility Suite (EMS) is poised to provide best-in-class solutions for a world with mobile devices and online services. Mobile Access v1: Mobile Laptops In the past, corporate data was hosted on-premises. It was accessed by desktops that were physically connected to the corporate network. Then, laptops emerged as the dominant corporate device, and the Virtual Private Network (VPN) was born. VPNs provided 3 primary functions: In the mobile-first, cloud-first world, a fundamentally different approach was needed, so we built access control and data protection directly into mobile devices, mobile apps, and the cloud infrastructure itself. In this world your network perimeter is replaced by an “identity perimeter.”
In the mobile-first, cloud-first world, a fundamentally different approach was needed, so we built access control and data protection directly into mobile devices, mobile apps, and the cloud infrastructure itself. In this world your network perimeter is replaced by an “identity perimeter.”
 That’s what we’ve built with Office 365 and the Enterprise Mobility Suite, as a supplement to the classic VPN provisioning mechanisms all EMM providers have for on-premises apps. EMS delivers integrated identity, access control, management, and data protection – built to protect your corporate data wherever it lives.
With EMS, whenever a mobile device or app attempts to authenticate to an online service (Microsoft or 3
rd
party) or on-premises web app (via
Azure AD Application Proxy
),
Azure Active Directory (AD)
subjects the request to criteria you define, consulting with the management system as needed. Is the mobile device managed and compliant with IT policies? Is the mobile app managed? Has the user presented multiple forms of authentication? Is the PC domain-joined and managed by ConfigMgr? Is the request coming from the corporate network or the internet? All of these criteria and more are provided without the need for VPN. It’s just built in. The diagram below shows how EMS ensures that you have the access controls in the cloud needed to replace the access controls in your VPNs.
That’s what we’ve built with Office 365 and the Enterprise Mobility Suite, as a supplement to the classic VPN provisioning mechanisms all EMM providers have for on-premises apps. EMS delivers integrated identity, access control, management, and data protection – built to protect your corporate data wherever it lives.
With EMS, whenever a mobile device or app attempts to authenticate to an online service (Microsoft or 3
rd
party) or on-premises web app (via
Azure AD Application Proxy
),
Azure Active Directory (AD)
subjects the request to criteria you define, consulting with the management system as needed. Is the mobile device managed and compliant with IT policies? Is the mobile app managed? Has the user presented multiple forms of authentication? Is the PC domain-joined and managed by ConfigMgr? Is the request coming from the corporate network or the internet? All of these criteria and more are provided without the need for VPN. It’s just built in. The diagram below shows how EMS ensures that you have the access controls in the cloud needed to replace the access controls in your VPNs.
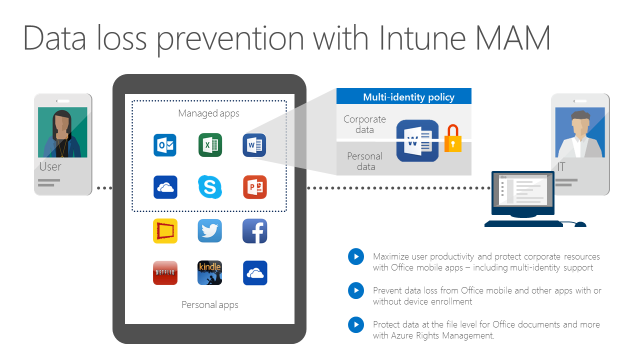
 In addition to providing cloud access control, Office 365 + EMS also provides native data protection. Again, this is based on identity and integrated with management. Was a corporate identity used to access the data? If yes, then the mobile apps will prevent the data from being shared with consumer apps or services via Save-As, Open-In, clipboard, etc (Intune MAM with or without device enrollment into MDM). Is the document itself explicitly protected by an access policy (Azure RMS)? If so, enforce access control on that file, even when it roams outside of apps and devices under management.
