- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Unleashing the Power of Microsoft Defender for Cloud – Unique Capabilities for Robust Protection
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Overview
Microsoft Defender for Cloud (MDC) is a cloud-native application protection platform (CNAPP) that is made up of security measures and practices that are designed to protect cloud-based applications from various cyber threats and vulnerabilities.
In this article we make a case that the unique capabilities provided by MDC will be hard to replicate with a customized/3rd party solution.
Note that there are many use cases where you will find MDC to have a natural edge. However, for brevity, we have picked a few common scenarios. So, the list below is not meant to be exhaustive, rather, representative.
What makes Microsoft Defender for Cloud Unique
Given that MDC is Azure Native (First Class citizen) it has pre-built integrations with other Azure Services. This allows MDC to:
- Reduce management overhead
- Generate security insights with push button deployment
- Scale natively with customer workloads
- Reduce threat detection latency
- Present accurate threat posture
Scenario 1 – Detecting threats at Cloud Management Layer
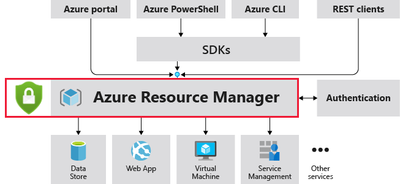
The cloud management layer is a crucial service connected to all your cloud resources. Because of this, it is also a potential target for attackers. Consequently, we recommend security operations teams monitor the resource management layer closely.
Microsoft Defender for Resource Manager automatically monitors the resource management operations in your organization, whether they're performed through the Azure portal, Azure REST APIs, Azure CLI, or other Azure programmatic clients. Defender for Cloud runs advanced security analytics to detect threats and alerts you about suspicious activity.
Fig 1. Defender for Resource Manager
Here is the list of Resource Manager alerts detected: https://learn.microsoft.com/en-us/azure/defender-for-cloud/alerts-reference#alerts-resourcemanager
Security alerts from Defender for Resource Manager are based on threats detected by monitoring Azure Resource Manager operations. Defender for Cloud uses internal log sources of Azure Resource Manager as well as the Azure Activity log, a platform log in Azure that provides insight into subscription-level events. So, replicating this functionality will be extremely arduous.
Scenario 2 – Detecting malware in Storage Objects in near real time
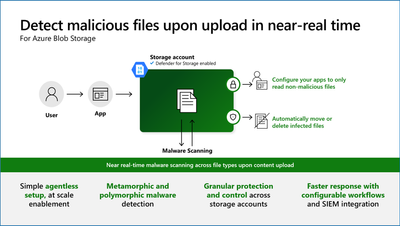
Malware Scanning in Defender for Storage helps protect your storage accounts from malicious content by performing a full malware scan on uploaded content in near real time, using Microsoft Defender Antivirus capabilities.
The Malware Scanning capability is an agentless SaaS solution that allows for simple setup at scale, with zero maintenance, and supports automating response at scale.
Fig 2. Malware scanning (near real time)
Since the integration with the scanning engine is done at Service level for near real time scan, this becomes a SaaS solution that allows simple enabling at scale with zero maintenance. This is very hard to replicate with a non-native Solution.
Scenario 3 – Near real time Database Protection with minimal impact to the workload
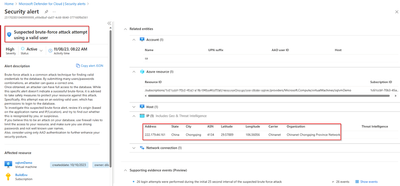
Defender for Databases allows you to protect your entire database estate with attack detection and threat response for the most popular database types in Azure. This advanced threat protection service continuously monitors your SQL servers for threats such as SQL injection, brute-force attacks, and privilege abuse.
Defender for Database is a one-click enable capability that has native integration with your Azure SQL, Cosmos, and Open-Source Relational Databases on Azure.
Because of this integration once enabled, the plan will monitor for activities on your database without any routing or configurations from your side.
Fig 3. Bruteforce detection
Refer https://techcommunity.microsoft.com/t5/microsoft-defender-for-cloud/better-together-defender-cspm-da... for more details and walkthrough.
Scenario 4 – Scaling protection with your workloads and as you modernize.
Scaling with your resources
Defender for Cloud is enabled at the subscription level so as your workloads scale the corresponding Defender for Cloud plans will protect your new resources.
Defender for Cloud automatically creates a default security policy for each of your Azure subscriptions. Defender for Cloud doesn't interfere with your normal operational procedures. Defender for Cloud passively monitors your deployments and provides recommendations based on the security policies you enabled.
When you add new resources (VMs, SQL DBs) to your Azure environment, Defender for Cloud automatically discovers these resources and begins to monitor their security, including PaaS web roles and worker roles. If Data Collection is enabled in the Security Policy, more monitoring capabilities are enabled automatically for your virtual machines.
Protection as you modernize
As you mature your Cloud workloads, you might decide to migrate from a VM based to a Container or API based workload. Defender for Cloud provides several plans that map to different types of Cloud Native Compute and Storage so your workloads will never be in an exposed state before, during, and after the migration. Each of these plans detects threats relative to that specific type of resource (https://learn.microsoft.com/en-us/azure/defender-for-cloud/alerts-reference)
Migrating to a secure environment
As you migrate to cloud, you want to make sure that the environment is set up securely and stays in a secure state post migration. Defender for Cloud recommendations that are part of Foundational CSPM (free) provide you security recommendations provide practical steps to remediate security issues and improve security posture. In addition, you also get a secure score that aggregates security findings into a single score so that you can assess, at a glance, your current security situation to make impactful improvements. The higher the score, the lower the identified risk level is. (https://learn.microsoft.com/en-us/azure/defender-for-cloud/concept-cloud-security-posture-management...)
Scenario 5 – Integration with your existing native IaC pipelines
Given that Microsoft Defender for Cloud is a native service, as you manage your infrastructure as a DevOps pipeline, you can very easily incorporate MDC. For example, you can enable at scale using REST API. A similar approach is applicable for enabling individual plans. This reduces your reliance on 3rd party libraries and APIs. These libraries not only introduce more risk in your environment, but also may not be supported by your IaC tool chain.
POST https://management.azure.com/subscriptions/{subscriptionId}
/providers/{resourceProviderNamespace}/register?
api-version=2021-04-01
More details:
Scenario 6 – Maintaining an access related blast radius
Defender for Cloud leverages Azure RBAC so you can continue to monitor the usage of the roles and associated user identities using existing roles and workflows. (see fig below) (https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-planning-and-operation...)
Fig 4. Defender for Cloud user personas
If a customer were to deploy a third-party solution, then:
- The solution will require its own set of Roles that would need to be monitored.
- The users most likely will be managed within the 3rd party solution itself. This adds additional monitoring requirements for the customer unlike in case of MDC
Summary
As we saw, MDC has a unique value proposition for integrating into your cloud security portfolio either as the primary solution or as a complement to your existing Cloud Security Posture Management (CSPM)
- What is Microsoft Defender for Cloud: Microsoft Defender for Cloud is a cloud-native application protection platform that protects cloud-based applications from various cyber threats and vulnerabilities.
- How Microsoft Defender for Cloud is unique: Microsoft Defender for Cloud has pre-built integrations with other Azure Services, which reduces management overhead, generates security insights, scales with customer workloads, reduces threat detection latency, and presents accurate threat assessments.
- Some use cases of Microsoft Defender for Cloud: Microsoft Defender for Cloud can detect threats at the cloud management layer, scan for malware in storage objects in near real time, protect databases from SQL injection and brute-force attacks, scale protection with the workloads and modernization, and integrate with native IaC pipelines.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.