- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Introducing Microsoft Security Exposure Management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In an era of expanding interconnected attack surfaces, organizations face a growing concern about a myriad of exposures, including software vulnerabilities, control misconfigurations, overprivileged access, and evolving threats leading to sensitive data exposure.
Navigating, and, more importantly, understanding this threat landscape and where you may be exposed can be extremely difficult, costly, and complex.
Therefore, it's important for you to increase visibility across your digital estate so that you can not only identify potential threats, but also take proactive measures to prevent them. With typical organizations using on average 80 different security tools, it’s very likely that you have dozens of tools related to security posture, each managing a limited scope of your environment.
The security posture data and insights in these tools are often siloed, or at best, loosely integrated, making it difficult to reason over threats and their possible impact to critical assets.
Microsoft is leading the next chapter of attack surface management so organizations can proactively improve their posture and reduce their exposure, faster than attackers are able to exploit them.
Today, March 13, we are thrilled to announce the public preview release of Microsoft Security Exposure Management. This transformative solution unifies disparate data silos, extending end-to-end visibility to security teams across all assets. By enabling a thorough assessment of security posture and exposure, this solution equips teams to not only grasp their current security landscape but also elevate it to new heights. Microsoft Security Exposure Management serves as a cornerstone for proactive risk management, empowering organizations to adeptly navigate and mitigate threat exposure across their entire attack surface.
Microsoft Security Exposure Management empowers customers to:
- Build an effective exposure management program with a continuous threat exposure management (CTEM) process.
- Reduce risk with a clear view of every asset and real-time assessment of potential exposures both inside-out and outside-in.
- Identify and classify critical assets, ensuring they are protected against a wide variety of threats.
- Discover and visualize potential adversary intrusion paths, including lateral movement, to proactively identify and stop attacker activity.
- Communicate exposure risk to business leaders and stakeholders with clear KPIs and actionable insights.
- Enhance exposure analysis and remediation by integrating with third-party data sources and tools
At launch, we are introducing new capabilities that are foundational to exposure management programs:
- Attack Surface Management: Provides a comprehensive view of the entire attack surface, allowing the exploration of assets and their relationships.
- Attack Path Analysis: Assists security teams in visualizing and prioritizing attack paths and risks across environments, enabling focused remediation efforts to reduce exposure and breach likelihood.
- Unified Exposure Insights: Provides decision-makers with a consolidated, clear view of an organization's threat exposure, facilitating security teams in addressing critical questions about security posture.
Visibility into the entire attack surface
Powered by our Enterprise Exposure Graph, Microsoft Security Exposure Management assists you in uncovering and overseeing your attack surface. Through seamless integration with both Microsoft and non-Microsoft security and infrastructure tools, it diligently collects and normalizes asset data, maps assets and their relationships, and delivers comprehensive visibility into the attack surface. This holistic approach enables the identification, prioritization, and remediation of critical exposures with precision and efficiency.
At present, Microsoft Security Exposure Management seamlessly integrates data across the following technologies:
- Vulnerability Management (VRM)
- Microsoft Defender Vulnerability Management (MDVM)
- Qualys Vulnerability Management (Preview)
- Rapid7 Vulnerability Management (Preview)
- External Attack Surface Management (EASM)
-
Microsoft Defender External Attack Surface Management
-
- Cloud Security (CSPM)
- Microsoft Defender Cloud Security Posture Management (CSPM)
- Endpoint Security (Device Security Posture)
- Microsoft Defender for Endpoint (MDE)
- Identity Security (ISPM)
- Microsoft Defender for Identity (MDI)
- Microsoft Entra ID (Free, P1, P2)
- SaaS Security Posture (SSPM)
- Microsoft Defender for Cloud Apps (MDA) including connectors to SaaS applications
- Email Security
- Microsoft Defender for Office (MDO)
- OT/IOT Security
- Microsoft Defender for IOT
- Asset & Configuration Management
- ServiceNow CMDB (Preview)
In our commitment to offering the most comprehensive exposure coverage, our future plans encompass extensive integration with a variety of additional Microsoft and non-Microsoft solutions, spanning diverse domains.
