- Home
- Security, Compliance, and Identity
- Microsoft Defender for Office 365 Blog
- Learn more about LinkedIn Smart Link Phish Campaigns
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
LinkedIn Smart Links are used by LinkedIn business accounts to deliver content and track user content engagements through the LinkedIn Sales Navigator. A typical Smart Link uses the LinkedIn domain followed by a ‘code’ parameter with an eight-alphanumeric character ID that may contain underscores and dashes. The Microsoft Defender for Office 365 security research team has observed a rise in the LinkedIn Smart Link phishing campaigns and this blog post aims at creating awareness when engaging with Smart Links, which are a legitimate, and critical tool for businesses. On LinkedIn, we help make sure the URL people click via a Smart Link is a trusted connection before it redirects. We also warn members with a security notice before they choose to click-thru to their destination, or may think twice before doing so.
However, malicious Smart Links can include other parts of information, such as obfuscated victim emails. Smart Links have proven to bypass security email gateways (SEGs) and other email security suites due to the link using a trusted domain. Threat actors are actively using Slinks in a new form of campaigns identified by Microsoft Defender for Office 365 Security Research team.
It is important to note that slinks are not inherently malicious. They are a legitimate feature used by LinkedIn business accounts to track user engagement with content. However, as with any feature, they can be abused by threat actors to carry out phishing campaigns.
Let us learn more on TPT (Tactics, Techniques and Procedure) behind these LinkedIn Smart link phishing campaigns.
Following is the standard Smart link format provided by the LinkedIn Sales Navigator.
https://www.linkedin.com/slink
From our LinkedIn Smart link campaign investigation, we observed that the smart links, instead of "scode" parameter containing alphanumeric characters, were containing obfuscated target emails. Upon clicking the malicious LinkedIn Smart Link, the user will be sent directly or through a series of redirects to the phishing website. The phishing kit will read the victim’s email from the Smart Link to autofill the malicious form, adding to the illusion of legitimacy that the victim has landed on the legitimate Microsoft sign-in page.
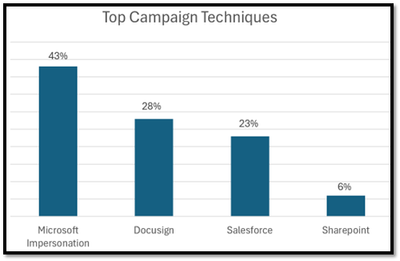
Following are some of the popular brands that were impersonated by the LinkedIn Smart Link campaigns.
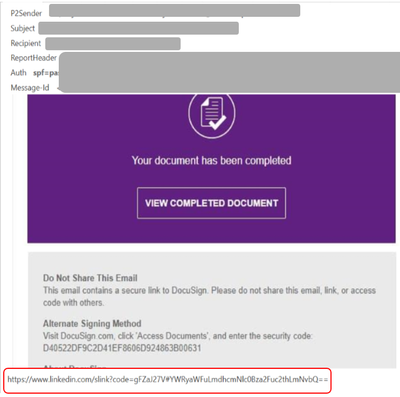
DocuSign Campaign template
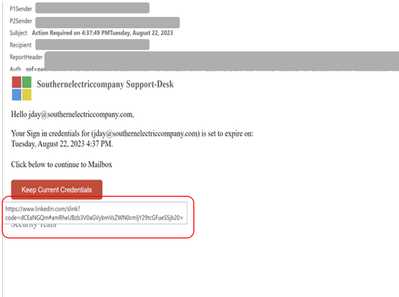
Microsoft Impersonation Template
SharePoint Campaign template
The observed pattern from these Smart Link Campaigns are outlined below.
- Emails employ a generic subject line to mimic benign behaviour
- Email body features a single image with a LinkedIn Smart Link embedding.
- Multiple redirections are employed before presenting the Phishing page to evade detection systems.
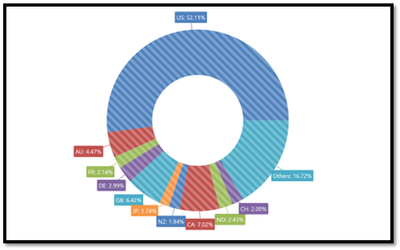
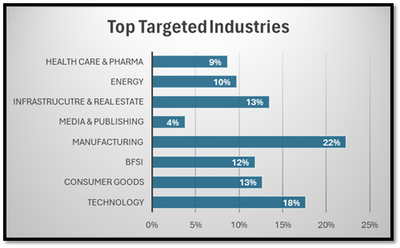
Following are the insights the research team observed from the Smart Links campaign data from Sep ‘23 to Dec ‘23.
Recommendations
It is important to be vigilant and cautious while opening emails, especially those that contain links. It is advisable to verify the authenticity of the email and the sender before clicking on any links or downloading any attachments. Especially when commonly used brands are part of email body that triggers the uses to click on the URLs, the users need to pay extra attention on the logo, content, redirection and the final landing URL legitimacy.
Organizations are highly recommended to use email security gateways like Microsoft Defender for Office 365 to reduce the exposure of such campaigns to their employees. Security teams are also recommended to train their users to stay resistant to such vulnerable emails by deploying advanced Simulation trainings through Defender for Office 365 attack and simulation capabilities.
If you are already using Defender for Office 365, we encourage your SOC/Security teams to report any such suspicious emails landing in the inboxes of your employees so that we can investigate in case of any policy overrides or sophisticated scenarios used by the threat actors.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.