- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Advancing Modern Strong Authentication
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In a previous blog, It's Time to Hang Up on Phone Transports for Authentication, I wrote about the vulnerabilities of multifactor authentication (MFA) mechanisms such as SMS and voice. A recent MFA research study from Microsoft concludes that SMS is 40% less effective in stopping bad actors compared to the Microsoft Authenticator app.
We've also continued to bolster our Authenticator offering by upleveling security. But, despite the clear advantages to moving away from phone-based authentication, we still see around 44% of MFA traffic through SMS and voice phone calls. Bad actors continue to exploit MFA based on phone methods. Together, we can use stronger authentication methods to protect our users.
Today, I am excited to share that we’re taking steps to help you do just that. First, we’re helping you get your users registered with better methods by improving the strong authentication registration campaign capabilities. Then, to make the use of flagship capabilities like FIDO2 more accessible in more environments, we’re releasing FIDO2 support on iOS and macOS browsers in general availability.
Modern strong authentication registration campaign
In November 2021, we released registration campaigns, a feature that allows enterprises to drive adoption of modern authentication methods, starting with Microsoft Authenticator. Since its release, we’ve had thousands of enterprises depend on this feature to drive adoption of modern authentication methods, helping over 1.3 million users configure and start using Microsoft Authenticator as their primary authentication method. However, we’ve heard from customers that they need more control over a user’s registration for modern strong authentication – so we’re adding new features to help.

To start, we’re introducing a maximum prompt skip limit. With our latest updates, users will be able to postpone their registration up to three times. This will give them enough time to plan and prepare for the change, while increasing the effectiveness of your campaigns.
Secondly, for organizations set as Microsoft managed, we’re enabling the feature automatically for users that are fully dependent on SMS or voice for MFA. Beginning this month (July 2023), we’ll initiate a phased rollout of this change. Keep an eye on the Message center in the Microsoft 365 admin center where we’ll notify admins when this change will impact their organization specifically.
FIDO2 support on iOS and macOS browsers in general availability
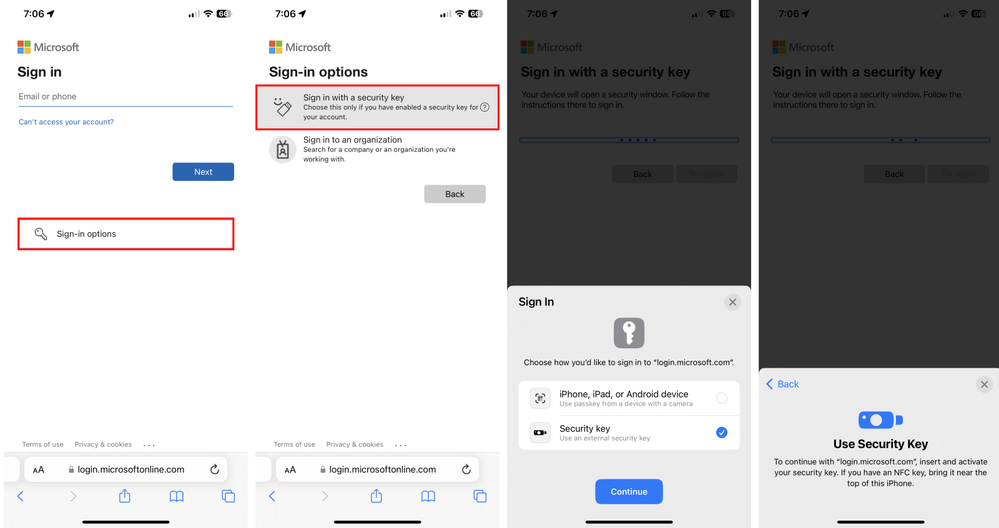
We’re also excited to announce that you can now use FIDO2 security keys to sign into Microsoft Entra ID federated applications on iOS and macOS web browsers. FIDO2 security keys provide strong, phishing-resistant authentication protected by a biometric factor (fingerprint) or PIN.
This can be especially useful for highly regulated organizations that have strict compliance requirements, such as US Government agencies who need to comply with Executive Order 14028, Improving the Nation's Cybersecurity, that require phishing-resistant authentication.
Follow the instructions on this page to enable passwordless sign-in with FIDO2 security keys.
Learn more about supported browser scenarios at https://aka.ms/FIDOMatrix.
Together we believe that these changes will make a real difference and propel millions of users to a better way of MFA.
Stay safe out there,
Alex
Learn more about Microsoft Entra:
- See recent Microsoft Entra blogs
- Dive into Microsoft Entra technical documentation
- Join the conversation on the Microsoft Entra discussion space and Twitter
- Learn more about Microsoft Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.