- Home
- Security, Compliance, and Identity
- Microsoft Sentinel
- Fortinet Integration with Sentinel
Fortinet Integration with Sentinel
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 07 2023 07:54 PM
I am trying to integrate the Fortinet firewall to sentinel. I've followed the Data Connector page steps to set up the Linux VM by installing the CEF collector. Also, the configuration at firewall is performed.
Both Linux VM(syslog) and Firewall are on Azure Cloud only.
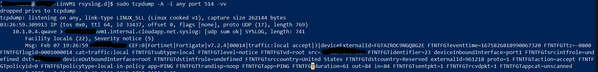
when i run the tcpdump command, I can see the logs from firewall to the Linux machine:
Post locating the syslog directory, I am getting an error as below:
Checking daemon incoming connection for tcp and udp
This will take 60 seconds.
sudo tcpdump -A -ni any port 25226 -vv
Could not locate "CEF" message in tcpdump
Simulating mock data which you can find in your workspace
This will take 60 seconds.
sudo tcpdump -A -ni any port 25226 -vv
Could not locate "CEF" message in tcpdump
Please make sure that traffic to the syslog daemon on port 514 and to the OMS agent on port 25226 are enabled on the internal firewall of the machine
When I run the validation command given in the Data Connector page, I see the below output:
[user@LinVM1 rsyslog.d]$ sudo wget -O cef_troubleshoot.py https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/CEF/cef_troubleshoot.py... python3 cef_troubleshoot.py 0b78f928-d0ee-454e-a004-10039e95fbc8
--2023-02-08 03:39:17-- https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/CEF/cef_troubleshoot.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.109.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 40148 (39K) [text/plain]
Saving to: ‘cef_troubleshoot.py’
cef_troubleshoot.py 100%[====================================================================================================>] 39.21K --.-KB/s in 0.002s
2023-02-08 03:39:17 (18.7 MB/s) - ‘cef_troubleshoot.py’ saved [40148/40148]
Note this script should be run in elevated privileges
Please validate you are sending CEF messages to agent machine.
Trying to use the 'locate' command to locate omsagent
Located 'omsagent'
Located security_events.conf
Validating /etc/opt/microsoft/omsagent/0b78f928-d0ee-454e-a004-10039e95fbc8/conf/omsagent.d/security_events.conf content.
Current content of the daemon configuration is:
<source>
type syslog
port 25226
bind 127.0.0.1
protocol_type tcp
tag oms.security
format /(?<time>(?:\w+ +){2,3}(?:\d+:){2}\d+|\d{4}-\d{2}-\d{2}T\d{2}:\d{2}:\d{2}.[\w\-\:\+]{3,12}):?\s*(?:(?<host>[^: ]+) ?:?)?\s*(?<ident>.*CEF.+?(?=0\|)|%ASA[0-9\-]{8,10})\s*:?(?<message>0\|.*|.*)/
<parse>
message_format auto
</parse>
</source>
<filter oms.security.**>
type filter_syslog_security
</filter>
Omsagent event configuration content is valid
File permissions valid
omsagent security configuration supports Cisco ASA parsing
OMS Agent syslog field mapping is correct
Checking if firewalld is installed.
systemctl status firewalld
Warning: you have a firewall running on your linux machine this can prevent communication between the syslog daemon and the omsagent.
Checking if firewall has exception for omsagent port [25226]
Found exception in the firewalld for the omsagent port.[25226]
Checking if security enhanced linux is enabled
getenforce
['root 135065 1 0 03:10 ? 00:00:05 /usr/sbin/rsyslogd -n']
Found rsyslog process running on this machine.
Checking rsyslog daemon:
Testing if the daemon configuration folder exists
Located /etc/rsyslog.d directory.
Checking omsagent configuration under the name of: 'security-config-omsagent.conf'
Located security-config-omsagent.conf
rsyslog daemon found, checking daemon configuration content - forwarding all data to port 514
Trying to validate the content of daemon configuration.
For extra verification please make sure the configuration content is as defined in the documentation.
/etc/rsyslog.d/security-config-omsagent.conf
Current content of the daemon configuration is:
if $rawmsg contains "CEF:" or $rawmsg contains "Fortigate-" or $rawmsg contains "ASA-" then @@127.0.0.1:25226
rsyslog daemon configuration was found valid.
