- Home
- Security, Compliance, and Identity
- Microsoft Defender Threat Intelligence Blog
- New at Secure: Corpus of Intel Profiles Available in Defender XDR
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Microsoft Defender Threat Intelligence (MDTI) team is excited to announce that we are revealing previews for each of our 350+ intel profiles to all Defender XDR customers for the first time. This represents Microsoft’s broadest expansion of threat intelligence content to non-MDTI premium customers yet, adding nearly 340 intel profiles to Defender XDR customers' view, including over 200 tracked threat actors, tools, and vulnerabilities that Microsoft has not named anywhere else.
We are also revealing the full content for an additional 31 profiles, building on our initial set of 17 profiles released to standard (free) users at Microsoft Ignite. Defender XDR customers now can access 27 full threat actor profiles, including new profiles like Periwinkle Tempest and Purple Typhoon; 13 full tool profiles, such as Qakbot and Cobalt Strike; and eight full vulnerability profiles, including CVE-2021-40444 and CVE-2023-45319.
Note: Profiles in the standard edition will not contain indicators of compromise (IOCs), which are reserved for MDTI premium customers.
Intel Profiles standard edition experience
You can visit our more than 350 intel profiles on the “Intel profiles” tab under the “Threat intelligence” blade in the left navigation menu:
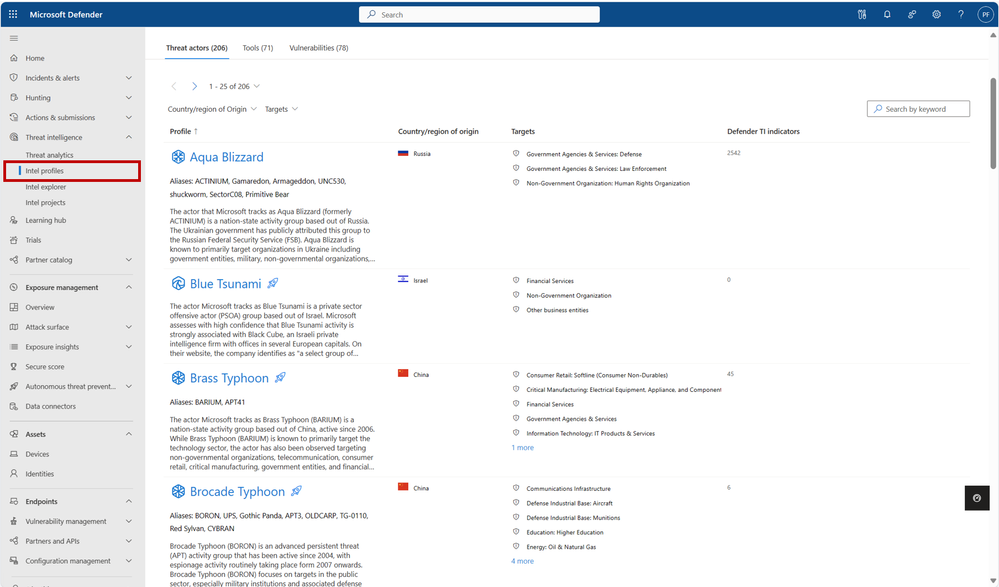
Currently, our corpus of shareable finished threat intelligence contains 205+ named threat actors, 70+ malicious tools, and 75+ vulnerabilities, with more to be released on a continual basis. To view our full catalog for each of the three profile types – Threat Actors, Tools, and Vulnerabilities – click their respective tab near the top of the page.
