- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- End to end container security with unified SOC experience
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In the dynamic landscape of cloud security, the journey from code to runtime protection is a narrative of innovation and adaptation. At the heart of this evolution lies Microsoft Defender for Cloud, a CNAPP solution designed to fortify multi-cloud environments seamlessly.
Today we are announcing recent releases and enhancements for container security in Defender for Cloud with the general availability of Defender for Containers in AWS and GCP, containers risk-based prioritization, attack path analysis, Kubernetes identity monitoring, new eBPF sensor, detections and investigation capabilities.
Let's delve into the story of Microsoft Defender for Cloud’s recent capabilities across different stages of container applications deployment lifecycle.
Forging a Secure Kubernetes Chain: From Supply Chain to Cluster Compliance
The security of your containerized environment isn't a standalone battle – it's a war fought across the entire software supply chain. Vulnerabilities can lurk anywhere, from code repositories to containers, waiting to be exploited. Microsoft Defender for Cloud understands this interconnected landscape and offers a multi-pronged approach to fortify your Kubernetes security from end to end.
Imagine a detailed map of your Kubernetes environment, revealing not just containers but also internet exposure and permissions to other cloud resources. This is the power of Microsoft Defender for Cloud's new Kubernetes RBAC data, analyzing roles and permission configurations of the various cluster assets. Think of it as uncovering hidden tunnels beneath your castle walls – potential weaknesses that attackers could exploit to gain unauthorized access. With the new attack path engine in Defender CSPM, which uses path-finding algorithm to detect every possible attack path that exists in your cloud environment, Defender for Cloud finds many more attack paths in your environment and detect more complex and sophisticated attack patterns that attackers can use to breach your Kubernetes environment. You can proactively identify and address posture issues before they become a security breach. More information on attack path can be found here: Identify and remediate attack paths.
Taking our commitment to comprehensive container security a step further, Defender CSPM has introduced risk-based prioritization for recommendations, complementing existing vulnerability assessments with vulnerabilities at the image and container level with a comprehensive risk assessment. The risk is calculated using a graph of your cloud assets in their security context. This holistic view allows you to prioritize remediation efforts based on potential impact and empower you to focus on the most critical threats first, maximizing your cloud posture with efficient resource (time and effort) allocation. For more information on risk-based prioritization in Defender for Cloud see: Risk prioritization.
Strong security requires following best practices. Microsoft Defender for Cloud simplifies compliance by integrating Center for Internet Security (CIS) Kubernetes benchmarks into your security dashboard. These benchmarks automatically assess your clusters and provide clear steps to achieve a fully secure Kubernetes environment. Check out the full list of supported compliance standards
Building a resilient supply chain requires vigilance at every step. Defender for Cloud goes beyond Kubernetes clusters to equip organizations with the tools they need to fortify their container security during CI/CD. Defender for Cloud, now covering also OCI and Windows container images across clouds and registries powered by Microsoft Defender Vulnerability Management (MDVM).
With these new security measures, Microsoft Defender for Cloud empowers you to take control of your containerized environment, from the moment your code is written to its final deployment in your Kubernetes environment. This holistic approach allows you to proactively mitigate supply chain risks, navigate compliance challenges, and ultimately safeguard your containerized applications across your entire cloud journey.
Seamless Multicloud Security: Defender for Cloud's Unified Approach to Container Security Across AWS, Azure, and GCP
As organizations embrace multicloud, the silos between cloud environments can become barriers for a holistic approach to container security. Defender for Cloud continues to adapt, offering new capabilities that resonate with the fluidity of multicloud architecture.
With the general availability release of Defender for Containers in AWS and GCP, Defender for Cloud completes the parity of Defender for Containers across the 3 main cloud providers – AWS, Azure and GCP. On top of that it has simplified the provisioning process, providing effortless scalable onboarding, removing the overhead to onboard each cluster and environment separately.
