First published on CloudBlogs on May, 04 2015
Howdy folks, It's a big big big day for us here in the Identity and Security Services team at Microsoft! If you've seen one of my presentations ("Identity is the new control plane"), you know that one of the things that sets us apart is our focus on delivering a complete hybrid identity solution. We want to be a one stop shop for all your identity needs, on premise and in the cloud. That includes providing a set of great security and health monitoring systems to manage and protect your identity control plane. This vision of building a complete solution motivated us to create Azure AD Connect Health , it motivated the investments we've made in Azure MFA, and it motivates our work in machine learning applied to security detection and mitigation. Today in the cloud we can detect and help protect your organization against a host of attacks, including brute force attacks, attacks from anonymizers, anomalous attacks from atypical locations and many other types of attacks. Customers have told us that they LOVE the level of monitoring and security we provides them. In many cases it's richer than what they get on-premises. And customers are constantly asking "Could you give me something that provides me the same level of monitoring and security for my on-premises Active Directory that you give me for Azure AD in the cloud?" Today I'm happy to be able to answer "Why yes, we can!" We've just released the preview of Microsoft Advanced Threat Analytics (ATA). Microsoft ATA is a new on-premises product that brings Azure AD style security monitoring and anomaly detection on-premises. Microsoft ATA is based on the innovative work done by Aorato, a startup company we acquired in November . To give you the details, I've asked Idan Plotnik, the former CEO of Aorato and now the Principal Group Manager of our Microsoft ATA team, to write a guest blog post which you'll find below. I've had the opportunity to get to know Idan and his team over the past ~9 months and I couldn't be more excited about the passion and energy they bring or the product they are building! I hope you'll be as excited about Microsoft ATA as we are. And of course as always, we would love to get any feedback or suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity and Security Division ---------------------------------------- Hi all! My name is Idan Plotnik. I am the Principal Group Manager of Microsoft Advanced Threat Analytics team and the former CEO of Aorato, acquired by Microsoft . At Microsoft, my group is responsible for on-premises user behavior and advanced threat analytics. Microsoft Advanced Threat Analytics in public preview Today, I'm super excited to announce the public preview of Microsoft Advanced Threat Analytics (ATA), an innovative product based on Aorato technology. Since the acquisition, we have been working nonstop on integrating our technology and team with Microsoft to bring this to our customers as quickly as possible, and to help identify security breaches before they cause damage. In this blog post, I will share the details of this new and innovative on-premises product that will help you protect your organizations from advanced targeted attacks. The blind spot in IT security Cybersecurity attacks are more frequent and more sophisticated than ever. We know you are now living in a world where you assume you are breached and attackers are already in your systems. We know from our customers and industry studies that it's not unusual for attackers to have access to a corporate networks for 200 days or more before they're discovered. They do this by taking advantage of privileged or non-privileged user accounts to access resources without their knowledge. This is a huge blind spot in most IT security systems. When the attackers use this blind spot to hide in a company's network, innovative and advanced technology is needed to detect the breach, mitigate and prevent further attacks. I'm happy to let you know that starting today, we're making a preview of this technology available to you! We founded Aorato in 2010 based on the belief that the only way to detect advanced attacks is a combination of entity (users, devices, and resources) behavior analysis (usually referred as User Behavior Analytics [UBA] today) and real-time detection of the attacker's Tactics, Techniques and Procedures (TTPs). After working closely with customers and building ATA with the group, I want to share two important insights we have learned about protecting your organization from security breaches: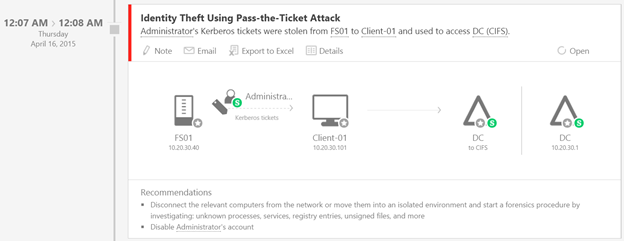 To increase accuracy and save you time and resources, ATA doesn't only compare the entity's behaviors to its profile, but also to the profiles with similar roles in its interaction graph. This means that the number of false positives are dramatically reduced, freeing you up to focus on the real threats.
