1 Access management
Azure Kubernetes Service (AKS) supports Microsoft Entra ID integration, which allows you to control access to your cluster resources using Azure role-based access control (RBAC). In this tutorial, you will learn how to integrate AKS with Microsoft Entra ID and assign different roles and permissions to three types of users: An admin user, who will have full access to the AKS cluster and its resources. A backend ops team, who will be responsible for managing the backend application deployed in the AKS cluster. They will only have access to the backend namespace and the resources within it. A frontend ops team, who will be responsible for managing the frontend application deployed in the AKS cluster. They will only have access to the frontend namespace and the resources within it. By following this tutorial, you will be able to implement the least privilege access model, which means that each user or group will only have the minimum permissions required to perform their tasks.
1.1 Introduction
In this third part of the blog series, you will learn how to:
- Harden your AKS cluster. - Update an existing AKS cluster to support Microsoft Entra ID integration enabled.
- Create a Microsoft Entra ID admin group and assign it the Azure Kubernetes Service Cluster Admin Role.
- Create a Microsoft Entra ID backend ops group and assign it the Azure Kubernetes Service Cluster User Role.
- Create a Microsoft Entra ID frontend ops group and assign it the Azure Kubernetes Service Cluster User Role.
- Create Users in Microsoft Entra ID
- Create role bindings to grant access to the backend ops group and the frontend ops group to their respective namespaces.
- Test the access of each user type by logging in with different credentials and running kubectl commands.
1.2 Prequisities:
This section outlines the recommended prerequisites for setting up Microsoft entra ID with AKS. Highly recommended to complete Azure Kubernetes Service Baseline - The Hard Way here!
or follow the Microsoft official documentation for a quick start here! Note that you will need to create 2 namespaces in kubernetes one called frontend and the second one called backend.
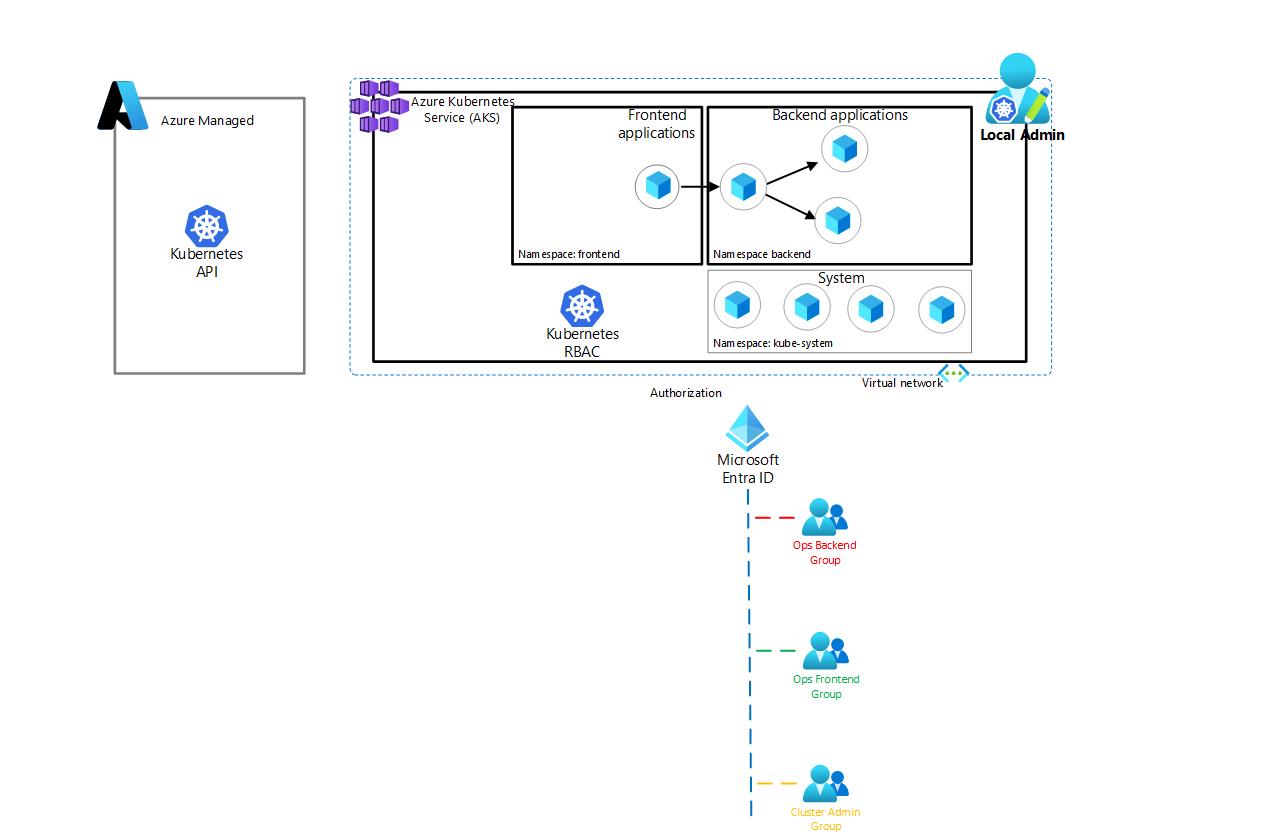
1.3 Target Architecture
Throughout this article, this is the target architecture we will aim to create: all procedures will be conducted by using Azure CLI. 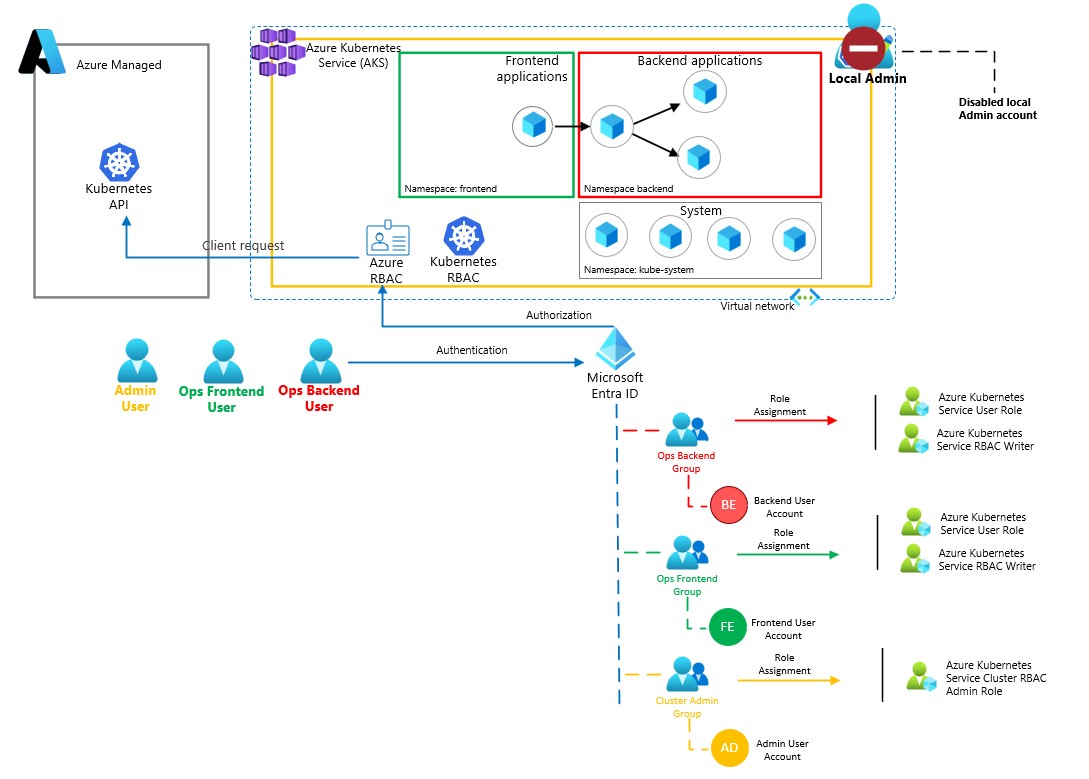 The current architecture can be visualized as followed:
The current architecture can be visualized as followed: 
1.4 Deployment
1.4.1 Prepare Environment Variables
This code defines the environment variables for the resources that you will create later in the tutorial.
