EDIT: this post was edited on 9/25/2007 to clarify information related to the hotfix mentioned in KB 937031. Thanks to Vanitha for the edit!
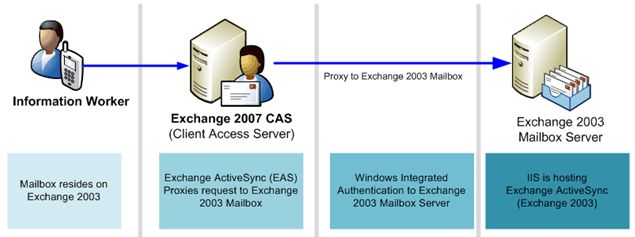
As we mention in Exchange 2007 documentation, the first server role that should be upgraded when migrating to Exchange Server 2007 is the Client Access Server or CAS role.
In order for your users to continue to synchronize their mobile devices via Exchange ActiveSync with their mailboxes hosted on Exchange 2003 mailbox servers, you will need to ensure that Integrated Windows Authentication is enabled on all of the Exchange ActiveSync virtual directories (Microsoft-Server-ActiveSync) on Exchange 2003 mailbox servers.
The following illustrates the process of how an ActiveSync user whose mailbox resides on an Exchange 2003 server gets to their mailbox through an Exchange 2007 CAS:
Steps to Enable Integrated Windows Authentication
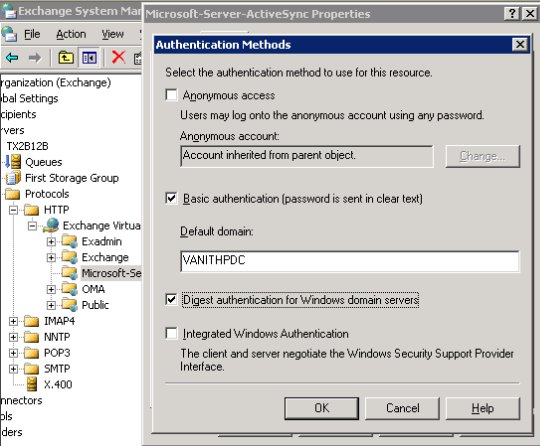
Previously this authentication change had to be done using Internet Services Manager (ISM) because the authentication settings were grayed out in Exchange System Manager. However when the changes were made through ISM, the DS2MB process overwrote the settings in certain scenarios. A hotfix 937031 is now available to enable Integrated Windows Authentication using Exchange System Manager.
Steps to Enable Integrated Windows Authentication after installing hotfix 937031
1. Start Exchange System Manager, and then browse to the following location:
Server_name\Protocols\HTTP\Exchange Virtual server\Microsoft-Server-Activesync
2. Right-click Microsoft-Server-Activesync and then click Properties.
3. Click the Access tab, and then click Authentication.
4. Check Integrated Windows Authentication
You have already installed your CAS; how can you check if you have this problem?
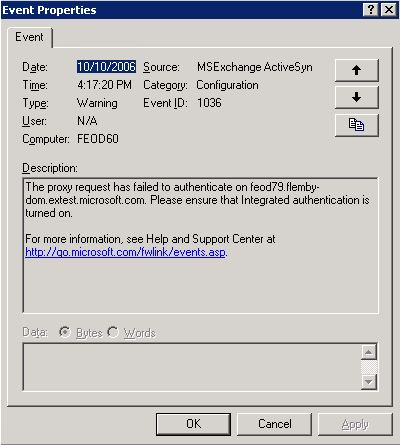
On your Exchange 2007 CAS server, there are two indicators of the problem with proxying to Exchange 2003 servers due to authentication settings:
1. The application log of the CAS server will show event 1036 which will look as follows:
2. The IIS log on the CAS server will show the following:
2006-10-10 23:17:30 W3SVC1 10.197.93.214 OPTIONS /Microsoft-Server-ActiveSync User=e2k3user&DeviceId=6F24CAD599A5BF1A690246B8C68FAE8D&DeviceType=PocketPC&Log=PrxTo:feod79.flemby-dom.extest.microsoft.com_Error:NTLM+not+on+the+destination+CAS_ 80 flemby-dom\e2k3user 157.56.217.199 MSFT-PPC/5.1.2000 401 5 0