ATA is the only user behavior analytics solution today that will dynamically prompt the user for inputs, and automatically adjusts its learning and detection capabilities.
Designed for simplicity
We love to keep it simple! Microsoft Advanced Threat Analytics is a non-intrusive solution, our deployment is very simple, you don't need any rules, policies or agents, just configure port-mirroring and within a few hours you will see results!
Many security analysts have told us that they are overwhelmed with the constant reporting of traditional security tools and the task of sifting through them to locate anomalies. The ATA attack timeline is a clear, efficient, and convenient feed that surfaces the right things at the right time, giving you the power of perspective on the who, what, when, why, and how. ATA provides visibility like in a social network, you can search for any users, devices or resources and see their behavioral profile.
Try it today
You can start evaluating Microsoft Advanced Threat Analytics today. Please
download
our public preview version and our
deployment guide
and enjoy the ride! You can your questions and feedback in the discussion
forum
and we will respond to you as quickly as possible.
And if you are interested in cybersecurity or hearing about our latest updates and improvements, please follow me on Twitter
@IdanPlotnik
. For questions or feedback you can contact
me
directly, or send your feedback directly to the
group
.
Last but not least, a few words on our special group including engineers, data scientists, security researchers and program managers: we have top notch cybersecurity experts and our goal is to help you protect your organization from security breaches.
Thank you! We are here for you!
Idan Plotnik (Twitter:
@IdanPlotnik
)
Principal Group Manager
Microsoft Identity and Security Service Division
To increase accuracy and save you time and resources, ATA doesn't only compare the entity's behaviors to its profile, but also to the profiles with similar roles in its interaction graph. This means that the number of false positives are dramatically reduced, freeing you up to focus on the real threats.
ATA is the only user behavior analytics solution today that will dynamically prompt the user for inputs, and automatically adjusts its learning and detection capabilities.
Designed for simplicity
We love to keep it simple! Microsoft Advanced Threat Analytics is a non-intrusive solution, our deployment is very simple, you don't need any rules, policies or agents, just configure port-mirroring and within a few hours you will see results!
Many security analysts have told us that they are overwhelmed with the constant reporting of traditional security tools and the task of sifting through them to locate anomalies. The ATA attack timeline is a clear, efficient, and convenient feed that surfaces the right things at the right time, giving you the power of perspective on the who, what, when, why, and how. ATA provides visibility like in a social network, you can search for any users, devices or resources and see their behavioral profile.
Try it today
You can start evaluating Microsoft Advanced Threat Analytics today. Please
download
our public preview version and our
deployment guide
and enjoy the ride! You can your questions and feedback in the discussion
forum
and we will respond to you as quickly as possible.
And if you are interested in cybersecurity or hearing about our latest updates and improvements, please follow me on Twitter
@IdanPlotnik
. For questions or feedback you can contact
me
directly, or send your feedback directly to the
group
.
Last but not least, a few words on our special group including engineers, data scientists, security researchers and program managers: we have top notch cybersecurity experts and our goal is to help you protect your organization from security breaches.
Thank you! We are here for you!
