Video Transcript:
- What if I told you that with just one portal, you can manage your entire multicloud security operation from one place, so you don’t need to jump between a SIEM, Extended Detection Response and Threat Intel systems and it lets you interact with all of your security data using generative AI with Security Copilot. That’s what we’re delivering and that’s what you just saw with the new unified SIEM and XDR experience in the Microsoft Defender portal. And Rob Lefferts is back to tell us all about it.
- Always great to be back as we keep evolving and improving.
- I’m really looking forward to this so tell us how Microsoft Defender then has changed and how it’s evolving.
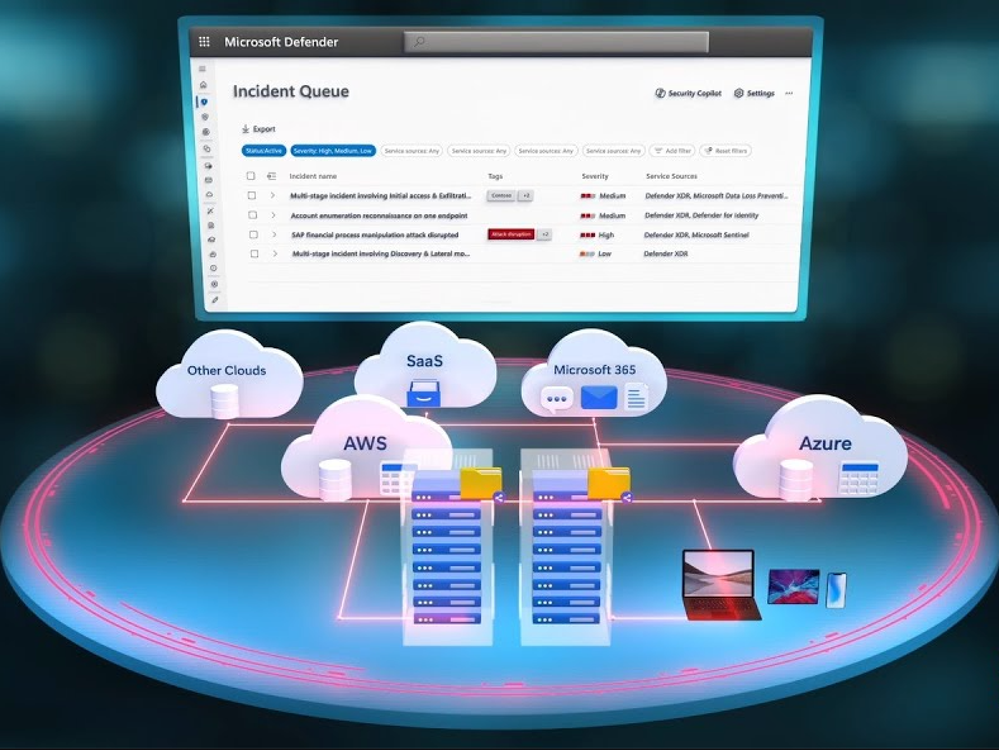
- So to build on what we’ve covered here on the show through various seasons, we’ve been working towards a unified security operations platform for a while and now it’s here. First, we are extending Microsoft 365 Defender with signals from Defender for Cloud and renaming it to Microsoft Defender XDR. Additionally, we’re bringing in all of Microsoft Sentinel with its vast insights to deliver a truly unified security operations platform. So now, instead of multiple interfaces and data streams that you’d need to learn, navigate, and use to work through your security incidents, we’ve made things much easier. The Microsoft Defender portal provides a single experience to help you coordinate threat detection, prevention, investigation and response. And you get a comprehensive overview of incidents across your digital estate, whether they are related to endpoints, SaaS services, your network in the cloud, or on-prem infrastructure. Additionally, as security events happen, you can disrupt them at machine speed to protect users identities and endpoints, and now even business applications. Which of course takes things a step further in the prevention of data exfiltration.
- Right, in terms of the pain that goes away, these are incidents and activities that might have spanned a few different services like different islands kind of in the past.
- Absolutely. And as a result, SOC teams would need to jump between those islands carrying the context and piecing together the full scope and details of an incident in their heads. Not the most efficient way to carry out an investigation where seconds count. And just to be clear, with Microsoft Defender portal’s unified approach, you won’t be losing any of the functionality you rely on today in each service. You can still jump back into those connected services. It just means that you can now operate within one island when that 360 degree context matters.
