- Home
- Security, Compliance, and Identity
- Microsoft Entra
- soft match with proxyAddresses
soft match with proxyAddresses
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 09 2024 05:15 AM
Hi,
I would like to connect on-premise AD with Entra ID. Users exist in both. Some users' UPN are the same in the on-premise AD and in Entra, but some have different UPNs, and I want to connect them with proxyAddresses. I created test users. I filled proxyAddresses for them in the on-premise AD and in Entra ID like SMTP:email address removed for privacy reasons, but when I run test, I the following error:
"No action required. User '....' is not a newly discovered entry to be provisioned in the target application, nor one with an update that should flow to a target entry with which it was previously matched."
Skipreason: JoinNotFound.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 09 2024 08:28 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 11 2024 05:29 AM
When I create an ou based filter, so not every user will be syncronized, what will happen with the cloud-managed users, who don't have matching on-premise pair?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 11 2024 07:18 PM
Azure AD-native accounts will remain unaffected.
Accounts that originated from on-premise or were subsequently joined (becoming on-premise mastered) are soft-deleted once they fall out of AAD Connect's scope of management.
Cheers,
Lain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 12 2024 12:18 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 12 2024 03:04 AM - edited Apr 12 2024 04:52 AM
It's unlikely that they're Azure-native accounts now. It's possible, but unlikely.
The only way I recall being able to "convert" a user from Active Directory-managed to Azure AD native - without turning off directory synchronisaiton - is to:
- Ensure it's no longer being managed via Azure AD Connect (which will cause Azure AD Connect to soft-delete the user account from Azure AD);
- Recover the soft-deleted user account from the Azure AD "recycle bin" (within 30 days, or else it's hard deleted and no longer recoverable), at which point it's restored as an Azure AD-native account.
If you are ready to turn off directory synchronisation, then doing so converts all synchronised accounts (i.e. from Active Directory) to Azure AD-native accounts, but this is not something you do frivolously.
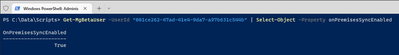
To verify if the account is Azure AD or not, check the OnPremisesSyncEnabled attribute. If it's "true" (as shown in the following screenshot), then it's still mastered by Active Directory, not Azure AD.
You can probably check using the Azure Portal, too, though I can't tell you exactly what the attribute might be labelled as, as I don't use it.
Cheers,
Lain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 12 2024 04:49 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 12 2024 05:00 AM
I'd check the OnPremisesSyncEnabled to be sure, but from what you're describing - given that you've already restored them, they ought to be Azure AD-native accounts now.
Auditing OnPremisesSyncEnabled is simply prudent as a safety check.
For any account where OnPremisesSyncEnabled is not true, you can freely manage or even delete the Active Directory or Azure AD accounts independently. Changes and deletions will not magically replicate from Active Directory to Azure AD or vice versa. (The obvious caveat is that any desired changes must be made manually to both account representations, too.)
Cheers,
Lain