- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Automate tasks management to protect your organization against threats
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
When investigating an incident, analysts follow certain steps – tasks – to ensure that the investigation is conducted effectively and efficiently. Standardizing the process is necessary for both generic steps and specific types of incidents, and their availability in the context of the incident allows for faster and more efficient management and remediation.
Tasks in Microsoft Sentinel can help security analysts streamline their workflow and improve their efficiency. Analysts can add tasks to specific incidents or alerts, enabling them to track the progress of investigations and remediation activities. While tasks can be added manually from within the Sentinel console, playbooks, and automation rules can be used to automatically create tasks based on certain conditions. Today we’re happy to announce the release of new playbooks, a workbook, and Log Analytics logs as well as an update to the SOC Process Framework. Along with a new integration with Microsoft 365 Defender SecOps playbooks, this will allow even more efficiency in managing incidents and the SOC’s tasks, with out-of-the-box content delivered by our security experts.
New playbooks with tasks for BEC, Ransomware, and Phishing investigation
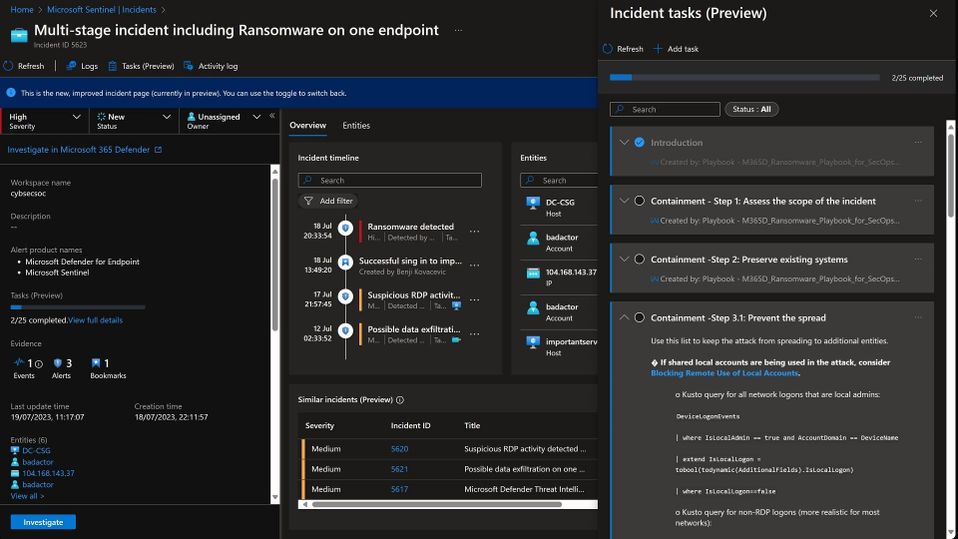
Handling complex incidents can be a long, challenging task that requires lots of expertise in different fields. Microsoft 365 Defender SecOps workflows offer security analysts a detailed guided response playbook for investigating and responding to security incidents, including Phishing, Ransomware, and BEC. Developed by some of the world's top security researchers and backed by Microsoft's extensive experience in threat detection and response, these workflows provide unparalleled security value, significantly bolstering an organization's defenses.. And now, with dedicated playbooks in Sentinel, these workflows can be easily transformed into tasks. Simply deploy the phishing, BEC, and ransomware playbooks in your workspace and apply them to the corresponding incidents. By integrating Defender workflows with Sentinel tasks, security teams can enjoy a more structured and efficient workflow, enabling them to respond to threats with greater speed and accuracy. The playbooks are now published in the "SOAR essentials" solution in Content Hub and are ready for use by your SOC.
New workbook to manage tasks in the SOC
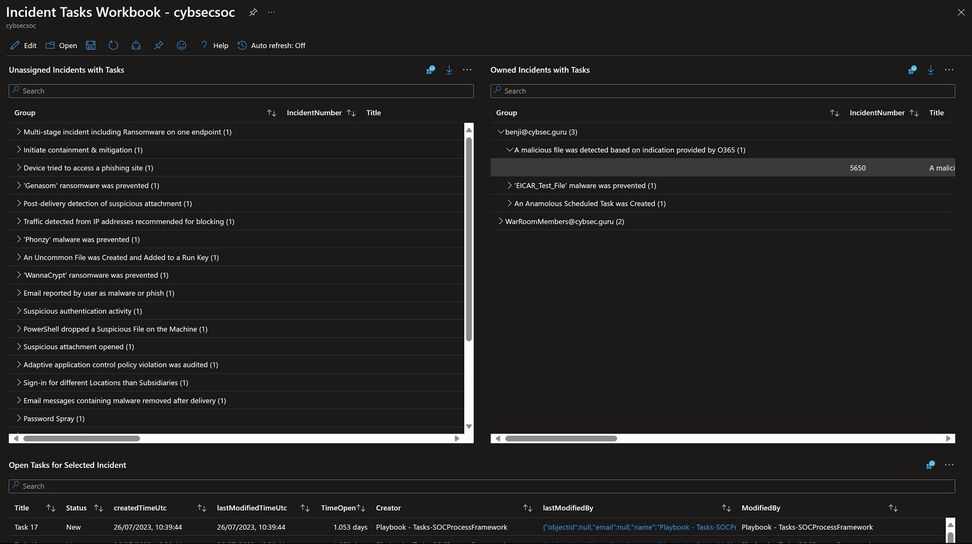
Now that tasks are integrated into the SOC’s incidents, the new tasks workbook offers a way for security teams to analyze task progress and completion, providing a comprehensive overview of all the tasks that exist in the Sentinel workspace. This is particularly important for SOC managers, as it allows them to easily monitor and manage the security workflow of their team. With a centralized view of all tasks, managers can quickly identify any bottlenecks or areas for improvement, including tasks that take the longest to complete. Additionally, a dashboard that shows tasks per incident/incidents and owner can help managers gain greater visibility into the workload of their team and allows analysts to manage their tasks in a timely and organized manner. The new Workbook allows toggling between those perspectives. The Workbook is now published in the "SOAR essentials" solution in Content hub.
