- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Learn how to investigate Microsoft Purview Data Loss Prevention alerts in Microsoft Sentinel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This is a step-by-step guided walkthrough of the Microsoft Sentinel experience for Microsoft Purview Data Loss Prevention (DLP) incident management. This is based on the open-source connector that can be found here Learn how to install the open source connector to investigate Microsoft Purview Data Loss Preventio....
Prerequisites
- License requirements for Microsoft Purview Information Protection depend on the scenarios and features you use. To understand your licensing requirements and options for Microsoft Purview Information Protection, see the Information Protection sections from Microsoft 365 guidance for security & compliance and the related PDF download for feature-level licensing requirements.
- Before you start, turn on alerts for all your DLP policies in the Microsoft Purview compliance portal and enable the integration with Microsoft Sentinel following the steps outlined in this blog post.
- permissions to the analysts to access the Microsoft Sentinel workspace where the DLP data is being processed.
Step-by-step guided walkthrough
In this guide, we will provide the most common operations carried out by a DLP analyst using Microsoft Sentinel as the incident management tool. This guide is specific to open source integration, you can also integrate using the Microsoft 365 Defender connector. The Microsoft 365 Defender connector will transfer both security and DLP events to the workspace, it will not include organizational enrichment or data matches. The connector will enable many of the abilities presented in this guide.
- Go to https://portal.azure.com to access the Microsoft Sentinel experience.
- Select Microsoft Sentinel
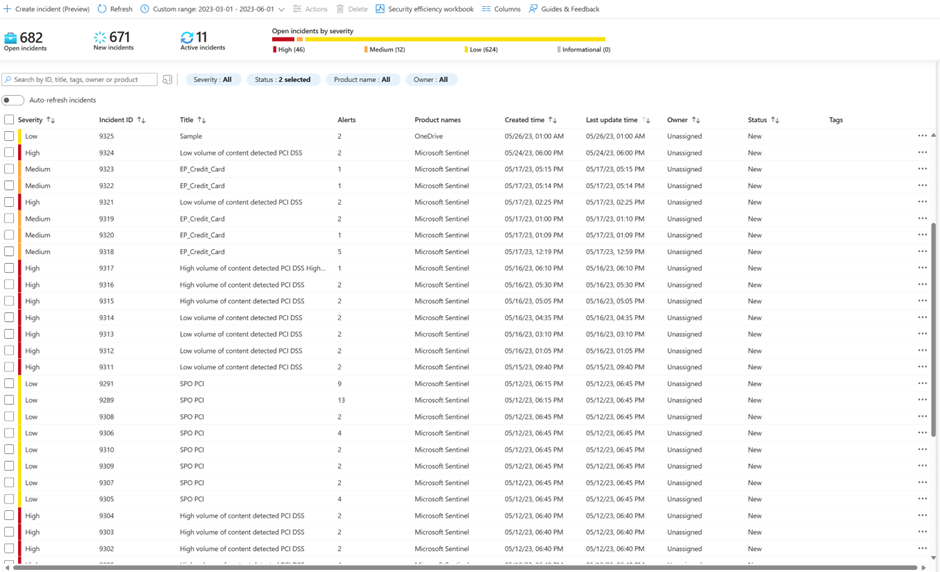
- Select Incidents on the left navigation pane and click on Incidents to view the Incidents queue
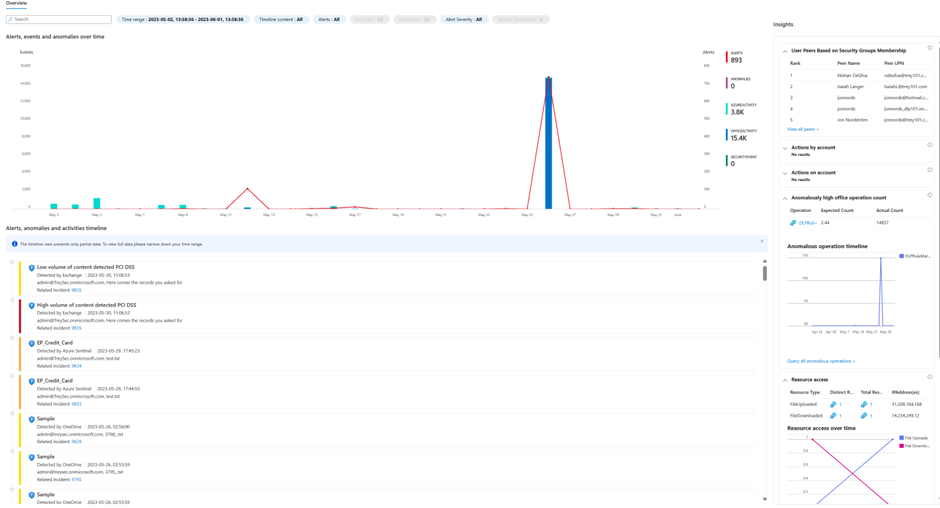
- The queue can be filtered by the Severity, Status, Product Name and Owner of the incident. The queue can also be search based on the entities in the alerts. In Microsoft Sentinel it is possible to create your own custom workbook that allows you to create your own custom incident workbook that allows you to create your own custom filters.
