- Home
- Azure
- Microsoft Developer Community Blog
- The Importance of updating Azure SDKs: performance, security, and reliability
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In this article, we will explain why it is important to keep the Azure SDKs versions up to date and what are the consequences of not doing so. We will also show you where to find the support lifecycle information of each SDK and how to automate the process with tools and custom scripts.
Why keeping Azure SDKs updated is important?
Azure platform is continuously changing, which is a good thing since it is constantly adding new features and improving existing services.
Also Azure SDKs needs to change to adapt to those changes. But keeping compatibility between Azure service and many Azure SDKs version is hard (or sometimes breaking changes are needed). That is why sometimes product group decides to deprecate certain versions (and therefore if not to make breaking changes, at least testing is not performed in these versions so there is no guarantee that it will work). SDKs versions are marked as deprecated in package managers, to notify developers that they must update the SDKs.
The most obvious reason to update SDKs is to avoid application issues, due to the previously mentioned breaking changes. But there are other important reasons such as performance improvement (that can optimize costs), security and reliability.
How to be aware of deprecated SDKs?
You can manually review the support policy, to understand the lifecycle: Policies: Support | Azure SDKs, and review Azure SDK Releases in order to check the support state of the version the application is using.
Of course, doing it manually is tedious, since you will need to review the source code, get the components used and then match it with the documentation. Also, it can be harder if we do not have easy access to source code.
So, the ideal solution is to automate these checks in the CI/CD phase. There are many CI/CD tools and package managers (nuget, maven, npm, etc...). In today's article we will be focusing on Azure DevOps and nuget, but we will also tackle GitHub Actions and other repositories in future articles.
The best approach would be to use existing tools, but I could not find one that looked exactly for deprecated (out of support) nuget packages. Please add in the comments if you know one that does it. Here is a list of tools I evaluated:
- Azure DevOps Marketplace: There are useful components that can help to list nuget dependencies that are not in the latest version (although they can still be under support). Really useful to have a quick start and get to know the status of your applications.
- OWASP Dependency Check: Valuable tool to detect packages with known security vulnerabilities, but it does not focus on out of support versions.
- Azure DevOps Advanced Security: Great security tool, not only to analyze package dependencies, but also source code. But, again, only focused on security, not supportability.
- Sonar: Great Static Code Analysis tool, in the past it did not focus on Software Composition Analysis (dependencies), now they have deeper SAST that analyze dependencies, but from a security perspective.
Since it seems there is not a CI/CD tool to detect deprecated components, we can easily create a script that does it. It will be based on a dotnet command line, that already supplies a way to list used packages. Here is an article that explain this in detail: How to Scan NuGet Packages for Security Vulnerabilities - The NuGet Blog (microsoft.com)
First, we can write a PowerShell script that lists all the deprecated components (and since it is so easy) also detects packages that have more updated versions and security issues. This script will create an md file that we will use in our Azure DevOps pipeline to publish it, so anyone can read the report. The code is simple and self-explanatory, if you are not familiar with powershell, you can use GitHub Copilot to help you understand it ;)
# DEPRECATED PACKAGES REPORT
dotnet list package --deprecated --format json > report.json
# load report.json file into a variable
$report = Get-Content -Raw -Path report.json | ConvertFrom-Json
" # 💀 Deprecated packages" | Set-Content -Path nugetreport.md
"<br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
# Loop over the projects
foreach ($project in $report.projects) {
# Print the project file path
" " | Add-Content -Path nugetreport.md
" ## Project file: $($project.path)" | Add-Content -Path nugetreport.md
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
" | Package name | used version " | Add-Content -Path nugetreport.md
" ---| :--- | :--- " | Add-Content -Path nugetreport.md
# Loop over the top level packages and print their IDs
foreach ($package in $project.frameworks.topLevelPackages) {
" 💀 | $($package.id) | $($package.requestedVersion)" | Add-Content -Path nugetreport.md
}
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
}
# OUTDATED PACKAGES REPORT
dotnet list package --outdated --format json > reportoutdatedpackages.json
# load report.json file into a variable
$report = Get-Content -Raw -Path reportoutdatedpackages.json | ConvertFrom-Json
" <br/><br/>" | Add-Content -Path nugetreport.md
" # 🔔 Outdated packages" | Add-Content -Path nugetreport.md
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
# Loop over the projects
foreach ($project in $report.projects) {
# Print the project file path
" " | Add-Content -Path nugetreport.md
" ## Project file: $($project.path)" | Add-Content -Path nugetreport.md
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
" | Package name | used version | latest version " | Add-Content -Path nugetreport.md
" ---| :--- | :--- | :--- " | Add-Content -Path nugetreport.md
# Loop over the top level packages and print their IDs
foreach ($package in $project.frameworks.topLevelPackages) {
" 🔔 | $($package.id) | $($package.requestedVersion) | $($package.latestVersion)" | Add-Content -Path nugetreport.md
}
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
}
# VULNERABLE PACKAGES REPORT
dotnet list package --vulnerable --format json > reportvulnerablepackages.json
# load report.json file into a variable
$report = Get-Content -Raw -Path reportvulnerablepackages.json | ConvertFrom-Json
" <br/><br/>" | Add-Content -Path nugetreport.md
" # 💥 Vulnerable packages" | Add-Content -Path nugetreport.md
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
# Loop over the projects
foreach ($project in $report.projects) {
# Print the project file path
" " | Add-Content -Path nugetreport.md
" ## Project file: $($project.path)" | Add-Content -Path nugetreport.md
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
" | Package name | used version | advisory url " | Add-Content -Path nugetreport.md
" ---| :--- | :--- | :--- " | Add-Content -Path nugetreport.md
# Loop over the top level packages and print their IDs
foreach ($package in $project.frameworks.topLevelPackages) {
" 💥 | $($package.id) | $($package.requestedVersion) | $($package.vulnerabilities.advisoryurl)" | Add-Content -Path nugetreport.md
}
" <br/>" | Add-Content -Path nugetreport.md
" " | Add-Content -Path nugetreport.md
}
Then we only need to call that powershell in our Azure DevOps pipeline and call the "vso[task.addattachment" command to upload the report to the result of the pipeline run.
