First published on CloudBlogs on Oct 30, 2015
We are excited to share information on how to deploy Device Guard on Windows 10 devices managed by Configuration Manager, using existing capabilities in System Center 2012 R2 Configuration Manager SP1. With this inventory data you can build custom reports or create collections. Having a collection is beneficial as that can then be used to target deployments.
With this inventory data you can build custom reports or create collections. Having a collection is beneficial as that can then be used to target deployments.
 Device Guard Task Sequence Steps:
All of the following steps except the last are of type Run Command Line.
Device Guard Task Sequence Steps:
All of the following steps except the last are of type Run Command Line.

We are excited to share information on how to deploy Device Guard on Windows 10 devices managed by Configuration Manager, using existing capabilities in System Center 2012 R2 Configuration Manager SP1.
Why Device Guard?
Device Guard is a new feature of Windows 10 that provides better security against malware and zero-day attacks by blocking anything other than trusted apps. You are in control of what apps Device Guard considers trustworthy, either via vendor or Windows Store digital signatures, or via an easy process by which you can sign apps to be trusted by Device Guard. Device Guard can use hardware technology and virtualization to further isolate the Windows components which determine whether apps are trustworthy, which helps provide protection from attackers or malware that have elevated privileges. This gives Device Guard a significant advantage over traditional anti-malware and app control technologies like AppLocker, which can be subject to tampering by elevated users or processes. See the following article for more information on Windows 10 Device Guard: https://msdn.microsoft.com/en-us/library/dn986865.aspx .Manage Device Guard with Configuration Manager
You can use Configuration Manager today to help deploy Device Guard and Device Guard-enabled apps in your environment. Configuration Manager assists with the following scenarios:- Determine which clients meet the prerequisites to support Device Guard
- Enable Device Guard settings
- Deploy Device Guard policy
- Deploy Device Guard-enabled apps
- Open the Configuration Manager Console , switch to the Administration workspace, and select Client Settings . For purposes of this demonstration, let’s just open properties of the Default Client Settings (but understand that you could create a custom client device setting for this purpose).
- Select the Hardware Inventory group, and then click Set Classes .
- Device Guard includes a WMI class to query its configuration and management state, which can be added as a custom hardware inventory class. Click Add .
- Click Connect . If you are running the console on a Windows 10 client, then keep the local computer name. Otherwise, you will need to specify the name of a remote Windows 10 client. In either case, the WMI namespace is rootMicrosoftWindowsDeviceGuard
- Select the Win32_DeviceGuard class
- Click OK to save everything.
 With this inventory data you can build custom reports or create collections. Having a collection is beneficial as that can then be used to target deployments.
With this inventory data you can build custom reports or create collections. Having a collection is beneficial as that can then be used to target deployments.
- Create a device collection. (See How to Create Collections in Configuration Manager in the TechNet Library.)
- Use the following WQL statement as the query rule for this collection:
- If you have a custom image of Windows 10, enable Hyper-V Hypervisor in the captured image
- Enable the Hyper-V Hypervisor feature in a custom Unattend.xml answer file during the Windows 10 deployment
- For an operational system that does not already have this feature enabled, create a simple script which calls DISM to enable the Hyper-V Hypervisor feature, and deploy that script as a package or application.
 Device Guard Task Sequence Steps:
All of the following steps except the last are of type Run Command Line.
Device Guard Task Sequence Steps:
All of the following steps except the last are of type Run Command Line.
- Enable Isolated User Mode Feature dism.exe /NoRestart /Online /Enable-Feature:IsolatedUserMode /All
- Enable Virtualization Based Security reg.exe add "HKLMSYSTEMCurrentControlSetControlDeviceGuard" /v "EnableVirtualizationBasedSecurity" /t REG_DWORD /d 1 /f
- Require Platform Security Features reg.exe add "HKLMSYSTEMCurrentControlSetControlDeviceGuard" /v "RequirePlatformSecurityFeatures" /t REG_DWORD /d 2 /f
- Enable Hypervisor-Enforced Code Integrity reg.exe add "HKLMSYSTEMCurrentControlSetControlDeviceGuard" /v "HypervisorEnforcedCodeIntegrity" /t REG_DWORD /d 1 /f
-
Install Code Integrity Policy
xcopy \servershareSIPolicy.p7b C:Windowssystem32CodeIntegrity /y
- NOTE: you will need to put the SIPolicy.p7b file on a real file share and update the path accordingly. Also remember that the task sequence runs under the context of Local System, so you need to make sure that the computer account (for example, domaincomputername$) has permissions to the share and file.
-
Restart Computer
- Be sure to set the option, “The currently installed default operating system”
- You can configure the notification and timer options as needed.
