With Exchange 2013, we released a new data loss prevention (DLP)capability based on deep content analysis that helps you identify, monitor, and protect sensitive information. We’re continually looking to expand our DLP capabilities, and today we’re bringing two new ones to you—Document Fingerprinting and Policy Tips in Outlook Web App (OWA). Both are being rolled out for Office 365 users right now, and they’ll be part of the Exchange Server 2013 SP1 release for our on-premises users (please stay tuned for more information on SP1).
Watch this short video that explains what DLP has to offer today and how the new capabilities can help your organization be more compliant.
Let’s look at these two new capabilities in more detail.
Document Fingerprinting
Document Fingerprinting enables you to match documents that are derived from the same template. This can be useful for organizations that frequently use standard forms or templates, for example:
- A hospital that has an insurance form that patients fill in, each with a different insurance provider.
- A tax processing office that uses several standard tax forms that it applies to a wide range of situations.
- A law firm that uses a standard template to drafts patent applications that it files on behalf of its clients.
To understand how this works, let’s take a look at a scenario.
Contoso Pharma is a pharmaceutical company with a research division. Employees in the research division collaborate with their peers across the company to create new products and services, and file patents to protect their intellectual property. The law firm used by the company for patent filing uses a standard template for patent applications.
Say you’re an administrator at Contoso Pharma. You can use Document Fingerprinting to define a customized sensitive information type called “Patents.” To do so, you use the new administrative interface in the Exchange Admin Center (EAC) to create a new document fingerprint. Select the file you want to fingerprint, and then select the standard template that employees use for that file, in this case, patent applications.
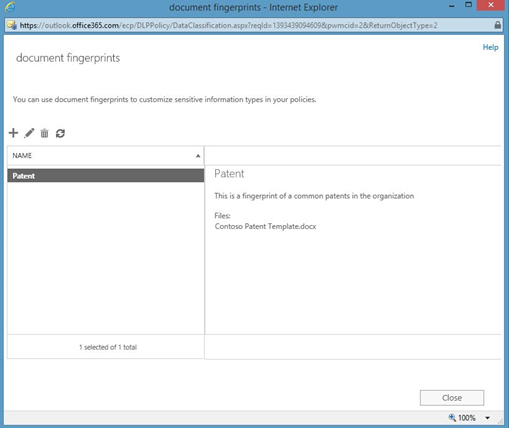
You create document fingerprints in the EAC by selecting the file and then the sensitive information type.
This creates a template of that kind of document, which is used to detect other documents that are derived from the template.
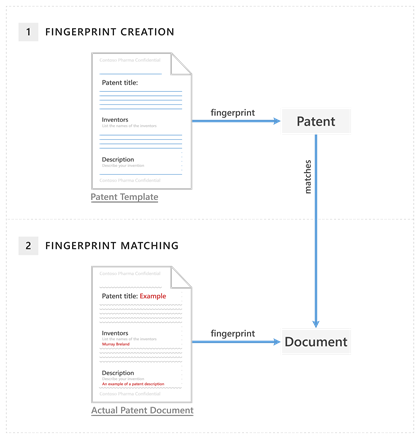
When you fingerprint a document, a template of that kind of document is created (1) that is then used to detect documents (2) created with it.
Continuing with our Contoso Pharma scenario, once the patent template is fingerprinted, you (as an administrator) can use the existing Exchange Transport Rules and DLP infrastructure to create a rule to detect email with sensitive information of type “Patents” and define any of the supported actions in DLP. For example, you could block emails with patent documents attached from being sent externally. If Contoso Pharma uses an outside counsel for filing patents, you can allow users to send the email with an override option from Policy Tips! (See the introduction to Policy Tips in OWA section below.)
Although the scenario above refers to patents, you can easily imagine document fingerprinting being used to detect sensitive information in many other circumstances, like a hospital fingerprinting custom forms that contain personal health information, or a tax processing agency fingerprinting the 1040 EZ or W2 forms in the U.S.A.
Document fingerprinting is just one method organizations can use to detect sensitive content. Here’s a quick guide to the different methods of detecting sensitive content and the uses of each:
- Detection of standardized entities supported by Microsoft out of the box. If you want to detect standard entities like credit cards, debit cards, and so on, check if this kind of detection is supported in the out-of-the-box list provided by Microsoft and, if it is, use it. You can customize this method of detection; learn how in this TechNet topic.
