- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Critical Asset Protection with Microsoft Security Exposure Management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In recent years, enterprises attack surface has exploded in volume and diversification. Security teams are struggling to keep pace with the technological advancements and changes occurring daily. New technologies, emerging work trends (such as remote work and distributed teams), expansion of the supply chain, cloud adoption, and more have led to an exponential growth in the size and complexity of the enterprise attack surface.
This rapid expansion has brought about new risks, and in turn, new tools to deal with these risks. The rapid increase of the attack surface has led to a rapid proliferation of security tools. The numbers are truly staggering with large organizations often using dozens of security tools. Combined with the shortage of security personnel and knowledge gaps, security teams are experiencing more than just alarm fatigue; they are facing risk fatigue.
If everything is important, then nothing is.
Risk fatigue occurs when there are so many potential risks or security issues to address that it becomes overwhelming, leading to decreased effectiveness in risk management efforts. Risk fatigue is a direct consequence of the inability to single out exposures with the highest potential impact; those that truly pose a tangible risk, from the entire exposure surface. Without context to support their decisions, security teams are forced to rely on inaccurate and suboptimal prioritization. Addressing the wrong issues results in a double loss – wasted team time and unresolved actual risks.
To effectively address risk fatigue, security teams should embrace a contextual risk-based approach. This entails thorough consideration of various security-related contexts, including the business criticality of an asset and the likelihood of it being compromised. By doing so, teams can strategically prioritize activities that yield the greatest security impact, bolstering the organization's overall resilience. In this blog post, we will explore how Microsoft Security Exposure Management helps enterprises in identifying and managing their most critical assets and in focusing on mitigating risks to these assets.
Not all assets are created equal
As mentioned, a crucial aspect of adopting a contextual risk-based approach involves considering the business criticality of each asset and responding accordingly. Identifying critical assets isn't just a recommended strategy for supporting risk-based prioritization; it is crucial in adopting the mindset of potential adversaries. Attackers often target critical assets in malicious operations like data theft, cyber espionage, disruption, ransomware attacks, and more. Given that attackers are laser-focused on critical assets, it's imperative for defenders to mirror this focus.
However, in today's highly complex, distributed, and dynamic enterprise environments, keeping pace is nearly impossible. This, combined with the above-mentioned shortage of security personnel, and knowledge gaps around adversary techniques, makes it highly challenging for organizations to identify, manage, monitor, and prioritize their business-critical assets. That's where Microsoft Security Exposure Management comes in!
Focus first on what matters most with Microsoft Security Exposure Management
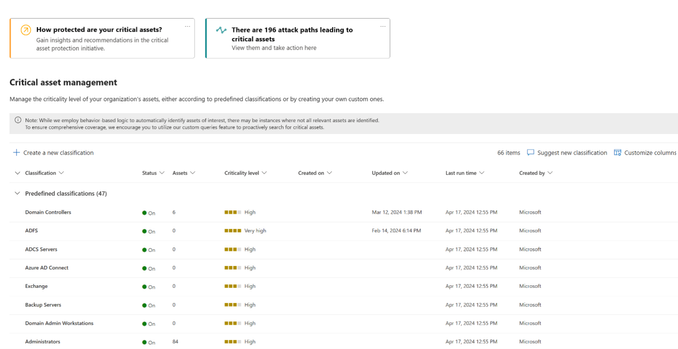
Microsoft Security Exposure Management provides users with everything they need to prioritize their business-critical assets. This includes a comprehensive out-of-the-box library of predefined classifications designed to identify and label your most critical devices, identities, and cloud resources. This includes classification for domain controllers, Azure AD Connect, ADFS servers, Backup servers, security administrators, domain administrators, databases with sensitive data and many more.
Creating these predefined classifications is no simple task, especially if you aim to accurately mark only critical assets that “meet the criteria”. For example, the process of identifying a critical domain controller involves a robust data collection procedure from Windows servers and workstations. Initially, various logics are implemented to identify devices offering Active Directory services. Next, different types of telemetry data, such as user-login events, device domain membership information, and various network signals, are processed to create a comprehensive understanding of the criticality of each domain entity. This process enables us to classify the domain controllers managing these domains as critical assets, regardless of whether they are onboarded to Microsoft Defender for Endpoint or not, across organizations of all sizes.
Figure 1: The critical asset management screen in Microsoft Security Exposure Management
Naturally, many organizations may have their own unique definitions for business-critical assets. Keeping this in mind, we empower customers to craft their own custom classification rules. For instance, if you have a specific naming convention for resources relevant to a business-critical application, you can now create a custom classification to label only these assets as critical.
Additionally, echoing once more that "Not all assets are created equal," we can also acknowledge that not all critical assets hold the same level of importance. Some assets may be classified as tier 0, while others, although still important for business continuity, might fall under tier 1 or even tier 2. For this reason, our customers can choose from four different criticality levels to ensure sufficient granularity and cater to their specific needs.