- Create the application (in this demonstration we’re using 7-Zip)
- Create one deployment type with the command line to install the app per normal
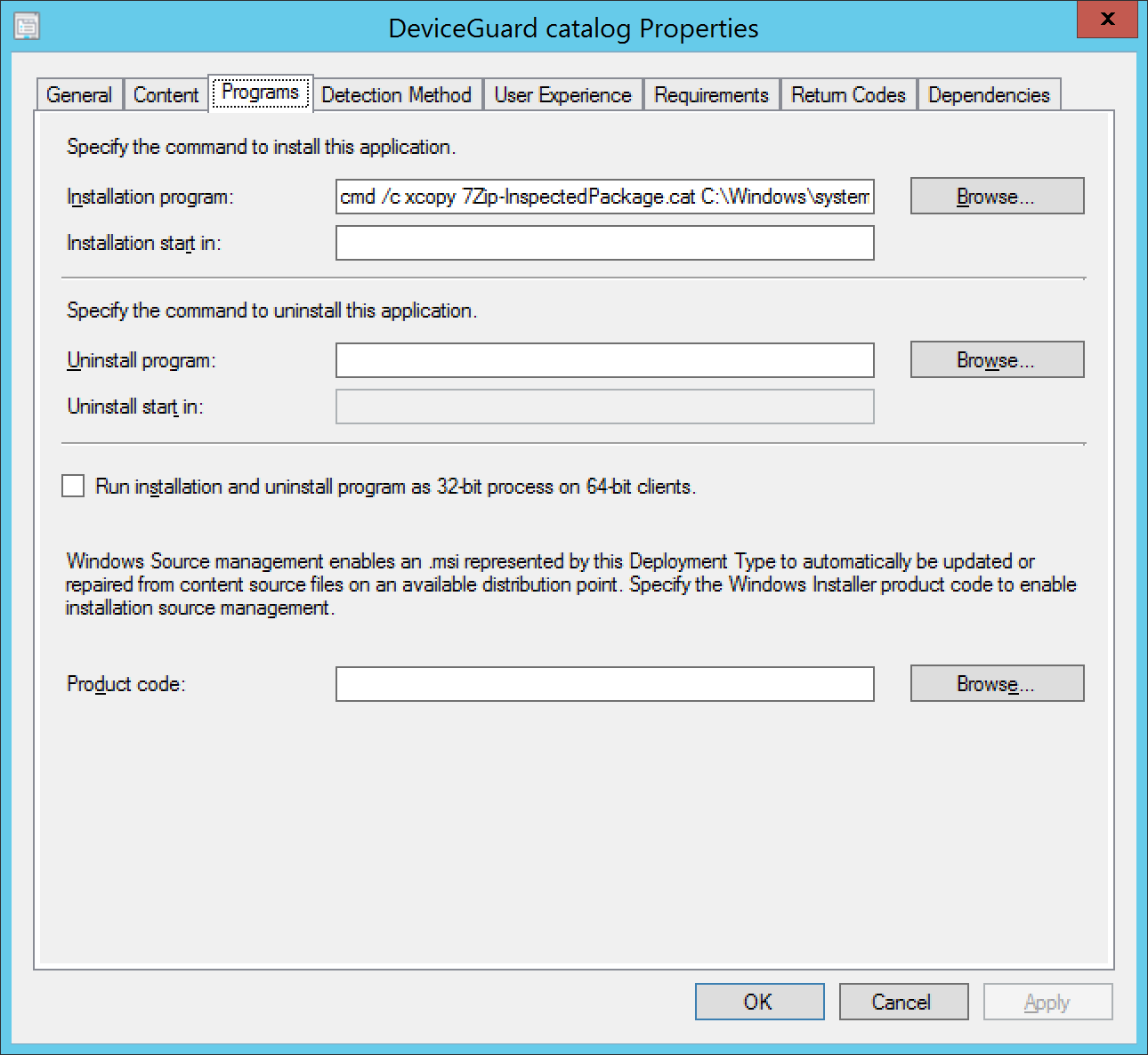
- Create a second deployment type (script) using the same content directory with the following command line: cmd /c xcopy 7Zip-InspectedPackage.cat C:Windowssystem32catroot{F750E6C3-38EE-11D1-85E5-00C04FC295EE} /y
-
Other options that can be configured on this DT to fully leverage the capabilities of the Configuration Manager application model:
- Detection Method: the catalog file exists in the catroot folder
- Requirements: Operating system is Windows 10
- Make the first “install” DT dependent upon the second DT. This will cause the catalog to be copied and then the setup command line run



Conclusion
As we said above this can be used right now with in-market versions of Configuration Manager to support Device Guard. We are investigating more integrated support for Device Guard in a future release of Configuration Manager. Contributors:- Aaron Czechowski, Senior Program Manager, Enterprise Client Management
- Dune Desormeaux, Program Manager, Enterprise Client Management
- Nazmus Sakib, Program Manager, Windows Enterprise and Security
- Jeffrey Sutherland, Principal Program Manager Lead, Windows Enterprise and Security
Published Sep 08, 2018
Version 1.0yvetteomeally Microsoft
Microsoft
 Microsoft
MicrosoftJoined August 30, 2016
Microsoft Security Community Blog
Follow this blog board to get notified when there's new activity