- Developing Sensitive Information rule packages. If you need to detect entities that are specific to your organization (for example, an insurance number or an employee number), you can develop custom rules based on a combination of regular expressions and keywords. For details, see this TechNet topic.
- Document Fingerprinting. If you have an established business practice in which you use standard forms or templates (for example, patent filings, health insurance forms, tax forms, and so on), you can use document fingerprinting to detect the completed forms. For details, see the Document Fingerprinting topic on TechNet.
Policy Tips in OWA
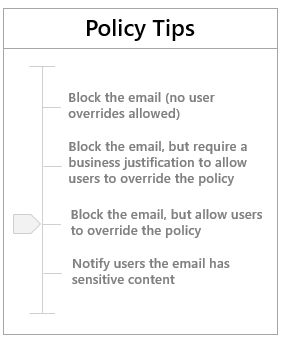
Policy tips are designed to notify users in your organization when they are sending sensitive information over email. Policy Tips are similar to MailTips, and you can use them in Outlook in several different ways to help your users avoid sending sensitive information in email. For example, you can use Policy Tips to:
- Inform your users of the presence of sensitive information and block the email from being sent.
- Educate your users through a Notify Policy Tip when sensitive content is present in their emails.
- Empower your users to make case by case decisions by allowing them to override the sensitive information policy—with the option of including a business justification for the override.
With this new release in the Office 365 service and Exchange Server 201 3 SP1, all the rich capabilities of Policy Tips previously available in Outlook 2013 will now also be available across the OWA interfaces.
As an administrator, you have the flexibility to set these different ways of using policy tips based on your business requirements. For example, you could set up a policy to only send a notification if an email contains one or two social security numbers, but block the mail from being sent and require a business justification if an email has a spreadsheet attached that contains more than 50 social security numbers.
DLP Policy Tips in OWA and OWA for Devices
As of Exchange 2013 SP1, OWA and OWA for Devices will both have Policy Tips support. The experience is in line with the experience in Outlook 2013, where users see a Policy Tip based on the DLP rules set by their administrator. If you already have a DLP policy with Policy Tips turned on, they will automatically apply in OWA. That means administrators do not need to create new configurations or turn switches on for this feature to work in OWA.
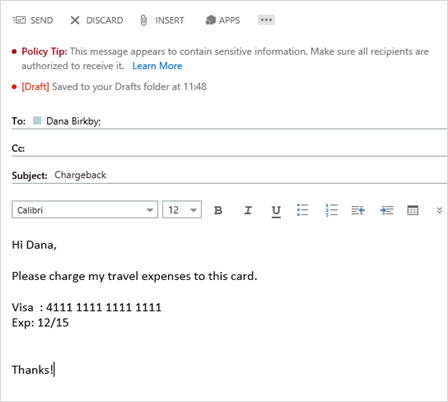
When you include sensitive information in an email message, a DLP Policy Tip notifies you before you send the message.
Policy Tips in OWA also show the user what sensitive content was detected in an email; in Outlook, it also allows the user to report back to the administrator if they think the email content is not sensitive. This empowers users that are closest to the data to provide feedback on the efficacy of detecting sensitive content.
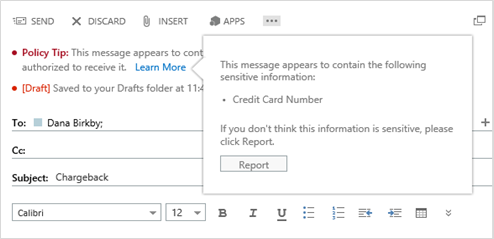
A callout displays the sensitive content that was detected in the email and allows the user to report a mistake in the detection.
Administrators can also block emails that contain a large number of sensitive content (for example, an Excel attachment with more than 50 credit card numbers). Just as in Outlook 2013, the attachment with the sensitive content is highlighted so the user can easily identify it. Depending on the organization’s policy, users can be empowered to override the policy—with the option of requiring them to include a business justification—and send the email.
