Protect against identity-based attacks with Identity Threat Detection and Response capabilities. Ensure your organization is equipped to protect identities wherever they are — on-premises, in the cloud or hybrid. As an integral component of the XDR experience, identity alerts are contextualized within broader security incidents, enhancing your ability to manage threats effectively. The integrated Copilot experience and advanced hunting capabilities allow for in-depth investigation of alerts and activity logs. Security analysts and identity admins can collaborate seamlessly with bidirectional integration between Defender XDR and Microsoft Entra.
Daniel Lynch, Microsoft Defender for Identity’s Senior Product Manager, shares how Identity Threat Detection and Response can be utilized in daily operations and coordinated actions throughout every phase of an identity-related security incident, strengthening your organization’s defense posture.
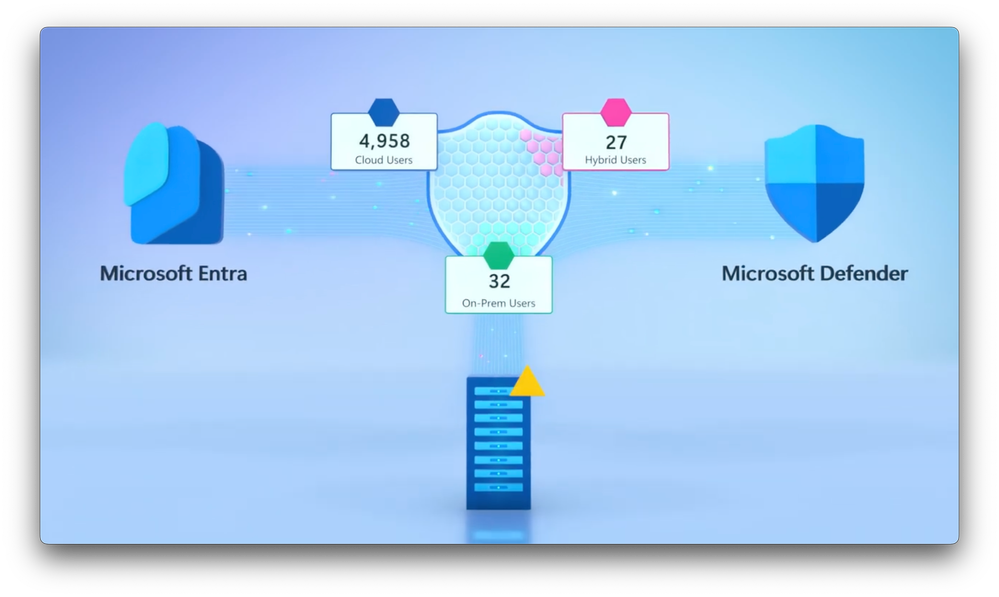
Improve your identity security posture.
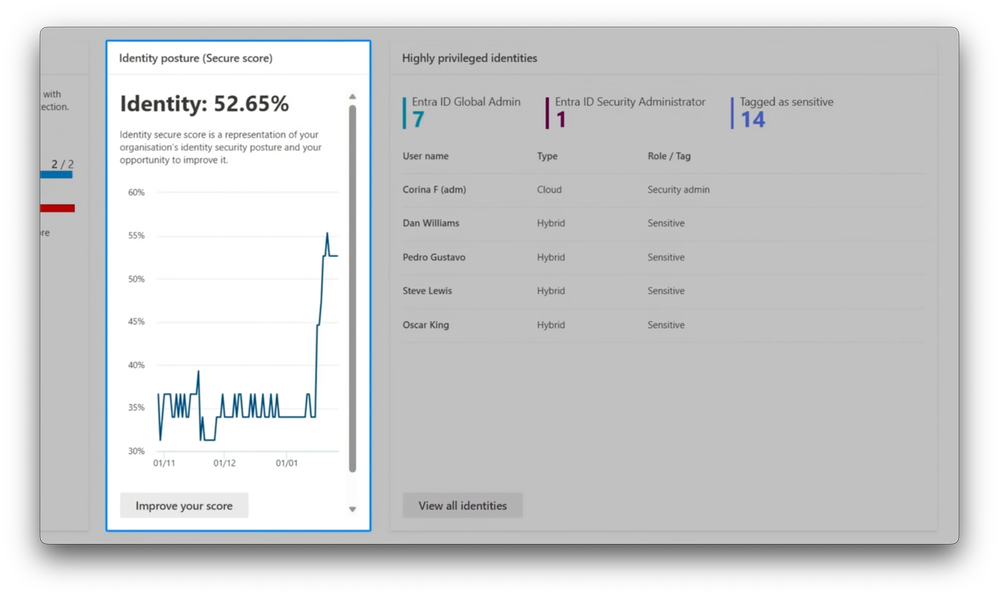
Expose areas of potential risk, get a summary of protections in place, & take recommended actions from your Secure Score. Check out the ITDR dashboard in the Microsoft Defender XDR portal.