This integrated approach to data loss prevention enables the same application to isolate the corporate and personal data that it handles. This means your employees will not have to use separate apps for work. They can just use Office mobile apps for work and personal use and the right protections will apply at the right times. The diagram below shows this concept.
In addition to providing cloud access control, Office 365 + EMS also provides native data protection. Again, this is based on identity and integrated with management. Was a corporate identity used to access the data? If yes, then the mobile apps will prevent the data from being shared with consumer apps or services via Save-As, Open-In, clipboard, etc (Intune MAM with or without device enrollment into MDM). Is the document itself explicitly protected by an access policy (Azure RMS)? If so, enforce access control on that file, even when it roams outside of apps and devices under management.
This integrated approach to data loss prevention enables the same application to isolate the corporate and personal data that it handles. This means your employees will not have to use separate apps for work. They can just use Office mobile apps for work and personal use and the right protections will apply at the right times. The diagram below shows this concept.
 The Advantages of the Cloud-first, Mobile-first Approach Used by Office 365 + EMS
As mobile access evolves from VPN-based to identity-based, you’ll see several benefits:
The Advantages of the Cloud-first, Mobile-first Approach Used by Office 365 + EMS
As mobile access evolves from VPN-based to identity-based, you’ll see several benefits:
Do you remember what it was like when everyone had desktop computers and data security focused on the best way to physically lock computers to heavy desks? In this article, we’ll review the ways security and access control have changed over the years, highlighting how Enterprise Mobility Suite (EMS) is poised to provide best-in-class solutions for a world with mobile devices and online services. Mobile Access v1: Mobile Laptops In the past, corporate data was hosted on-premises. It was accessed by desktops that were physically connected to the corporate network. Then, laptops emerged as the dominant corporate device, and the Virtual Private Network (VPN) was born. VPNs provided 3 primary functions:
- They made it possible for laptops to reach corporate services on the Intranet
- They restricted corporate access to Internet-connected laptops
- They helped prevent data loss by encrypting communications and running agents on the laptops that helped contain data
 In the mobile-first, cloud-first world, a fundamentally different approach was needed, so we built access control and data protection directly into mobile devices, mobile apps, and the cloud infrastructure itself. In this world your network perimeter is replaced by an “identity perimeter.”
In the mobile-first, cloud-first world, a fundamentally different approach was needed, so we built access control and data protection directly into mobile devices, mobile apps, and the cloud infrastructure itself. In this world your network perimeter is replaced by an “identity perimeter.”
 That’s what we’ve built with Office 365 and the Enterprise Mobility Suite, as a supplement to the classic VPN provisioning mechanisms all EMM providers have for on-premises apps. EMS delivers integrated identity, access control, management, and data protection – built to protect your corporate data wherever it lives.
With EMS, whenever a mobile device or app attempts to authenticate to an online service (Microsoft or 3
rd
party) or on-premises web app (via
Azure AD Application Proxy
),
Azure Active Directory (AD)
subjects the request to criteria you define, consulting with the management system as needed. Is the mobile device managed and compliant with IT policies? Is the mobile app managed? Has the user presented multiple forms of authentication? Is the PC domain-joined and managed by ConfigMgr? Is the request coming from the corporate network or the internet? All of these criteria and more are provided without the need for VPN. It’s just built in. The diagram below shows how EMS ensures that you have the access controls in the cloud needed to replace the access controls in your VPNs.
That’s what we’ve built with Office 365 and the Enterprise Mobility Suite, as a supplement to the classic VPN provisioning mechanisms all EMM providers have for on-premises apps. EMS delivers integrated identity, access control, management, and data protection – built to protect your corporate data wherever it lives.
With EMS, whenever a mobile device or app attempts to authenticate to an online service (Microsoft or 3
rd
party) or on-premises web app (via
Azure AD Application Proxy
),
Azure Active Directory (AD)
subjects the request to criteria you define, consulting with the management system as needed. Is the mobile device managed and compliant with IT policies? Is the mobile app managed? Has the user presented multiple forms of authentication? Is the PC domain-joined and managed by ConfigMgr? Is the request coming from the corporate network or the internet? All of these criteria and more are provided without the need for VPN. It’s just built in. The diagram below shows how EMS ensures that you have the access controls in the cloud needed to replace the access controls in your VPNs.
