- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- What’s new: Run playbooks on entities on-demand
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Thanks @Maayan_Magenheim for taking part in leading this feature and writing this blog
Incident entities are a key element in understanding and resolving a security incident. A potential attack may involve a compromised account, an unknown IP address that sent, received, or forwarded traffic, a phishing URL, a suspicious activity detected on a host or a malicious FileHash. Collecting more data and taking remediation and response actions on entities is an integral part of handling an incident.
for example:
- Confirm a user as compromised, reset a user password or disable the account
- Send a user an email template
- Block traffic from a malicious IP in a firewall
- Run an antivirus scan on a host or isolate it
- Add IP to safe/unsafe watchlist or to your external CMDB
- Get a FileHash report from an external TI source
- Create a ticket/task for an external team to take actions on an entity
Each of these actions requires SOC analysts to pivot to an external tool, remember a set of steps they need to take, audit somewhere they took the action and track the action outcomes. The SOC engineer needs to assign permissions for the analysts to interact with those tools and monitor them. In some teams, instead of performing these actions, analysts will need to pivot to external systems to create a ticket for other teams (such as IT) to take the actions. The above takes time and effort, slows the investigation, increases the response time, and reduces productivity.
Now available: Create and run playbook on entities on-demand
- SOC engineers can now encapsulate any repetitive action on entities into Microsoft Sentinel playbooks, grant the playbook the exact permissions required to perform the actions, and grant access to SOC analysts to trigger these playbooks.
- When handling an incident, SOC analysts can select an entity and perform an action on it while staying in context, avoiding dealing with implementation details and saving time.
Microsoft Sentinel automation everywhere
Before this feature, playbooks on-demand could be run on incidents (an informative modifiable case with aggregation of all alerts, entities, and evidence) and alerts (single pieces of evidence) and perform actions on all or some of the entities. Now, playbooks can run on selected entity (specific threat actor).
Hybrid automation approach for the SOC
Using both automated response and actions on-demand helps to increase productivity:
- Full automation is the best solution for as many incident-handling, investigation, and mitigation tasks as you're comfortable automating. Any repetitive flow that always happens when incidents are created or updated (and certain conditions hold) can be set as automated response with automation rules, that trigger playbooks.
As a result, analysts find in their incident queue only the incidents that require their attention, with the most updated fields and all the required information already collected as incident formatted comments, and with any immediate remediation actions already taken. - Playbooks on-demand allows analysts to have a set of actions that can be taken, with their discretion, as part of the incident workflow. Use playbooks to consolidate a string of activities against a range of systems into a single command, but trigger them only when and where you decide.
Feature highlights
Run playbooks as part of incident investigation
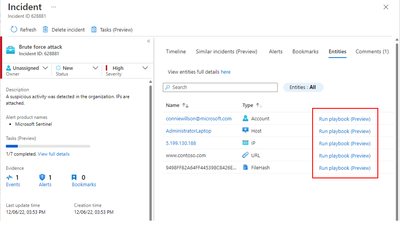
- Find the entity you wish to run a playbook on.
Run playbook on-demand on entities from incident or investigation graph.
- Click on Run playbook (Preview).
- A side panel will open and show all the playbooks that:
- Have the entity trigger on this selected type.
- You have access to view.
A list of playbooks, configured with entity type selected, will be shown.
- Click on Run to trigger the playbook.
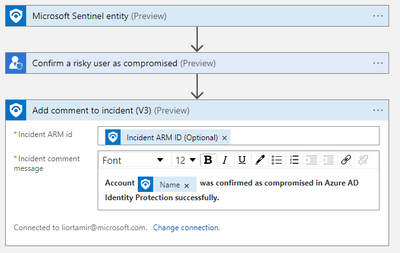
Playbooks created with the Entity trigger and triggered from an incident context can update an incident or add a comment after taking action on the entity.
Proactively take actions on entities while hunting
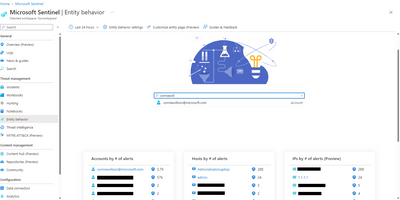
Microsoft Sentinel entity pages help advanced analysts (tier 3, “hunters”) to pro-actively hunt for threats, even before an incident is created. Under Entity Behavior hunters can search for specific entities or select from the lists of top risky entities. When utilizing the information and tools provided on the entity pages, hunters can now take action to protect your organization from potential threats without switching screens and losing context.
Search for entities using Microsoft Sentinel entity behavior.
Run playbook on-demand on entities from entity page.
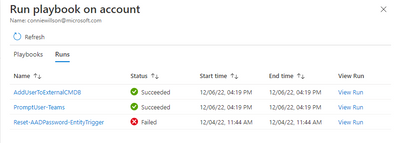
View run history
You can see the run history for playbooks on an entity by selecting the Runs tab. It might take a few seconds for any just-completed run to appear in the list. Selecting a specific run will open the full run log in Logic Apps.
View all previous playbook runs on this entity under Runs tab.
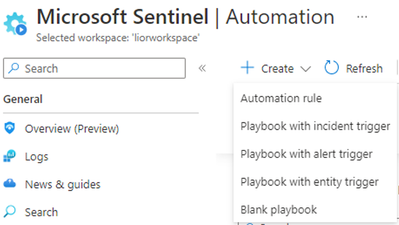
Develop playbooks
- Under Automation, click on + Create and select Playbook with entity trigger.
Alternatively, select Blank playbook, select either Consumption or Standard playbook, and in the newly created playbook find the new Microsoft Sentinel entity trigger:
- Select the entity type you want this playbook to receive as an input:
- Create your flow of actions.
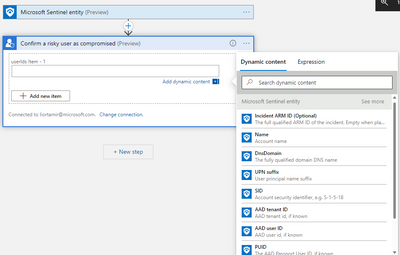
The Dynamic content menu will offer the selected entity fields based on your previous selection: - If this playbook is intended to run from an incident context (from incident page, or from investigation graph of incidents), use the Incident ARM ID to write comments or update the incident.
New RBAC role: Grant analyst permissions to run playbooks
Using playbooks to encapsulate actions, analysts don’t have to get direct permissions on external tools to run actions - playbooks (Logic Apps connectors) encapsulate the permissions required.
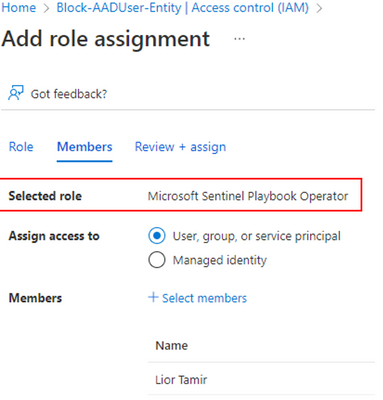
Then, you can use the Microsoft Sentinel Playbooks Operator RBAC role to give analysts permissions to run (but not edit) a specific playbook (or to a Resource Group of multiple playbooks).
This way analysts see a list of playbooks which serve as their actions toolbox; Each tier can have their own level of actions required to be run.
Select the Microsoft Sentinel Playbook Operator when assigning permissions on a playbook.
Learn more
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.