- Home
- Security, Compliance, and Identity
- Security, Compliance, and Identity Blog
- Harnessing Advanced Audit to power your forensic investigations in 5 steps
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
It is estimated that over 300 million people are now working remotely1, and Forrester predicts remote work will permanently increase by 300% from pre-pandemic levels2.
Unfortunately, attackers continue to direct ransomware and phishing attacks at organizations, and this has only increased with remote work, as users access critical and sensitive data from outside the corporate firewalls. Additionally, organizations may face significant regulatory fines if they are unable to efficiently determine what data was compromised.
Advanced Audit can help organizations scope data compromise and respond to regulatory obligations by providing access to audit events that are important for forensic investigations, and by extending audit log retention for up to a year.
Here’s 5 steps to quickly get started with Advanced Audit within Microsoft 365 compliance center out of the box.
Be prepared:
1. Manage and configure audit log retention policies
Ponemon Institute reported in the 2020 Cost of a Data Breach study that it takes on average 280 days to identify and contain a breach3. Advanced Audit supports on-going investigations and investigations into historical activity by retaining audit log data for key workloads like Exchange, SharePoint, and Azure Active Directory for up to one year by default. That includes audit events such as SharePoint File Accessed, Exchange Messages Sent, User Searches in Exchange and SharePoint, and many others that can support a breach analysis. For workloads that are not enabled by default, such as Power BI, you can manually extend audit log events to one year in Advanced Audit. Review the full list of Microsoft 365 services that have audit events to support your forensic investigations here.
For regulatory obligations that require audit logs to be retained for longer periods of time, organizations can optionally retain audit log records for up to 10 years by adding on the 10-year Audit Log Retention license to Advanced Audit.
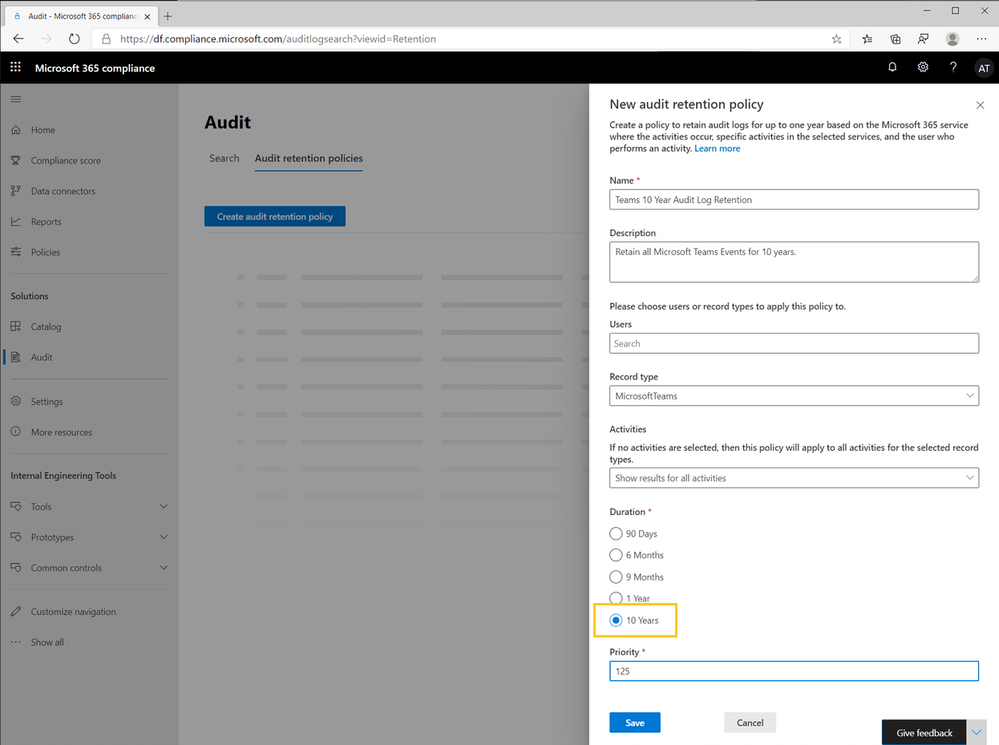
To help manage the policies in place in your organization, we are announcing the Audit retention policies tab which provides a dashboard to view, edit, and delete audit retention policies. In the Audit retention tab, you can also validate your retention policy configuration to make sure you are retaining the Audit activities you want for as long as you need them. Learn more about how to manage audit retention policies and view the policies in the dashboard.

Know what to do when a data breach is detected:
2. Use search patterns to scope and assess attackers’ intention
Once it’s clear which user accounts were compromised, use search patterns as a way to scope the data breach and assess an attacker’s intentions by gaining insight into what searches were performed by the attacker using the compromised users’ accounts. For example, you can learn if the attacker was looking for IP, PII data, trade secrets, or even conducting reconnaissance.
To understand search patterns in Advanced Audit, specify the compromised user and date range of the attack, and filter for specific search activity events in Exchange or SharePoint. View which mail items or files they tried to find (and possibly accessed) through the search bar in Outlook (web, mobile, desktop) or in SharePoint sites (home, communication sites, and Microsoft Teams sites). Learn more about how to use the search query events in Advanced Audit here.