Investigate threats with detailed activity logs.
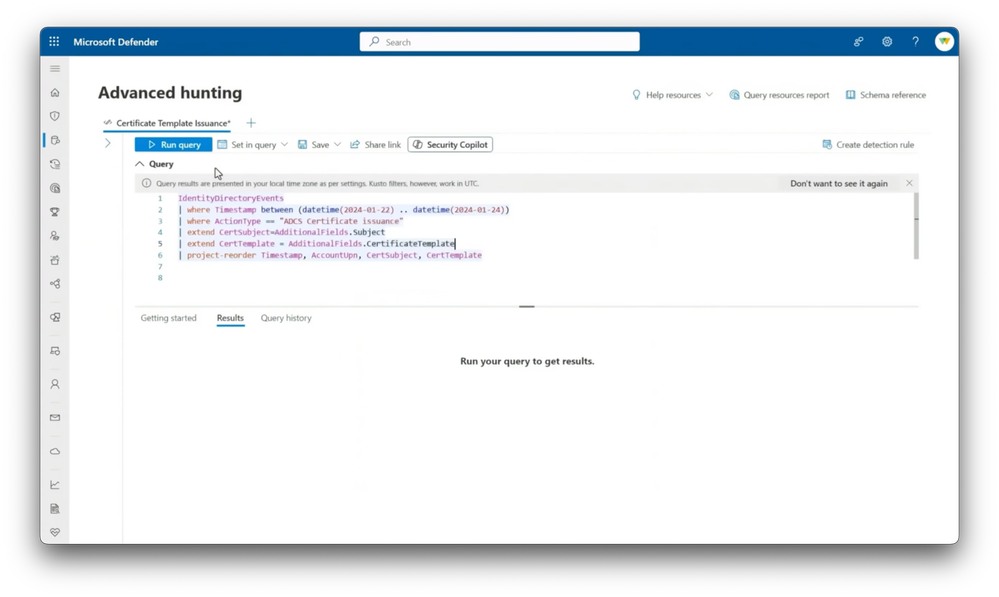
Use advanced hunting in Microsoft Defender XDR. Check out Identity Threat Detection and Response capabilities.
Block a compromised user account.
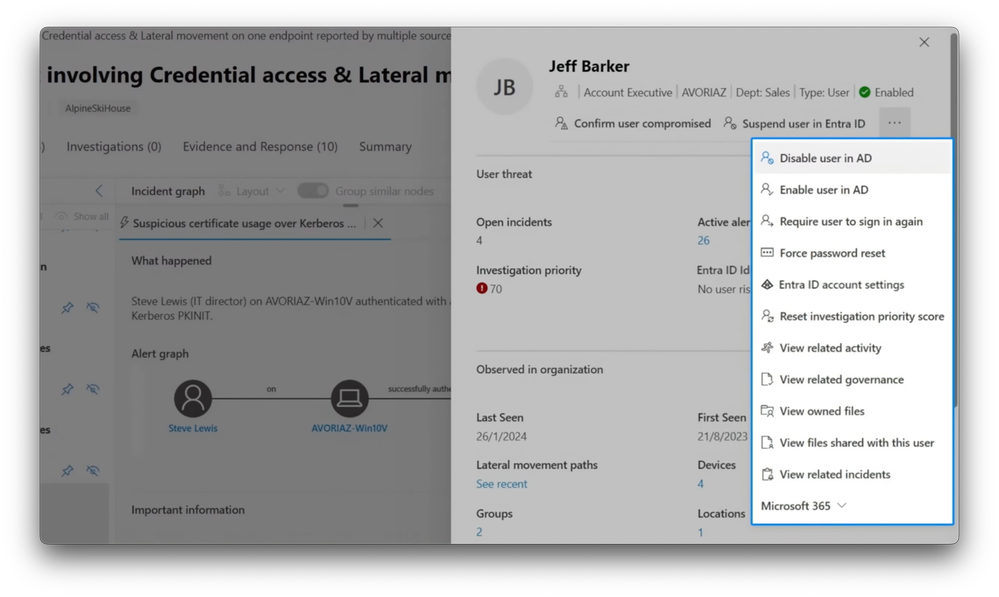
Bridge the gap between Identity and Security teams with bidirectional integration between Entra and Defender. Start here with Identity Threat Detection and Response capabilities.