Exploring the attack surface
To navigate the attack surface, Exposure Management provides both an intuitive interactive graphic exploration and a robust, fully flexible data query experience. The attack surface visualization map enables security teams to understand asset relationships, identify the blast radius of threatened assets, and pinpoint weaknesses further in the sequence. For enhanced flexibility in accessing and comprehending asset exposure, Graph data is seamlessly integrated within Advanced Hunting tables. This allows users to create and execute powerful KQL queries, facilitating the integration of graph data with all other available Microsoft Defender data in Advanced Hunting.
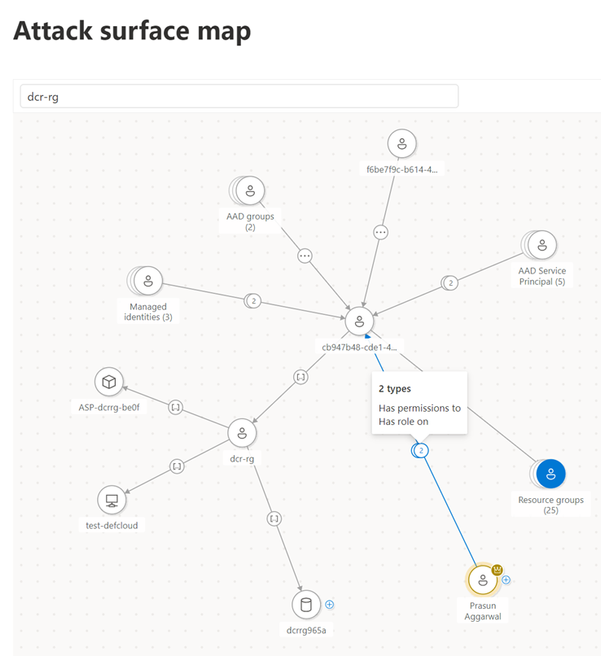
Mapping and identifying critical assets
Safeguarding an organization's critical assets is of paramount importance in the realm of attack surface management. These key assets often represent the core pillars of an enterprise, encompassing sensitive data, proprietary information, and essential systems. By meticulously mapping and identifying these critical components, businesses gain a profound understanding of their attack surface, enabling strategic fortification against potential threats. Focusing protective measures on these high-priority assets ensures a targeted and efficient security approach, minimizing the risk of breaches and disruptions. Effectively protecting critical assets not only safeguards sensitive information but also fortifies the overall resilience of the organization, fostering a proactive security stance in an ever-evolving threat landscape.
To tackle this challenge, we are unveiling the Critical Asset Management capability. This new capability automatically discerns assets critically from an attacker's viewpoint and assigns them a crucial security context.
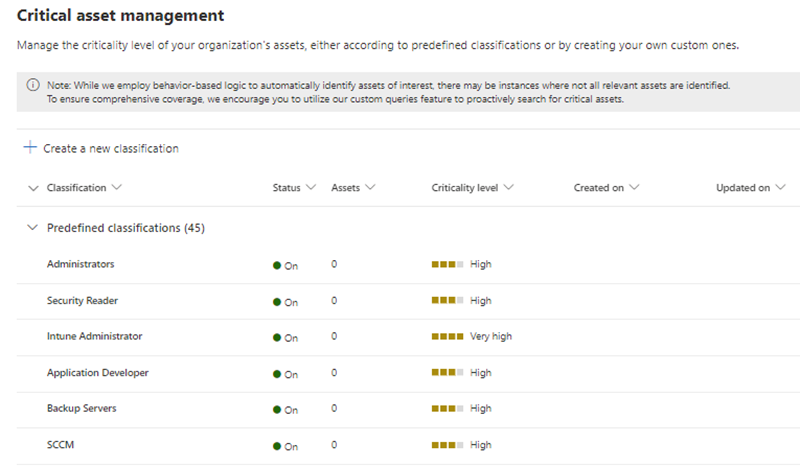
Critical Asset Management automatically identifies and labels various critical assets throughout your organization, encompassing entities such as DCs (Domain Controllers), ADFS servers, and more. Moving forward, our commitment extends to continually enhancing this capability by expanding the list of identified critical asset types. Additionally, we provide the flexibility for you to create your own classifications based on critical asset criteria, utilizing all the context from exposure graph.