Moving forward with one unified Microsoft solution for vulnerability assessments for the different clouds and hybrid workloads, Defender for Cloud has introduced an out-of-the-box container vulnerability assessment powered by MDVM across AWS, Azure and GCPs registries and managed Kubernetes offerings. With the general availability release of MDVM vulnerability assessment for ECR, GCR, and GAR container images, MDC is leaping ahead, streamlining security measures across clouds and throughout the supply chain.
More information on the unified Vulnerability Assessment can be found in this blog: Defender for Cloud unified Vulnerability Assessment powered by Defender Vulnerability Management.
Acknowledging the unique security requirements of government and regulated industries, Defender for Containers is now fully supported in Azure Government and Azure China Clouds, enabling organizations to uphold stringent compliance standards.
Level Up Your Container Defense with native integration into Microsoft Defender XDR
The powerful integration between Microsoft Defender for Cloud and Microsoft XDR is here, and it's constantly evolving to elevate your container security, empowering your Security Operations Center (SOC) team to become even more effective cyber defense champions.
New Threat Detection Sensor
A new Defender sensor for Defender for Containers is available. It includes performance and security improvements, leveraging Microsoft’s open-source technology - Inspektor Gadget. The innovative sensor plays a pivotal role in strengthening Defender for Containers runtime protection capabilities. With its recent support for ARM64 node, Inspektor Gadget broadens its reach across diverse cloud environments. Think of it as a highly skilled security guard patrolling your containerized kingdom, able to identify and neutralize threats before they can infiltrate your crown jewels. For more information about our new sensor see: eBPF-Powered Threat Protection using Inspektor Gadget
Deep Detection and Investigation for Containers and Kubernetes in Microsoft Defender XDR
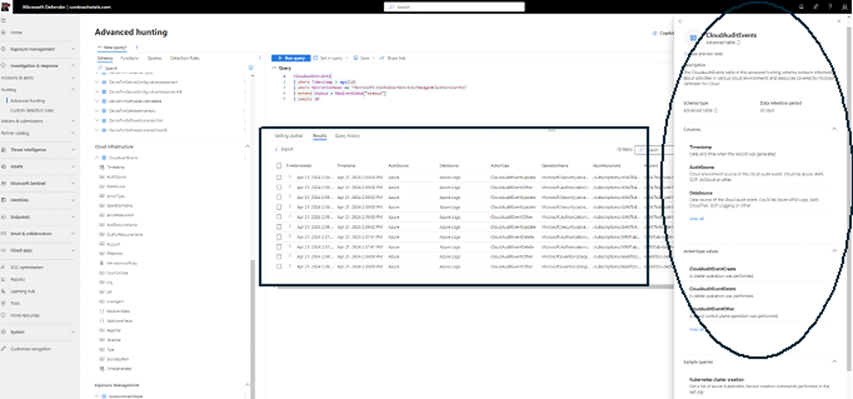
Traditionally, investigating container threats has been akin to working a case in the dark. Valuable evidence might be scattered or inaccessible, hindering your SOC team's ability to identify the malicious activities. Microsoft Defender for Containers sheds light on this challenge by collecting and integrating Kubernetes Audit Logs into Microsoft Defender XDR’s advanced hunting experience, equipping your SOC team with a wealth of new Kubernetes data, empowering them to conduct deeper investigations in a single unified leading XDR platform. Think of it as dusting for fingerprints at a crime scene – the more data you have, the stronger the case you can build.
On top of the continued evolving Microsoft’s built-in detection mechanisms, you can now add your own custom detection rules in Microsoft Defender XDR. These custom rules act like personalized fingerprint identification kits for your environment. You can tailor them to identify specific threats relevant to your organization. More information about can be found here: Advanced hunting and Custom detections in Microsoft Defender XDR
To summarize,
As the CNAPP story continues to unfold, Microsoft Defender for Cloud is committed to innovation and security excellence, providing the tools and insights your organization needs to secure its containerized journey on the cloud, at every stage of the container’s deployment lifecycle, from code to runtime. Enable Defender for Cloud premium offering today and join us on this journey to empower your organization with unparalleled protection in the ever-evolving landscape of cloud native security.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.