Video Transcript:
-If you’re using SIMM or XDR solutions today to manage breaches after they’ve happened, today, I’ll show you what you can do to prevent incident and breaches before they happen with Microsoft’s new Security Exposure Management capabilities in Microsoft Defender, which not only helps you proactively assess your security posture, put the right defenses in place to mitigate threats and track your progress over time, but it also identifies attack entry points and even maps out potential attack paths, importantly, giving you visibility into the blast radius of critical choke points leading to multiple high-value assets, so that you can close them down before they get exploited.
-It addresses the complexity you might be facing today where your security perimeter and the vulnerability points across your infrastructure are continually expanding. From the network boundary with on-prem resources, the device endpoints connecting to it, anything from laptops, smartphones, or IoT devices and even new device types, the increasing number of cloud apps in use, distributed data stores, certificates and domains along with potentially multiple cloud infrastructures with multiple identity services.
-And then, of course, the introduction of less secure networks as people work remotely, as they access resources. At each layer of defense, you’re probably using dozens of security tools from multiple vendors to harden each part of your infrastructure against different attack vectors.
-These may be siloed or, at best, loosely integrated, making it difficult to find and prioritized security gaps. Where relevant, you might also prioritize software fixes to address CVEs and deploy them as soon as you can. In short, you’re having to make sense of and coordinate your threat exposure across these different tools, and this, in turn, can increase your risk. And that’s what Security Exposure Management will increasingly solve for.
-It unifies data and signals from the tools you’re using today, starting with solutions from Microsoft, and we’ll be adding additional connectors over time for non-Microsoft tools to proactively harden your security before attacks happen. Let me show you how this works, starting with knowing what you have in place to understand and quantify your attack surface exposure.