The critical asset criteria is valuable not just within Exposure Management but other Defender products like Defender for Cloud are also enhanced by incorporating level of criticality on assets in evaluating risks and providing recommendations. Learn more about the updates in Defender for Cloud.
Extending attack path analysis across the entire attack surface
To strengthen the defense of your critical assets, we're introducing an advanced Extended Attack Path Analysis component. This feature provides a comprehensive attacker perspective, outlining the potential steps adversaries may take to infiltrate your critical assets. Specifically, it identifies paths originating from possible attack entry points, such as vulnerable internet-facing devices, and traces their course toward critical assets where lateral movement becomes feasible. By mapping these potential routes, the analysis sheds light on vulnerabilities and attack vectors that attackers may exploit, enabling a focused approach to fortify these critical pathways and bolster overall security measures.
Moreover, given that Attack Path data is accessible in Advanced Hunting, customers can seamlessly correlate it with all other data points. This integration enhances the depth of analysis, allowing for a more comprehensive understanding and proactive response to potential security threats.
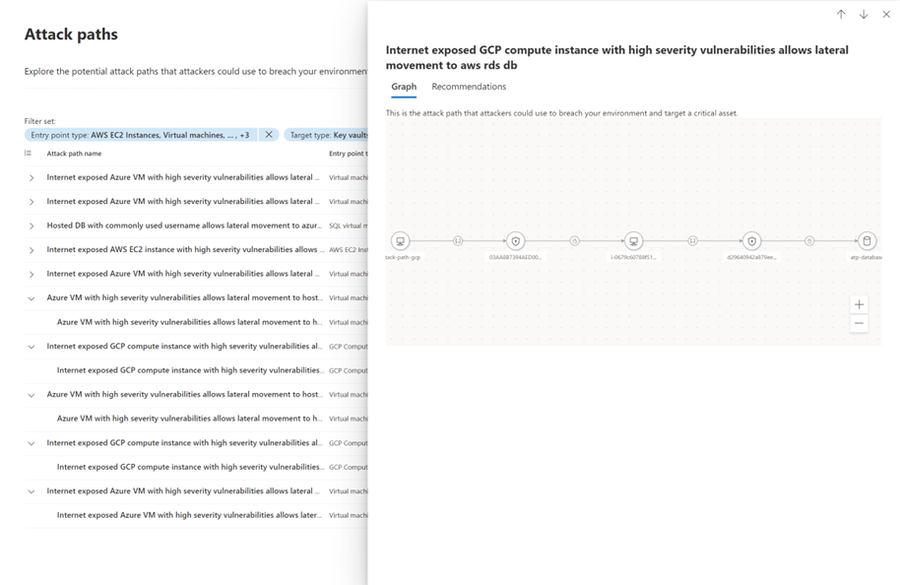
Empowered by this new capability, you can now:
- Visualize attack paths to your critical assets across on-premises and the cloud, mirroring an actual attack scenario.
- Map potential routes that threat actors might pursue to exploit vulnerabilities.
- Unlock a range of new use-cases, including enhanced vulnerability prioritization, guided penetration testing, as well as improved threat modeling and incident response.