The new workbook is based on new information in Log Analytics’ SecurityIncident table. Please refer to Appendix 2 for documentation of the new tasks fields.
Tasks details in SecurityIncident table
Task details in Log Analytics can be used as dashboards to monitor task progress, investigate security incidents, and track compliance and auditing activities. The tasks details include the task name and status, task number, last completed time (in case the task was modified after it was closed), and more. If you wish to explore the new task details in the SecurityIncident table, please refer to documentation and some recommended queries provided in Appendix 2 at the end of this blog post.
Updates to the SOC Process Framework
The SOC Process Framework solution, which can be found in Content Hub, is also updated to support Tasks. With the new version, instead of writing tasks into incident comments, the SOC Process Framework will create tasks defined in the watchlist into Microsoft Sentinel Incident Tasks. As a reminder, the SOC Process Framework Solution is designed to easily integrate with Microsoft Sentinel and establish a standard SOC Process and Procedure Framework within your organization, including incident or alert tasks.
Summary
Automating task management in Microsoft Sentinel using playbooks and automation rules can help security analysts streamline their workflow and improve efficiency. Integrating Microsoft Defender workflows with Sentinel tasks provides security teams with a more structured and effective way to investigate and respond to security incidents, significantly improving an organization's security posture. Additionally, Workbooks offer valuable insights into task progress and completion, enabling security teams to monitor their workflow and identify areas for improvement. The new SecurityIncident audits allow for full flexibility in querying tasks details and integrating them into more of the SOC’s tools.
Appendix 1: Tasks resources
Use tasks to manage incidents in Microsoft Sentinel | Microsoft Learn
What’s new: Incident tasks - Microsoft Community Hub
Appendix 2: suggested queries using the new tasks details
For documentation on managing tasks using Log Analytics: Audit and track changes to incident tasks in Microsoft Sentinel
SOC analysts open tasks per incident:
SecurityIncident
| where Owner.userPrincipalName == “<upn>”
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where status !in ('Completed', 'Deleted')
| order by lastModifiedTimeUtc desc
| project IncidentNumber, Title, Description, Severity, TaskTitle = ['title'], TaskStatus = ['status'], createdTimeUtc, lastModifiedTimeUtc, TaskCreator = ['createdBy'].name, lastModifiedBy, ModifiedBy = ['lastModifiedBy'].name
| order by IncidentNumber desc
Check deleted Tasks:
SecurityIncident
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where status == 'Deleted'
| project TaskTitle = ['title'], TaskStatus = ['status'], createdTimeUtc, lastModifiedTimeUtc = column_ifexists("lastModifiedTimeUtc", datetime(null)), TaskCreator = ['createdBy'].name, lastModifiedBy, TaskCloser = ['lastModifiedBy'].name, IncidentNumber, IncidentOwner = Owner.userPrincipalName
| order by lastModifiedTimeUtc desc
To check Tasks that are re-opened:
SecurityIncident
| where IncidentNumber == 553
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where lastCompletedTimeUtc < lastModifiedTimeUtc
| project TaskTitle = ['title'], TaskStatus = ['status'], createdTimeUtc, lastModifiedTimeUtc = column_ifexists("lastModifiedTimeUtc", datetime(null)), TaskCreator = ['createdBy'].name, lastModifiedBy, TaskCloser = ['lastModifiedBy'].name, IncidentNumber, IncidentOwner = Owner.userPrincipalName
| order by lastModifiedTimeUtc desc
Check Tasks that are not completed but incident is closed:
SecurityIncident
| summarize arg_max(TimeGenerated, *) by IncidentNumber
| where Status == 'Closed'
| mv-expand Tasks
| evaluate bag_unpack(Tasks)
| summarize arg_max(lastModifiedTimeUtc, *) by taskId
| where status !in ('Completed', 'Deleted')
| project TaskTitle = ['title'], TaskStatus = ['status'], createdTimeUtc, lastModifiedTimeUtc = column_ifexists("lastModifiedTimeUtc", datetime(null)), TaskCreator = ['createdBy'].name, lastModifiedBy, IncidentNumber, IncidentOwner = Owner.userPrincipalName
| order by lastModifiedTimeUtc desc
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.