Idan Plotnik (Twitter:
@IdanPlotnik
)
Principal Group Manager
Microsoft Identity and Security Service Division
Howdy folks, It's a big big big day for us here in the Identity and Security Services team at Microsoft! If you've seen one of my presentations ("Identity is the new control plane"), you know that one of the things that sets us apart is our focus on delivering a complete hybrid identity solution. We want to be a one stop shop for all your identity needs, on premise and in the cloud. That includes providing a set of great security and health monitoring systems to manage and protect your identity control plane. This vision of building a complete solution motivated us to create Azure AD Connect Health , it motivated the investments we've made in Azure MFA, and it motivates our work in machine learning applied to security detection and mitigation. Today in the cloud we can detect and help protect your organization against a host of attacks, including brute force attacks, attacks from anonymizers, anomalous attacks from atypical locations and many other types of attacks. Customers have told us that they LOVE the level of monitoring and security we provides them. In many cases it's richer than what they get on-premises. And customers are constantly asking "Could you give me something that provides me the same level of monitoring and security for my on-premises Active Directory that you give me for Azure AD in the cloud?" Today I'm happy to be able to answer "Why yes, we can!" We've just released the preview of Microsoft Advanced Threat Analytics (ATA). Microsoft ATA is a new on-premises product that brings Azure AD style security monitoring and anomaly detection on-premises. Microsoft ATA is based on the innovative work done by Aorato, a startup company we acquired in November . To give you the details, I've asked Idan Plotnik, the former CEO of Aorato and now the Principal Group Manager of our Microsoft ATA team, to write a guest blog post which you'll find below. I've had the opportunity to get to know Idan and his team over the past ~9 months and I couldn't be more excited about the passion and energy they bring or the product they are building! I hope you'll be as excited about Microsoft ATA as we are. And of course as always, we would love to get any feedback or suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity and Security Division ---------------------------------------- Hi all! My name is Idan Plotnik. I am the Principal Group Manager of Microsoft Advanced Threat Analytics team and the former CEO of Aorato, acquired by Microsoft . At Microsoft, my group is responsible for on-premises user behavior and advanced threat analytics. Microsoft Advanced Threat Analytics in public preview Today, I'm super excited to announce the public preview of Microsoft Advanced Threat Analytics (ATA), an innovative product based on Aorato technology. Since the acquisition, we have been working nonstop on integrating our technology and team with Microsoft to bring this to our customers as quickly as possible, and to help identify security breaches before they cause damage. In this blog post, I will share the details of this new and innovative on-premises product that will help you protect your organizations from advanced targeted attacks. The blind spot in IT security Cybersecurity attacks are more frequent and more sophisticated than ever. We know you are now living in a world where you assume you are breached and attackers are already in your systems. We know from our customers and industry studies that it's not unusual for attackers to have access to a corporate networks for 200 days or more before they're discovered. They do this by taking advantage of privileged or non-privileged user accounts to access resources without their knowledge. This is a huge blind spot in most IT security systems. When the attackers use this blind spot to hide in a company's network, innovative and advanced technology is needed to detect the breach, mitigate and prevent further attacks. I'm happy to let you know that starting today, we're making a preview of this technology available to you! We founded Aorato in 2010 based on the belief that the only way to detect advanced attacks is a combination of entity (users, devices, and resources) behavior analysis (usually referred as User Behavior Analytics [UBA] today) and real-time detection of the attacker's Tactics, Techniques and Procedures (TTPs). After working closely with customers and building ATA with the group, I want to share two important insights we have learned about protecting your organization from security breaches:
-
Using only machine learning algorithms in User Behavioral Analytics is not enough to detect advanced attacks : a more comprehensive approach is neededIn most cases, the algorithms will detect anomalies after the fact when there is a good chance the attacker was already successful. The way to detect advanced attacks, is through the combination of detecting security issues and risks, attacks in real-time based on TTPs, and behavioral analysis leveraging Machine Learning algorithms. Only this combined approach gives you a comprehensive, timely view of your security posture.
-
Analysis of Multiple Data sources is the key to detecting advanced attacks .Analyzing logs will only tell you half the story and in the worst case will provide you false positives. The real evidence is located in the network packets. This is why you need the combination of deep packet inspection (DPI), log analysis, and information from Active Directory to detect advanced attacks.
- Abnormal Behavior : ATA uses Machine Learning algorithms to identify normal and abnormal entity behavior and will detect anomalous logins, abnormal resource access, and even unusual working hours.
- Advanced attacks in near real-time based on TTPs: ATA uses DPI and information from other sources to identify advanced attacks such as Pass-the-Hash, Pass-the-Ticket, Overpass-the-Hash, Forged PAC ( MS14-068 ), Golden Ticket, and Remote Execution on the Domain Controllers, Skeleton Key Malware, Honey token activities and more.