Communicating and optimizing your security posture
With Microsoft Security Exposure Management, organizations can seamlessly transform technical data into business insights and actionable intelligence crucial for both business decision-makers and practitioners. This real-time translation of cyber risk addresses stakeholders' pivotal cybersecurity inquiries, such as "How secure are we?", "What are the risks?", "How are we progressing over time?", and "What do we need to remediate first to reduce exposure from a given threat?" This is achieved by providing clear metrics to measure, compare, and easily communicate cyber risk.
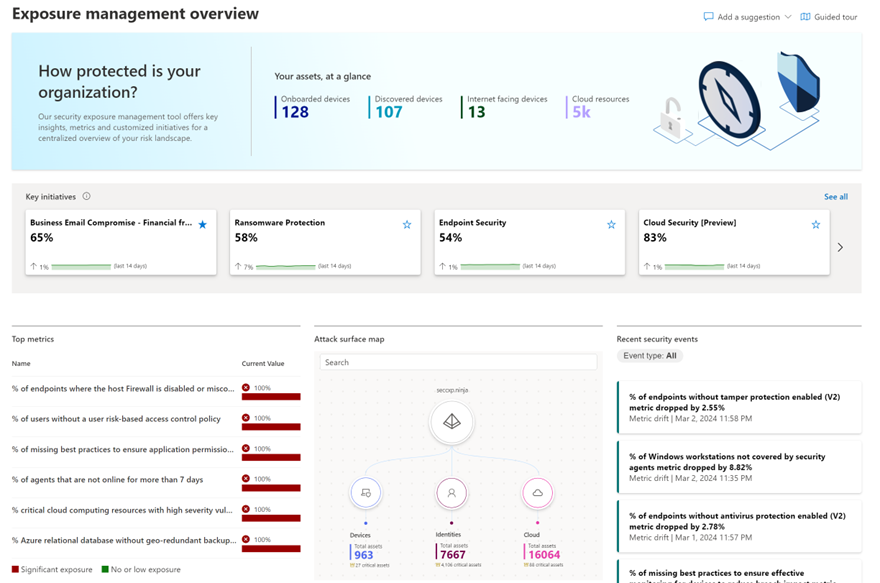
To steer you and your security teams toward adopting a continuous threat exposure management mindset, we introduce "Security Initiatives." Through these initiatives, you can strategically define your attack surface and focus teams on aspects crucial to the business. This involves the discovery, prioritization, and validation of security findings, empowering teams to recognize and effectively communicate with all stakeholders for remediation and measurement purposes.
Within the initiative catalog, you'll find an expanding list of security programs critical for teams to govern, enhance, and report on. These initiatives are divided into two types - Domain Initiatives, addressing areas like improving cloud security, maturing zero-trust practices, external attack surface and securing SaaS applications; and Threat Initiatives, concentrating on specific attack actors like Octo Tempest and vectors such as Ransomware and Business Email Compromise.
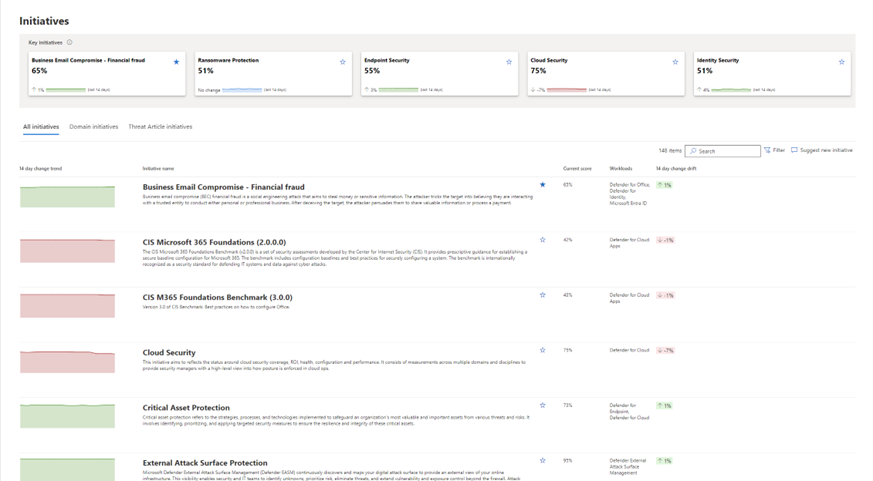
Within each initiative, you'll discover real-time security metrics meticulously curated by our experts. Additionally, there are specific security recommendations aimed at guiding efforts to enhance the maturity of the program, along with insights into security events that impact the score. This functionality empowers you to closely monitor the program's progress over time.
