- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Seamlessly secure your data estate with Microsoft Purview
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In the era of AI, data is the fuel that drives innovation and progress. It powers the algorithms that drive our businesses, our economies, and our daily lives. As we generate and consume more data than ever before, it is crucial that we take the necessary steps to secure it. Failing to do so can have consequences, from data breaches and identity theft to the loss of trust and reputation. To run responsible analytics and business processes, organizations are looking for ways to seamlessly secure data across the entire lifecycle, from creation to consumption. Only then can we unlock its full potential and activate the data effectively.
Microsoft Purview, as we revealed at Ignite in November 2023, simplifies the process of getting insight into data locations from a new consolidated portal, including sensitive data from Microsoft 365, Microsoft Fabric, Azure, AWS, and other cloud environments. It provides a single data scanning and classification engine that can apply across both structured and unstructured data sources.
Today, we are excited to share some of the next steps in our journey to secure your data estate. In this blog, we will unpack how we are enabling customers to:
- Apply built-in data security controls in Microsoft Fabric.
- Establish uniform protection policies across multiple data sources.
- Enhance user risk signals in Insider Risk Management.
Apply built-in data security controls in Microsoft Fabric
Security admins can apply sensitivity labels in Microsoft Purview Information Protection to Microsoft Fabric workloads. This will allow users to manually label Fabric items with their sensitivity level, and the label will flow to and from these items based on the policies set by administrators. All label settings will be respected consistently. Moreover, Purview Data Loss Prevention (DLP) policies will also work for Microsoft Fabric. This will help security teams automatically detect when Fabric workspaces contain sensitive data based on sensitive information types or sensitivity labels and take actions such as blocking sharing.
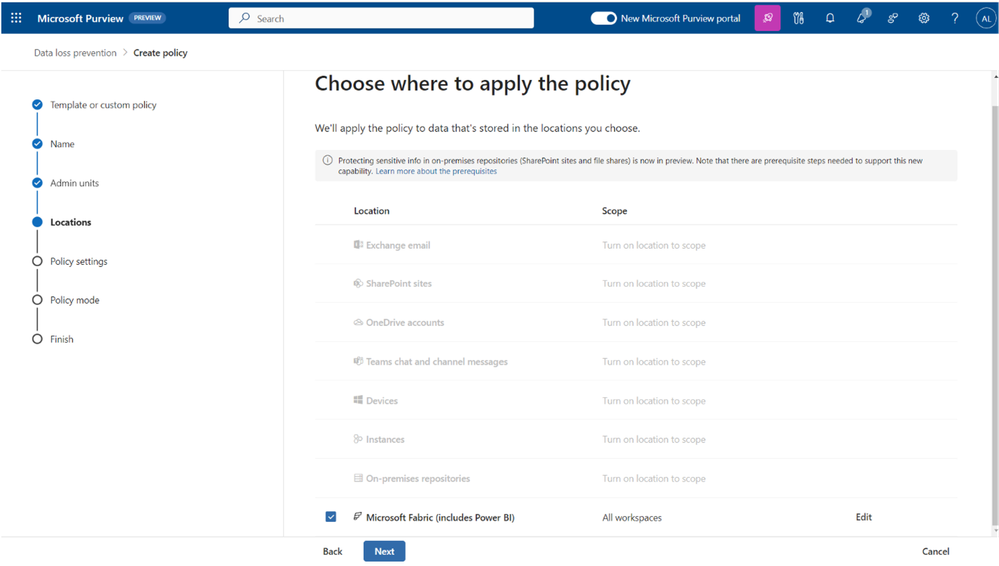
With DLP policies enabled for Microsoft Fabric, end users in Fabric workspaces will see a policy tip when they deal with sensitive data that informs them of their organizations' policies to handle sensitive data.