Note: Ensure environment variable $STUDENT_NAME and placeholder <TENANT SUB DOMAIN NAME>is set before adding the code below.
# Define the name of the admin group
ADMIN_GROUP='ClusterAdminGroup-'${STUDENT_NAME}
# Define the name of the frontend operations group
OPS_FE_GROUP='Ops_Fronted_team-'${STUDENT_NAME}
# Define the name of the backend operations group
OPS_BE_GROUP='Ops_Backend_team-'${STUDENT_NAME}
# Define the Azure AD UPN (User Principal Name) for the frontend operations user
AAD_OPS_FE_UPN='opsfe-'${STUDENT_NAME}'@<SUB DOMAIN TENANT NAME HERE>.onmicrosoft.com'
# Define the display name for the frontend operations user
AAD_OPS_FE_DISPLAY_NAME='Frontend-'${STUDENT_NAME}
# Placeholder for the frontend operations user password
AAD_OPS_FE_PW=<ENTER USER PASSWORD>
# Define the Azure AD UPN for the backend operations user
AAD_OPS_BE_UPN='opsbe-'${STUDENT_NAME}'@<SUB DOMAIN TENANT NAME HERE>.onmicrosoft.com'
# Define the display name for the backend operations user
AAD_OPS_BE_DISPLAY_NAME='Backend-'${STUDENT_NAME}
# Placeholder for the backend operations user password
AAD_OPS_BE_PW=<ENTER USER PASSWORD>
# Define the Azure AD UPN for the cluster admin user
AAD_ADMIN_UPN='clusteradmin'${STUDENT_NAME}'@<SUB DOMAIN TENANT NAME HERE>.onmicrosoft.com'
# Placeholder for the cluster admin user password
AAD_ADMIN_PW=<ENTER USER PASSWORD>
# Define the display name for the cluster admin user
AAD_ADMIN_DISPLAY_NAME='Admin-'${STUDENT_NAME}
1.4.2 Create Microsoft Entra ID Security Groups
We will now start by creating 3 security groups for respective team.
- Create the security group for Cluster Admins
az ad group create --display-name $ADMIN_GROUP --mail-nickname $ADMIN_GROUP
2. Create the security group for Application Operations Frontend Team
az ad group create --display-name $OPS_FE_GROUP --mail-nickname $OPS_FE_GROUP
3. Create the security group for Application Operations Backend Team
az ad group create --display-name $OPS_BE_GROUP --mail-nickname $OPS_BE_GROUP
Current architecture can now be illustrated as follows:
1.4.3 Integrate AKS with Microsoft Entra ID
1. Lets update our existing AKS cluster to support Microsoft Entra ID integration, and configure a cluster admin group, and disable local admin accounts in AKS, as this will prevent anyone from using the --admin switch to get full cluster credentials.
az aks update -g $SPOKE_RG -n $AKS_CLUSTER_NAME-${STUDENT_NAME} --enable-azure-rbac --enable-aad --disable-local-accounts
Current architecture can now be described as follows:
 1.4.4 Scope and Role Assignment for Security Groups
1.4.4 Scope and Role Assignment for Security Groups
This chapter describes how to create the scope for the operation teams to perform their daily tasks. The scope is based on the AKS resource ID and a fixed path in AKS, which is /namespaces/. The scope will assign the Application Operations Frontend Team to the frontend namespace and the Application Operation Backend Team to the backend namespace.
- Lets start by constructing the scope for the operations team.
AKS_BACKEND_NAMESPACE='/namespaces/backend'
AKS_FRONTEND_NAMESPACE='/namespaces/frontend'
AKS_RESOURCE_ID=$(az aks show -g $SPOKE_RG -n $AKS_CLUSTER_NAME-${STUDENT_NAME} --query 'id' --output tsv)
2. Lets fetch the Object ID of the operations teams and admin security groups. Application Operation Frontend Team.
FE_GROUP_OBJECT_ID=$(az ad group show --group $OPS_FE_GROUP --query 'id' --output tsv)
Application Operation Backend Team.
BE_GROUP_OBJECT_ID=$(az ad group show --group $OPS_BE_GROUP --query 'id' --output tsv
Admin.
