- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Manage your devices with ease using dynamic rules for device tagging in Microsoft Defender
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In today's ever-evolving cybersecurity landscape, where effective asset management is critical, tags have emerged as a powerful tool for streamlining security operations across various scenarios. Given the dynamic nature of devices, which often undergo updates, replacements, or reconfigurations, the proper management of tags as a tool for device context becomes essential for upholding strong security hygiene.
Today we are excited to announce that dynamic rules for tagging devices is now generally available. This feature enables security teams to create and manage rules that automatically assign and remove tags from devices based on user-defined criteria directly in the Microsoft Defender portal.
Dynamic tagging benefits
- "Set and forget" convenience: Dynamic tags simplify tag management, saving valuable time and effort for security teams. Automating tagging with dynamic rules reduces manual efforts, minimizing management overhead, and ensures accurate and up-to-date device classification for enhanced security insights.
- Optimized device management: Dynamic tags facilitate efficient device tracking and management, enabling organizations to monitor devices effectively and allocate resources with streamlined processes.
- Proactive compliance management: Dynamic tags can simplify compliance by automatically categorizing non-compliant devices, proactively identifying risks, and ensuring a continuous and compliant security posture.
The challenge of managing tags in a dynamic environment:
Tags offer various benefits – they enable security teams to categorize devices based on multiple attributes like operating systems, onboarding status, naming convention and more, supporting various scenarios in incident response, case management, asset tracking, and automated security workflows. Security teams using tags can be more efficient, organized, and can translate valuable insights into action fast – enhancing the overall security posture of their organization.
However, as organizations grow and the security landscape becomes increasingly complex, manually managing device tags becomes increasingly unmanageable. The dynamic nature of the environment poses several challenges, like constant changes in device attributes, evolving security requirements, and rapidly shifting threats. With each update or modification, maintaining tags for devices demands substantial management overhead. The resulting complexity can lead to errors, inconsistencies, and inefficiencies in security operations.
Making tag management simple
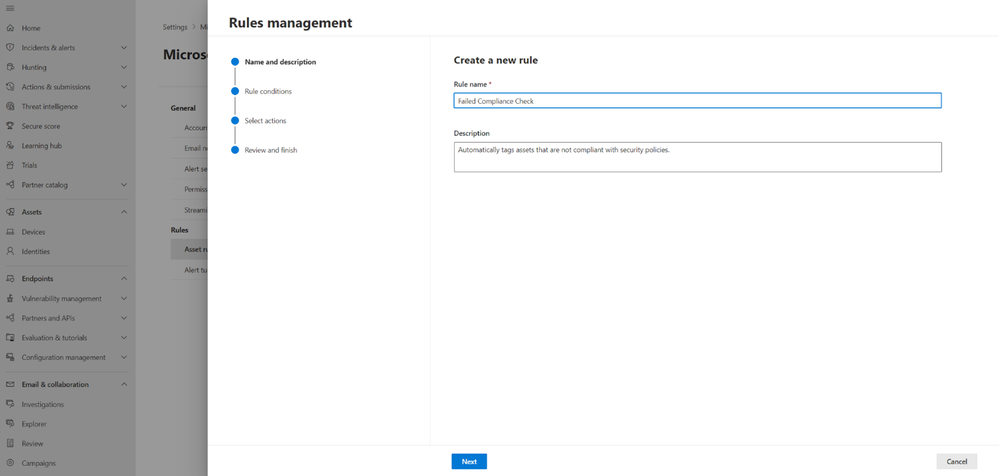
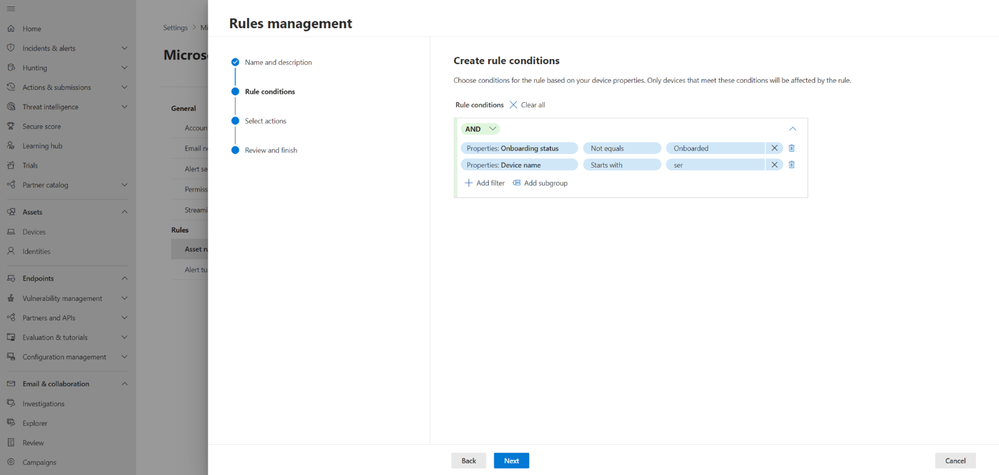
To address the challenge of tag management in an evolving environment, admins can now create dynamic rules that define certain conditions using multiple attributes. As devices meet or do not meet these specified criteria, the associated tags are automatically applied or removed. This fluid approach ensures that device tags stay up-to-date, relevant, and aligned with the organization's evolving security requirements.
Figure 1: A new way to create tags - rule-based tagging
Figure 2: Dynamic tagging rules management screen
Figure 3: Creating a new rule
Figure 4: Building the rule query
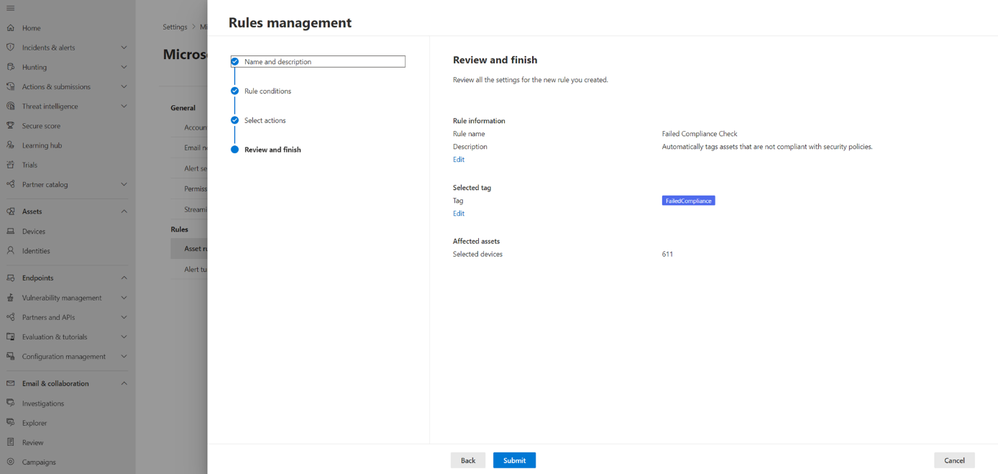
Figure 5: Review rule and potential impact (“affected assets”)
Note: It may take up to 1 hour for changes to be reflected in the portal.
Start streamlining device tagging, today
Dynamic tagging simplifies device management with a simple setup, reduces the need for manual updates to device tags, and enhances security insights with accurate and up-to-date tags. This helps security teams optimize device management, automate security workflows, and proactively maintain compliance.
To learn more about dynamic tagging read the official documentation on Microsoft Learn
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.