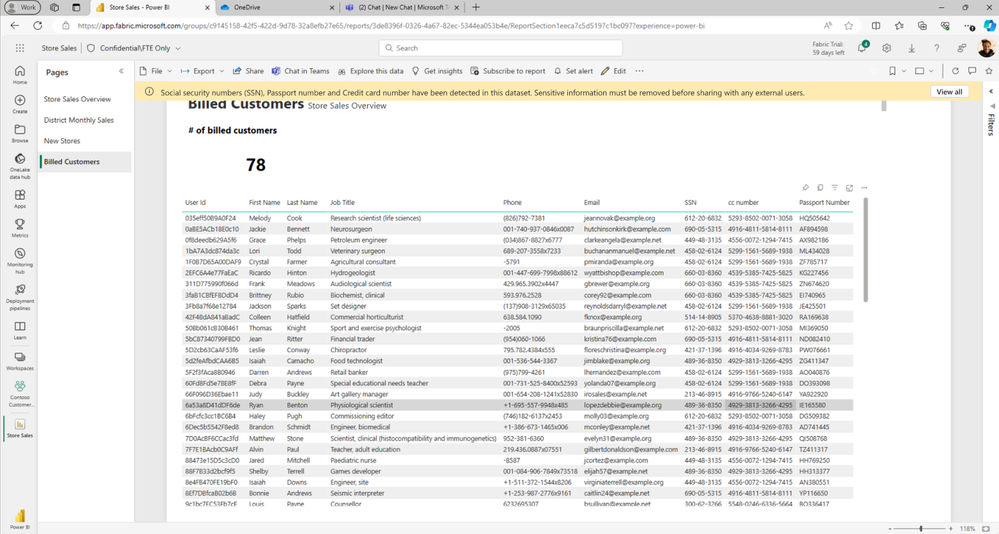
Check out the Microsoft Mechanics video to learn how we are extending our Data Security controls to Microsoft Fabric!
Establish uniform protection policies across multiple data sources.
Organizations have uneven protections because they use many different solutions that do not have a consistent protection standard. Today, we are happy to announce that label-based protection support is now possible for Azure SQL, Azure Data Lake Storage, and Amazon S3 buckets, all within Microsoft Purview Information Protection. You may already know how to protect Microsoft 365 data like documents or e-mails with sensitivity labels, and you will now be able to apply these labels and the related protections to these additional sources. For example, you can set up access controls based on the labeled data for specific users.
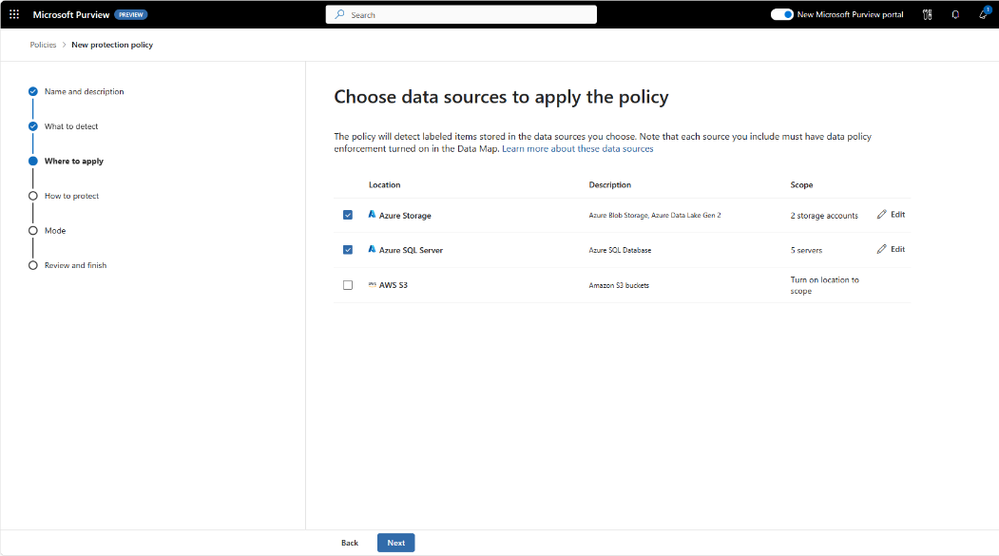
In addition, we are providing a consistent framework for your sensitive information by allowing you to use your existing label scheme and extending it to apply within these sources. When you create a protection policy, you can choose which data sources e.g. databases, or storage buckets are included, and which users or groups are allowed access based on the sensitivity of the data (via sensitivity labels). Users who do not meet these criteria will be prevented from accessing the data. As data moves from one system to another – for example: data moving from Azure SQL to Power BI to Excel - the protections will persist.
