Now that Windows 2003 SP1 is out, I wanted to mention a tool that has shipped as part of Windows 2003 SP1. While the tool itself is not installed by SP1, the shortcut to the Help file is placed on the server desktop when SP1 is installed.
What does that have to do with Exchange? About the tool:
Security Configuration Wizard (SCW) is an attack surface reduction tool that is part of Windows Server 2003 SP1. SCW uses a roles-based metaphor (e.g. "File Server", "Web Server", "Domain Controller", etc.) to determine the desired functionality of a particular type of server, then disables functionality that is not required for the role(s) the server needs to perform. Specifically, SCW:
- Disables unneeded services
- Blocks unused ports
- Allows further (address or security) restrictions for ports that are left open
- Prohibits unnecessary web extensions (if running IIS)
- Reduces Protocol Exposure (SMB, LanMan, LDAP)
- Defines an Audit Policy
SCW guides you through the process of creating, editing, applying, or rolling back a security policy based on the selected roles of the server. The security policies that are created with SCW are XML files that, when applied, configure services, network security, specific registry values, audit policy, and if applicable, Internet Information Services (IIS).
So - really, what does all this have to do with Exchange, you ask?
There is a known issue with Exchange server installed into a non-default path (something other than %ProgramFiles%\Exchsrvr) where SCW is run and application of resultant policy might cause Exchange Server not to be accessible by clients anymore. The possible gotcha is in the "Network Security" portion of SCW which configures the Windows Firewall. This portion of SCW is used to turn on and add exceptions to the Windows Firewall. Exceptions are added by pointing the Windows Firewall to the EXE file to the application that is exempt from firewall blocking. SCW however expects those applications (in our case - services) to be in their default installation paths.
Now, before we start to get nervous, we should understand that the SCW will indicate to the Administrator if it runs into this problem. In other words - the UI will indicate there are issues with services that were "not found", and the Admin will have a chance to correct this before any changes are made to server configuration.
Once you get to the SCW part that configures Network Security, and if you are running SCW on the server that is not installed into the default installation path, you will see this:
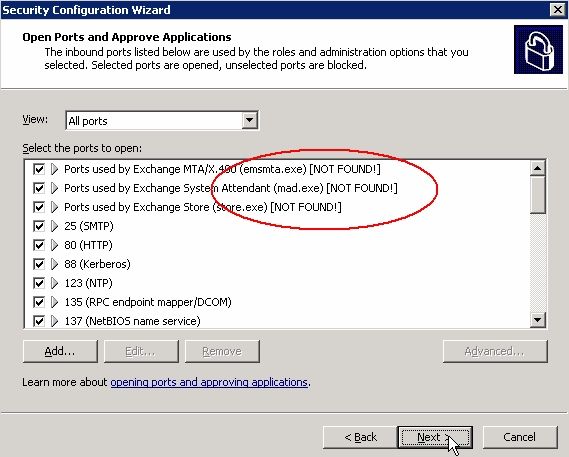
In above example - the MTA Stacks, System Attendant and Store are the services that SCW expects to find in one location, but the actual EXE files are not physically there. If we continued to run SCW here and said YES to the popup that will warn you that some services were not found - after the server reboot, those services would not be accessible by their clients, as Windows Firewall would block their ports.
Please see the following article for information how to configure SCW to point to valid file locations, as well as how to recover if the server is already in the situation where services are blocked by Windows Firewall after SCW policy was applied:
896742 After you run the Security Configuration Wizard in Windows Server 2003
http://support.microsoft.com/?id=896742
There are few extra things I wanted to mention on this:
At the end of the SCW run, you will save the policy under a name you can choose. SCW lets you then take this policy and apply it to other servers in your Organization.
The possible problem here is - if the policy was created on the "default installation path" Exchange server, it will cause problems after import on the "non-default installation path" Exchange server, and vice versa. The above warnings (and a chance to correct them before policy application) are seen only during the policy creation not during the policy import.
Additionally - assuming that Windows Firewall was activated on the server and exceptions were added to the firewall policy, if administrator then adds a component or a service to the server (for example, POP3, IMAP4 or SRS are enabled) - the service will effectively be blocked from it's clients until the SCW is re-run, the added service is approved through it and policy is reapplied. Alternatively, you can manually add the service into exceptions of Windows Firewall.
I personally love the tool, but - we just have to be careful when using it!