Trying to restart syslog daemon
Restarting rsyslog daemon - 'sudo service rsyslog restart'
Redirecting to /bin/systemctl restart rsyslog.service
rsyslog daemon restarted.
This will take a few seconds.
Omsagent restarted.
This will take a few seconds.
Incoming port grep: 0.0.0.0:514
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN
udp 0 0 0.0.0.0:514 0.0.0.0:*
Daemon incoming port 514 is open
Incoming port grep: 25226
unix 2 [ ACC ] STREAM LISTENING 25226 /var/run/lsm/ipc/sim
Omsagent is listening to incoming port 25226
Validating CEF\ASA into rsyslog daemon - port 514
This will take 60 seconds.
sudo tcpdump -A -ni any port 514 -vv
b'tcpdump: listening on any, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes\n'
b'03:39:56.847938 IP (tos 0x0, ttl 64, id 8437, offset 0, flags [none], proto UDP (17), length 739)\n'
b' 10.1.0.4.qwave > 10.0.1.4.syslog: [udp sum ok] SYSLOG, length: 711\n'
b'\tFacility local6 (22), Severity notice (5)\n'
Received CEF\ASA message in daemon incoming port.[514]
Notice: To tcp dump manually execute the following command - 'tcpdump -A -ni any port 514 -vv'
Fetching CEF messages from daemon files.
Taking 2 snapshots in 5 seconds diff and compering the amount of CEF messages.
If found increasing CEF messages daemon is receiving CEF messages.
Validating the CEF\ASA logs are received and are in the correct format when received by syslog daemon
sudo tac /var/log/syslog
Located 0
CEF\ASA messages
Validating the CEF\ASA logs are received and are in the correct format when received by syslog daemon
sudo tac /var/log/syslog
Located 0
CEF\ASA messages
Error: no CEF messages received by the daemon.
Please validate that you do send CEF messages to agent.
Checking daemon incoming connection for tcp and udp
This will take 60 seconds.
sudo tcpdump -A -ni any port 25226 -vv
Could not locate "CEF" message in tcpdump
Simulating mock data which you can find in your workspace
This will take 60 seconds.
sudo tcpdump -A -ni any port 25226 -vv
Could not locate "CEF" message in tcpdump
Please make sure that traffic to the syslog daemon on port 514 and to the OMS agent on port 25226 are enabled on the internal firewall of the machine
No auto sync with the portal
Validating that the OMI vulnerability patch is installed.
Protected from OMI vulnerability, patch is installed.
['root 138310 1 0 03:39 ? 00:00:00 /usr/sbin/rsyslogd -n']
Found rsyslogd process running on this machine.
[]
Notice: syslog-ng is not running but found configuration directory for it.
Warning: please make sure your logging daemon configuration does not store unnecessary logs. This may cause a full disk on your machine, which will disrupt the function of the oms agent installed. For more information:
https://www.rsyslog.com/doc/master/configuration/actions.html
Completed troubleshooting.
Please check Log Analytics to see if your logs are arriving. All events streamed from these appliances appear in raw form in Log Analytics under CommonSecurityLog type
Notice: If no logs appear in workspace try looking at omsagent logs:
tail -f /var/opt/microsoft/omsagent/0b78f928-d0ee-454e-a004-10039e95fbc8/log/omsagent.log
Warning: Make sure that the logs you send comply with RFC 5424.
Kindly help here to fix the issue. Do let me know if any more info is required.
Thanks. Much appreciated.
- Labels:
-
Integration
-
SIEM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 13 2023 05:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 13 2023 05:29 AM
However, I was facing this issue on RedHat Linux machine(syslog). When I tested this on Ubuntu platform, it worked successfully. Not sure what is the issue on RedHat Linux platform.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 13 2023 10:26 AM
It works pretty smoothly with Ubuntu.
Did you check the oms configuration in RedHat? Was the Fortinet facility (local7) allowed there?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 17 2023 03:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 17 2023 11:59 PM - edited Feb 18 2023 12:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 18 2023 11:38 PM
Not sure if someone has also come across this issue ?