In the intel profiles page list view, profiles containing limited information are marked with an 
Our intel profiles containing full content can be distinguished from the limited profiles in the list view as they do not contain the icon. Full profiles can contain much additional detail beyond a Snapshot, including:
- Real details from past threat actor activity, tool usage, and vulnerability exploits, including phishing templates, malicious attachments, code excerpts and more from actual threat investigations
- Detailed TTPs (tactics, techniques, and procedures) and attack path analyses, based on both past and potential future exploitation attempts, and their corresponding MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) techniques
- Detections and Hunting Queries, which list alerts and detections that may indicate the presence of the above threats
- Advanced Hunting queries to identify adversary presence within a customer’s network
- Microsoft Analytic Rules, which result in alerts and incidents to signal detections associated with adversarial activity
- Recommendations to protect your organization against the threat
- And References for more information.
To see the full content and IOCs for all intel profiles, start a free trial or upgrade to premium.
Discovering relevant profiles
On the intel profiles page, each of the tabs for the three profile types contains a local search box, enabling you to quickly discover profiles of interest by matching keywords. Additionally, the Threat actors tab enables you to filter for the Country/Region of Origin and Targets (representing Targeted Industries) of actor groups, helping to narrow the list down to the profiles that are most important to your organization:
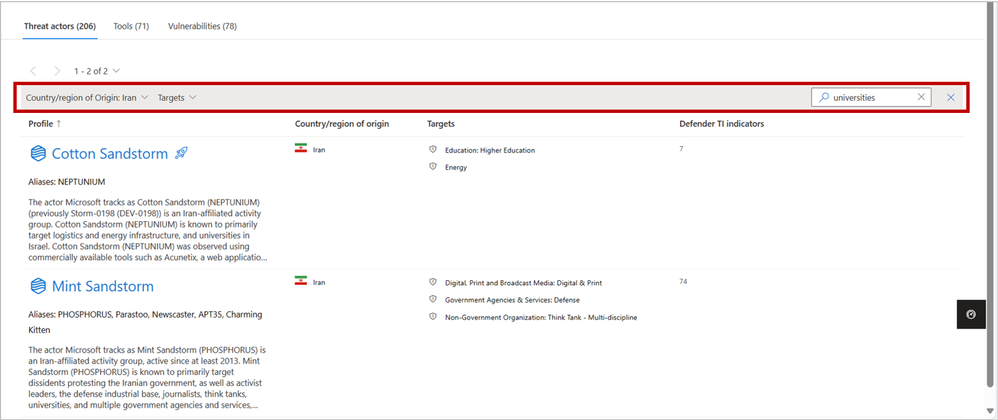
With the inclusion of MDTI results in Defender XDR’s global search bar, you also may use this top-level search to discover intel profiles from anywhere in the portal based on keywords. Refer to the linked blog for inspiration on what you can search for and what other MDTI results you can expect.
About intel profiles
Intel profiles are Microsoft’s definitive source of shareable knowledge on tracked threat actors, malicious tools, and vulnerabilities. Written and continuously updated by our dedicated security researchers and threat intelligence experts, intel profiles contain detailed analysis of the biggest threats facing organizations, along with recommendations on how to protect against these threats and IOCs to hunt for these threats within your environment.
As the defender of four of the world’s largest public clouds, Microsoft has unique visibility into the global threat landscape, including the tools, techniques, and vulnerabilities that threat actors are actively using and exploiting to inflict harm. Our team of more than 10,000 dedicated security researchers and engineers is responsible for making sense of more than 65 trillion security signals per day to protect our customers. We then build our findings into highly digestible intel profiles, so high-quality threat intelligence is available where you need it, when you need it, and how you need it.
Just one year after launching intel profiles at Microsoft Secure last year, Microsoft’s repository of shareable threat intelligence knowledge has expanded to over 205 named threat actors, 70 tools, and 75 vulnerabilities, with more added every month.
Next steps
Learn more about what you can do with the standard edition of MDTI in Defender XDR.
We want to hear from you!
Learn more about what else is rolling out at Microsoft Secure 2024, and be sure to join our fast-growing community of security pros and experts to provide product feedback and suggestions and start conversations about how MDTI is helping your team stay on top of threats. With an open dialogue, we can create a safer internet together. Learn more about MDTI and learn how to access the MDTI standard version at no cost.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.