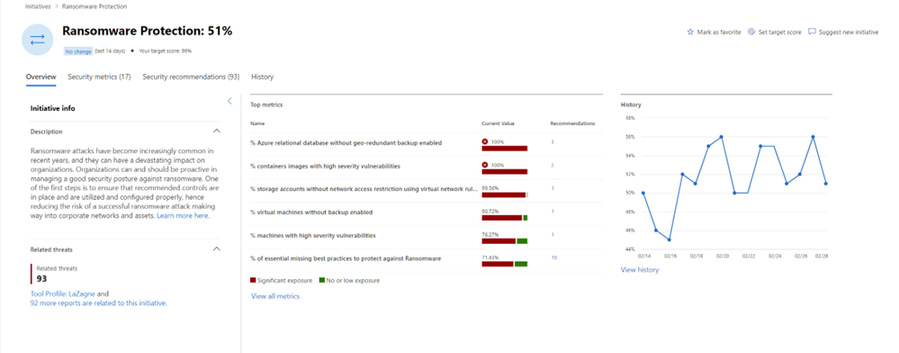
Security drift is an unavoidable consequence within the ever-changing realm of business technology. Rapid advancements in threat activity demand regular tuning and adjustments to controls to adequately address emerging risks.
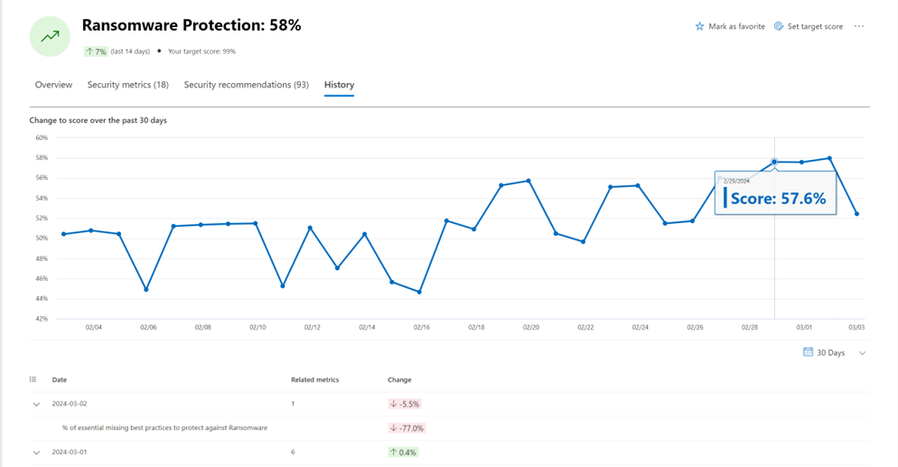
To proactively monitor shifts in security posture, Exposure Management provides an event timeline section in the dashboard, and a history tab on each security initiative. This empowers you to identify and address significant exposures that have developed over time, ensuring a vigilant approach to prioritizing and enhancing overall cybersecurity measures.
Learn More
Achieving robust attack surface visibility and understanding posture are imperative in effectively managing threat exposure. Microsoft Security Exposure Management provides the essential tools and insights needed for proactive cybersecurity measures. It is not just a choice; it's a strategic move towards fortifying your organization's defenses in the face of evolving threats. Dive into a new era of cybersecurity resilience by getting started today.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.