- Home
- Security, Compliance, and Identity
- Microsoft Security Experts Blog
- Follow the Breadcrumbs with Microsoft IR & MDI: Working Together to Fight Identity-based Attacks
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In cybersecurity incidents, one of the first goals of any Threat Actor is to gain credentials and elevate their privileges. For this reason, they will almost always target user identities and the underlying identity infrastructure. This blog post discusses how Microsoft Incident Response and Microsoft Defender for Identity (MDI) work together to fight identity-based attacks. We demonstrate how MDI can be used to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions. MDI is an identity security solution that monitors key identity systems—both on-premises and hybrid—to detect and help respond to identity-related threats. It provides valuable insight into suspicious activities and events, helping security teams take appropriate actions to protect their organization from identity-based threats. As a core element of the Security Strategy alerts and data from MDI are correlated with signals from across other security domains offering security teams more comprehensive visibility into the entirety of an attack.
For at the onset of many engagements, Microsoft Incident Response often uses identity-specific queries and tools that can also help your team proactively identify potential risks or investigate Threat Actor activities.
The queries below can all be executed within the Advanced Hunting page in Microsoft Defender XDR. They leverage the following tables which contain MDI data:
- IdentityDirectoryEvents – Contains a variety of directory change events in Active Directory, including alerts, group membership changes, and system events on the Domain Controllers.
- IdentityInfo – Contains information about identity objects from multiple identity sources.
- IdentityLogonEvents – Contains raw logon events captured by MDI and Microsoft Defender for Cloud Apps.
- IdentityQueryEvents – Any queries run against Active Directory are saved here.
These tables all contain 30 days’ worth of data, but can be connected to Sentinel or Microsoft Defender for Cloud Apps for longer retention.
Lateral Movement Paths (LMP)
Lateral movement path is defined as the steps an attacker takes to navigate your network and gain additional access to secure data. Lateral Movement Paths (LMPs) reporting is available for every identity tracked by Microsoft Defender for Identity and serves as a visual guide that can demonstrate routes from non-sensitive to sensitive accounts.
Microsoft Incident Response leans on these LMPs frequently via both Advanced Hunting and the visual guides to understand the potential scope of access for a compromised identity.
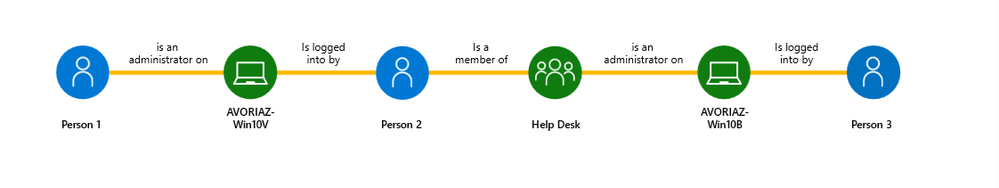
During an investigation, the following query can identify service accounts granted a high level of privileges, as well as the machines those accounts regularly logged into. This can help investigators rapidly identify and remediate Lateral Movement risks.
IdentityDirectoryEvents
| where ActionType == "Potential lateral movement path identified"
| project Timestamp, ActionType, Application, AccountName, AccountDomain, AccountSid, AccountDisplayName, DeviceName, AdditionalFields
Microsoft Defender for Identity continuously monitors your environment and alerts you to sensitive accounts with the riskiest lateral movement paths. This assists Microsoft Incident Response during engagements by providing insights into the customer’s attack surface. In scenarios where we engage after an incident, it’s more efficient to retrieve this information via query.
Group Membership Changes
Privileged groups can grant permissions in Active Directory and other applications, and allow access to resources such as SCCM administration, Domain Admins, and more. As a result, Threat Actors often add themselves to privileged groups to gain access to a resource that is useful to them.
The query below can be used to review group changes and track which accounts were added to which groups.
IdentityDirectoryEvents
| where Application == "Active Directory"
| where ActionType == "Group Membership changed"
| where DestinationDeviceName != ""
| extend ToGroup = tostring(parse_json(AdditionalFields).["TO.GROUP"])
| extend FromGroup = tostring(parse_json(AdditionalFields).["FROM.GROUP"])
| extend Action = iff(isempty(ToGroup), "Remove", "Add")
| extend GroupModified = iff(isempty(ToGroup), FromGroup, ToGroup)
| extend Target_Group = tostring(parse_json(AdditionalFields)["TARGET_OBJECT.GROUP"])
| project Timestamp, Action, GroupModified, Target_Account = TargetAccountDisplayName, Target_UPN = TargetAccountUpn, Target_Group, DC=DestinationDeviceName, Actor=AccountName, ActorDomain=AccountDomain, AdditionalFields

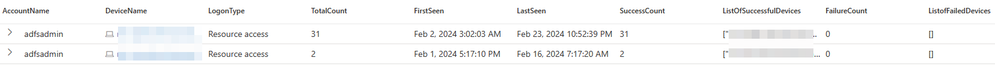
Account Login Review
When investigating a potential compromise, it can often be helpful to understand which devices or locations a user typically logged into, and which type of logon was used. Typically, the most interesting types of logon for an investigation are Interactive, Remote Interactive and Network. This information is useful in both proactive and reactive contexts since it can give an indication of the pattern of life of a user and helps identify anomalies.