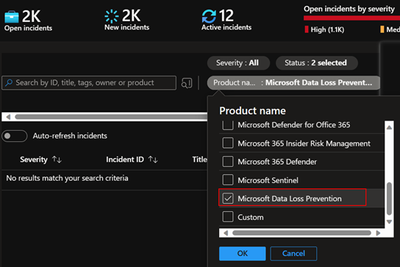
4.1 If you are using the Microsoft 365 Defender integration you can filter to only DLP incidents by selecting product.
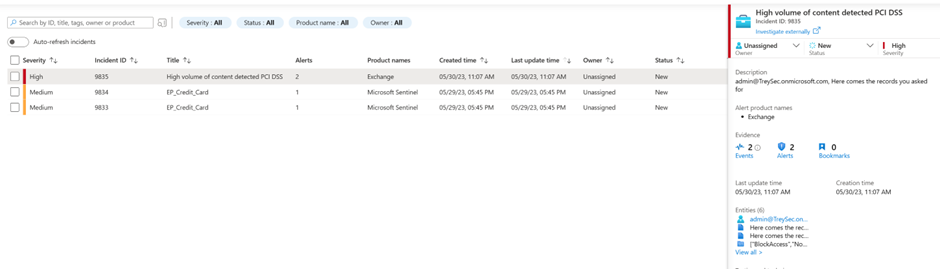
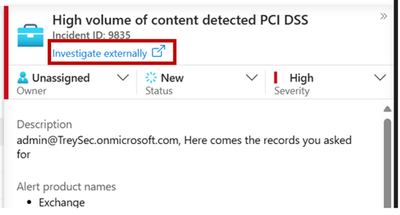
- Select a specific incident to view the incident summary details.
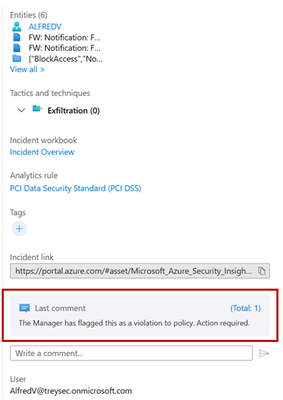
- In the preview of the incident you can set status, assign ownership, severity and add tags if necessary.
- Scroll down in the preview to see additional high level detail of the incident including a sample of what matched the rule. The fields are fully customizable, Manager, JobTitle, Department or other key detail that matters to you can be added.
