- Home
- Windows Server
- Storage at Microsoft
- Getting started with Central Access Policies - Reducing security group complexity and achieving data access complia...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Following the introduction to Dynamic Access Control , I’d like to give you a few practical examples of how you can utilize Dynamic Access Control in your File Server environment.
For many IT and Security architects that we talked to about Dynamic Access Control, the first reaction has been that this is a very powerful feature set. Then comes the obvious question of how do I get started? What information should I target first? …
Let’s explore two common Central Access Policy scenarios that this technology helps you solve:
1. Safe Harbor access compliance
2. Reducing the complexity for security groups
For both examples, I am going to use Dynamic Access Control with security groups so that all you need in your environment to achieve this are:
· A Windows Server 2012 File Server
· A domain with a Windows Server 2012 schema (so that you can define central access policies)
You can find a demo video that shows the deployment steps of the two scenarios here
Safe Harbor - Access compliance sample scenario
If your company needs to deal with data that falls under the US-European Union Safe Harbor regulation, Dynamic Access Control can help you limit access to that data to the specific group of people allowed access to Safe Harbor data.
The steps to achieve this are:
1. Tagging the data by marking the folders that contain Safe Harbor data (Compliancy=Safe Harbor)
2. Configuring a Central Access Rule that specifies that only specific security groups can access data that is marked as Safe Harbor
3. Applying a Central Access Policy to the appropriate Windows Server 2012 File Servers in your organization
Note that there is no need to change the current NTFS access rules since the Central Access Policy acts as a safety net that enhances the local NTFS access rules.
Now, when someone wants to review who can access Safe Harbor information, you can simply show the security group(s) specified in the central access rule.
You can find instructions on how to configure Central Access Policies in our TechNet documentation ( http://technet.microsoft.com/en-us/library/hh831717.aspx ) that includes both step-by-step and PowerShell Cmdlets. Since the documentation provides a more general example that also includes user claims, here are a few screenshots that show the specific configuration for the Safe Harbor scenario:
(Note: This walkthrough is for illustration only since it skips some of the configuration steps such as group policy. For a complete walkthrough please use the abovementioned TechNet documentation)
· Using Active Directory Administration Center to enable the pre-defined “Compliancy” resource property so that it can be used to tag files

Here are the PowerShell commands and syntax to enable the “Compliancy” property definition:
Set-ADResourceProperty Compliancy_MS -Enabled:$true -Server:"DC1.contoso.com"
· Using Active Directory Administration Center to create a Central Access Rule for Safe Harbor