ADMIN_GROUP_OBJECT_ID=$(az ad group show --group $ADMIN_GROUP --query 'id' --output tsv)
3) This commands will grant the Application Operations Frontend Team group users the permissions to download the credential for AKS, and only operate within given namespace.
az role assignment create --assignee $FE_GROUP_OBJECT_ID --role "Azure Kubernetes Service RBAC Writer" --scope ${AKS_RESOURCE_ID}${AKS_FRONTEND_NAMESPACE} az role assignment create --assignee $FE_GROUP_OBJECT_ID --role "Azure Kubernetes Service Cluster User Role" --scope ${AKS_RESOURCE_ID}4) This commands will grant the Application Operations Backend Team group users the permissions to download the credential for AKS, and only operate within given namespace.
az role assignment create --assignee $BE_GROUP_OBJECT_ID --role "Azure Kubernetes Service RBAC Writer" --scope ${AKS_RESOURCE_ID}${AKS_BACKEND_NAMESPACE} az role assignment create --assignee $BE_GROUP_OBJECT_ID --role "Azure Kubernetes Service Cluster User Role" --scope ${AKS_RESOURCE_ID}
5) This command will grant the Admin group users the permissions to connect to and manage all aspects of the AKS cluster.
az role assignment create --assignee $ADMIN_GROUP_OBJECT_ID --role "Azure Kubernetes Service RBAC Cluster Admin" --scope ${AKS_RESOURCE_ID} Current architecture can now be described as follows: 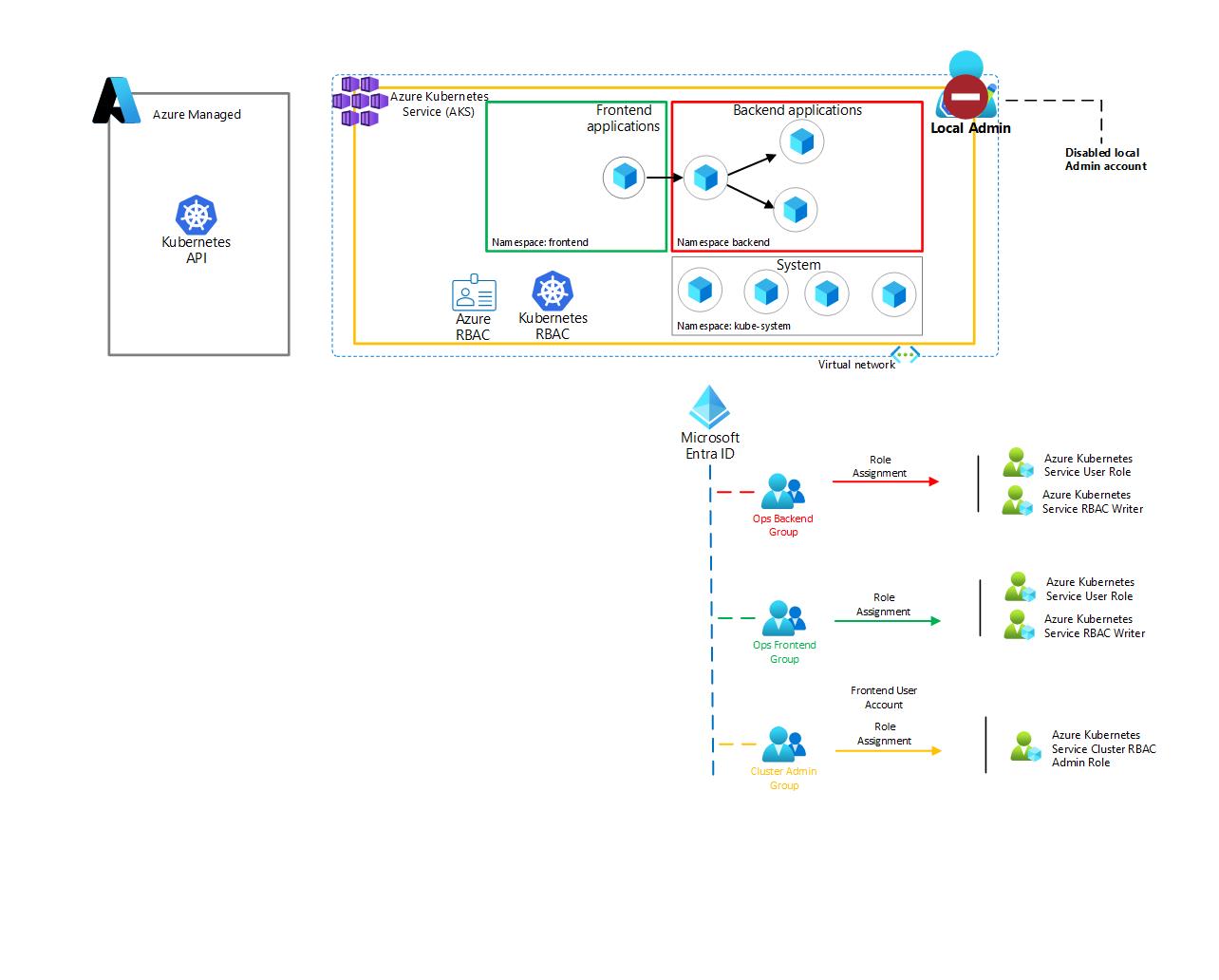 1.4.5 Create Users and Assign them to Security Groups.
1.4.5 Create Users and Assign them to Security Groups.
This exercise will guide you through the steps of creating three users and adding them to their corresponding security groups.
- Create the Admin user.
az ad user create --display-name $AAD_ADMIN_DISPLAY_NAME --user-principal-name $AAD_ADMIN_UPN --password $AAD_ADMIN_PW
2. Assign the admin user to admin group for the AKS cluster. First identify the object id of the user as we will need this number to assign the user to the admin group.
ADMIN_USER_OBJECT_ID=$(az ad user show --id $AAD_ADMIN_UPN --query 'id' --output tsv)
3. Assign the user to the admin security group.
az ad group member add --group $ADMIN_GROUP --member-id $ADMIN_USER_OBJECT_ID4. Create the frontend operations user.
az ad user create --display-name $AAD_OPS_FE_DISPLAY_NAME --user-principal-name $AAD_OPS_FE_UPN --password $AAD_OPS_FE_PW5. Assign the frontend operations user to frontend security group for the AKS cluster. First identify the object id of the user as we will need this number to assign the user to the frontend security group.
FE_USER_OBJECT_ID=$(az ad user show --id $AAD_OPS_FE_UPN --query 'id' --output tsv)
6. Assign the user to the frontend security group.
az ad group member add --group $OPS_FE_GROUP --member-id $FE_USER_OBJECT_ID
7. Create the backend operations user.
az ad user create --display-name $AAD_OPS_BE_DISPLAY_NAME --user-principal-name $AAD_OPS_BE_UPN --password $AAD_OPS_BE_PW
8. Assign the backend operations user to backend security group for the AKS cluster. First identify the object id of the user as we will need this number to assign the user to the backend security group.
