Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Achieve higher security with certificate bindings - How it works!
Achieve higher security with certificate bindings - How it works!
Discussion Options
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 02 2023 07:23 AM
Dear Microsoft Entra friends,
In this article I would like to take a closer look at the subject of certificate affinity binding. So that even more security can be applied during authentication.
Let's start with a few links to the Microsoft documentation pages.
Overview of Microsoft Entra certificate-based authentication:
How to configure Microsoft Entra certificate-based authentication:
Microsoft Entra certificate-based authentication technical deep dive:
What does it mean "Achieve higher security with certificate bindings"?
Microsoft Entra ID, formerly known as Azure Active Directory, is a cloud identity and access management solution that controls application access and protects identities. The term “Achieve higher security with certificate bindings” refers to a feature of Microsoft Entra ID that enhances user authentication security. This feature is part of the certificate-based authentication (CBA) process. Certificate bindings refer to the methods used to bind a certificate to a user’s identity, enhancing the security of the authentication process. There are seven supported methods for certificate bindings. These methods are considered high-affinity if they’re based on identifiers that can’t be reused, such as Subject Key Identifiers or SHA1 Public Key. This way, Microsoft Entra ID provides a secure and efficient way for users to authenticate and access applications.
Let's examine achieve higher security with certificate bindings.
Object Identifiers (OID):
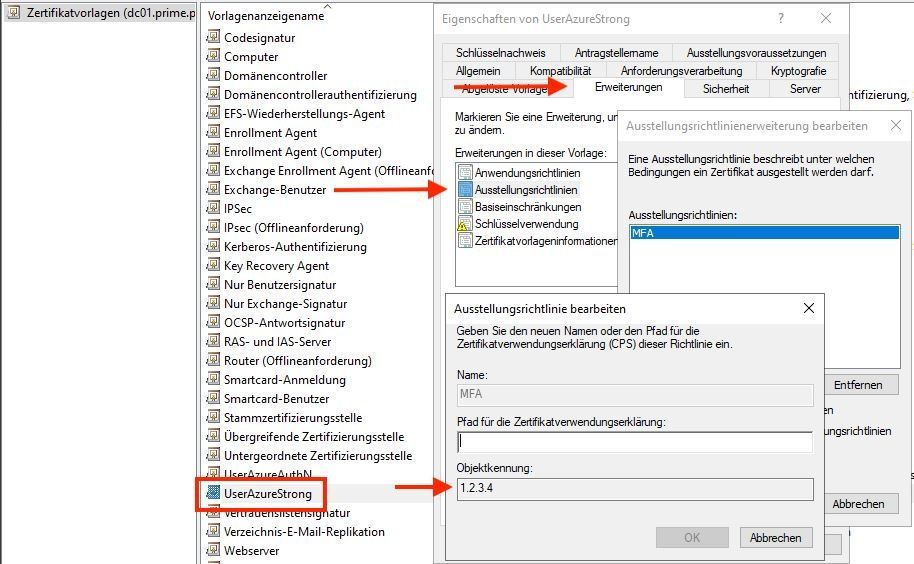
First we look at the certificate template on the certificate server (sorry some print screens are in German). Here we see the details of the Object Identifiers (OID).
Add a new rule:
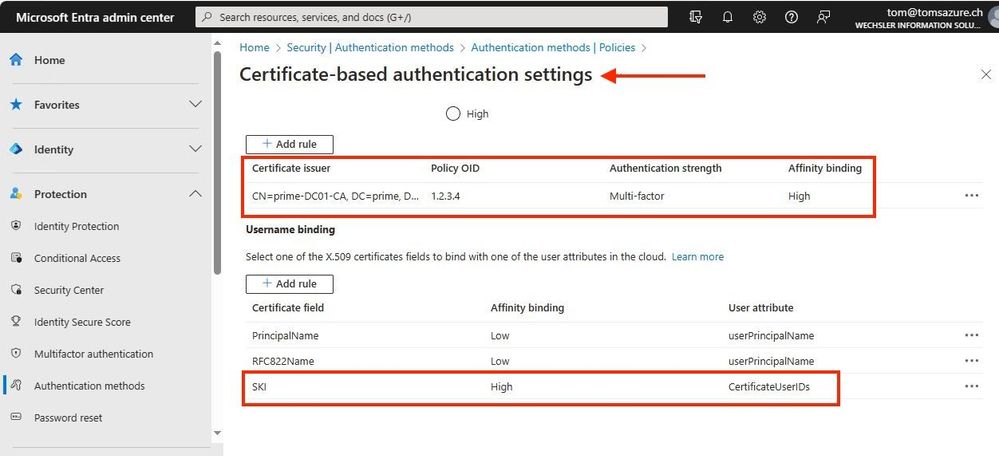
Configure an additional rule in the Entra ID Admin Center and use the same Object Identifiers (OID) value here as in the certificate template.