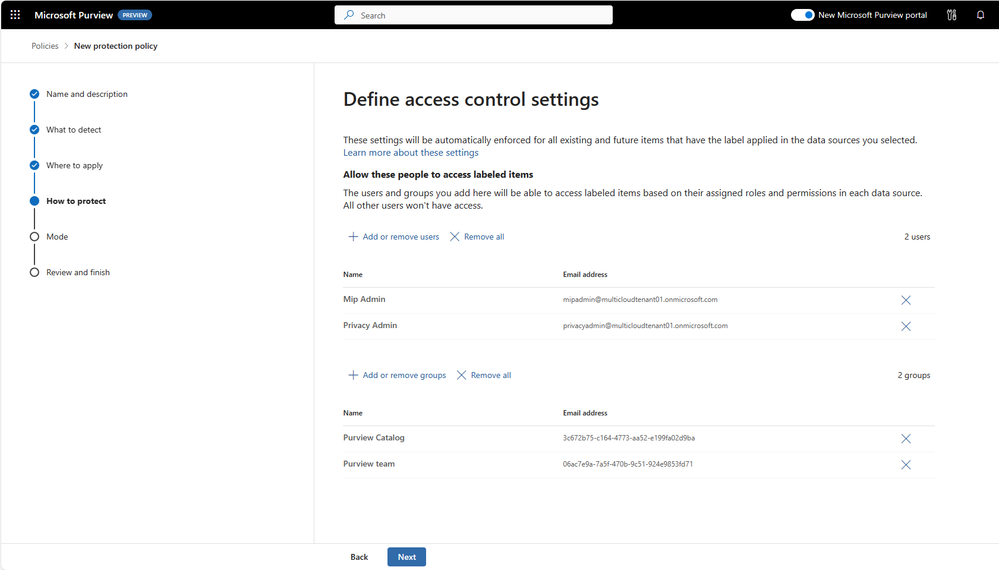
Enhance user risk signals in Insider Risk Management.
A comprehensive data security strategy requires more than just knowing and classifying the data. People access and interact with data, and insider risks often come from trusted users who have permission to sensitive data and may deliberately or accidentally do risky things. This can result in possible data security incidents, such as data theft, data leakage, or data damage. Microsoft Purview has improved its Insider Risk Management solution to easily ingest, process, and link events from cloud sources like Microsoft Fabric, Azure, AWS, Box, Dropbox, and Google Drive, providing ready-made indicators to detect potential data theft and data leak activities that may cause data security incidents across the data estate.