Watch our video here:
QUICK LINKS:
00:00 — Stop identity-based attacked
01:13 — How to use Identity Threat Detection and Response
02:37 — See an active multi-stage incident
03:57 — Use Copilot for Security
05:08 — Advanced Hunting in Microsoft Defender XDR
05:38 — Block a compromised user account
06:44 — Improve security posture in Microsoft Defender XDR
08:04 — Wrap Up
Link References:
For more information, check out https://aka.ms/ITDR
Unfamiliar with Microsoft Mechanics?
As Microsoft’s official video series for IT, you can watch and share valuable content and demos of current and upcoming tech from the people who build it at Microsoft.
Keep getting this insider knowledge, join us on social:
- Do you have the right controls in place to stop identity-based attacks? And when a breach does happen, how quickly can you detect, respond, and ultimately prevent future incidents? Well, that's where Microsoft's Identity Threat Detection and Response capabilities come in.
-We've natively unified signals, including alerts and activities from your Identity and Access Management solutions like Microsoft Entra or Active Directory on-premise, and our Microsoft Defender XDR platform, for a more proactive protection and coordinated response to identity attacks. In fact, this is all based on our broad and unique expertise across both pre-breach access management and post-breach incident investigation and remediation. And it works whether your identities are managed in the cloud, on-premise, or hybrid.
-As a core part of the XDR experience, identity alerts are surfaced within the broader context of security incidents. You can also use the integrated Copilot experience to investigate alerts, along with advanced hunting to explore detailed activity logs. Then bidirectional integration between Defender XDR and Microsoft Entra lets security analysts and identity admins work hand in hand to address identity-related security incidents and protections.
-In fact, let me show you how you can use Identity Threat Detection and Response, both day to day and to coordinate actions during every phase of an identity-related security incident. It starts with assessing your identity security posture. In the Microsoft Defender XDR portal, you'll find the ITDR dashboard. At the top, again, you'll see a visual representation of your unique identity footprint. Then top insights uses intelligence to expose areas of potential risk, like lateral movement or dormant accounts.
-And below that, in the Deployment Health card, you can get a quick summary of the health of your identity protections across on-premise identities and infrastructure and Microsoft Entra services. And this is where identity posture comes in. We give you a score based on the protections you've implemented against a recommended baseline.
-These are identity-specific recommendations within Microsoft's broader secure score metrics that I'll get into in a second. Now, because privileged identities are a top target for attackers, you'll see a list with the most sensitive global and security admins. Below that, you'll find a count of users at risk and your connected domains, and then you'll find a prioritized list of active identity-related incidents. Now, if we go back to our Secure Score, we can see all of the recommended actions to improve your identity posture, along with their score impacts and status.
-As you can see, we've got some work to do here. Now that we know what to do to improve our posture, let's dig into an active incident. With Microsoft Defender XDR, again, your identity-related events are correlated and surfaced within the context of the incident. Let me show you. I have an active multi-stage incident open here, which goes beyond simple password compromise.
-Defender detects anomalies automatically, whether it's reconnaissance, credential access, lateral movement, or persistence. And here I have the attack visualization open and you can see the detailed attack story with related activities, including identity-specific alerts. In this instance, it starts with an anomalous lookup, then some suspicious exploration activity. And from the first couple of alerts, it looks like a user Jeff may have been compromised on the Windows10V machine.