Here are the PowerShell commands and syntax to define the “Safe Harbor” Central Access Rule:
New-ADCentralAccessRule -CurrentAcl:"O:SYG:SYD:AR(A;;FA;;;WD)" -Name:"Safe Harbor Central Access Rule" -proposedAcl:"O:SYG:SYD:AR(A;;FA;;;OW)(A;;FA;;;SY)(A;;0x1301bf;;;S-1-5-21-3479418876-2348745693-2649290146-1224)" -ProtectedFromAccidentalDeletion:$true -ResourceCondition:"(@RESOURCE.Compliancy_MS Any_of {`"US-EU Safe Harbor`"})" -Server:"DC1.contoso.com"
· Using the Folder properties Classification tab to tag a folder with Compliancy = Safe Harbor
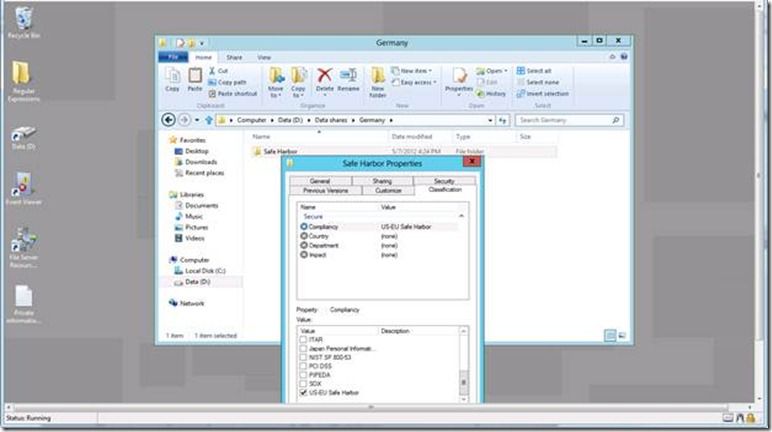
Here are the PowerShell commands and syntax to set the “Compliancy” to “US-EU Safe Harbor” on a specific folder:
$cls = new-object -com Fsrm.FsrmClassificationManager
$cls.SetFileProperty("d:\data shares\germany", "Compliancy_MS", "US-EU Safe Harbor")
· Assigning a Central Access Policy (that includes the Safe Harbor Central Access Rule) to a File Server share using Folder properties à Security à Advanced
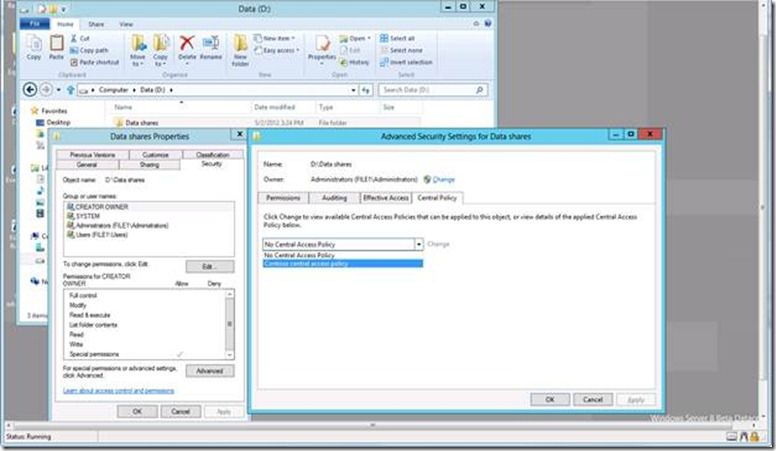
Here are the PowerShell commands and syntax to set a Central Access Policy on a folder:
(Note that to get to this step we skipped the distribution of the central access policy through group policy that is covered in the TechNet documentation)
$acl = get-acl “d:\Data shares” –audit
set-acl “d:\Data shares” $acl “Contoso central access policy”
Reducing the complexity for security group – Need to know sample scenario
In this example, I’d like to describe a generic common scenario that shows how you can use Dynamic Access Control to considerably reduce the complexity of a combinatorial number of security groups (e.g.: From 2,000 to less than a 100) so that you can have a clear understanding of who can access what data and you are able to easily adjust access when people move between different roles in the company.
The example is for a company that has branches in 50 countries and has 20 different departments and for each department in each country there is some sensitive information.
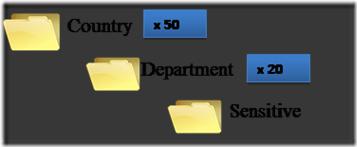
If we structure the folders as shown above, we would need more than 2,000 groups to cover all the combinations so that we can assign the appropriate access control.
You will then need to define an access control list (ACL) for each of the folders using the designated security groups for that folder structure. This will result in more than 2,000 different ACLs.
Last, if a person from the Finance department with access to sensitive information moves to the HR department, we need to change at a minimum 100 security groups (Remove from 50 and add to 50)
So, we have 2,000 groups, 2,000 ACLs and many groups that are affected by a person changing a role not to mention the complexity of adding another level (say Branch) or the implications if we want to change the folder structure.
With Dynamic Access Control, you can cut the number of groups down from 2,000 to 71 (50 for country, 20 for department and 1 for sensitive data access). This is made possible by the ability to use expressions in Windows ACL. For example: You would use MemberOf (Spain_Security_Group) AND MemberOf (Finance_Security_Group) AND MemberOf(Sensitive_Security_Group) to limit access to Spain’s finance department sensitive information.
In addition, if a person from the finance department with access to sensitive information moves to the HR department, you would need to make only 2 changes to the security groups (vs. 100 changes) removing the person from the finance security group and adding him/her to the HR security group.
Still, if you want to apply the conditions to each folder, you would need more than 2,000 ACLs. This is where Central Access Rules in combination of data tagging can be used to reduce the number of access conditions to 71 matching each group with the appropriate data tagging. By using this method for controlling access, it is also easy to add and make changes to the folder structure.
To use Central Access Rules for reducing the complexity, you would tag each country folder with the appropriate country value, each department folder with the appropriate department value and the sensitive folder with a high sensitivity value. Then you would configure three Central Access Rules: one for country, one for department and one for sensitive information.
The country Central Access Rule would govern the access to each country sub tree and will contain 50 different access conditions such as: Resource.Country = US AND User.MemberOf(US_Security_Group) which allows only people from the US_Security_Group to access files that are tagged as Country=US .
The department Central Access Rule would govern the access to each department sub tree and will contain 20 different access conditions such as: Resource.Department = Finance AND User.MemberOf(Finance_Security_Group) which allows only people from the Finance_Security_Group to access files that are tagged as Department=Finance .
Last, the sensitive information Central Access Rule would govern the access to each of the sensitive information sub tree and will contain 1 access condition: User.MemberOf(Sensitive_Security_Group) .
The configuration is very similar to the Safe Harbor configuration outlined above. Here are the steps for creating the “Country” related access rule:
· Using Active Directory Administration Center to create “Country” resource property and populate it with the list of allowed values