- Right, and this really helps when time is of the essence. And plus you’ve got a lot of different time savers, which then leads us to the big news that we announced last March, GPT-based Security Copilot. So, how does that play into Microsoft Defender?
- It gives you a powerful natural language interface over your security data so that you can easily query it and sometimes can catch details that you may have missed. Security Copilot, in fact, has been specifically trained and fine-tuned on cybersecurity. So we’ve evolved the large language model itself and we’ve built an orchestration layer underneath that to find and parse through massive amounts of security data and signals across Microsoft Defender XDR, Microsoft Sentinel, and all of your non-Microsoft connected services completely tailored to your environment and SOC scenarios. Then as you work in Microsoft Defender, Security Copilot is embedded within each Microsoft Defender experience. With all of this training and connected knowledge in the Security Copilot sidebar, each incident automatically gets a generated summary and will even create reports for you. And as you investigate alerts, it can analyze scripts and commands in context as you work. And in Advanced Hunting, you can use natural language to author KQL queries with Security Copilot. Building an AI system like this is something we’re uniquely able to do with our expertise in cybersecurity and in operating large language models.
- Right Rob, I bet you know where this is going. I’d love to see all this working so do you have an example you can show us?
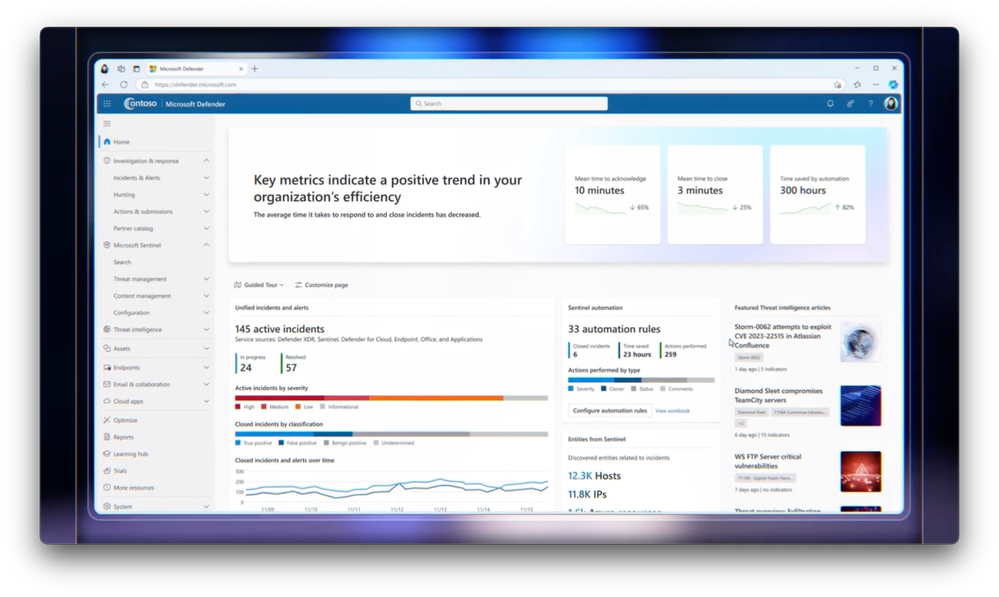
- Sure, I have a great one lined up for you. In this case, we have an active incident with our SAP environment, so it’s business critical and we need to contain it fast. Here, I’m in the new Microsoft Defender portal, which as I mentioned has everything you need from its cloud-based SIEM capabilities, full breakdown of active incidents, complete set of investigation tools with threat intelligence built in, attack story visualizations and more. We see total unique incidents, a unified list across Microsoft Sentinel and Defender XDR insights into data connectors, top risky entities and more. While Defenders used to have two different homepages to go into to get started and determine what to do that day, now they have just one. I can quickly see all of the active attacks in my environment and on my network. And from the data connectors and automation tiles, you can see the extent of our data integration from our SIEM. Let’s dig into the active attacks on my network. This is our new unified incident queue. You can easily see alerts correlated into incidents, and these are prioritized based on machine learning. Now let’s look at this incident on the top. A financial process manipulation on SAP. SAP is a critical ERP and CRM product used by many companies containing both company and employee data, making it a popular target for cyber attacks. But, we see this incident is already tagged with attack disruption, and if you’re new to attack disruption, it automatically intervenes and stops the progression of advanced attacks within Microsoft Defender XDR. And we’ve already had this for Microsoft 365 workloads, but this is new. It’s taking action to disrupt an attack directly on SAP, including protecting the SAP user account.