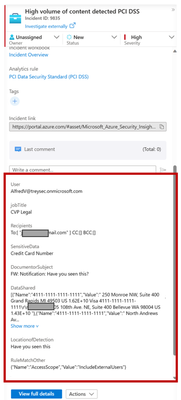
- To view the full Microsoft detail and allow you to download content click this link
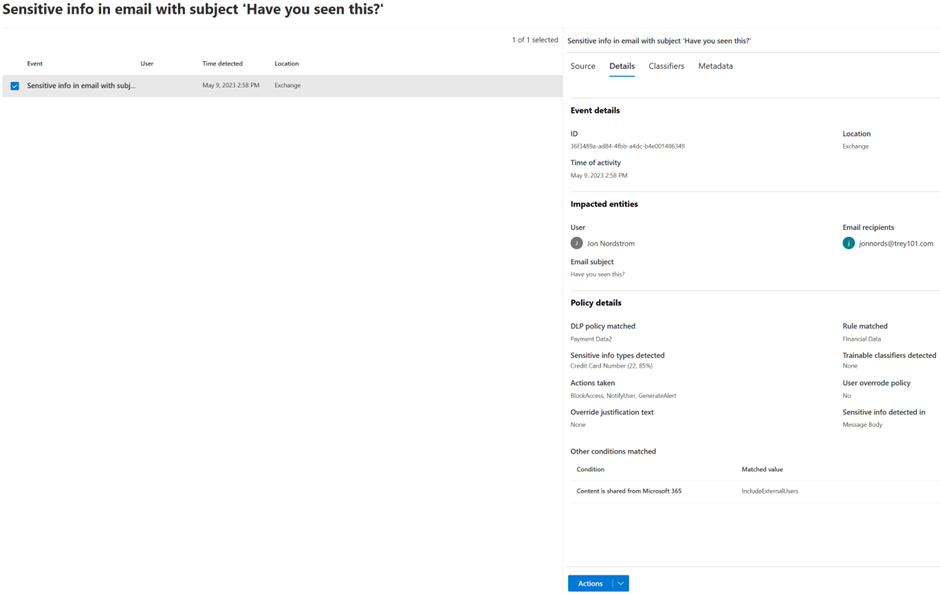
- This will expand the Microsoft Purview compliance portal investigation experience. Where you can see document details, source content as well as the ability to download the content. Note it does not expand the incident experience.
- Click on the Source tab to view the e-mail body so that the surrounding text of the match can be identified. Note: To access the Content preview feature and the Matched sensitive content and context feature, you must have the required permission (see details here).
If the content is in an attachment or you need to get the full e-mail use the Download email action. If you determine that the match was a false positive, select “Not a match”.
For remediation actions on files on SharePoint Online or One Drive for Business sites, you can see actions like
- Apply retention label
- Apply sensitivity label
- Unshare file
- Delete
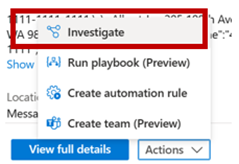
- To get a better understanding of the overall behaviour of the user and any related threats use the investigate view to drill in to actions and devices.
- If you need more information about an entity in the match and you have User and Entity behaviour analytics enabled you can click on the entity. This will provide you with behavioural data across the workloads.
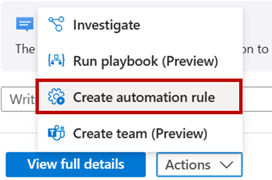
- If you want to see the full incident with all details select view full details
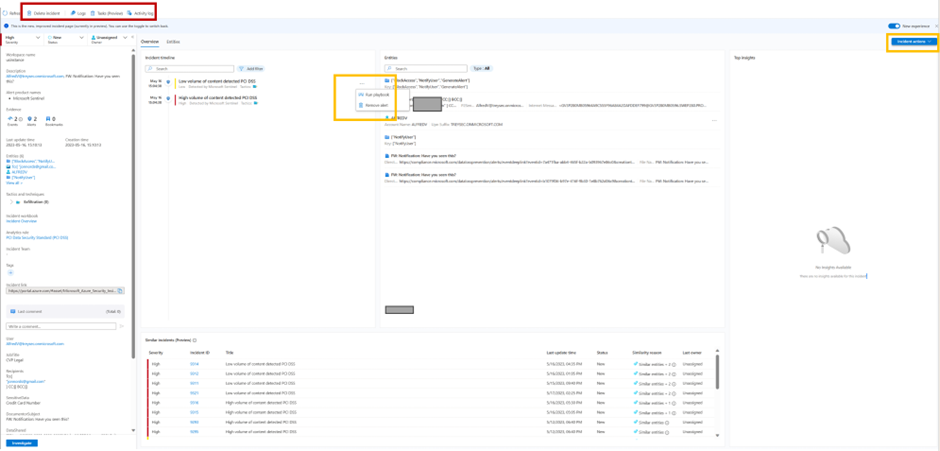
- In the full details experience there are several options available.
