Video Transcript:
-What if I told you that without any code changes, you can now enable more secure access to all your private on-prem and cloud resources beyond what you can do today with traditional VPNs?
-This is made possible with Microsoft Entra Private Access, which is one of two solutions, including Internet Access, that comprise Microsoft’s security edge solution. Private access takes an identity-centric, Zero Trust network access approach, and uniquely leverages the Conditional Access policy engine to assess risk in real-time, using identity, device, and application signals. And apply additional network conditions to protect any app or any resource, like file shares or virtual machines.
-And with many of us now working outside of the corporate network, this approach isn’t just a nice to have, it’s necessary. That’s because VPN solutions are typically relied on as a primary method to control corporate network access. And once private network connectivity is established, the front door to your network is unlocked. And it’s very common for users and devices to have more permissions than they need, they are over-permissioned.
-This increases your attack surface with cybersecurity attacks significantly rising. In fact, unprotected VPN access is what contributed to the 2021 Colonial Pipeline ransomware attack, where the password breach of an employee resulted in 17 US states declaring an emergency, and the FBI paying $4.5 million to the attackers to regain control.
-The good news is that Microsoft Entra Private Access can be deployed quickly to block lateral attack movement, and reduce the risk of excessive access and replace your legacy VPNs. The approach even goes way beyond what’s possible using traditional access control lists or ACLs. It works by using a locally installed global secure access agent on your user’s managed devices.
-Then, in your local network, you’ll install a lightweight private network connector as an agent to handle traffic, which uses outbound connections. These work together to securely broker the connection between the user and the private app. And importantly, the solution integrates deeply with your identity systems and Conditional Access real-time risk assessment controls, which means less time and complexity to strengthen the security of your hybrid and multi-cloud architectures.
-And you can modernize protections for all your legacy apps without any code changes, let me show you. Starting in the Microsoft Entra admin center, let’s begin with how you’d set up identity-centric private app access without using a VPN.
-In connect, I’ve already set up a few private network connectors to establish secure communication between my on-premises network and the service. Then from the enterprise applications page, you’ll see I already have a few here, I’ll add a new application. Now, I’ll enter the name of an internal app. In my case, it’s einvoice, that is hosted in my company’s data center on-premises.
-Next, in the connector group, I select the one that I want, based on my app. And I can configure controls, all the way down to application segments across the network, for very granular control, so I’ll add one. I can choose from an IP address, fully qualified domain name, or an IP address range. Here, I’ll use an FQDN, I’ll paste in the address. Now, I’ll define the port, which can be just any port, I’ll use 443. And since this is an on-premises application, I’ll also configure a local IP address in the same way and use the same port.
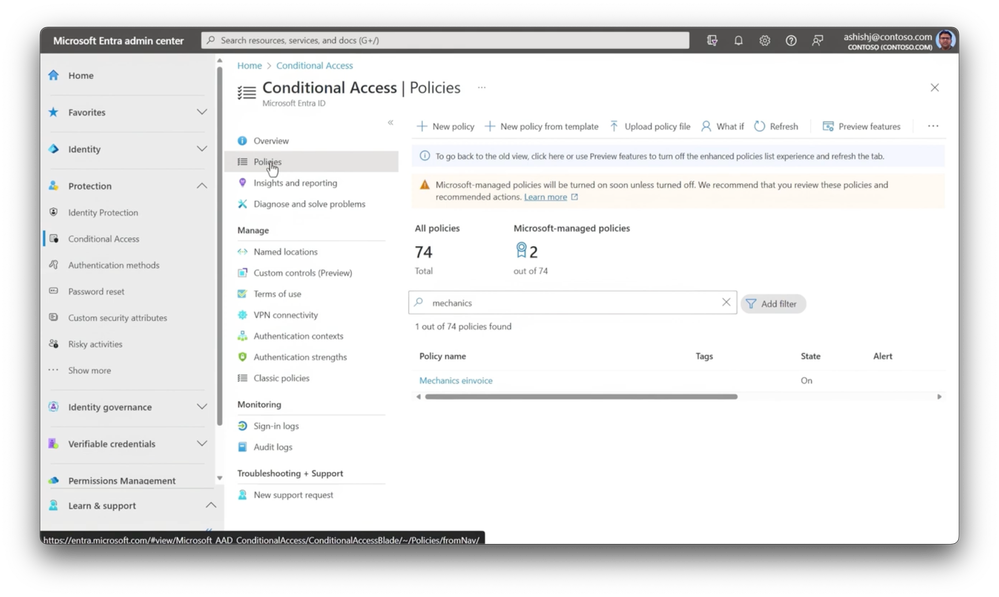
-Now, I’ll save it and the app is configured. And with the app configured, I can head over to my Conditional Access policies. And, to save time, I’ve created a policy in advance. I’ll open my policy for our app, and by expanding the target resources, I can find the private app that I just created, which links this policy to the app.
