First published on CloudBlogs on Jun, 23 2016
Howdy, I'm super excited to announce preview of Azure AD Conditional Access policies for Exchange and SharePoint Online is now available. These policies can be used to require multi-factor authentication (MFA) or block access based on network location. We've heard over and over again how critical it is for organizations to apply additional security to Exchange and SharePoint, while not impacting access to other services. Now, as part of the Conditional Access public preview, rules can be applied to Exchange or SharePoint Online. This is a big step forward as we continue to build up the Conditional Access policy framework. As part of this release we are adding support for the following rules to Exchange and SharePoint Online:
Howdy, I'm super excited to announce preview of Azure AD Conditional Access policies for Exchange and SharePoint Online is now available. These policies can be used to require multi-factor authentication (MFA) or block access based on network location. We've heard over and over again how critical it is for organizations to apply additional security to Exchange and SharePoint, while not impacting access to other services. Now, as part of the Conditional Access public preview, rules can be applied to Exchange or SharePoint Online. This is a big step forward as we continue to build up the Conditional Access policy framework. As part of this release we are adding support for the following rules to Exchange and SharePoint Online:
- Always require MFA
- Require MFA when not at work
- Block access when not at work.
Client Apps
Conditional Access policy applies to browser based access to OWA and SharePoint Online (which includes OneDrive) web sites. It also works for desktop and mobile application access when using applications that support modern authentication. Using modern authentication allows the Azure AD sign in page to be shown from the app, either prompting the user for MFA, or explaining why access has been blocked. We've spend a lot of time validating the behavior across client applications and platforms. Here are the applications we've tested so far, that use Exchange and SharePoint: For Windows 10, Windows10 Mobile, Windows 8.1, Windows 7 and Mac- Outlook, Word, Excel and PowerPoint in Office 2016
- Outlook, Word, Excel and PowerPoint in Office 2013 (with modern authentication enabled)
- OneDrive Sync Client (with modern authentication)
- Outlook email app
Getting Started
Let's start by applying an MFA conditional access policy to access Exchange. This will apply to mobile and desktop applications as well OWA in the browser. As a pre-requisite you'll need an Office365 and Azure AD Premium license.- Start by signing into the Azure management portal .
- Under the Active Directory section, select your directory and then select the Applications tab.

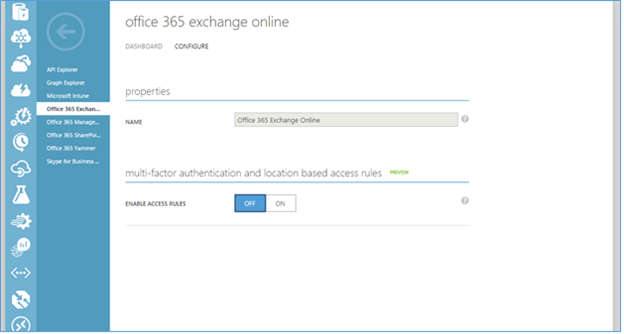
- Select Office 365 Exchange Online. Then select the Configure tab.

- On this tab you can enable 'multi-factor authentication and location based rules' by setting Enable Access Rules to ON.
- Once the rule is enabled you will be shown the rule options. In this example we're going to apply Conditional Access to all users. Instead of selecting all users, you also have the option to identify users based on their security groups.

- The rule selected "Require multi-factor authentication" will require users to have performed MFA before they can access the mailbox. Users will still sign into other sites using web apps, like the Office 365 portal, with just username password.

Once signed in, the user can go to their mail.

At this point the Conditional Access policy we set above, and the user will need to complete MFA before getting access.

Try it out
We're excited to be making this preview available. Please give it a spin and let us know what you think. You can learn more about Conditional Access here . This is a set of capabilities that I know a LOT of you have been asking for. I hope you'll find it useful. And as always, we would love to receive any feedback of suggestions you have. Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity DivisionUpdated Jul 24, 2020
Version 6.0Alex Simons (AZURE) Microsoft
Microsoft
 Microsoft
MicrosoftJoined May 01, 2017
Microsoft Entra Blog
Stay informed on how to secure access for workforce, customer, and workload identities, from anywhere, to multicloud and on-premises resources, with comprehensive identity and network access solutions.