First published on CloudBlogs on Oct, 20 2015
Howdy folks, Today I'm happy to share the news with you that we've released a Public Preview of Azure AD's PowerShell Module with support for Azure MFA. This enables admins to turn on MFA while still getting the efficiency benefits of PowerShell Scripting! In addition, we've added a new set of PowerShell commands that let you manage devices in Azure AD. To give you the low down on these new capabilities, I've asked Shawn Tabrizi, one of PM leading the work in this area to write up a quick blog post. You'll find it below. I hope you'll find these enhancements useful and as always, we'd love to receive any feedback and suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division ------------------------------- Hello everyone, I'm Shawn Tabrizi from the Identity team at Microsoft. Today I'm happy to announce the public preview of modern authentication and device management with the Azure Active Directory PowerShell Module. Modern authentication uses the Active Directory Authentication Library (ADAL) to bring a better sign-in experience for the user, with more advance authentication options like Multi-Factor Authentication (MFA) . Now when managing your Office 365 services or Azure Active Directory Tenant, you can expect the same secure sign-in experience you currently have with your other Office 365 products. In addition to these authentication changes, we have bundled a new set of cmdlets that allow you to manage your devices in AAD , something that was only previously possible through the Graph API. PowerShell and the Graph API are the only supported public interfaces for programmatic access to AAD, and it is great to know that they now both support modern authentication and device management.
Howdy folks, Today I'm happy to share the news with you that we've released a Public Preview of Azure AD's PowerShell Module with support for Azure MFA. This enables admins to turn on MFA while still getting the efficiency benefits of PowerShell Scripting! In addition, we've added a new set of PowerShell commands that let you manage devices in Azure AD. To give you the low down on these new capabilities, I've asked Shawn Tabrizi, one of PM leading the work in this area to write up a quick blog post. You'll find it below. I hope you'll find these enhancements useful and as always, we'd love to receive any feedback and suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division ------------------------------- Hello everyone, I'm Shawn Tabrizi from the Identity team at Microsoft. Today I'm happy to announce the public preview of modern authentication and device management with the Azure Active Directory PowerShell Module. Modern authentication uses the Active Directory Authentication Library (ADAL) to bring a better sign-in experience for the user, with more advance authentication options like Multi-Factor Authentication (MFA) . Now when managing your Office 365 services or Azure Active Directory Tenant, you can expect the same secure sign-in experience you currently have with your other Office 365 products. In addition to these authentication changes, we have bundled a new set of cmdlets that allow you to manage your devices in AAD , something that was only previously possible through the Graph API. PowerShell and the Graph API are the only supported public interfaces for programmatic access to AAD, and it is great to know that they now both support modern authentication and device management.

Modern Authentication
One of our goals for this public preview is to enable administrators who have accounts protected with MFA to authenticate and use AAD PowerShell, while minimizing the number of changes to the existing cmdlets. You should notice no differences when using the new PowerShell module after you have authenticated, but we have made a few changes to the initial Connect-MSOLService cmdlet:- We have added a new parameter: Connect-MSOLService –AccessToken where you can sign in to AAD PowerShell by providing an AAD Access Token that you have acquired elsewhere.
- We have removed the Connect-MSOLService –CurrentCredentials parameter.
Let's try it out!
I own a small company called Contoso, and I am looking to expand and hire a few new employees. Adam is my current user administrator who has MFA enabled for his account.

Connect-MsolService
Adam submits his organizational account credentials, and is prompted to enter a verification code that is sent to him via text message:

Get-MsolUser
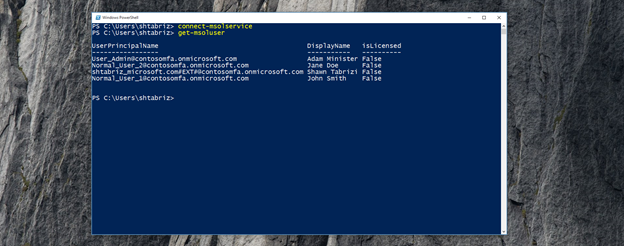
New-MsolUser -UserPrincipalName JWarner@contosomfa.onmicrosoft.com -DisplayName "Jamie Warner" -FirstName "Jamie" -LastName "Warner"

Device Management
Along with the updates to how the Azure Active Directory PowerShell module authenticates, you will also find a new suite of cmdlets that allow you to manage the devices registered in your directory. Previously, if you wanted to manage your AAD registered devices, you had to do so through the Graph API. Now you are able to do this through the AAD PowerShell Module, alongside your other administrative tasks. You will find the following new commands:- Get-MsolDevice
- Enable-MsolDevice
- Disable-MsolDevice
- Remove-MsolDevice
Let's try it out!
Contoso practices the Bring Your Own Device (BYOD) program, where we allow our employees to register their own devices for use at work. One of our employees, Greg, recently lost his laptop that was registered with his account in the directory. We want to make sure that we disable this device until he can find it again. First thing we do is query all the devices that Greg owns:Get-MsolDevice –RegisteredOwnerUpn GMonet@contosomfa.onmicrosoft.com

Disable-MsolDevice –DeviceId a7892334-730b-4d49-bd13-54c2a4928009
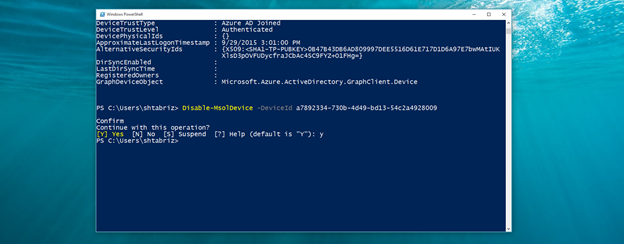

Enable-MsolDevice -DeviceId a7892334-730b-4d49-bd13-54c2a4928009
Which will change the device back to Enabled = True If not, we can remove the device to make sure it does not affect Greg's device quota:Remove-MsolDevice -DeviceId a7892334-730b-4d49-bd13-54c2a4928009

Final Notes
To install the public preview, you will first need to uninstall any previous version of the AAD PowerShell Module. For the purposes of this preview, we are only supplying a 64-bit version of the module, and we are looking for your feedback to understand the demand for a 32-bit build. In addition, we are looking for you to provide any feedback about specific issues you encounter when using the module, or various authentication and device management scenarios we may have missed here. You should reach out to us via email at AADPowerShellPreview@microsoft.com, and if it is about an error please include:- The steps to reproduce the error
-
The log files found here:
- C:Users[youralias]AppDataLocalMicrosoftOffice365Powershell
Updated Jul 27, 2020
Version 2.0Alex_Simons Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for any identity to any resource, anywhere, with comprehensive identity and network access solutions powered by AI.