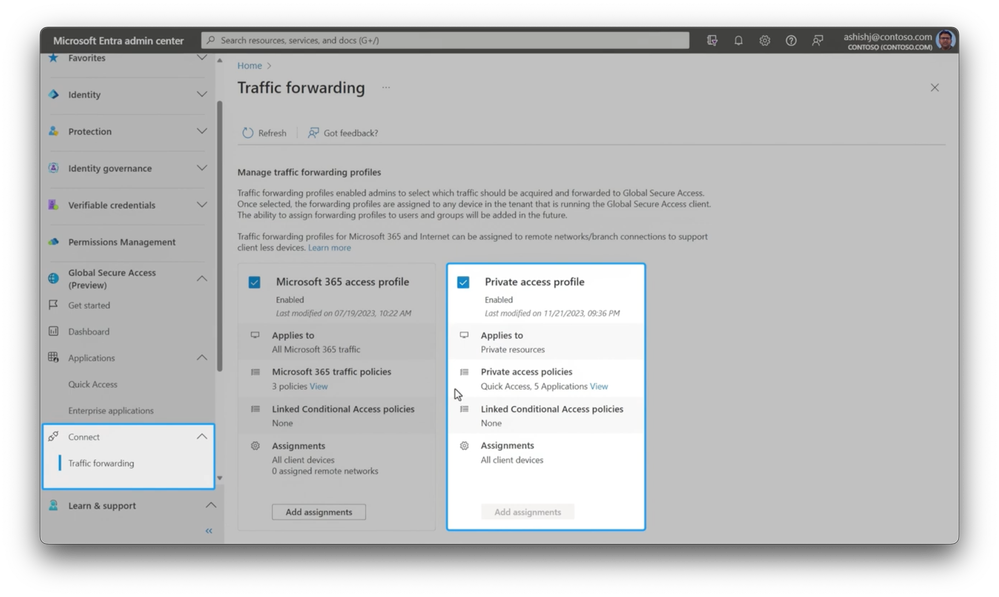
-And under grant access, controls are set for strong authentication with MFA using the authenticator app, to add an MFA authentication if a risk is detected. Next, in connect and in traffic forwarding, I’ve already enabled the private access profile in my case, but this is something you’ll need to do to get everything working. Then you’ll see the details of what’s already in place and where this applies.
-So you can start to see the granularity of identity and network access controls available to you. I’ll try this out to show how this approach minimizes the risk associated with implicit trust compared to a typical VPN connection. I’m using an enrolled device, with a global secure access client installed. I’ll paste the legacy app address into my browser.
-And as you might expect, I’ll reach the site without step up auth to a second factor, because this is a trusted device, trusted user, and a trusted sign in location, in this case, Redmond in Washington. This time, I’ll show you how this works on the same device, except for its wifi network connection. First, I’ll change the connection in settings to Fourth Coffee free wifi.
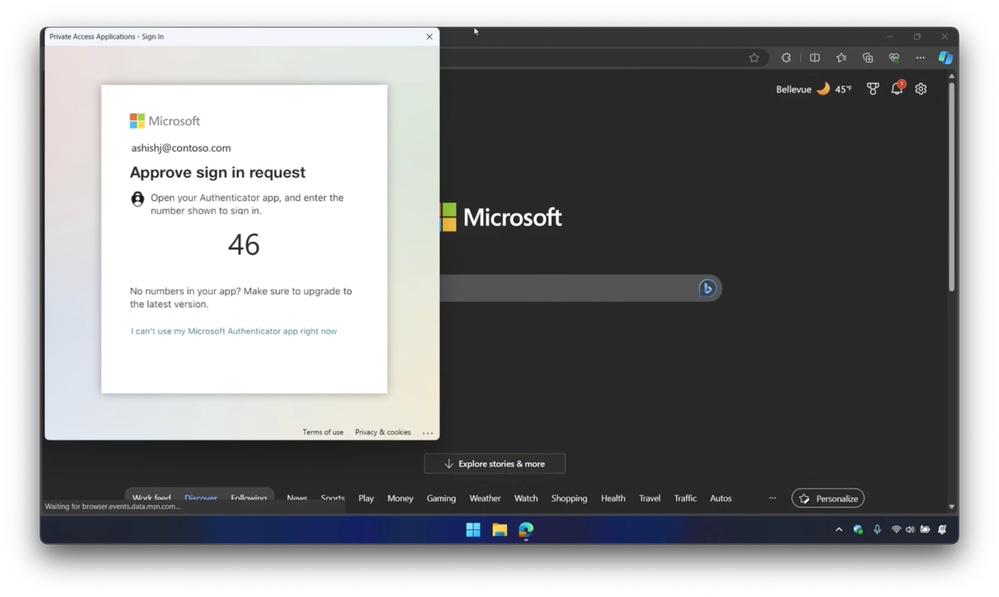
-Now, when I paste in the URL for an app, we saw before, Conditional Access from Microsoft Entra ID recognizes the change of location and determines that there is an additional risk, and asks me to reauthenticate. And even though this is a new location, I can still prove my identity with a strong authentication method, in this case, a passwordless auth.