BE_USER_OBJECT_ID=$(az ad user show --id $AAD_OPS_BE_UPN --query 'id' --output tsv)
9. Assign the user to the backend security group.
az ad group member add --group $OPS_BE_GROUP --member-id $BE_USER_OBJECT_IDCurrent architecture can now be described as follows: 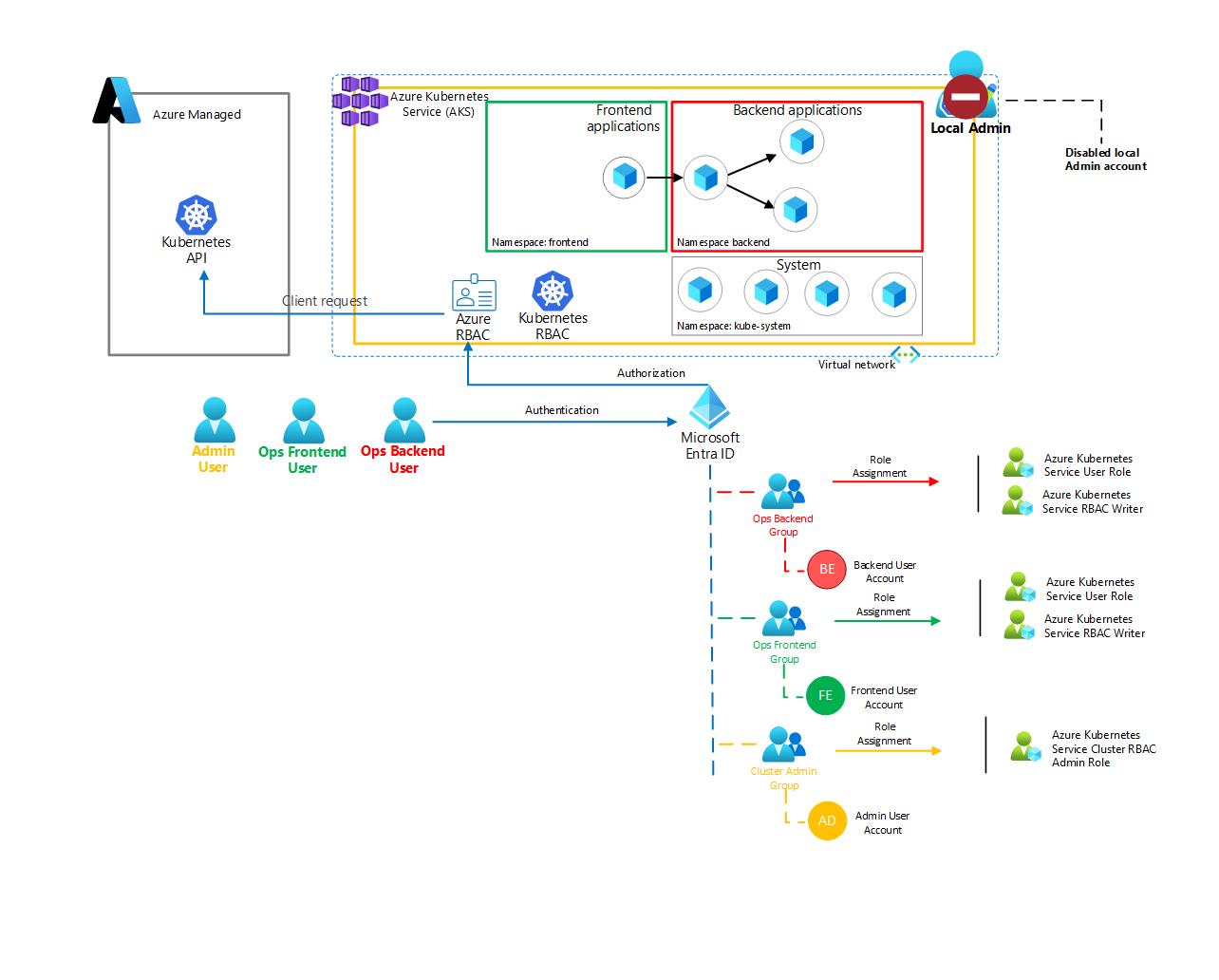
1.4.6 Validate your deployment in the Azure portal.
- Navigate to the Azure portal at https://portal.azure.com and enter your login credentials.
- Once logged in, on your top left hand side, click on the portal menu (three strips).
- From the menu list click on Microsoft Entra ID.
- On your left hand side menu under Manage click on Users.
- Validate that your users are created, there shall be three users, each user name shall end with your student name.
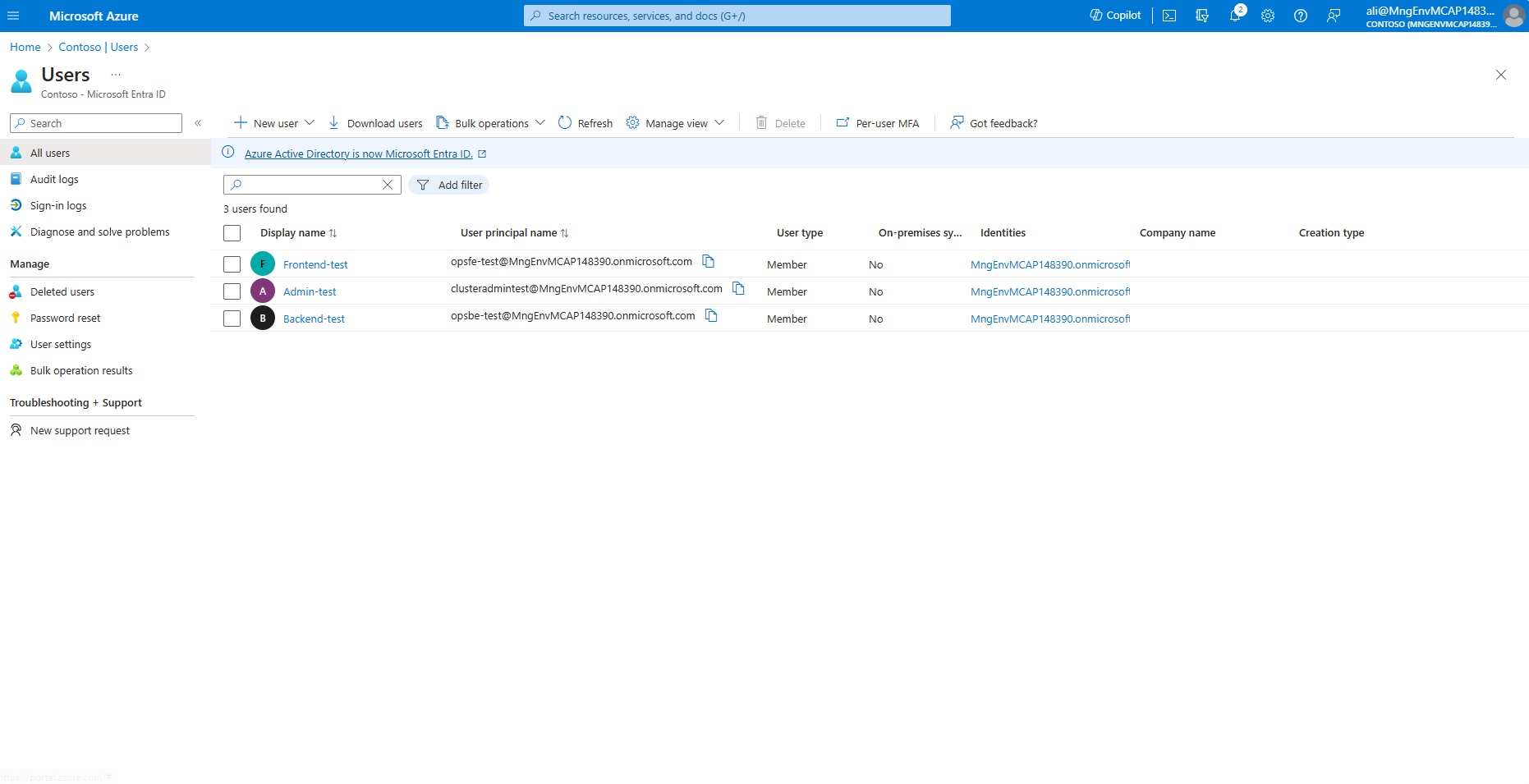
- On the top menu bar click on the Users link.
