Video Transcript:
-The majority of data breaches resulting in data theft, around 60% of all incidents, in fact, are caused by people, insiders, if you will, working inside your organization. So how can you stop this? Well, the good news is that with the new Insider Risk condition in Microsoft Entra’s Conditional Access. Insider risk protections powered by Adaptive Protection in Microsoft Purview, ensure that users can access resources as usual when their risk level is low.
-But if something changes to elevate their insider risk level, access to critical assets can be blocked automatically. This is powerful in situations where the user inside of your organization is the perpetrator of a data breach versus an external threat that has compromised the user account. This expands Conditional Access as you may know it, beyond traditional identity and access management, where you can set conditions against unauthorized access to organization resources.
-These include conditions for user risk, where we detect if there’s a repeated compromised state of a user’s account, sign-in risk, where we detect an anomalous sign in attempt based on an unusual behavioral pattern, like impossible travel, as well as other conditions, like the device platform, network locations, and client application types. The new Insider Risk condition now extends Conditional Access to mitigate data security incidents at the time of access through native integration with adaptive protection, which is part of Insider Risk Management in Microsoft Purview.
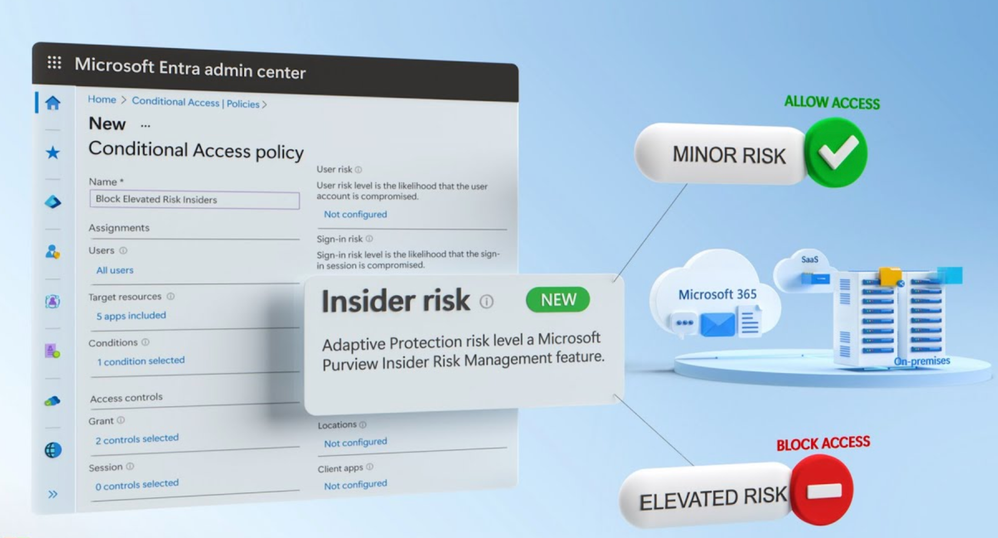
-The combined solution takes a privacy first approach to algorithmically correlate risk indicator signals, including a user’s data activity and specific events like a resignation. It then assigns an insider risk level to a user across three tiers, minor, moderate, and elevated, and policy controls can be defined for each risk level. For example, if specified, a user with an elevated risk can be automatically blocked from accessing Microsoft 365, SaaS apps, and even your on-prem resources.
-Importantly, the risk level of a user can dynamically adapt over time, and as that happens, access to resources will automatically adapt too. All of this is possible without requiring multiple tool sets or manual work to keep track of insiders engaging in potentially risky activity. So how is it that insider risk levels are calculated? Well, they’re calculated based on the Insider Risk policies you’ve deployed. For that, you’ll use Insider Risk Management in Microsoft Purview, and I’ll quickly demonstrate the steps.
-First, you can configure the types of policy indicators you want to detect, which can be office indicators, like downgrading sensitivity labels, or other risky activity across Microsoft 365 workloads, device indicators, like moving files to USB storage or uploading to an unsanctioned website, Defender for Endpoint indicators, risky browsing activity, physical access, or Cloud App access. You can also enable machine learning derived cumulative risk detections, like bulk file exfiltration over time based on organization and peer group norms. This is where, for example, a user shares more files than others on their team over a 30-day period.
-And you can also take advantage of Risk Score Boosters, which give you access to specific models, like potential high impact user, which applies to users with higher level of privilege that could increase their potential to do more damage, like a global admin in your organization. Next, Insider Risk Management policies can be scoped to the right user groups within your organization, and be defined to detect risky activities and certain scenarios, like data theft by departing users, where you can also prioritize content that you care about most, based on location, sensitivity and file types.
-That said, of course, we want to adapt protections dynamically based on a user’s changing risk over time by defining the protections we want at each insider risk level. The fastest way to get this running is by selecting quick setup that will implement standard configurations. I’ve already done this in advance on another tenant, and you’ll see a few policies already set up. There’s two for Data Loss Prevention in audit mode, and one for Conditional Access in report-only mode. And of course, you can edit these policies further.