-Then I’ll get access to my private app. So I’ve just added two factor strong authentication, along with real-time risk assessment using Conditional Access, all without any code changes to my legacy app. This also lets you safely connect to infrastructure resources on-premises without a VPN and without a domain joined device, even using single sign-on with Kerberos. Let me show it to you.
-Here, I’m on a Windows 11 machine. On the top, I have the global secure access advanced diagnostics view open to display traffic, a command prompt, and a File Explorer window. I’ll start by showing the management status of this machine in the command prompt, by using the dsregcmd command. And you’ll see this device is only joined to Azure AD, or Microsoft Entra ID. It’s not a hybrid, not a domain joined PC.
-Now, I’ll run klist to show if I have any cached Kerberos tickets, and you can see that I don’t have any. Despite that, I’m going to try to reach a local SMB server path in File Explorer. And when I do that, you’ll see the request to authenticate, and I’ll enter my username along with a password to sign in.
-I’ll opt in for it to send me a verification code to my phone, via a text message. Now, I’ll enter the code, and notice the traffic activity is to destination port 88, which is actually the Kerberos port on the on-premises domain controller. My connection to internal servers and the domain controller resolved using private DNS support, now available with Entra private access.
-So I can now get to my data. And if I go back to the command prompt and list my Kerberos tickets, you’ll see that I now have a few cached. So for a local SMB file share, I added two factor authentication with Conditional Access on a non domain joined machine using single sign-on with Kerberos, all without a VPN. Now, let me show you another way to connect to on-premises infrastructure, this time from a mobile device, with Conditional Access policies and privileged identity controls to ensure you have sufficient permissions.
-Here, I’m on an iPad. Notice that I have Microsoft Defender installed. The Global Secure Access client is built into Microsoft Defender, so there are no additional agents or management profiles for you to deploy on iOS and Android. I’m going to open the Remote Desktop app, and try to connect to this local server, as you can see from its IP address.
-As I access, an authentication notification is triggered by the Defender app for me to sign in. I’m using passwordless strong authentication, and even though I have entered the correct number sequence from my phone, you’ll see that I’m blocked due to insufficient privileges. In this case, my connection is gated by a Conditional Access policy, which also includes a condition to check my role permissions.
-So let’s take a look at that. From the Microsoft Entra admin center, my account is set up for just in time access to ensure that I don’t have persistent permissions to critical resources. I’ll navigate to my roles, and in groups, you’ll see that I’m part of an RDP privileged group where I can access time-limited role privileges. I’ll do that and leave the default, in this case, of eight hours.
-Now, I’m required by policy to type a reason, so I’ll just type live site, and activate. And that will take a moment to process, but importantly, I now have the right privilege level. So next, let me retrace my steps from before, first with the Remote Desktop client.
-And as you can see, there’s that authentication notification from before, this time with a new number. And when I input that from my phone, you’ll see Defender confirms that I’m protected, and my device and global secure access status is also shown as healthy. As a result, I can now access my server using my Remote Desktop app, and I’m connected to my local server.
-And good news here is that I don’t need to leave any open inbound port 3389 for RDP to work. This uses secure outbound connections over port 443. So that was an overview of how Microsoft Entra adds Security Service Edge controls for private connections to extend modern, identity-centric, Zero Trust protections to all apps and resources on your private network. You can get started today at entra.microsoft.com. And to learn more, check out aka.ms/SSEPrivateAccessDocs.
-And for an overview of Microsoft Entra Internet Access, which is the other half of our security service edge solution, check out our playlist at aka.ms/SSEMechanics. Keep watching Microsoft Mechanics for the latest in tech updates, hit subscribe, and thank you for watching.