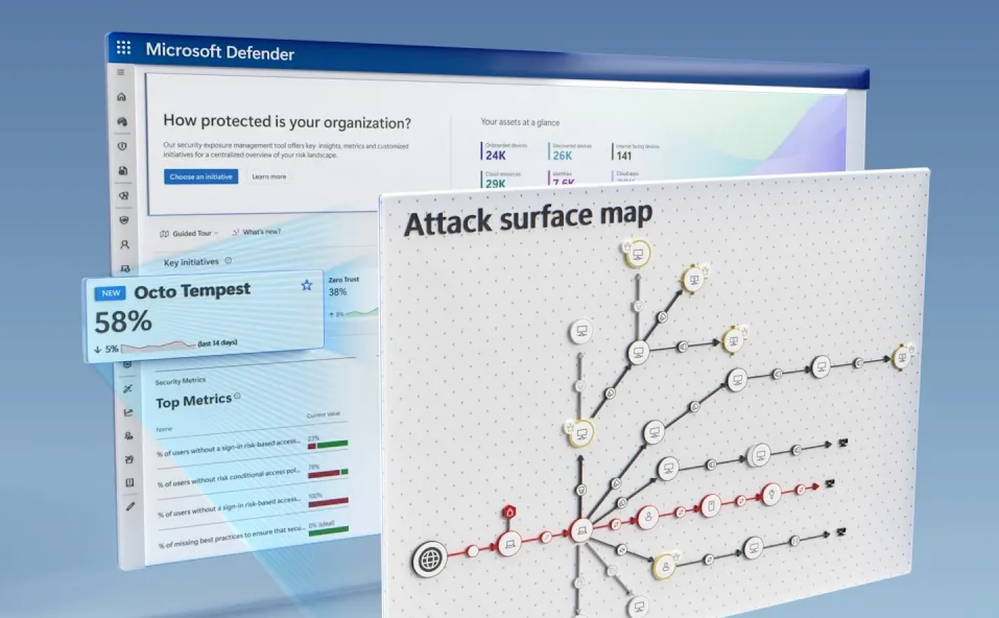
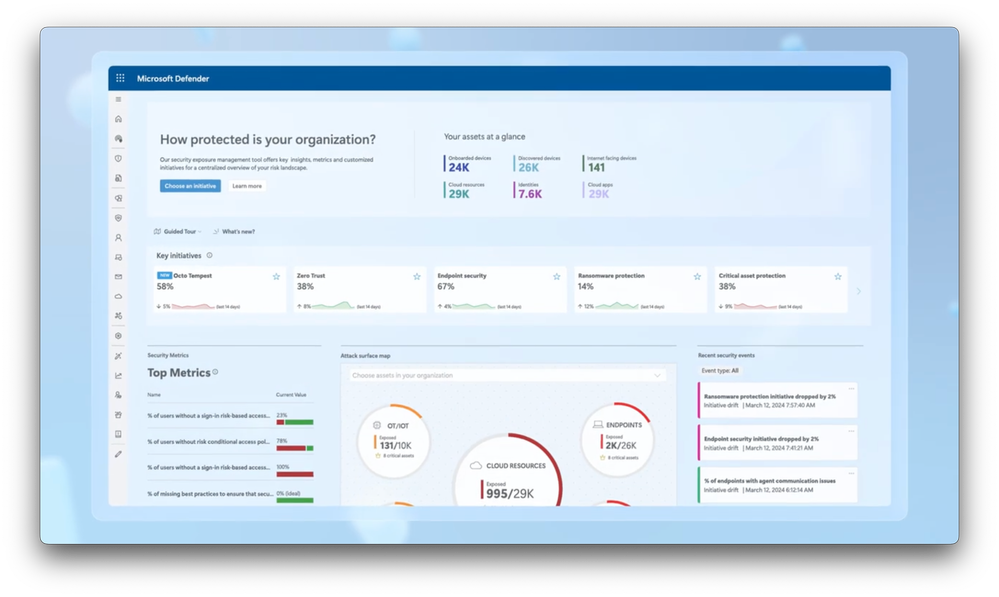
-This is the Security Exposure Management experience in the Microsoft Defender portal. I can see my assets at a glance with Onboarded, Discovered, Internet-facing devices, and Cloud resources and more. There are also key initiatives that your organization has selected to work on. I’ll dive into that more in a moment.
-Next, in Security Metrics, I see a few key data-driven indicators of specific high-value vulnerabilities and security controls and their current values against targets. We also show you the distribution of exposed asset types and their exposure levels as well as recent security events and changes that have occurred in your environment. So we give you a 360-degree view of your organization’s security posture in one place.
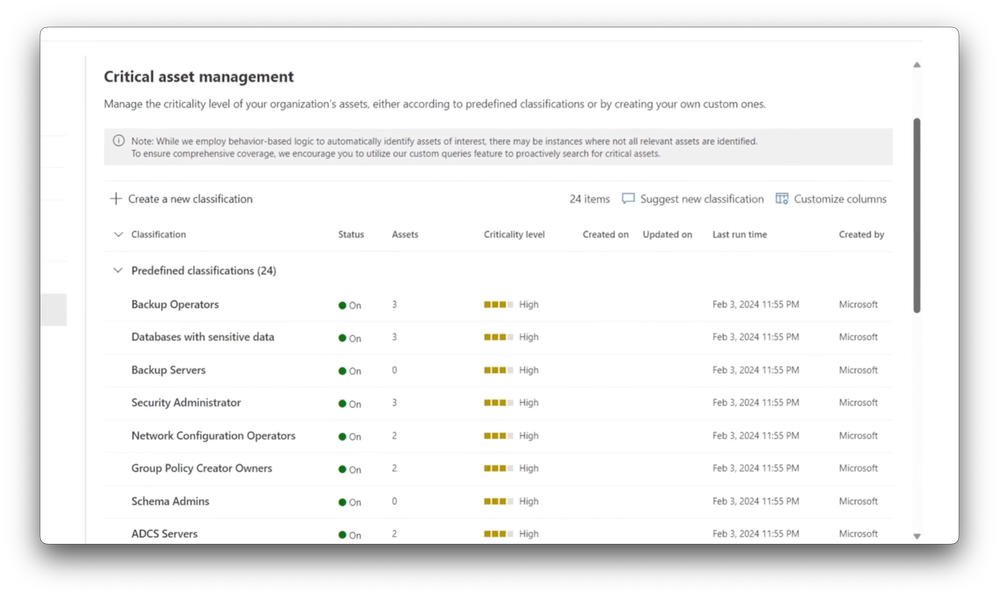
-Because you can’t fix everything at once, it’s important to prioritize where to focus your efforts. Security Exposure Management helps with that too. First, let’s go back to our most important business critical data and sensitive information. In order to prioritize them, you have to discover and identify them, and we make it easy for you with a set of predefined classifications of common critical assets.
-And then you can define your own custom classifications and have the tool automatically mark them as critical. Now, let’s go back and look at the initiatives important to your organization. Exposure Management provides a list of initiatives for you to choose from. This is a curated and continuously evolving list with threat actor groups, common workloads and trending attack types. For now, I’ll choose Octo Tempest.
-If you haven’t heard about them, they typically use broad social engineering campaigns to compromise credentials and gain access to private networks. I can see the all-up score at the top, which is a measure of how strong our posture is for this particular initiative. It’s at 78%, which is better than our target of 67, along with security metrics, critical assets, and more.