- In the red box
- You can delete the incident if required
- You can stat logs and it will allow you to do advanced queries without having to switch context
- Tasks allows you to use a run book for the tasks the analyst are going to carry out.
- The yellow boxes
- You can select to run play books on individual alerts like highlighted in the middle yellow box.
- You can also run Playbooks and automation on the entire incident see the yellow box in the right hand corner.
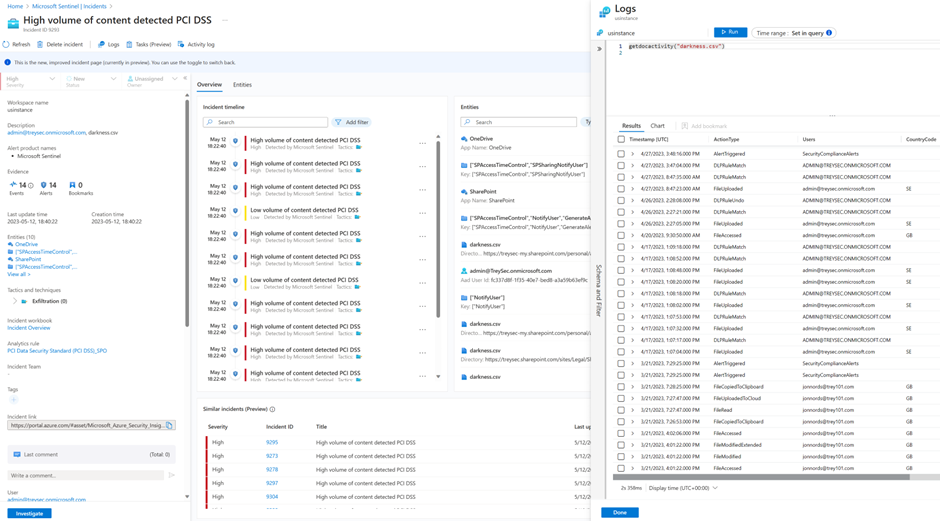
- In the red box
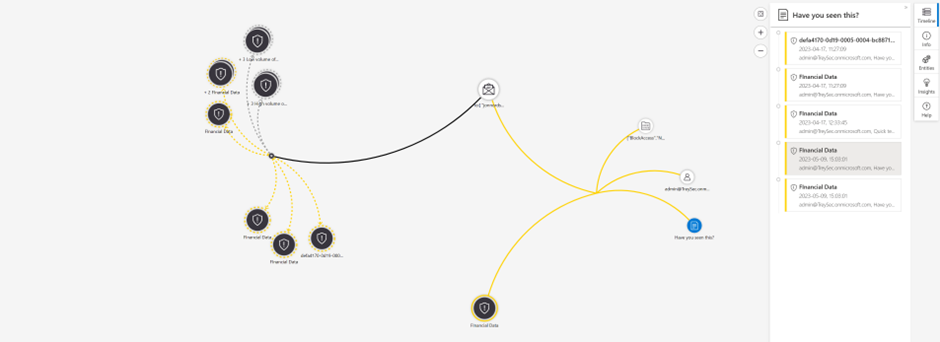
- This is an example of running a query without switching. In this example a function called getdocactivity is used. Microsoft Sentinel functions is something that you can create as a template for your queries.
- In this example, we are initiating a Microsoft Sentinel Playbook based on an alert in the incident. The Playbooks are based on Logic Apps and you can create your own Logic apps to fit your purpose.
- The Manager receives an e-mail that can be customized based on your needs.
b. If the manager reports the use, the ticket in Microsoft Sentinel is updated with a comment calling the analyst to action. This can kickstart other automation like escalating to an investigation and associated run book.
- If you have very noisy incidents that you still want to keep for tracking. As an example you may want to keep DLP Incidents where the e-mail was blocked, but you don’t need to manually triage the incident.