- Right, and you’ve got all the sentinel information right there in context inside of Defender, but I also see that you’ve also got Jonathan Wolcott and he’s back. So, is he in trouble again?
- Well, he’s had his moments in previous shows, I hope he is okay. Let’s open up this incident and in fact, he’s not okay. As we can see, he has been attacked and attack disruption has already kicked in and things have happened on two fronts. First, Jonathan Wolcott’s AD account has been disabled to get the attacker out of his productivity applications, but his SAP account has also been locked. So the attacker can’t, for example, redirect payment from a business to their own accounts. So being able to disable additional IDs is increasingly important with multi identity stores and many different applications that organizations leverage. By bringing first and third party insights together here, we are getting better coverage and higher confidence that the combined forces of SIEM+XDR automatically take the right actions like this one to defend against advanced attacks. I’m going to need to let our manager and potentially the board know what has happened here. And the good news is that we now have Microsoft Security Copilot reasoning over both Microsoft Sentinel and Defender XDR data right here in the portal to create a summary. Just by clicking this generate an incident report, Copilot gives us a detailed summary of what has happened and why. You see that Jonathan Walcott got a phishing email with a link, which turned out to be a malicious URL, resulting in his credentials being stolen. We even see the IP that was used by the attacker. Now you can easily ship this summary off to a manager, the board, whoever needs to get a heads up about what happened and how it was addressed automatically with your security tools.
- Nice and this really provides a high level recap in terms of what happened. But what else might you do then to find out more or contain that threat?
- One thing you might want to do is find out where any other files accessed from this malicious IP. And the good news is Copilot will guide you to Advanced Hunting to do some research. In this new unified hunting experience, you can look through both Microsoft Sentinel and Defender XDR data. No matter where it’s from, this also means your SAP data, your device events, all your information will be there. Before this as a tier one analyst, hunting using KQL was quite a challenge to me, but now I can use Microsoft Security Copilot to query and return results. And in this case it even figured out what I should be looking for and wrote the prompt for me. And I can continue using natural language prompts or suggested prompts. And in this case it says, “Hey, you should check out were there any successful connections.” And when I do that, you’ll see that they were able to access a few more files but nothing confidential. We were able to stop them before they reached the important stuff. With this, unified advanced hunting, it’s working across Microsoft Sentinel and Defender XDR. So I was able to query everything in one place without having to keep track in my head of where to find what relevant information.
- Right and everything you did there just saved a ton of time in terms of investigation and response. So this is Mechanics again and a lot of implementers are watching. How would I get all this stuff set up?
- So if you’re already on Microsoft Defender E5 and using Microsoft Sentinel, you’ll see this banner displayed in Defender’s Homepage at the top with a button to connect your Microsoft Sentinel Workspace. And when I click on it, it takes me through a simple Wizard process to onboard my workspace. The entire process takes only a few minutes so there’s no complicated onboarding required. And Microsoft Sentinel continues to work in the Azure portal just like usual. It’s pretty easy and brings everything together in one place.
- Which as you showed, makes it a lot easier than to work through your incidents with all the tools and intelligence you need. And it’s right there for you. So for anyone who’s watching right now, looking to get started, what do you recommend?
- Well that’s easy. If you’re already using Microsoft Sentinel and Microsoft Defender XDR as we just showed, it’s super simple to get everything up and running. And you can find out more at aka.ms/SOCPlatform and join our private preview, we’d love to hear from you.
- Thanks again, Rob, for joining us today.
- Thank you.
- And it’s great to see the unified experience there with Defender and all things you’re doing and also Security Copilot. And by the way, for deeper dives like this in the latest tech, be sure to subscribe to Microsoft Mechanics. Thanks for watching, we’ll see you next time.