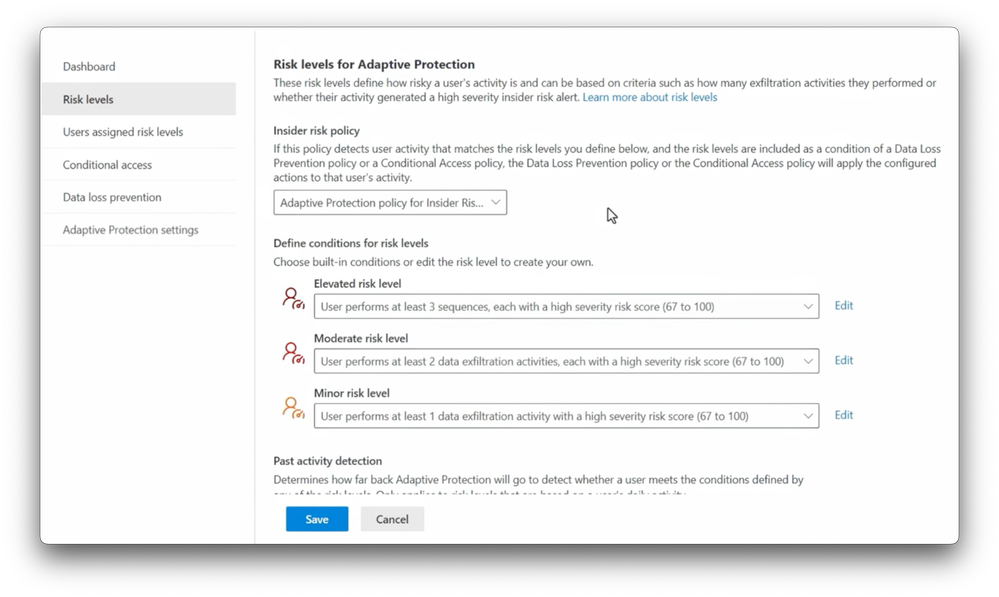
-It’s also created an insider risk policy scoped to all users inside my organization and set default thresholds for each risk level, elevated, moderate and minor, and you can modify the conditions to control when the risk level is assigned to users, according to your organization’s risk tolerance. For example, you can define the time span for past activity and how long a user stays at a specific risk level before it’s reset. You can learn more about the policies you can set up here at aka.ms/IRMMechanics.
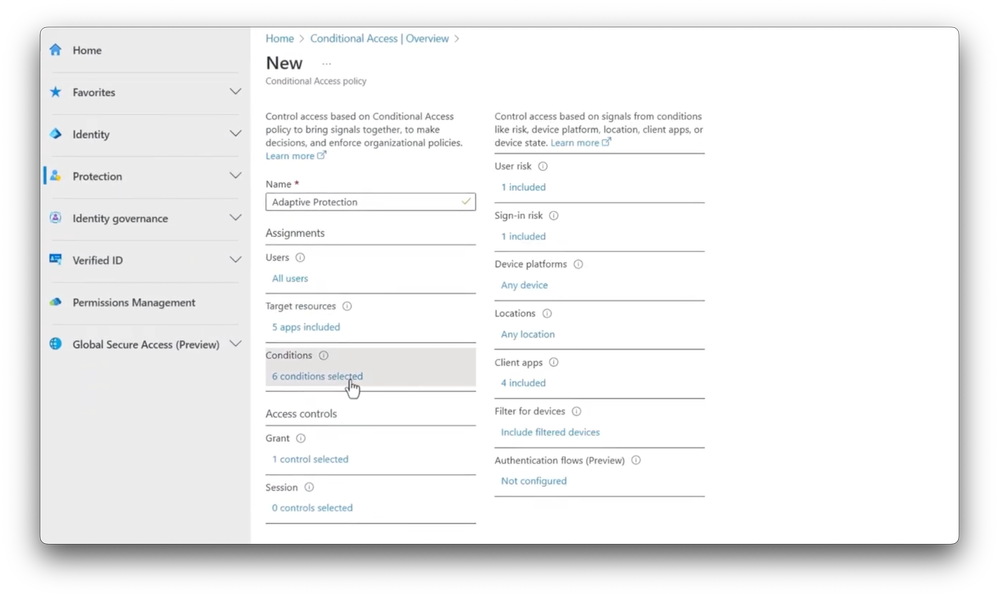
-Next, let me show you how you can go beyond the default policy set up in Microsoft Purview so that we can set specific policies against different insider risk levels. For this, I’m going to switch back to Microsoft Entra. I have my Conditional Access policy blade open, you can see the default policy, to block access to users with elevated risks that we just set up.
