- Home
- Security, Compliance, and Identity
- Microsoft Defender Vulnerability Management Blog
- Microsoft FAQ and guidance for XZ Utils backdoor
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
On March 28, 2024 a backdoor was identified in XZ Utils. This vulnerability, CVE-2024-3094 with a CVSS score of 10 is a result of a software supply chain compromise impacting versions 5.6.0 and 5.6.1 of XZ Utils. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recommended organizations to downgrade to a previous non-compromised XZ Utils version. See below details and Microsoft response for this vulnerability.
Change log:
4 April: Threat Intelligence, Microsoft Defender Antivirus and Defender for Endpoint added to Guidance on using Microsoft products to assess your exposure to CVE-2024-3094 section.
Frequently Asked Questions
What is XZ Utils and what is the library used for?
XZ Utils is data compression software included in common Linux distributions that plays a crucial role in compressing various file formats, including release tarballs, software packages, kernel images, and initramfs images.
Has this backdoor code been exploited?
Originally found by a Microsoft employee Andres Freund, the full extent of this vulnerability impact is still being investigated, we know it can be triggered by remote unprivileged systems connecting to SSH ports. This activation can lead to potentially compromise system integrity and performance issues.
What Linux distributions are affected?
Please see below the list of impacted Linux distributions. As this is a developing situation, we anticipate we will have further clarity for additional distributions and will continue to update this blog as necessary.
|
Fedora Rawhide |
https://www.redhat.com/en/blog/urgent-security-alert-fedora-41-and-rawhide-users |
|
Fedora 41 |
https://www.redhat.com/en/blog/urgent-security-alert-fedora-41-and-rawhide-users |
|
Debian testing, unstable and experimental distributions versions 5.5.1alpha-0.1 to 5.6.1-1. |
https://lists.debian.org/debian-security-announce/2024/msg00057.html |
|
openSUSE Tumbleweed and openSUSE MicroOS |
|
|
Kali Linux (Discovery supported) |
Are there patches or mitigations available?
CISA recommends developers and users to downgrade XZ Utils to an uncompromised version—such as XZ Utils 5.4.6 Stable. See Red Hat’s advisory for more information.
Guidance on using Microsoft products to assess your exposure to CVE-2024-3094
In the last few days our teams have worked to provide Microsoft customers with enhancements and guidance to assist in detecting software products in your environments which are affected by the vulnerability and a thorough discovery of the impacted devices which have the vulnerable software version installed. Below you will find guidance on how you can use Defender Vulnerability Management, Defender for Cloud, Microsoft Security Exposure Management, Threat Intelligence, Microsoft Defender Antivirus, Microsoft Defender for Endpoint. We will continue our work and will update this blog with more product updates and guidance.
Microsoft Defender Vulnerability Management
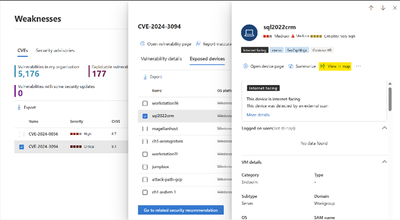
With Defender Vulnerability Management you see available information about CVE-2024-3094 in the Weaknesses inventory and can assess the presence of this vulnerability in your organization.
Note: you may need to change the default view by adding the ‘Doesn’t affect my organization’ filter option (as the vulnerability may not exist in your environment).
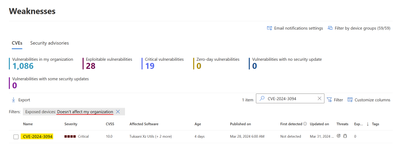
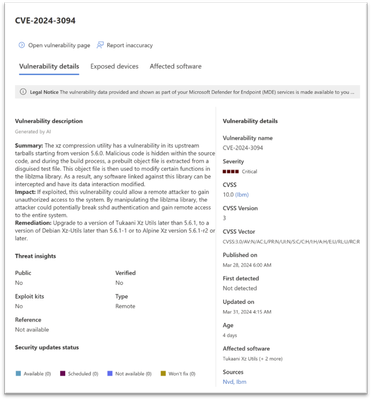
The side panel that opens up when you click the CVE includes detailed description of the vulnerability with potential impact and suggested remediation steps and additional CVE metadata.
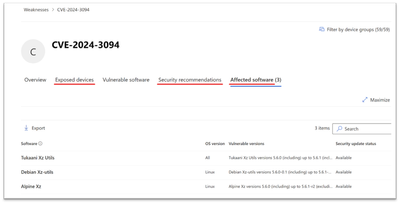
The vulnerability page provides additional insights such as list of Affected software products, list of Exposed devices which are directly exposed to the vulnerability, and Security recommendations to mitigate risk.
The following advanced hunting queries will allow security teams to perform an immediate assessment of the impact of CVE-2024-3094 on their environment.