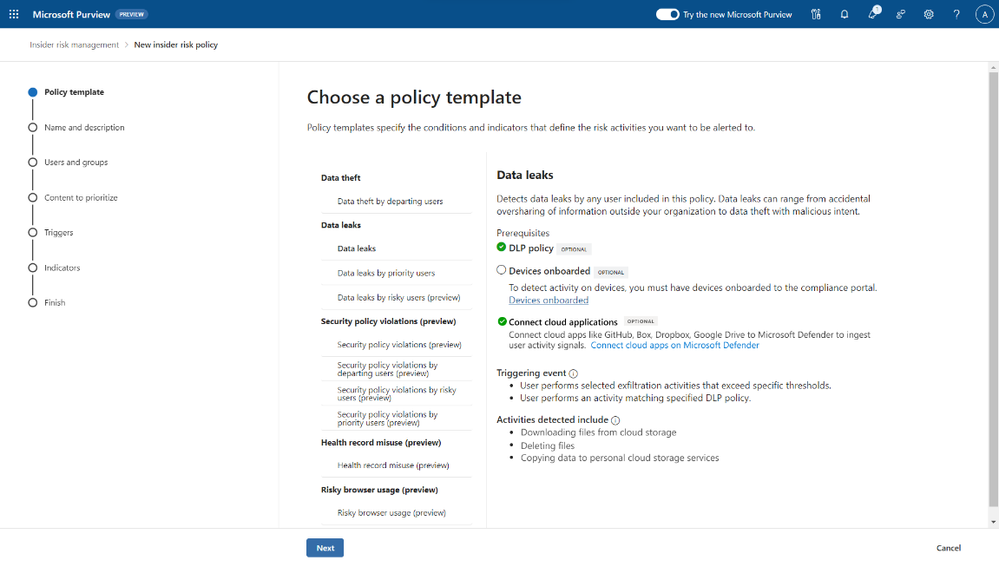
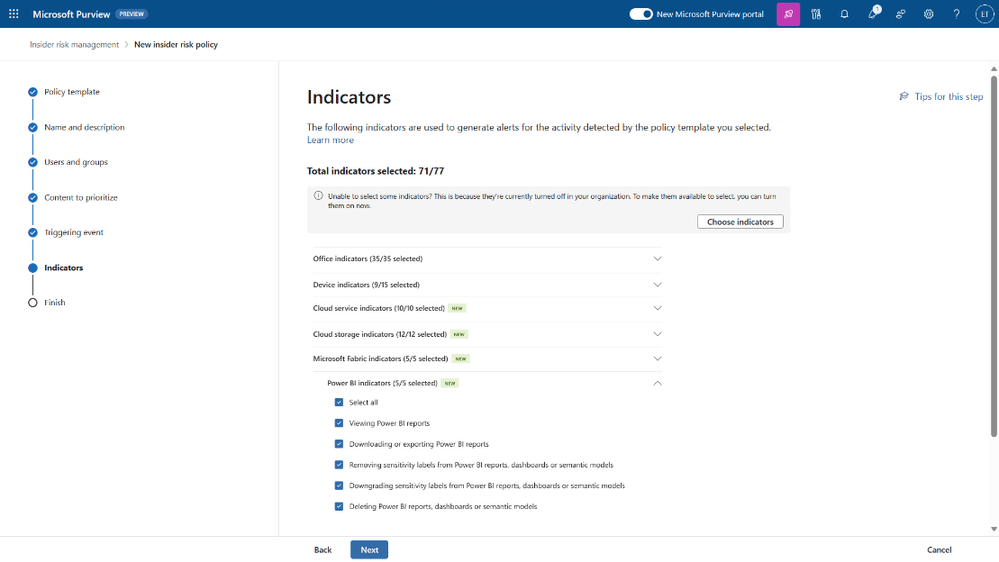
As people use various applications and cloud services in their daily work, security teams need to understand the risks related to these user activities that may lead to possible data security incidents. For example, customers can receive an alert if a user increases their privileges to manage all subscriptions in Azure, then removes Power BI reports that have sensitivity labels applied, and modifies the network access settings of storage accounts and blobs. All these insights are combined into a single alert, enabling analysts to speed up the review and response process.
