- Home
- Security, Compliance, and Identity
- Microsoft Defender XDR Blog
- Monthly news - August 2023
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
|
Microsoft 365 Defender |
 |
||||||||||||||||||||||||
|
This is our monthly "What's new" blog post, summarizing product updates and various new assets we released over the past month across our Defender products. In this edition, we are looking at all the goodness from July 2023. |
|||||||||||||||||||||||||
|
|||||||||||||||||||||||||
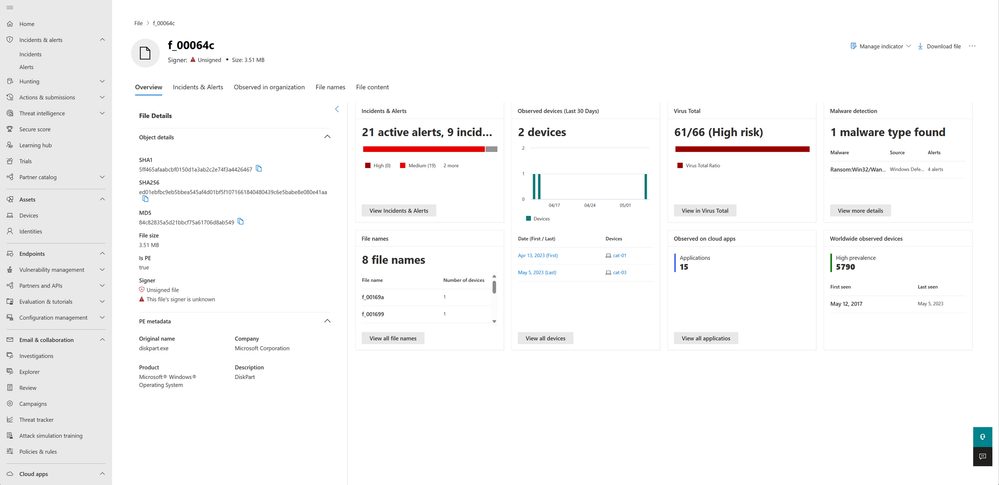
| Microsoft 365 Defender | ||||||
|
| Microsoft Security Experts | ||
|
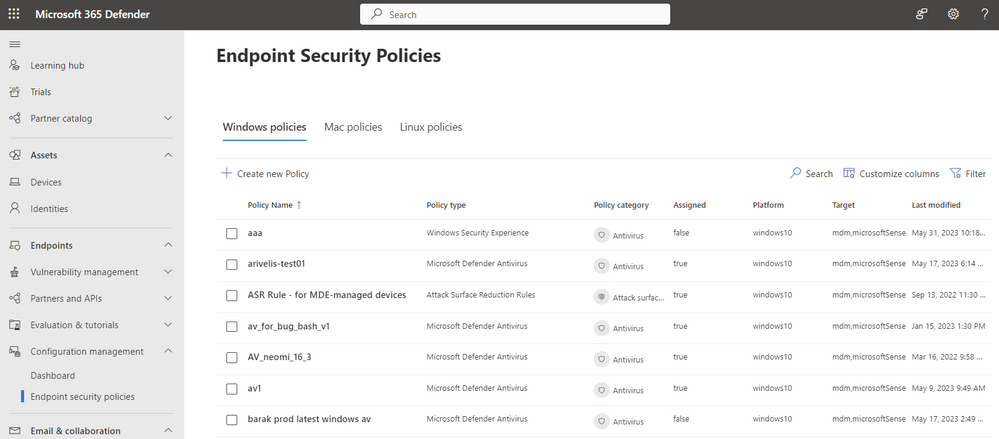
| Microsoft Defender for Endpoint | ||||||
|
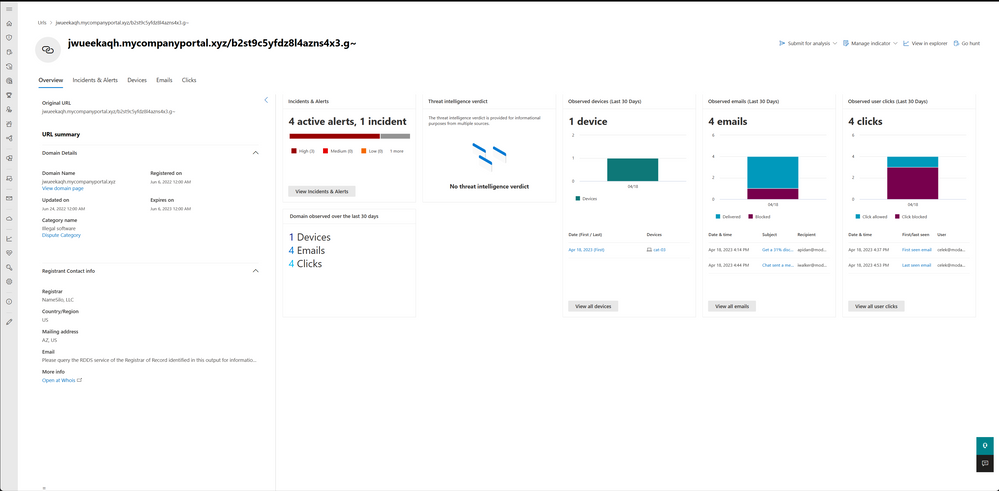
| Microsoft Defender for Cloud Apps | ||||
|
| Microsoft Defender for Identity | ||||||||||
|
| Microsoft Defender for IoT | ||
|
| Microsoft Defender for Office 365 | ||||||
|
| Microsoft Defender Vulnerability Management | ||
|
|
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.