- Known security issues and risks : ATA will identify known security issues and risks such as service account expose passwords in cleartext over the network, broken trust, weak protocols and protocol vulnerabilities.
-
An attacker starts the reconnaissance process to be able to build his attack path
-
Next he will use the relevant information to Brute Force accounts' passwords
-
once he gets his hands on a password he can log-in to different machines, move laterally and search for a privileged account that previously logged-in to a device:
- Then he can steal the NTLM hash or Kerberos tickets of that privileged account and perform a Pass-the-Hash/Ticket attack, moving laterally and access resources on-behalf of the user without their knowledge.
 To increase accuracy and save you time and resources, ATA doesn't only compare the entity's behaviors to its profile, but also to the profiles with similar roles in its interaction graph. This means that the number of false positives are dramatically reduced, freeing you up to focus on the real threats.
ATA is the only user behavior analytics solution today that will dynamically prompt the user for inputs, and automatically adjusts its learning and detection capabilities.
Designed for simplicity
We love to keep it simple! Microsoft Advanced Threat Analytics is a non-intrusive solution, our deployment is very simple, you don't need any rules, policies or agents, just configure port-mirroring and within a few hours you will see results!
Many security analysts have told us that they are overwhelmed with the constant reporting of traditional security tools and the task of sifting through them to locate anomalies. The ATA attack timeline is a clear, efficient, and convenient feed that surfaces the right things at the right time, giving you the power of perspective on the who, what, when, why, and how. ATA provides visibility like in a social network, you can search for any users, devices or resources and see their behavioral profile.
Try it today
You can start evaluating Microsoft Advanced Threat Analytics today. Please
download
our public preview version and our
deployment guide
and enjoy the ride! You can your questions and feedback in the discussion
forum
and we will respond to you as quickly as possible.
And if you are interested in cybersecurity or hearing about our latest updates and improvements, please follow me on Twitter
@IdanPlotnik
. For questions or feedback you can contact
me
directly, or send your feedback directly to the
group
.
Last but not least, a few words on our special group including engineers, data scientists, security researchers and program managers: we have top notch cybersecurity experts and our goal is to help you protect your organization from security breaches.
Thank you! We are here for you!
Idan Plotnik (Twitter:
@IdanPlotnik
)
Principal Group Manager
Microsoft Identity and Security Service Division
To increase accuracy and save you time and resources, ATA doesn't only compare the entity's behaviors to its profile, but also to the profiles with similar roles in its interaction graph. This means that the number of false positives are dramatically reduced, freeing you up to focus on the real threats.
ATA is the only user behavior analytics solution today that will dynamically prompt the user for inputs, and automatically adjusts its learning and detection capabilities.
Designed for simplicity
We love to keep it simple! Microsoft Advanced Threat Analytics is a non-intrusive solution, our deployment is very simple, you don't need any rules, policies or agents, just configure port-mirroring and within a few hours you will see results!
Many security analysts have told us that they are overwhelmed with the constant reporting of traditional security tools and the task of sifting through them to locate anomalies. The ATA attack timeline is a clear, efficient, and convenient feed that surfaces the right things at the right time, giving you the power of perspective on the who, what, when, why, and how. ATA provides visibility like in a social network, you can search for any users, devices or resources and see their behavioral profile.
Try it today
You can start evaluating Microsoft Advanced Threat Analytics today. Please
download
our public preview version and our
deployment guide
and enjoy the ride! You can your questions and feedback in the discussion
forum
and we will respond to you as quickly as possible.
And if you are interested in cybersecurity or hearing about our latest updates and improvements, please follow me on Twitter
@IdanPlotnik
. For questions or feedback you can contact
me
directly, or send your feedback directly to the
group
.
Last but not least, a few words on our special group including engineers, data scientists, security researchers and program managers: we have top notch cybersecurity experts and our goal is to help you protect your organization from security breaches.
Thank you! We are here for you!
Idan Plotnik (Twitter:
@IdanPlotnik
)
Principal Group Manager
Microsoft Identity and Security Service Division
Published Sep 06, 2018
Version 1.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.