-Then the attacker looks to have moved to our on-premise Active Directory Certificate Services, which is definitely something for us to look further into. Below that though is a more concerning alert for suspicious certificate usage over Kerberos. It's that same Windows10V machine, but this time with the user account Steve Lewis, an IT director with a privileged account.
-In the details, we can see the certificate thumbprint and issue date used by Steve to authenticate against the domain controller. And below that is an alert citing the possible use of Rubeus kerberoasting tool. So it looks like we've been compromised with a malicious certificate, and at this stage you'll probably want to alert the team.
-To save time explaining the situation, we can use Copilot for Security to automatically create an incident summary with a nice high-level description of what happened. Copilot also provides remediation recommendations like you're seeing here to reset Jeff's password, and we'll do that in a moment. Now if I drill into our user, Jeff, you'll see scoped insights for this account right here in context, and it even links us directly to the user page.
-On the user page, you'll find even more information helpful to our investigation. In fact, in the timeline view, I can see all of the identity-related activities from Jeff over the last 30 days. Because we're investigating a certificate services event, we can filter the activities to those related to ADCS certificate issuance. And now I'll filter a little bit more by type and just select User Activities and apply.
-And right on top, the most recent activity is a certificate issued on January 23rd. So now we have our certificate issuance event isolated and we can investigate this further. Let's get some more details using advanced hunting in Microsoft Defender XDR. Here I have a simple KQL hunting query that will find certificate issuance events between January 22nd and 24th in the ADCS event log.
-The results tell us that the certificate was issued to Jeff, but Steve's account was the cert subject with an existing cert template of our domain users. What makes this so suspicious is that we had one user, Jeff, from the sales team making certificate requests using Steve Lewis's privileged account. So let's go ahead and contain the attack. Back in the incident view, I have options to confirm the user is compromised and even suspend their Entra ID account.
-And there's even more actions I can take, including some for on-prem AD, like disabling the user or forcing password reset. These are all built into the SOC experience, again, so you don't need to hop between consoles. First, I'm going to mark Jeff's account as compromised and confirm. That will go back to Microsoft Entra and flag Jeff's account, bridging the connection between Microsoft Defender and Microsoft Entra.
-In fact, if I move into the Entra admin center and look at what an identity admin would see, under risky users, you can see that Jeff's account was just flagged with a high risk level, and you can click in to see why. Where this really comes into play is with your conditional access policies. The user risk condition checks for compromised accounts like Jeff's in real time and as resources are being accessed.
-Then in access controls, you can ensure that if a high-risk user tries to log in, we can set it to block access to any connected resource. Now we've blocked our compromised user account. Let's go back to improving security posture in Microsoft Defender XDR. Here in Secure Score, I can move into our recommended actions where I can filter actions based on category, status, regressions, and much more.
-Then under products, you'll see options for both Microsoft and non-Microsoft services, even coverage for other identity providers. In my case, I'll filter on Defender for Identity, and if I expand the column with the description, we get a better look at everything we need to implement. In row nine, you'll see the recommendation that corresponds with the incident we just addressed.
-And when I click in, you'll see the details of the misconfiguration, which allows users to submit certificates with arbitrary SANs, or Subject Alternate Names, into certificate requests, which could allow for the privilege elevation we just saw. Then in the Exposed entities tab, we can see which certificate template allows this. It's the same one we found earlier in our hunting query. So coming full circle, as you saw with the security posture recommendations, we actually had all the information that we needed to prevent this attack before it happened.
-And one more thing. While I demonstrated how an incident is managed hands-on by the SOC and identity teams, as we've shown previously on Mechanics, Defender can also use intelligent automation to disrupt a number of attacks in real time without interaction.
-That was a quick overview of how Microsoft's Identity Threat Detection and Response capabilities can help people stay ahead of identity-based attacks before they happen and contain them quickly when they do. To learn more, check out aka.ms/ITDR and keep watching Microsoft Mechanics for the latest tech updates. Be sure to subscribe and thanks for watching.