IdentityLogonEvents
| where AccountName contains "adfsadmin"
| where Application == "Active Directory"
| summarize TotalCount=count(),FirstSeen=min(Timestamp),LastSeen=max(Timestamp),SuccessCount=countif(ActionType=="LogonSuccess"),ListOfSuccessfulDevices=make_set_if(DeviceName,ActionType=="LogonSuccess"),FailureCount=countif(ActionType=="LogonFailed"),ListofFailedDevices=make_set_if(DeviceName,ActionType=="LogonFailure") by AccountName,DeviceName,LogonType
Service Creation Review
Services are often used by threat actors as persistence mechanisms, allowing them to leave a running executable which will allow a Threat Actor to maintain long-term access to a compromised system. The query below will display service creation events on machines protected by MDI, allowing for review to ensure that all newly created services are expected. These systems should only be used for domain management and any atypical service creation should be investigated. It is a simple query, but an effective one in many cases.
IdentityDirectoryEvents
| where ActionType == 'Service creation'
| project Timestamp, Application, AccountName, AdditionalFields.ServiceName
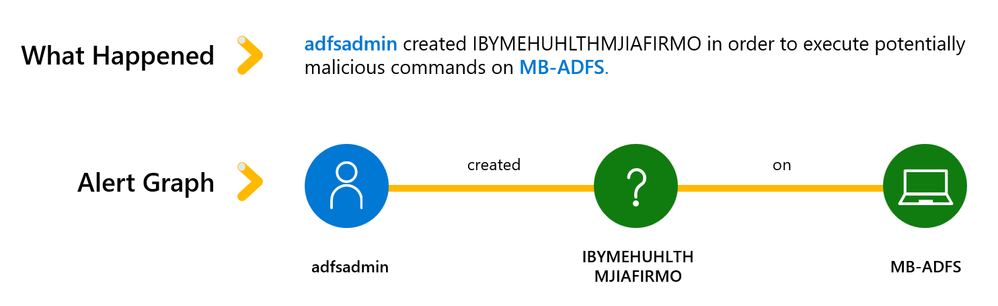 Figure 4: Example of a suspicious service being created
Figure 4: Example of a suspicious service being created
Honeytokens
Honeytokens are a type of deception technique used by defenders that can help detect and deter identity-based attacks (to see best practices, read this blog). They are accounts or credentials that are intentionally exposed to lure attackers who may try to use them to access sensitive resources or escalate their privileges. MDI can monitor and alert honeytoken activity, providing valuable insights into the Tactics, Techniques, and Procedures (TTPs) of a potential adversary.
During an incident response event, honeytokens can provide exceptional value to the defenders. Microsoft Incident Response has caught threat actors attempting to re-establish a foothold in an environment via honeytoken detection. For example, during a recent incident, this feature enabled the discovery of a web shell being used for persistence.
To tag an account as a honeytoken, follow the guidance here.
Reporting
MDI infuses identity-specific values into other elements of Microsoft's security suite. This includes Microsoft Secure Score, where MDI customers benefit from identity security posture assessments. These recommendations provide a set of data that help organizations monitor and analyze their security posture, giving valuable insights into the activity and behavior of users, devices, and resources within an organization. More information on the reporting capabilities of MDI can be found here.
- Identity security posture assessment: Provides an overview of the organization's identity security posture, including information about vulnerabilities, misconfigurations, and recommended actions to improve security.
- Lateral movement path report: Visualizes paths that a Threat Actor can use to move laterally across the environment to get access to sensitive accounts.
- Passwords exposed in cleartext: Provides information about potential password exposure when LDAP is being used without SSL.
- Modification to sensitive groups: Manipulation of administrative groups can be a sign of intrusion, and this report will detail instances of this activity.
These reports can all play a critical role in an investigation. They reveal details about the environment, and the lateral movement path report can often give insights as to how a Threat Actor obtained privileged credentials.
In conclusion, Microsoft Defender for Identity (MDI) offers deep insights into the identity plane. When combined with its integration capabilities with Microsoft Defender Endpoint, it empowers Microsoft Incident Response to monitor, disrupt, and analyze threat actor activity. Feel free to leverage the provided queries in your investigations or share your own insights in the comment section. MDI is a powerful tool for identifying, detecting, and investigating advanced threats, compromised identities, and malicious insider actions. Utilize MDI’s queries and tools proactively to identify risk areas and implement mitigations. Additionally, explore Lateral Movement Paths to understand the potential scope of access for compromised identities, and consider deploying honeytokens to detect and deter identity-based attacks.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.