Here are the PowerShell commands and syntax to create the “Country” property definition:
New-ADResourceProperty -DisplayName:"Country" -IsSecured:$true -ProtectedFromAccidentalDeletion:$true -PassThru:$null-ResourcePropertyValueType:"CN=MS-DS-SinglevaluedChoice,CN=Value Types,CN=Claims Configuration,CN=Services,CN=Configuration,DC=contoso,DC=com" -Server:"DC1.contoso.com" -SuggestedValues:@((New-Object Microsoft.ActiveDirectory.Management.ADSuggestedValueEntry("Canada", "Canada", "")), (New-Object Microsoft.ActiveDirectory.Management.ADSuggestedValueEntry("China", "China", "")), (New-Object Microsoft.ActiveDirectory.Management.ADSuggestedValueEntry("Germany", "Germany", "")), (New-Object Microsoft.ActiveDirectory.Management.ADSuggestedValueEntry("Spain", "Spain", "")), (New-Object Microsoft.ActiveDirectory.Management.ADSuggestedValueEntry("US", "US", "")))
Add-ADResourcePropertyListMember "Global Resource Property List" -Members Country_88cf03590d9e3476 -Server "DC1,contoso.com"
· Using Active Directory Administration Center to create a Central Access Rule for access to specific country information

Here are the PowerShell commands and syntax to create the “Country” Central Access Rule:
(Note that this is based on security group IDs and the unique ID of the Country property defined above)
New-ADCentralAccessRule -CurrentAcl:"O:SYG:SYD:AR(A;;FA;;;WD)" -Name:"Country based rule using groups" “-ProtectedFromAccidentalDeletion:$true -ProposedAcl:"O:SYG:SYD:AR(A;;FA;;;OW)(A;;FA;;;BA)(A;;FA;;;SY)(XA;;0x1301bf;;;AU;((Member_of {SID(S-1-5-21-3479418876-2348745693-2649290146-1223)}) && (@RESOURCE.Country_88cf03590d9e3476 == `"Spain`")))(XA;;0x1301bf;;;AU;((Member_of {SID(S-1-5-21-3479418876-2348745693-2649290146-1221)}) && (@RESOURCE.Country_88cf03590d9e3476 == `"China`")))(XA;;0x1301bf;;;AU;((Member_of {SID(S-1-5-21-3479418876-2348745693-2649290146-1220)}) && (@RESOURCE.Country_88cf03590d9e3476 == `"Canada`")))(XA;;0x1301bf;;;AU;((Member_of {SID(S-1-5-21-3479418876-2348745693-2649290146-1222)}) && (@RESOURCE.Country_88cf03590d9e3476 == `"Germany`")))(XA;;0x1301bf;;;AU;((Member_of {SID(S-1-5-21-3479418876-2348745693-2649290146-1218)}) && (@RESOURCE.Country_88cf03590d9e3476 == `"US`")))" -ProtectedFromAccidentalDeletion:$true -ResourceCondition:"(Exists @RESOURCE.Country_88cf03590d9e3476)" -Server:"DC1.contoso.com"
· Using the Folder properties Classification tab to tag a folder tree with Country = US
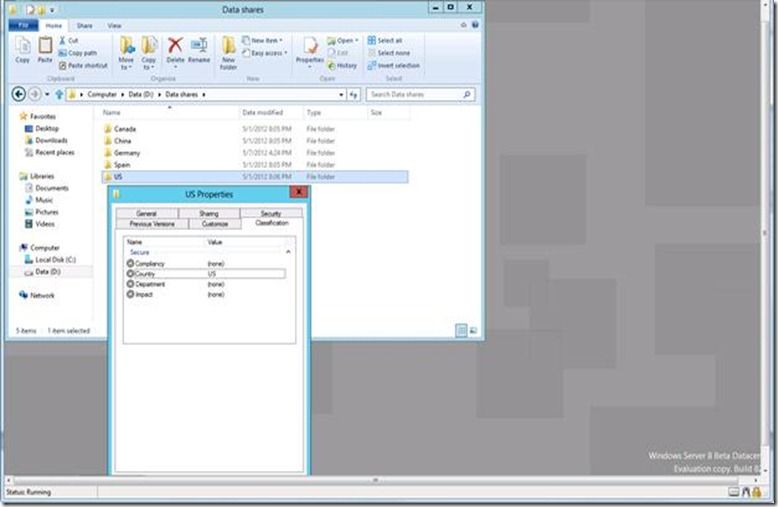
Here are the PowerShell commands and syntax to set the “Country” property to “US” on a folder:
(Note that the country resource property has a unique identifier that is automatically assigned on creation and this identifier is used when calling SetFileProperty)
$cls = new-object -com Fsrm.FsrmClassificationManager
$cls.SetFileProperty("d:\data shares\us", "Country_88cf03590d9e3476", "US")
· Assigning a Central Access Policy that includes the three Central Access Rules for Country, Department and Sensitive information to the root of the File Server share for all countries (note that this is exactly the same screenshot as the one we use for Safe Harbor since we can use one Central Access Policy that contains both access control for Safe Harbor information and countries/department information)

Here are the PowerShell commands and syntax to set a Central Access Policy on a folder:
(Note that to get to this step we skipped the distribution of the central access policy through group policy which is covered in the TechNet documentation)
$acl = get-acl “d:\Data shares” –audit
set-acl “d:\Data shares” $acl “Contoso central access policy”
Nir Ben-Zvi
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.