 In addition to providing cloud access control, Office 365 + EMS also provides native data protection. Again, this is based on identity and integrated with management. Was a corporate identity used to access the data? If yes, then the mobile apps will prevent the data from being shared with consumer apps or services via Save-As, Open-In, clipboard, etc (Intune MAM with or without device enrollment into MDM). Is the document itself explicitly protected by an access policy (Azure RMS)? If so, enforce access control on that file, even when it roams outside of apps and devices under management.
This integrated approach to data loss prevention enables the same application to isolate the corporate and personal data that it handles. This means your employees will not have to use separate apps for work. They can just use Office mobile apps for work and personal use and the right protections will apply at the right times. The diagram below shows this concept.
In addition to providing cloud access control, Office 365 + EMS also provides native data protection. Again, this is based on identity and integrated with management. Was a corporate identity used to access the data? If yes, then the mobile apps will prevent the data from being shared with consumer apps or services via Save-As, Open-In, clipboard, etc (Intune MAM with or without device enrollment into MDM). Is the document itself explicitly protected by an access policy (Azure RMS)? If so, enforce access control on that file, even when it roams outside of apps and devices under management.
This integrated approach to data loss prevention enables the same application to isolate the corporate and personal data that it handles. This means your employees will not have to use separate apps for work. They can just use Office mobile apps for work and personal use and the right protections will apply at the right times. The diagram below shows this concept.
 The Advantages of the Cloud-first, Mobile-first Approach Used by Office 365 + EMS
As mobile access evolves from VPN-based to identity-based, you’ll see several benefits:
The Advantages of the Cloud-first, Mobile-first Approach Used by Office 365 + EMS
As mobile access evolves from VPN-based to identity-based, you’ll see several benefits:
- Cost savings compared to VPNs . VPN technology is typically expensive and complex. Deploying VPN agents, profiles, and certificates is also complex and expensive. As more and more of your data moves to the cloud, you’ll enable larger and larger populations of cloud-only users that don’t require a VPN and everything it carries.
- Simpler access infrastructure to operate . Instead of operating a global scale network perimeter with various proxies, gateways, and VPNs, you just need to connect your existing on premise AD with the Azure Active Directory. From there, Office 365 and other SaaS apps will route their authentication through Azure AD and your modern access controls will be enforced.
- Better end user experiences . With EMS’s identity-based access control, your end users will not have to install and launch separate VPN apps. The access control experience is natively a part of the sign-in experience in the mobile apps. Since your traffic isn’t bounced from the Internet to the Intranet and back, your employees get better latency and performance in their mobile apps.
- Positioned for the future . Once your basic cloud access infrastructure is in place, you have a fantastic foundation for future innovation. In the past year, we’ve introduced many enhancements in EMS for access control and data protection. A small sampling includes things like tracking mobile document usage (Azure RMS), enabling cloud access control for requests coming from desktop apps (Azure AD), and enabling MAM on unmanaged BYOD devices (Intune). Because these capabilities are provided from the cloud, they come often and automatically. You don’t need to plan upgrades or migrations to start to take advantage of the latest and greatest. Compare this to your VPN infrastructure today and the tremendous amount of effort it takes to upgrade to the latest and greatest.
- Watch a deep dive on conditional access capabilities in EMS
- Read how EMS prevents data loss from Office 365 and Office mobile apps
- Check out a step-by-step deployment guide for conditional access with Intune
- Find out how to migrate to Intune
- Get a free 30-day trial for EMS
- Provide feedback to Intune engineering team
Published Sep 08, 2018
Version 1.0Intune Team
Brass Contributor
Joined September 05, 2018
Microsoft Security Community Blog
Follow this blog board to get notified when there's new activity