trigger:
- main
pool:
vmImage: windows-latest
# This pipeline also works in linux: ubuntu-latest
steps:
# No need to compile
# perform a dotnet restore, since under certain circumstances dotnet list package fails
- task: DotNetCoreCLI@2
inputs:
command: 'restore'
feedsToUse: 'select'
- task: PowerShell@2
inputs:
filePath: '$(System.DefaultWorkingDirectory)/generatereport.ps1'
errorActionPreference: 'silentlyContinue'
warningPreference: 'silentlyContinue'
showWarnings: true
ignoreLASTEXITCODE: true
- bash: |
echo "##vso[task.addattachment type=Distributedtask.Core.Summary;name=Dependency Analyzer;]$(System.DefaultWorkingDirectory)/nugetreport.md"
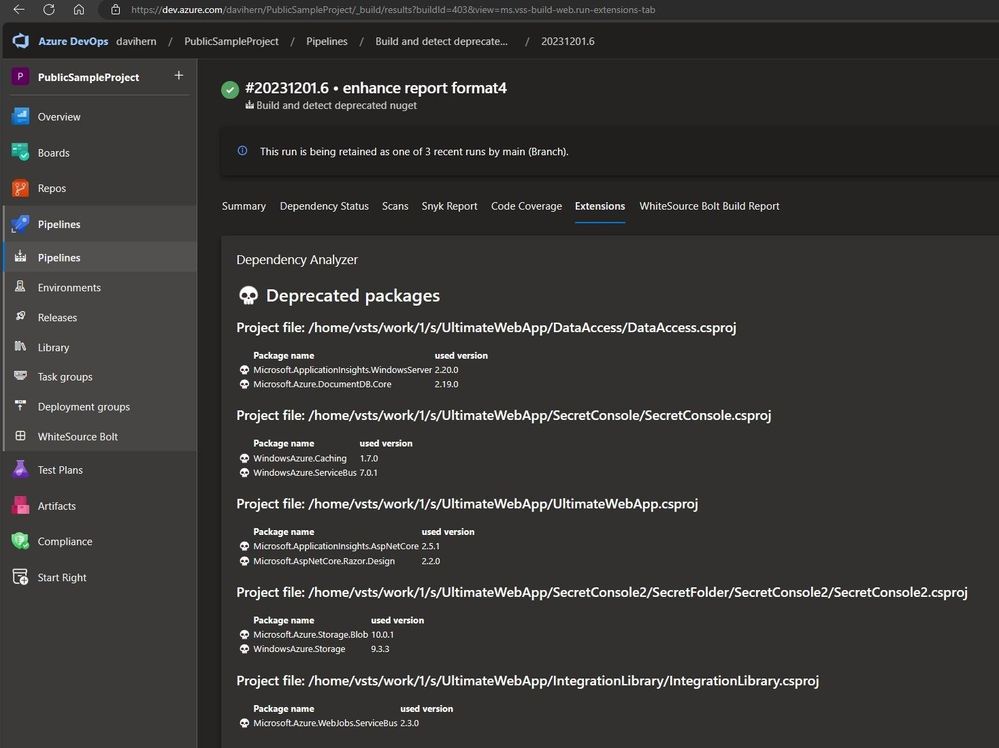
The result of the pipeline run, will display a report of the issues found, in the Extensions tab.
You can find the source code in this public Azure DevOps project: https://dev.azure.com/davihern/PublicSampleProject
Here is the output of the CI/CD pipeline: Pipelines - Run 20231201.6 (azure.com)
This simple script can be used as a kick start and can be easily adapted to perform more custom tasks, such as break builds in case of deprecated components, detect multiple versions of the same package, etc...
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.