- On your left hand side menu under Manage click on Groups. Ensure you have three groups as depicted in the picture, the group names should end with your student name.
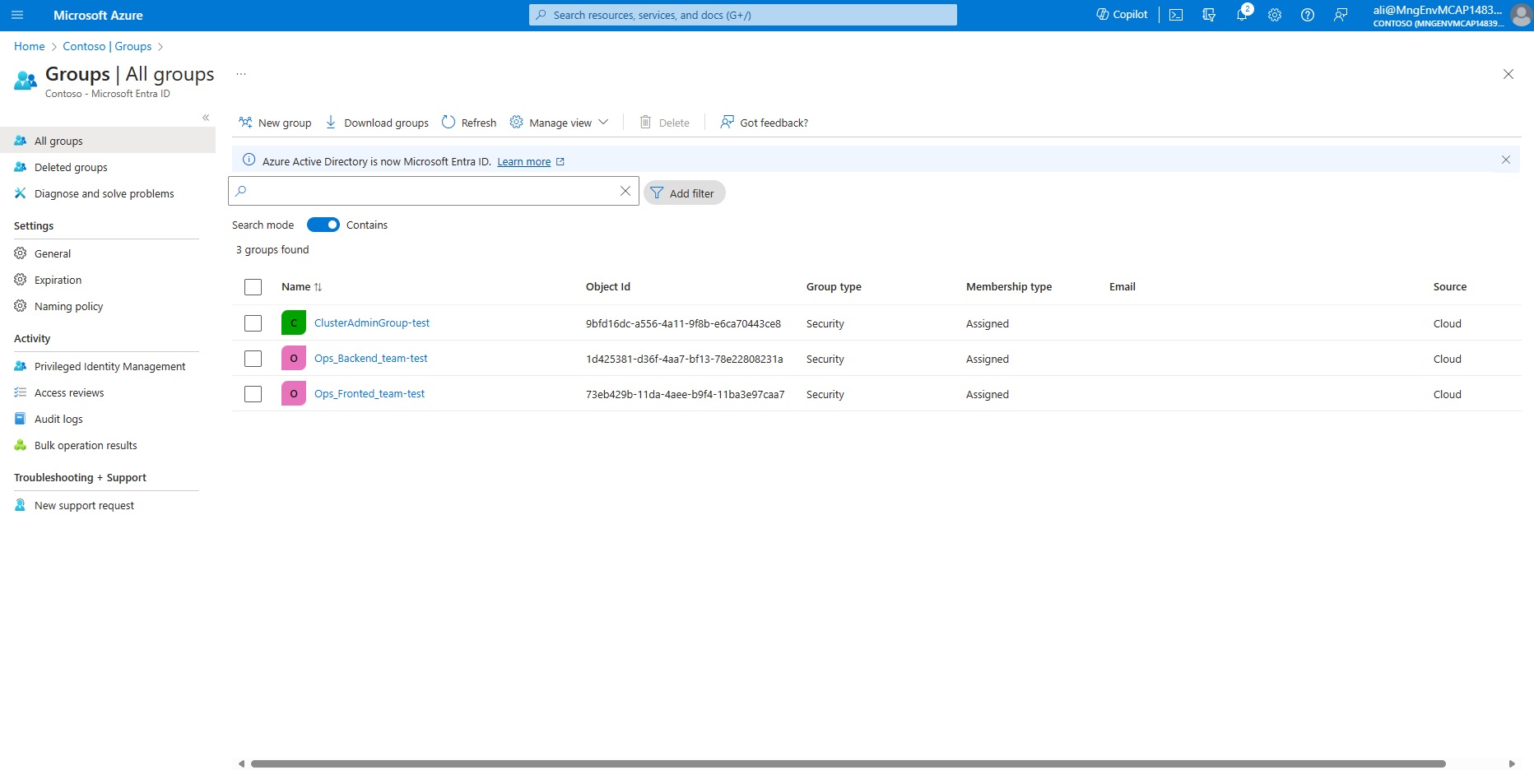
- Click on security group called Ops_Backend_team-YOUR STUDENT NAME.