-To set up a more custom policy to protect access to specific apps and resources based on a user’s insider risk level, I’ve already completed the standard fields and I’ve scoped it to all users and a few apps. Under Conditions, I’ll use the new Insider Risk condition and here I just need to switch Configure to Yes, and in this case, I’ll select Elevated. For Grant, because these are high-risk, elevated users, I’ll set this to Block Access Outright. This will ensure that anyone with this insider risk level will not be able to access our specified cloud apps.
-I also want to set a Conditional Access policy for users with a moderate risk level. But first, let me show you one more thing. I have Microsoft Entra Private Access configured for on-prem resources in my organization as well, which I’d recommend and here’s why. For two of my apps, I’ve selected my on-prem virtual machines and file shares, so I can also prevent access to those resources.
-And now, even if an insider tries to use a personal device, they won’t be able to connect to them. Next, for moderate risk users, I don’t want to be so heavy handed. I want to display a policy document, then grant access by requiring strong reauthentication. Again, to save time, I’ve started my Conditional Access policy. This time my Condition for Insider Risk is already enabled, and you can see that it’s set to Moderate.
-But if I head over to Grant, you’ll see that I’m requiring strong authentication, and to display the policy document from Contoso, I’ve created a terms of use entry that I can select from here. And if you’re new to Terms of Use and Conditional Access, let me show you that quickly. I have a PDF file open here with my terms of use from Contoso. And to create new terms, you just need to upload A PDF like this and add the additional settings you want to enforce.
-Once you do that, the Terms of Use option will appear in your Conditional Access policy under Grant, like we saw before. So let’s test this out with the user whose insider risk level is changing over time. Here they’re attempting to access Salesforce, and you’ll see that they’re required to add a passwordless authentication, and they’re then shown the Terms of Use so that they can acknowledge the company policy. It’s only after that they’re given access to Salesforce. Their experience reflects what we define for someone at a moderate risk level.
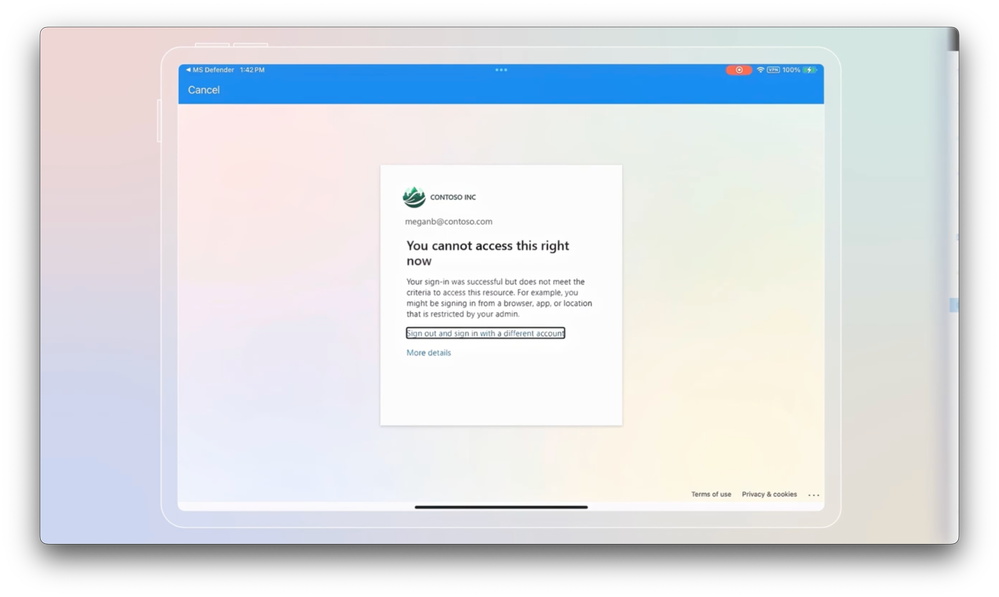
-Next, I’ll fast forward in time where a same user has engaged in even more risky insider activity. And on top of that, they’ve submitted their resignation, raising their risk level to elevated. Here they’re trying to remote into an on-prem virtual machine. And a fun fact here, we’ve seen people sometimes put these in place prior to leaving a company to serve as jump boxes with a path back into the corporate network. And as they try to access on-prem resources in this case, you’ll see they’re blocked outright. And remember, that’s because we also have Microsoft Entra Private Access deployed.
-So that’s how you can help prevent data breaches resulting from insiders working for your organization. The Insider Risk condition for Conditional Access is now available to try out and preview, and you can get started today with Insider Risk Management and Adaptive Protection in Microsoft Purview, and learn more at aka.ms/AdaptiveProtection. Additionally, for our ongoing series on Insider Risk Management capabilities, check out aka.ms/IRMMechanics. Keep watching Microsoft Mechanics for the latest updates, and I’ll see you soon.