Subject Key Identifier (SKID):
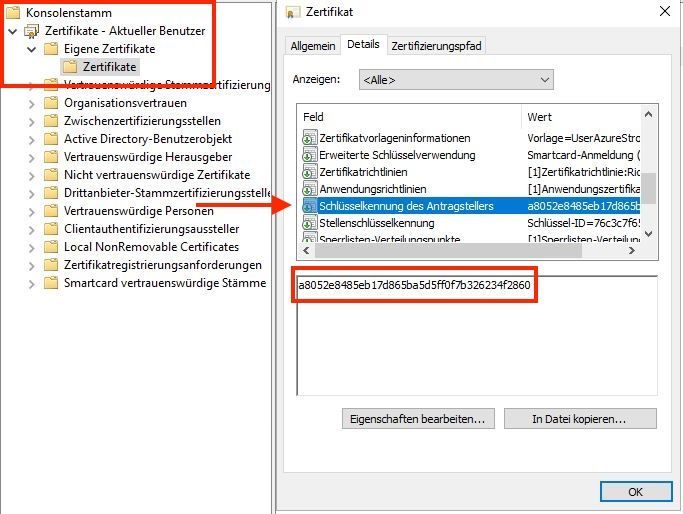
The certificate was issued on the user's system. We obtain the subject key identifier (SKID) from this certificate. We need this value in the Entra ID Admin Center to assign it to a person. The same person for whom the certificate was issued on the system (in my case it is Tina Fluenza).
Authorization info:
In the Entra ID Admin Center, we now set the value of the Subject Key Identifier (SKID) for the user in the properties.
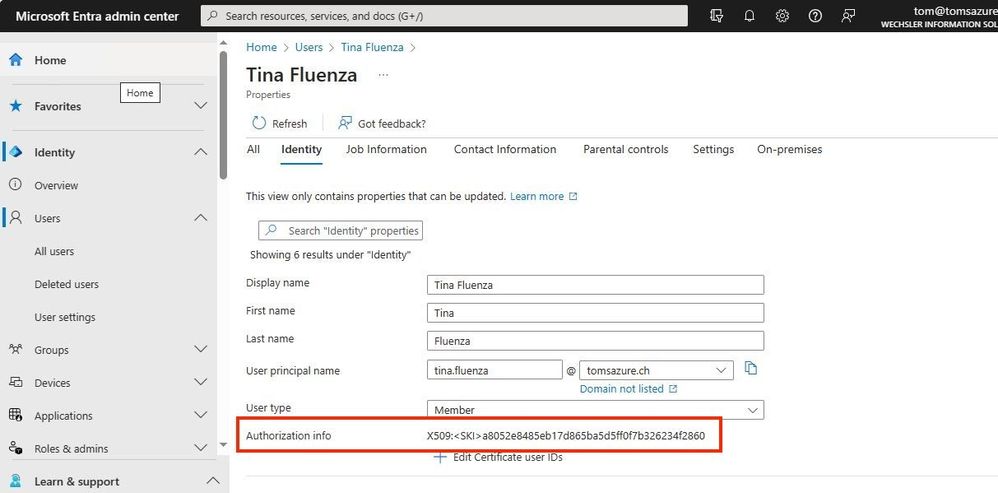
Note: Please pay attention to the syntax (X509:\<SKI\>a8052e8485eb17d865ba5d5ff0f7b326234f2860)
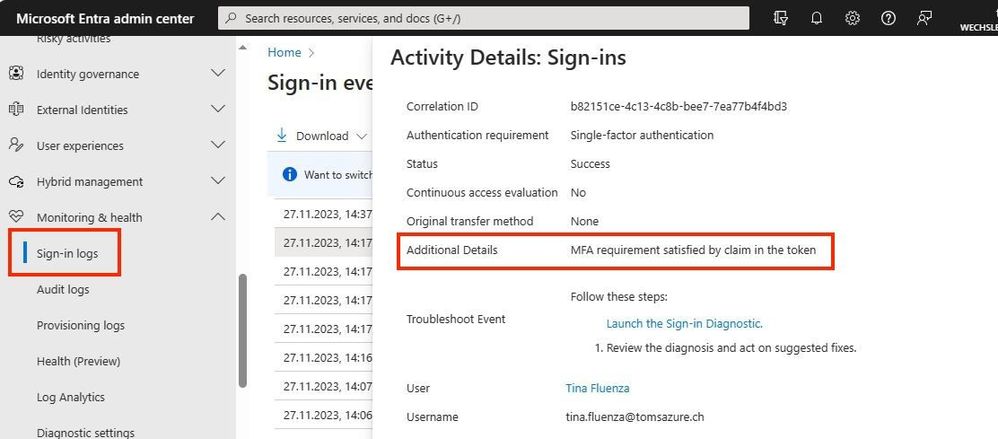
Entra ID Sign-In Logs:
"Tina Fluenza" has now registered on the portal https://myapps.microsoft.com and selected the certificate during the application process. This information can be found in the Entra ID Admin Center in the sign-in logs. With the confirmation of MFA by the claim in the token.
HAPPY BINDING!
I hope this information was helpful to you. I would like to thank you for your interest and for taking the time to read the article.
Best regards, Tom Wechsler
P.S. All scripts (#PowerShell, Azure CLI, #Terraform, #ARM) that I use can be found on GitHub! https://github.com/tomwechsler
Labels:
0 Replies