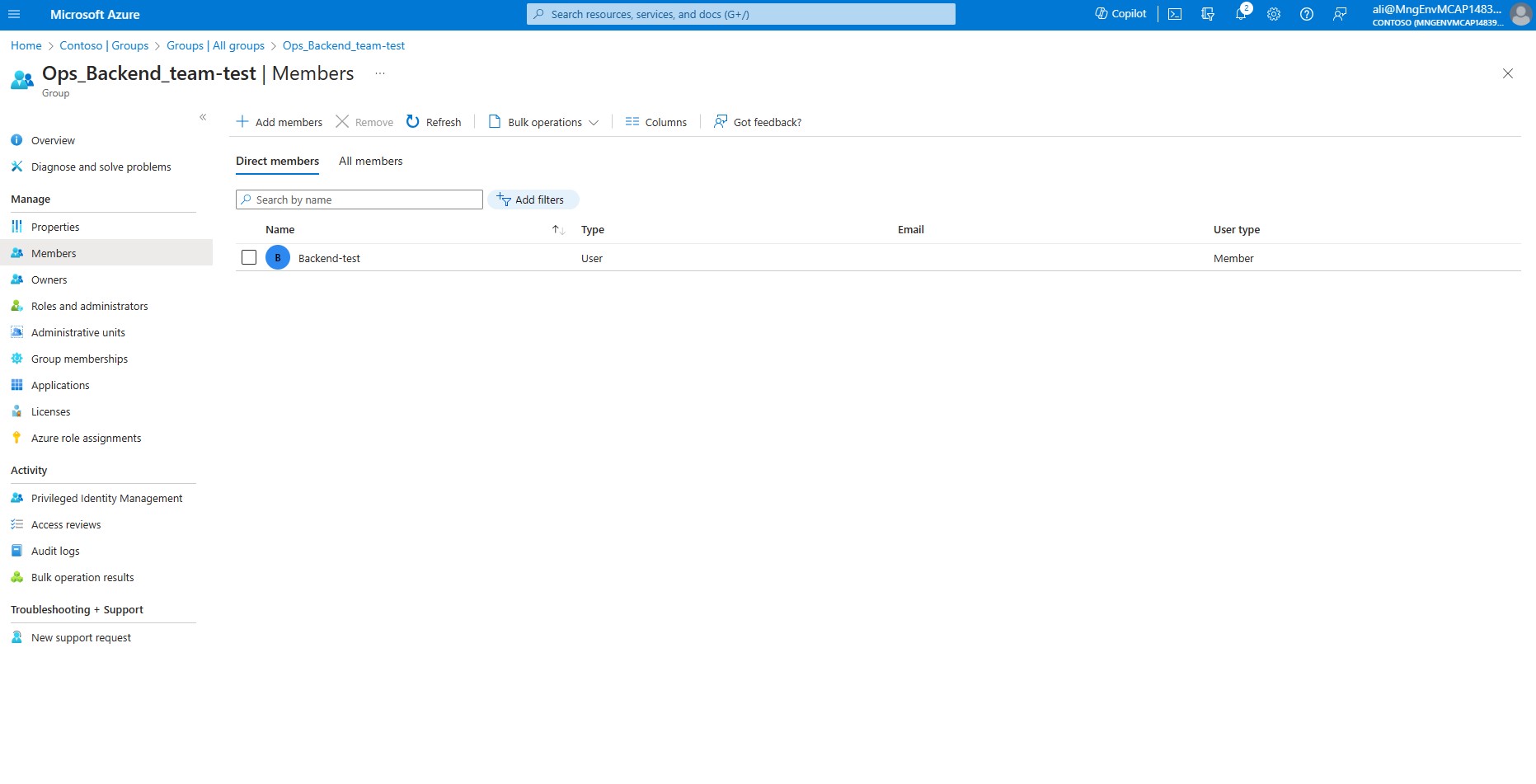
- On your left hand side menu click on Members, verify that your user Backend-YOUR STUDENT NAME is assigned.
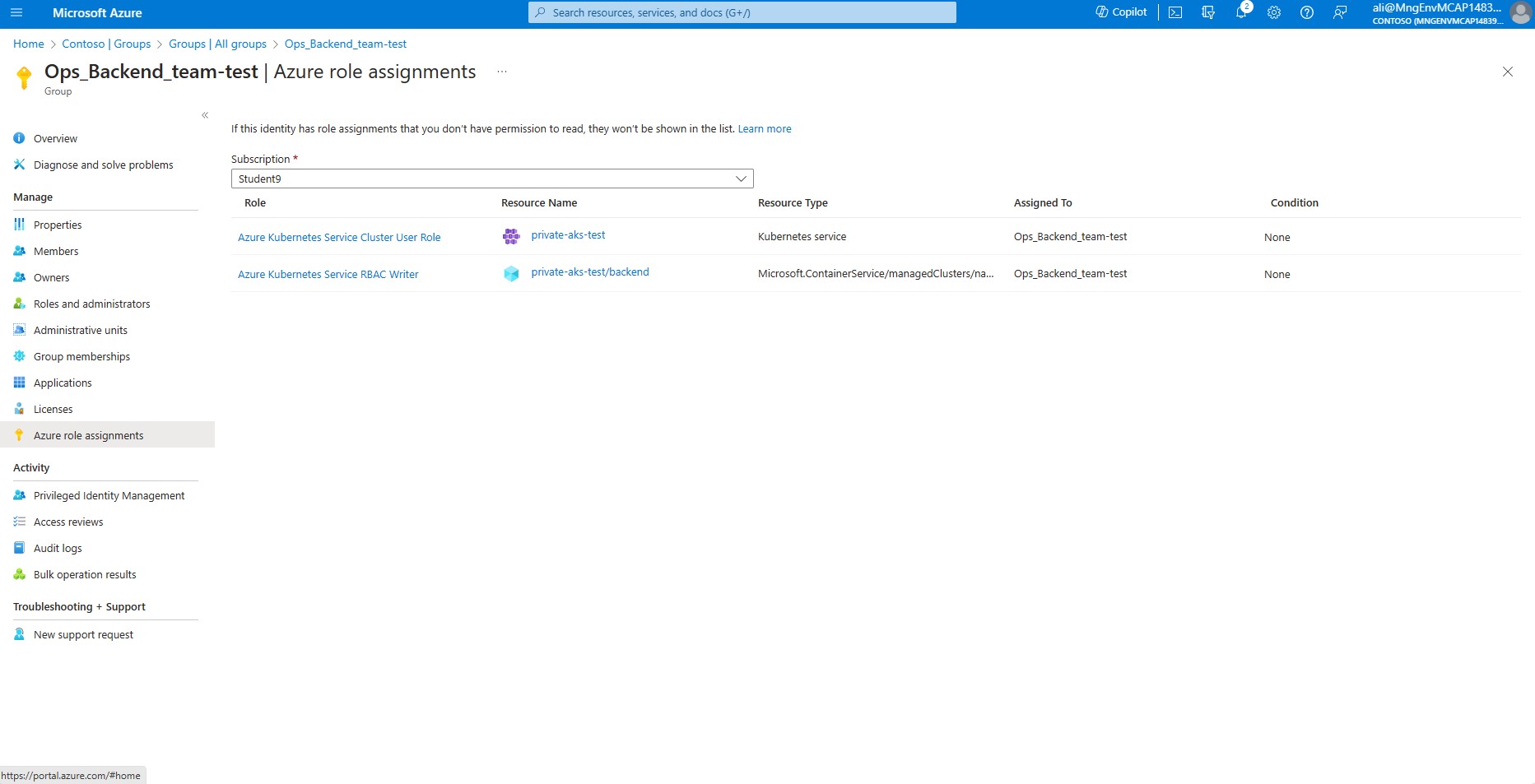
- On your left hand side menu click on Azure role Assignments, from the drop down menu select your subscription. Ensure the following roles are assigned to the group: Azure Kubernetes service Cluster User Role assigned on the Cluster level and Azure Kubernetes Service RBAC Writer assigned on the namespace level called backend.