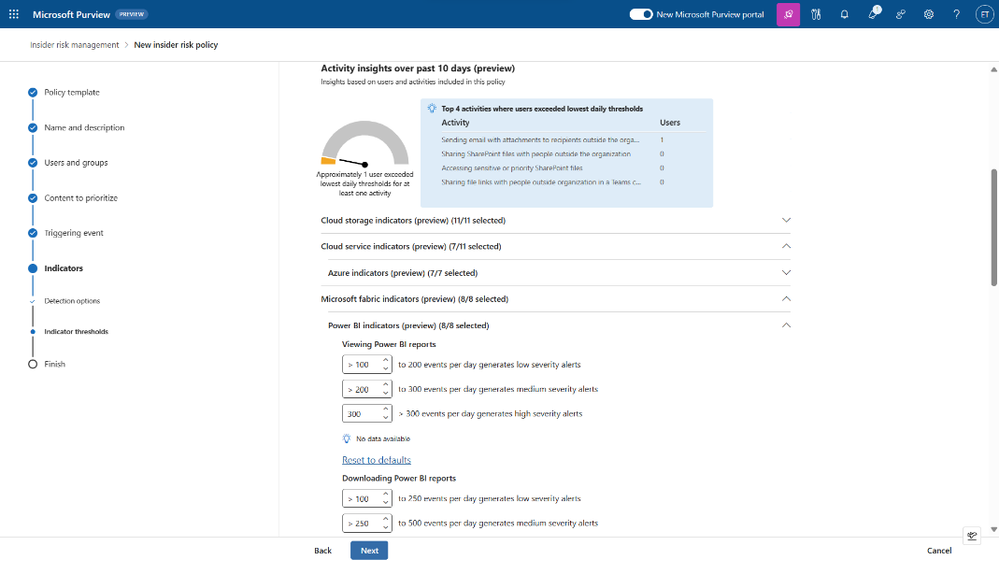
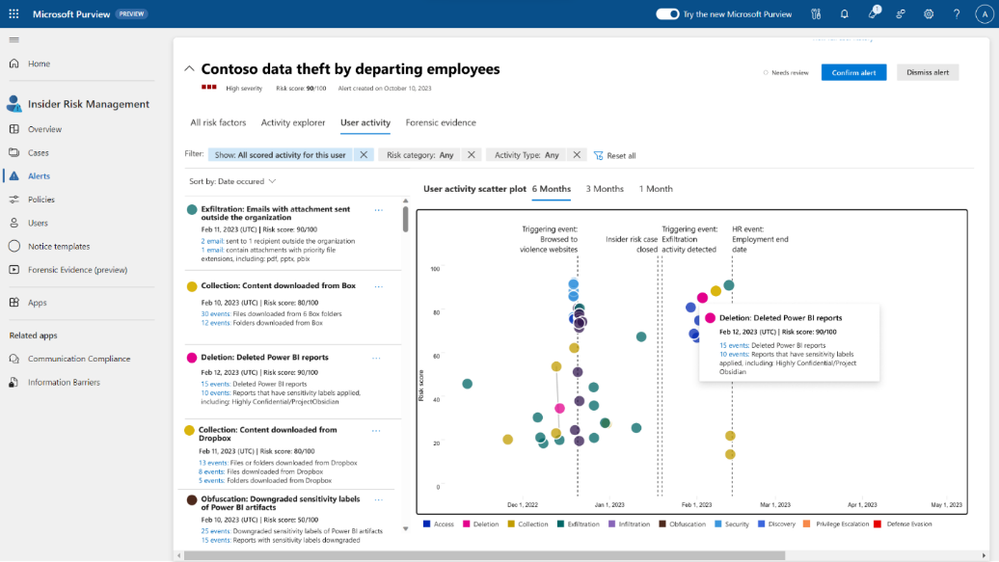
In the next few months, we will continue to add more data sources and capabilities across our Microsoft Purview stack. If you want to learn more about Purview and how it can help you protect and govern your data estate, check out our resources below and stay tuned for more!
Learn more:
- Read our announcements: https://aka.ms/PurviewFabricConference/Blog
- Microsoft Mechanics video – https://aka.ms/Purview+Fabric/video
- Microsoft Mechanics Ignite video - https://www.youtube.com/watch?v=fBW-_6vz2uI
- Download Microsoft Data Security Index report to learn more about the trends and best practices for an effective data security program.
- See how Microsoft Purview solutions are designed to help detect and respond to a corporate espionage incident.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.