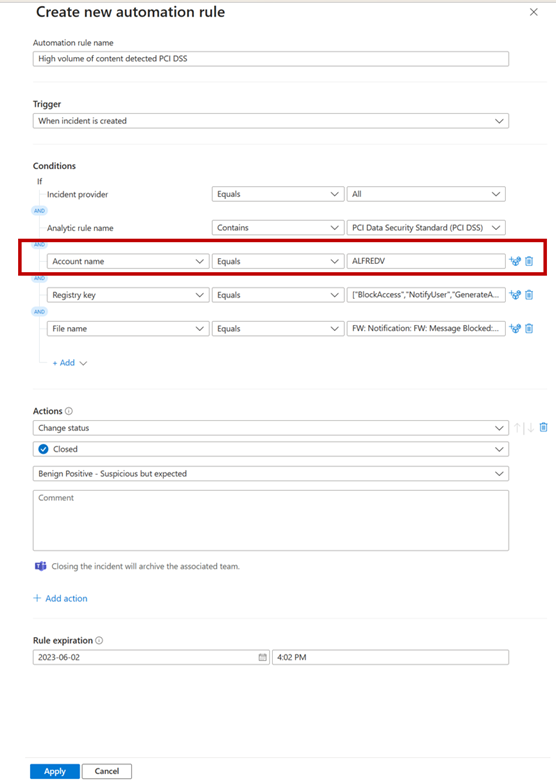
- With the incident selected, select Create new automation rule
- This will bring up this page where the suggested values pre-populated. It is enough to remove the Account name as an example to have a more general automation rule that can automatically close incidents.
- At the end of the review of the incident you can select to apply additional details like the appropriate custom incident tags, comments, actions that should be taken on the case, or resolve the incident.
- In many scenarios bulk actions are needed for ease of managing multiple incidents. Select multiple incidents and click on Manage incidents to take bulk actions on all of the selected incidents at once. Bulk actions include assign to, classification, addition of incident tags, status
Microsoft Sentinel Reporting
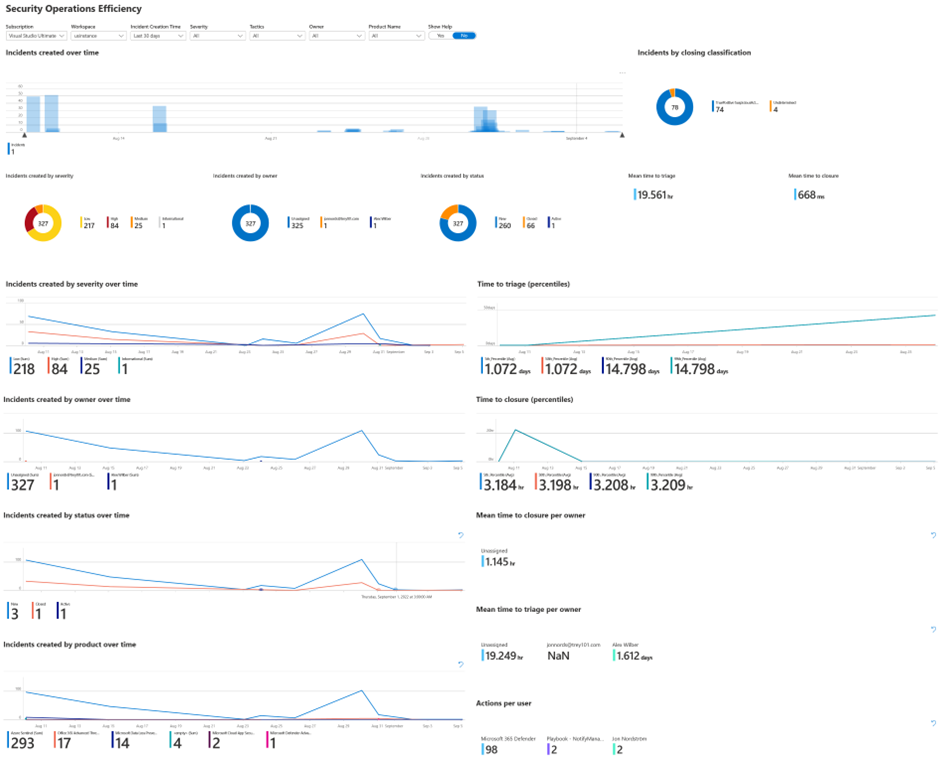
In this section, we will provide guidance on how to use the Workbooks. One of the built-in reports is called the SOC efficiency workbook it works for both Microsoft 365 Defender events and the open-source connector. It contains a holistic view of how analysts have processed incidents, the tags used, the time to triage, etc it can easily be amended based on custom requirements.