 11.On the top menu bar click on Groups link. Repeat step 7 - 11 for Ops_Frontend_team-YOUR STUDENT NAME and ClusterAdminGroup-YOUR STUDENT NAME
11.On the top menu bar click on Groups link. Repeat step 7 - 11 for Ops_Frontend_team-YOUR STUDENT NAME and ClusterAdminGroup-YOUR STUDENT NAME
1.4.7 Validate the Access for the Different Users.
This section will demonstrate how to connect to the AKS cluster from the jumpbox using the user account defined in Microsoft Entra ID.
Note: If you deployed your AKS cluster using the quick start method
We will check two things: first, that we can successfully connect to the cluster; and second, that the Operations teams have access only to their own namespaces, while the Admin has full access to the cluster.
- Navigate to the Azure portal at https://portal.azure.com and enter your login credentials.
- Once logged in, locate and select your rg-hub where the Jumpbox has been deployed.
- Within your resource group, find and click on the Jumpbox VM.
- In the left-hand side menu, under the Operations section, select Bastion.
- Enter the credentials for the Jumpbox VM and verify that you can log in successfully.
- First remove the existing stored configuration that you have previously downloaded with Azure CLI and kubectl. From the Jumpbox VM execute the following commands:
rm -R .azure/
rm -R .kube/
Note: The .azure and .kube directories store configuration files for Azure and Kubernetes, respectively, for your user account. Removing these files triggers a login prompt, allowing you to re-authenticate with different credentials.
7. Retrieve the username and password for Frontend user.
Important: Retrieve the username and password from your local shell, and not the shell from Jumpbox VM.
echo $AAD_OPS_FE_UPN echo $AAD_OPS_FE_PW8. From the Jumpbox VM initiate the authentication process.
az login
Example output:
bash azureuser@Jumpbox-VM:~$ az login To sign in, use a web browser to open the page https://microsoft.com/devicelogin and enter the code XXXXXXX to authenticate.
9. Open a new tab in your web browser and access https://microsoft.com/devicelogin. Enter the generated code, and press Next
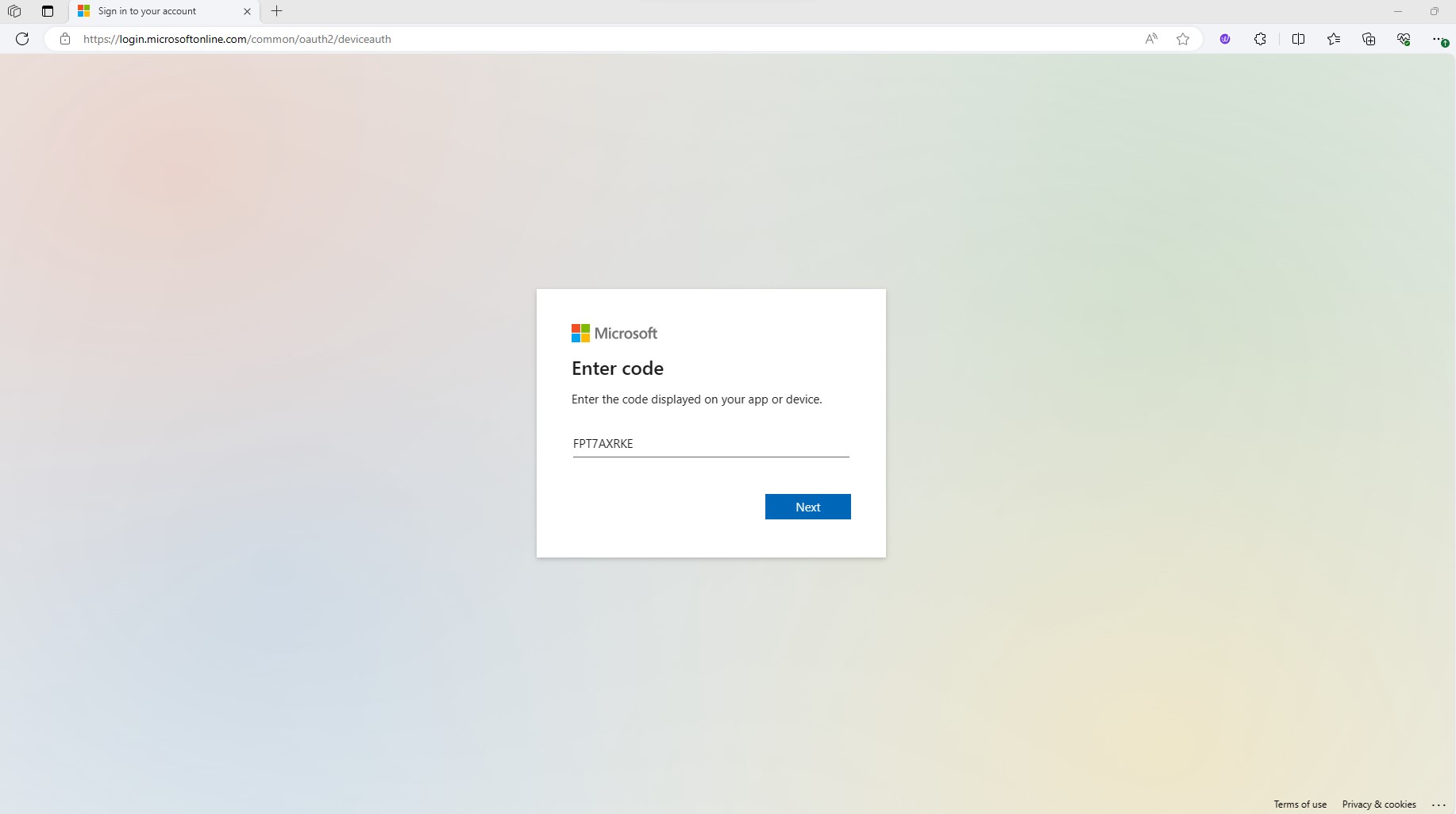
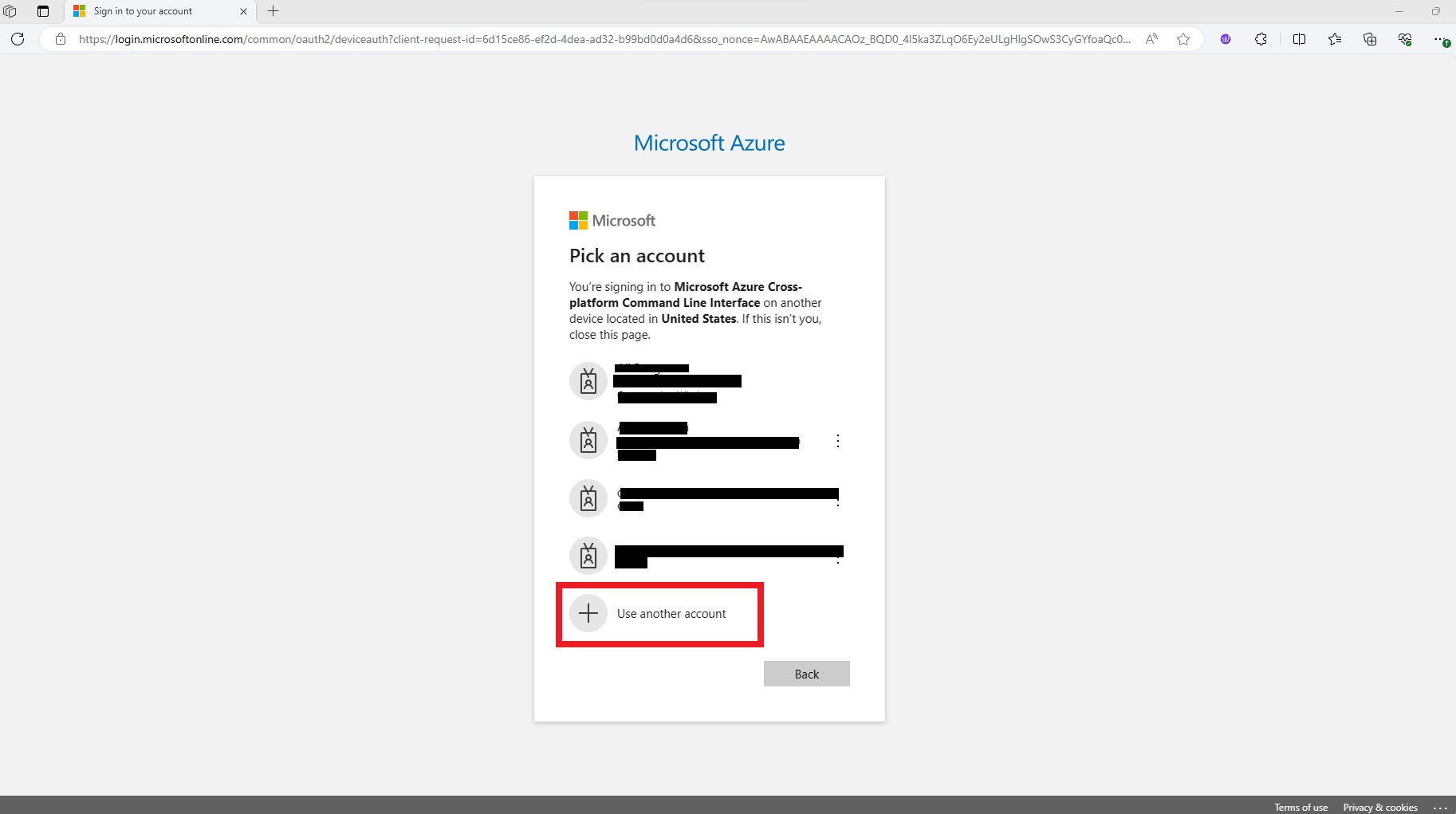
10. You will be prompted with an authentication window asking which user you want to login with select Use another account and supply the username in the AAD_OPS_FE_UPN variable and password from variable AAD_OPS_FE_PW and then press Next.
