- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Trusted launch for Azure Arc VMs on Azure Stack HCI
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Trusted launch for virtual machines
You may be familiar with Trusted launch for Azure virtual machines (VMs). It supports secure boot, virtual TPM (Trusted Platform Module), and boot integrity monitoring for virtual machines that run on Azure.
Trusted launch for Azure Arc VMs on Azure Stack HCI is now available, starting with version 23H2. This release of Trusted launch for Azure Arc VMs supports secure boot, virtual Trusted Platform Module (vTPM), and vTPM state transfer when a VM migrates or fails over within a cluster.
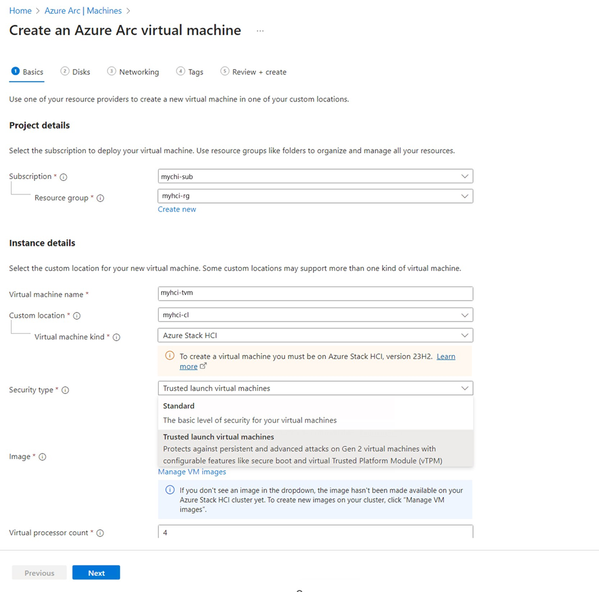
You can choose Trusted launch as a security type when creating Azure Arc VMs on Azure Stack HCI via Azure portal or Azure CLI.
Need to preserve vTPM state during VM migration and VM failover
With standard VMs, vTPM state is not preserved when a VM migrates or fails over to another node. This limitation is a problem for applications that rely on the vTPM and its state. To overcome this limitation, customers use manual methods to move the vTPM state. This affects functionality and availability of applications that rely on the vTPM.
With Trusted launch, vTPM state is automatically moved along with the VM, when a VM migrates or fails over to another node within a cluster. This allows applications that rely on the vTPM state to continue to function normally even as the VM migrates or fails over. Applications use TPM in a variety of ways. In general, any application that relies on the TPM will benefit from Trusted launch capabilities.
Following examples illustrate the importance of preserving vTPM state as the VM migrates or fails over to another node.
BitLocker encryption feature in Windows uses TPM as a key protector for the operating system (OS) volume. The boot state stored in the TPM is used to unseal the encryption key for the OS volume. If the boot state stored in the vTPM is not preserved during VM migration or VM fail over, the encryption key for the OS volume cannot be unsealed. This will result in BitLocker asking the user for recovery key when the migrated VM boots up.
Internet of Things (IoT) applications use TPM as a secure enclave to create and store device identity. If the vTPM state that stores the device identity is lost during VM migration or VM failover, the virtual device will not be able to authenticate and participate in the IoT network.
Device health attestation feature in Windows uses boot measurements stored in the TPM to verify system boot integrity. Proof of device health is typically used to provide conditional access to protected resources. If boot measurements stored in the vTPM are not preserved during VM migration or VM failover, the virtual device will lose access to resources which was conditionally provided based on proof of device health.
Applications use TPM as a secure enclave to store secrets. By using the vTPM, secrets can be securely stored in an isolated environment, making it difficult for attackers to get a hold of the secrets. If the vTPM state is not preserved during VM migration or VM failover, secrets stored in the vTPM will be lost, and applications that rely on those secrets cannot function properly.
Your feedback
Trusted launch for Azure Arc VMs on Azure Stack HCI is an important first step in our journey to bring confidential computing to the edge. For more information, you can read Trusted launch for Azure Arc VMs.
Try out Trusted launch for Azure Arc VMs. We look forward to your feedback!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.