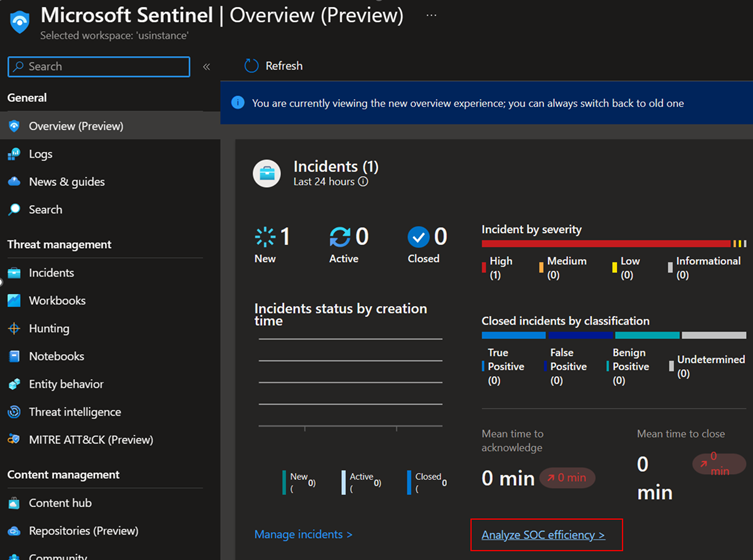
- To get to the workbook click Analyze SOC efficiency on the Microsoft Sentinel Overview page
- It will lead you to the following report.
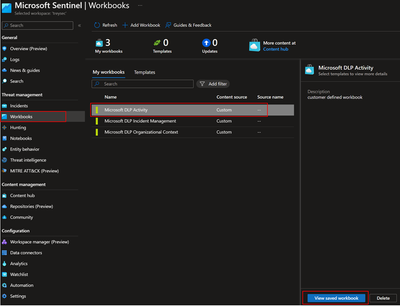
3. With the open source code we are including a few sample reports that can be used as a starting point. To see the reports click Workbooks, select the workbook to view and click View saved workbook.
A. This example shows trends for Exchange Online and Teams. It provides indications of overrides and other details. It includes a sample of a graph that can be used to identify what is standing out visually.
B. With the enrichment that can be done either by using a Watchlist or by the built-in enrichment in the open source code you can also get an organizational view of the incidents. The sample below shows violations per department.
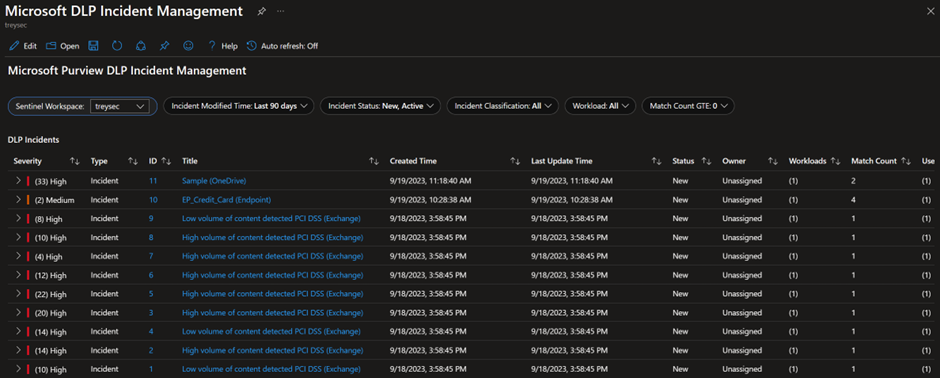
C. There is also an additional workbook that allows for custom filtering of incidents on top of what is available out of the box.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.