Note: When you authenticate with a user for the first time, you will be prompted by Microsoft Authenticator to set up Multi-Factor Authentication (MFA). Choose "I want to setup a different method" option from the drop-down menu, and select Phone, supply your phone number, and receive a one-time passcode to authenticate to Azure with your user account.
11. From the Jumpbox VM download AKS cluster credential.
SPOKE_RG=rg-spoke STUDENT_NAME= AKS_CLUSTER_NAME=private-aks az aks get-credentials --resource-group $SPOKE_RG --name $AKS_CLUSTER_NAME-${STUDENT_NAME}
You should see a similar output as illustrated below:
bash azureuser@Jumpbox-VM:~$ az aks get-credentials --resource-group $SPOKE_RG --name $AKS_CLUSTER_NAME-${STUDENT_NAME} Merged "private-aks" as current context in /home/azureuser/.kube/config azureuser@Jumpbox-VM:~$
12. You should be able to list all pods in namespace frontend. You will now be prompted to authenticate your user again, as this time it will validate your newly created user permissions within the AKS cluster. Ensure you login with the user you created i.e $AAD_OPS_FE_UPN, and not your company email address.
kubectl get po -n frontend
Example output:
azureuser@Jumpbox-VM:~$ kubectl get po -n frontend To sign in, use a web browser to open the page https://microsoft.com/devicelogin and enter the code XXXXXXX to authenticate. NAME READY STATUS RESTARTS AGE nginx 1/1 Running 0 89m
13. Try to list pods in default namespace
bash kubectl get pods
Example output:
bash azureuser@Jumpbox-VM:~$ kubectl get po Error from server (Forbidden): pods is forbidden: User "opsfe-test@xxxxxxxxxx.onmicrosoft.com" cannot list resource "pods" in API group "" in the namespace "default": User does not have access t o the resource in Azure. Update role assignment to allow access.
14. Repeat step 6 and 13 for the remaining users, and see how their permissions differs.
# Username and password for Admin user execute the command from your local shell and not from Jumpbox VM
echo $AAD_ADMIN_UPN
echo $AAD_ADMIN_PW
# Username and password for Backend user execute the command from your local shell and not from Jumpbox VM
echo $AAD_OPS_BE_UPN
echo $AAD_OPS_BE_PW
🎉 Congratulations, you made it to the end!
You’ve just navigated the wild waters of Microsoft Entra ID and AKS — and lived to tell the tale. Whether you’re now a cluster conqueror or an identity integration ninja, give yourself a high five (or a kubectl get pods if that’s more your style).
Now go forth and secure those clusters like the cloud hero you are. 🚀
And remember: with great identity comes great responsibility.
 Microsoft
Microsoft