This query will provide a list of all installed versions of XZ in your organization:
DeviceTvmSoftwareInventory
| where SoftwareName startswith “liblzma” or SoftwareName startswith “xz”
| summarize dcount(DeviceId) by SoftwareVendor, SoftwareName, SoftwareVersion
This query will provide a list of devices with vulnerable version installed:
DeviceTvmSoftwareInventory
| where SoftwareName startswith “liblzma” or SoftwareName startswith “xz”
| where SoftwareVersion contains “5.6.0” or SoftwareVersion contains “5.6.1”
Microsoft Defender for Cloud
Attack Paths
Defender for Cloud discovers all cloud resources affected by the vulnerability which are also exposed to the internet in SSH ports, and highlights them in the ‘attack path analysis’ page:
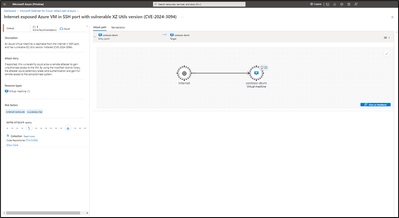
Use the following attack path title to filter the view only for exposed machines:
- “Internet exposed Azure VM in SSH port with vulnerable XZ Utils version (CVE-2024-3094)”
Security Explorer queries
You can use the Security Explorer feature within Defender for Cloud to perform queries related to your posture management across Azure, AWS & GCP, and investigate this specific CVE to find the affected machines and understand the risk associated with them.
We have developed dedicated queries for this CVE, which allow you to quickly gain an initial understanding of the risk posed by this vulnerability to your organization, with customization option:
- Virtual machines with vulnerable packages, which exposed on port 22 (Link to query)
- Virtual machines with CVE-2024-3094 detected, and exposed on port 22 (Link to query)
- Kubernetes pods running vulnerable container images, and exposed on port 22 (Link to query)
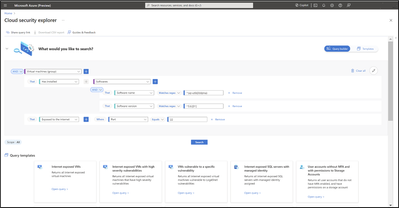
Note: The data is rolling out and should be available for all customers in the upcoming day.
Recommendations
You can use Defender for Cloud recommendations to detect vulnerable resources in your multi-cloud environment (Azure, AWS & GCP) and protect them from exploit:
- Remediate vulnerabilities - Use Defender for Cloud ‘remediate vulnerabilities’ recommendation to remediate affected VMs and containers across your multi-cloud environment.
- Secure Management ports - Use Defender for Cloud ‘Secure management ports’ recommendation to ensure the SSH ports on your machines are closed, or at least protected with just-in-time access control (Learn more>).
Microsoft Security Exposure Management
Recently released in public preview , Exposure Management unifies data and insights from security tools and provides an organizational wide view of exposure and attack paths. We mention this here as it could provide you with additional insight providing further exploration capabilities to the attack path in Defender for Cloud and the integration of attack surface map visualization in exposed devices in Defender Vulnerability Management.
Attack Surface Exploration
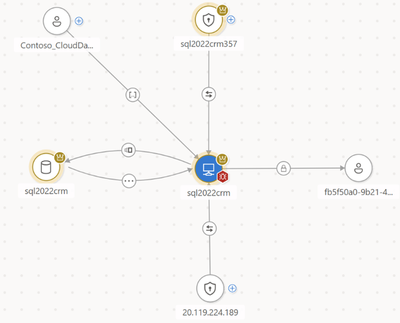
Using the new Attack Surface Map , you can achieve comprehensive visibility into entities, their insights, and relationships within your organization. This tool offers interactive capabilities to visually explore the potential attack paths an attacker could take to traverse the organization, enabling a better understanding of your organization’s attack surface and allowing you to prioritize your focus to protect your critical assets effectively.
Attack Surface Map integration in Microsoft Defender Vulnerability Management provides the ability to further explore the potential impact by accessing the organizational context of each asset. Simply select an exposed device, click on 'View in map,' and gain a clearer understanding of its significance within your environment. This streamlined approach enhances your capability to address vulnerabilities promptly and efficiently.
Microsoft Threat Intelligence
Microsoft Defender Threat Intelligence and Copilot for Security customers can learn more in the Vulnerability Profile here: https://security.microsoft.com/intel-profiles/CVE-2024-3094
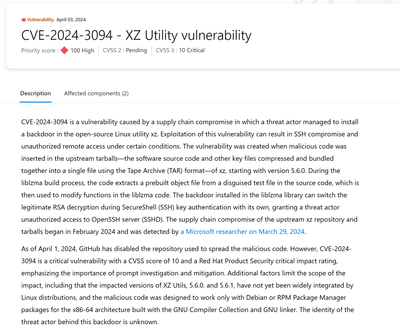
Microsoft Defender XDR customers can learn more in the CVE-2024-3094-XZ utility vulnerability report in Threat Analytics:
https://security.microsoft.com/threatanalytics3/89eab842-1d49-4b61-bacb-1f43361002c9/overview

Microsoft Defender Antivirus
Microsoft Defender Antivirus provides detections and protections for components and behaviors related to this threat under the following signatures:
- Exploit:Linux/CVE-2024-3094
- Behavior:Linux/CVE-2024-3094
- Backdoor:Linux/XZBackdoorBuild
- Trojan:Linux/Multiverze
Customers utilizing automatic updates do not need to take additional action. Enterprise customers managing updates should select the security intelligence build 1.409.17.0 or newer and deploy it across their environments.
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint provides customers with detections and alerts. Alerts with the following title in the Defender portal can indicate threat activity related to this attack on your network:
- Possible CVE-2024-3094 exploitation
As the investigation of this event continues, this blog will be updated with additional insights from Microsoft Security, the latest information obtained from the different software vendors and from publicly available security feeds and bulletins.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.