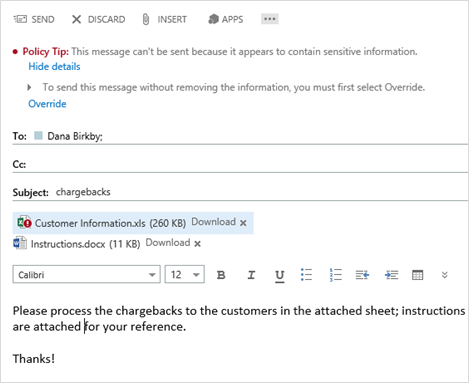
Policy Tips can be set up to block users from sending a large amount of sensitive content; attachments with sensitive content are highlighted for the user.
These experiences are also replicated on all mobile devices, from Windows Phone to iOS and Android devices.
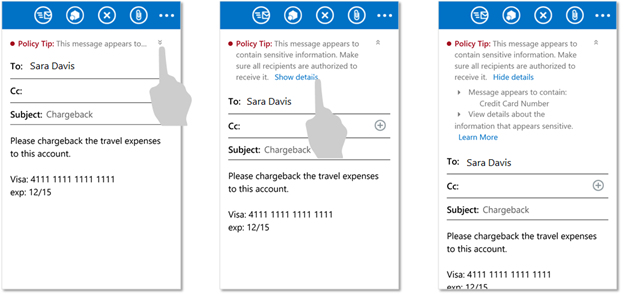
Policy Tips can be set up on the Mobile devices to educate users
Different kinds of Policy Tips can be triggered based on conditions, like the amount of sensitive data in an email. No new configuration is required to do this, if DLP in Outlook has already been enabled.
Shared configuration
Policy Tips in Outlook 2013 are turned on when an administrator creates a rule with a action to notify the end user with a policy tip, or configures a DLP policy with such a rule. In Exchange 2013 these rules are applied on both the server and the client (that is, Outlook 2013). These same rules now get applied in exactly the same manner in OWA as well. This means that Exchange, Outlook, and OWA all share these configurations:
- Exchange Transport Rules. When you configure a transport rule to look for sensitive content in an email, and take Policy Tip-based acti ons on them, they are uniformly applied in Outlook and OWA. This includes the predicates likes detecting sender group membership, and other properties of recipients as well. Specifically, the NotifySender action in Exchange Transport Rules triggers Policy Tips for both Outlook and OWA.

Different kinds of Policy Tips options can be triggered based on conditions, such as the one above where we notify the user about sensitive information but allow them to send the message.
- Definitions of sensitive content. When you configure a transport rule to look for any of the out-of-the-box sensitive content or any custom sensitive types, they are evaluated in exactly the same manner in all three places, Exchange, Outlook, and OWA. Specifically, the MessageContainsDataClassifications predicate in Exchange Transport Rules defines the sensitive content for both Outlook and OWA.
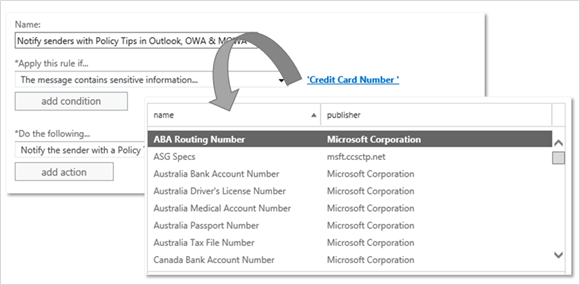
You can defining sensitive content for Outlook and OWA when you configure a transport rule.
- Policy Tip configurations. When you edit the Policy Tip configurations to customize the text displayed in a Policy Tip, or the Compliance URL, they are updated in Outlook 2013, OWA, and OWA for Devices.
Custom Policy Tip configurations, like compliance URLs or customized notification texts, are applied uniformly in Outlook, OWA, and OWA for Devices.
DLP planning and implementation are crucial for most organizations, because they impact the organization as a whole and all the users who work with sensitive data. Protecting sensitive information without decreasing users’ productivity is a key principle of DLP in Office 365, and Policy Tips and Document Fingerprinting can help you do just that. We hope adding these capabilities to our DLP arsenal will help make DLP management easier for your users. Stay tuned for more news about our work in compliance.
Shobhit Sahay