Spotlight: Identifying VMware vCenter
As mentioned, accurately pinpointing critical assets is complex, requiring careful distinction between true crown jewels and assets that may be mistaken as ones. A nice example is an Exchange server, which is installed in a small testing lab versus one which serves as the emailing infrastructure of the entire organization; simply looking for installed and configured server roles isn’t enough and more elaborate identification tactics are required to map these assets, which are also operationalized. Below is an overview of one of the classifications natively supported by Microsoft Security Exposure Management. - VMware vCenter.
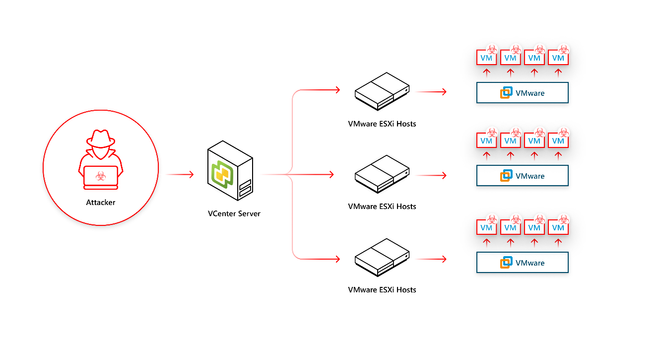
VMware vCenter is utilized as a centralized platform for managing and administering VMware virtualized environments. It enables administrators to perform various operations related to ESXi hosts, virtual machines, redundancy and more.
As vCenter operates as a centralized platform, it automatically becomes a crucial component within the network. Gaining access to vCenter means gaining access to every virtual component mentioned earlier and potentially compromising the virtual infrastructure. Consequently, Microsoft threat researchers have been observing a steady increase of incidents where attackers target vCenter devices to have a significant impact while remaining under the radar of traditional security measures. Once attackers gain privileged access to the vCenter servers, they can compromise running virtual guests and/or disrupt the organization’s operations by modifying, encrypting or deleting virtual machines and in some cases even their backups (which is often observed in recent ransomware attacks).
Figure 2: A compromised vCenter can lead to unauthorized access and control over virtualized infrastructure
Identifying a production vCenter can be challenging, mainly because it is a non-onboarded device, leading to limited visibility. To address this, we utilized Microsoft Defender for Endpoint “Device Discovery" capability which already accurately fingerprints vCenter device, alongside Microsoft Defender for Endpoint’s network connection events from onboarded devices. To identify such devices accurately, we analyze the number of users connected to the vCenter management system over time, determine which processes initiated these connections together with several other factors.
Use asset criticality context in the Defender suite.
Identifying and managing critical assets marks the initial step, however, to truly prioritize these assets, seamless integration and accessibility across existing security workflows are crucial for effective protection. Our goal is not only to display this context where applicable; it's to help security teams in prioritizing business critical assets effectively. Asset criticality context plays a vital role in generating potential attack paths leading to crown jewels, refining exposure scores and risk scores, facilitating contextual incident triage, and prioritizing security recommendations.
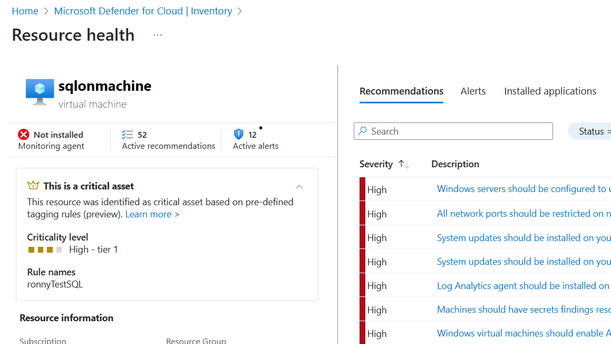
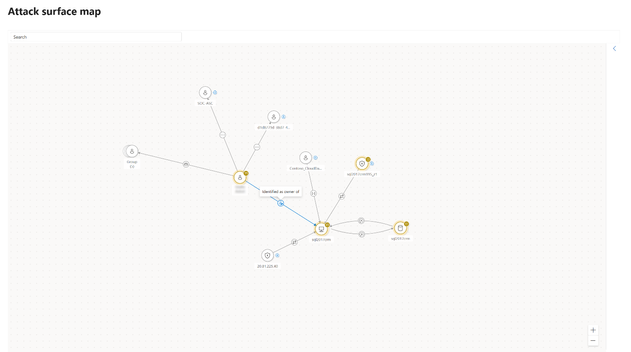
With this objective in mind, we are integrating asset criticality across various Defender products and areas, including Microsoft Defender for Cloud, Microsoft Defender Vulnerability Management (Preview), Microsoft Defender XDR (Preview), and Defender Device Inventory and Device Page. Additionally, asset criticality context is integrated in features within Microsoft Security Exposure Management, such as the Attack Surface Map, Attack Path Management, the Critical Asset Protection Initiative, and more.