-For this initiative, we’re going to assign Jane as the owner since she’s responsible for new or evolving threat actors. As an initiative owner, you can receive automatic emails detailing updates to any initiative you own, when there’s a drift in the protection level. In fact, let’s play that out. You can see an example of the email that Jane would receive in this event. In this case, there’s a 20% decrease in our protection against Octo Tempest, which can be investigated further.
-As you click in, you’re taking directly to Exposure Management, and now, you can see a connection to one of the tracked security metrics for Internet-facing devices, which has dropped significantly. And by clicking in further on that metrics, you can see a high-level view of the details. On the right, there’s also an Insight highlighting three new attack paths that have opened up based on the device now being Internet-facing.
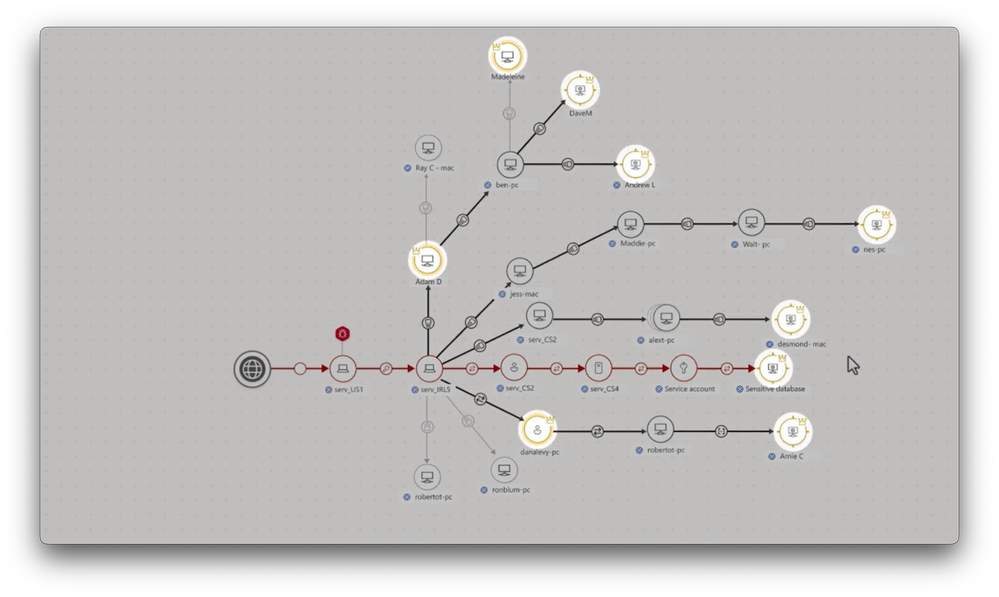
-The approach with bottling attack paths goes beyond just remediation of isolated security findings, like the discovered Internet-facing endpoint. Instead, as I’ll show you, it gives you a detailed visual mapping of the potential lateral movements an attacker can make along with impacted users, devices, and resource entities that can be used as an entry point. So let’s look at that experience.
-From the list of attack paths, you can now get details for each one. I’ll choose this one at the top with the highest criticality. The visual tells part of the story and kind of resembles the stops on a subway line where the Internet exposed device is the starting station and the critical assets is the end of the line, which all the lateral movements or stops in between to get there. These are the resources and assets that an attacker might reach with a well-crafted attack. In fact, this server, IRL5 device, in the middle is important. The double blue circle means that it’s a choke point.
-These are like subway hubs that connect to other destinations. When I expand this view by selecting Show blast radius, you’ll see why it’s a choke point. It provides the attacker with additional attack paths to other even more critical assets, which are circled in gold, which means if you can shut the hub down, you can close many attack paths.
-So now, if I take a closer look at this choke point, on the right, I can see more details about this device, and from there, I can see recommended actions for remediation. This is where we now can mobilize our vulnerability and posture management teams to prioritize remediating this choke point to close down multiple attack paths.
-And if we fast forward in time and go back into the initiative, we can check the impact of our remediation and you’ll see our protection level against Octo Tempest has increased from its dip of 58% back to a healthy state of 70, which is, again, above our target. And this is just one example. Secure Exposure Management will continuously monitor your threat exposure and help you improve your security posture, so you can stop attacks before they happen.
-To sign up for the preview, go to aka.ms/ExposureManagementpreview. And for more information, check out aka.ms/ExposureManagementdocs and keep watching Microsoft Mechanics for the latest tech updates. Make sure you subscribe and thank you for watching.