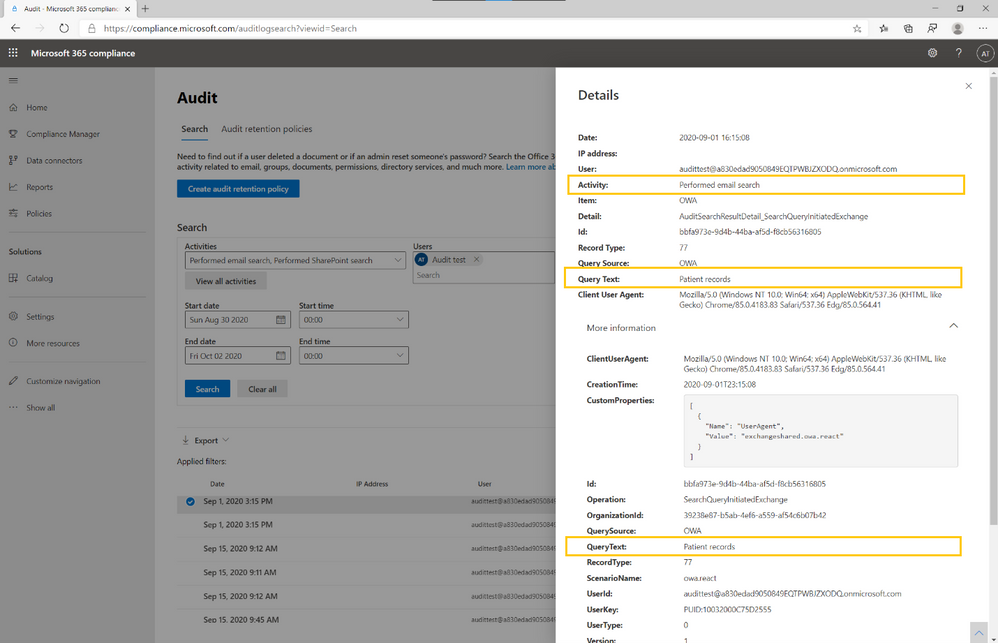
3. Further check to understand what potentially sensitive email data was accessed
The MailItemsAccessed event can help investigators identify data breaches and determine the extent of emails that may have been compromised. The details of this event provide important information, such as the date and time the item was accessed, and the IP address it was accessed from. These details can help you determine whether the access was legitimate or coming from a suspicious IP range.
Also, since it is common that an attacker may access a mailbox at the same time as the mailbox owner, you will need to differentiate between the two using audit record properties that define the context of the access. To learn more, read how you can use the MailItemsAccessed mailbox auditing action to investigate compromised accoun....

4. Check to see if sensitive information was forwarded to an external mailbox
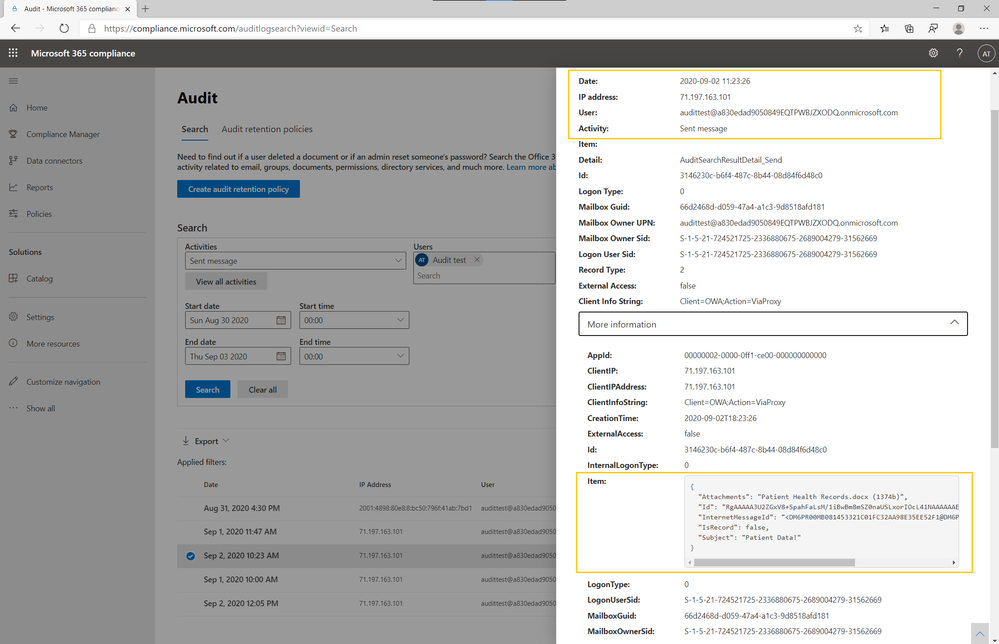
Often attackers will exfiltrate sensitive information to an external account. In Advanced Audit, you can identify emails sent from a potentially compromised account using the mail send event, even if an attacker deletes the sent message from the Sent Items folder to hide their tracks.
The mail send event is triggered when a user sends, replies to, or forwards an email message. When you search for the mail send event, in the details logged for the event you can find the InternetMessageId, subject line, and names and sizes of attachments (if they exist).
5. Export audit signals and share with other investigators, analysts or legal teams
Finally, you can export audit log data and pass the evidence over to the relevant teams for further action, such as your legal team to respond to regulatory compliance obligations, or external forensic investigators for further analysis. Either way, you have provided evidence that can help your organization take swift action or respond to regulatory requirements related to data breach to help minimize the financial and reputational cost to the organization.
Advanced Audit is one of many capabilities that can help your organization respond to a data breach. For additional and more comprehensive view of how to respond to a data breach, you can also read our recent post on the Microsoft Security blog
Get started today!
You can try this out in Advanced Audit Today.
- Sign up for a Microsoft 365 E5 trial
- Go to the Microsoft 365 compliance center to get started
- Watch Ignite skilling videos to see these features in action
- Access the Interactive Guide
References:
1https://www.bcg.com/publications/2020/covid-remote-work-cyber-security
2 Employee Experience In 2021: Remote Work Flourishes ... For Some (forrester.com)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.