Figure 3: Asset criticality insight in Microsoft Defender for Cloud resource page
Figure 4: Critical asset indications in Microsoft Security Exposure Management attack surface map
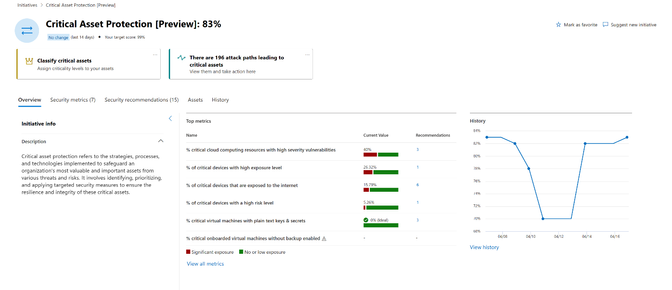
The Critical Asset Protection Initiative is a notable example of integrating asset criticality context. Within Exposure Management, security Initiatives serve as a guiding framework for security teams, encouraging a continuous approach to threat exposure management. Through a dedicated initiative, customers can monitor the current exposure of their critical assets and systematically track their progress in securing these assets. To learn more about initiatives, see Overview of exposure insights and secure score - Microsoft Security Exposure Management | Microsoft ...
Figure 5: Critical Asset Protection initiative in Microsoft Security Exposure Management dashboard.
Getting started with Critical Asset Protection
Here are some tips for getting started with critical asset protection concepts and features:
Explore our out-of-the-box criticality classification library: Review the critical classification library within Exposure Management. Discover assets associated with each classification and set criticality levels to align with your organization's strategic approach to safeguarding critical assets.
We are continuously expanding this library to better serve our customers’ needs. In this regard, make sure to utilize the "suggest new classification" button in the critical asset management screen to inform us which classification you would like us to support next.
Craft your own custom criticality classification: Within the critical asset management screen, you can generate custom queries to identify your organization's unique "crown jewels". For instance, you can target critical servers using specific naming conventions.
Prioritize attack paths leading to critical assets: Microsoft Security Exposure Management's attack paths feature offers insight into potential routes attackers may exploit to compromise critical assets. Utilize the "target criticality" filter on the attack path list screen to focus on paths involving critical assets. Addressing these paths by implementing the associated recommendations will mitigate potential risks to your critical assets.
Search for the critical asset "crown" icon in the map: The Microsoft Security Exposure Management attack surface map provides new exploration capabilities and insights into assets’ connections. Critical assets are denoted by the "Crown" icon , highlighting their significance. By focusing on the "vicinity" of your critical assets, you can identify potential risks or security gaps, such as unauthorized user permissions to sensitive information or inadequate implementation of security policies, exposing critical machines to the internet.
Monitor progress with Critical Asset Protection initiative: Work with the Critical Asset Protection Initiative to actively monitor and assess your progress in safeguarding critical assets.
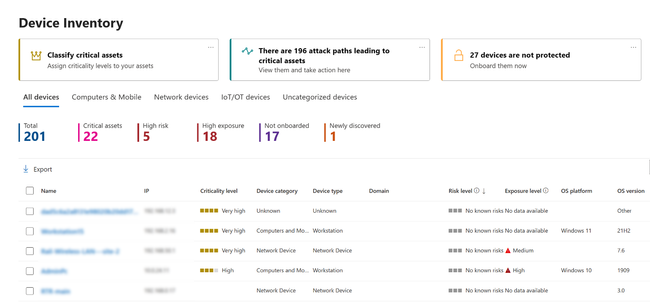
Gain visibility into your “critical organization”: Utilize the asset tab within the Critical Asset Protection Initiative and the “Criticality level” filter in the Device Inventory to obtain a comprehensive overview of your critical devices, identities, and cloud resources.
Figure 6: Device criticality in Defender Device Inventory
Establish dedicated procedures and SLAs for critical assets: Establish clear timelines and response protocols for business-critical assets. With the enhanced visibility and management capabilities for critical assets to support these procedures, you can now build a framework for prioritizing and addressing critical asset-related issues promptly and efficiently.
To sum up, effectively identifying and safeguarding business-critical assets in today's dynamic threat landscape is essential for enterprise resilience. Emphasizing the importance of a contextual risk-based approach, Microsoft Security Exposure Management provides comprehensive solutions for critical asset discovery and management, enabling customers to focus on protecting their most critical assets first.
For those looking to learn more about critical assets, attack paths and exposure management in general, here are some additional resources you can explore.
- Critical asset protection documentation: Overview of critical asset management in Microsoft Security Exposure Management - Microsoft Security...
- Microsoft Security Exposure Management documentation: Microsoft Security Exposure Management documentation - Microsoft Security Exposure Management | Micr...
- Microsoft Security Exposure Management website: Microsoft Security Exposure Management | Microsoft Security
- Microsoft Security Exposure Management release blog post: Introducing Microsoft Security Exposure Management - Microsoft Community Hub
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.