- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Securing DevOps with Microsoft's CNAPP: Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
As the landscape of DevOps continues to expand and confront increasingly sophisticated security threats, the need for proactive attack surface reduction measures has never been more critical. To enhance DevOps security and prevent attacks, Defender for Cloud, a Cloud Native Application Protection Platform (CNAPP), is enabling customers with new capabilities: DevOps Environment Posture Management, Code to Cloud Mapping for Service Principals, and new DevOps Attack Paths. These features represent a strategic shift towards a more integrated and holistic approach to cloud native application security throughout the entire development lifecycle.
DevOps Environment Posture Management
DevOps Environment Posture Management offers a deep dive into the security health of the cloud-native application lifecycle. Through deep scanning of source code management systems, Defender for Cloud identifies weaknesses in resources such as pipelines, repositories, and service connections, identifying potential vulnerabilities in platform configurations.
DevOps Environment Posture Management recommendations are critical for starting secure at the source and enhancing the overall security posture of cloud native applications end-to-end. They address key vulnerabilities and potential attack vectors in Azure DevOps and GitHub environments, including:
- Azure DevOps Pipelines: Ensure that secrets are not accessible in builds of forks to prevent external entities from accessing internal build pipeline secrets.
- GitHub Repositories and Organizations: Implement protection policies for default branches to safeguard against unauthorized or malicious changes.
- Azure DevOps Service Connections, Variable Groups, and Secure Files: Recommendations to limit the access of the secure CI/CD resources to only pipelines that need access to reinforce least privilege access and prevent against privilege escalation threats.
Imagine a scenario where a developer inadvertently allows Azure DevOps pipelines to expose secrets in forked builds. This could potentially allow external threat actors to access sensitive internal data. By implementing recommendations from the DevOps Environment Posture Management, such as ensuring secrets are not accessible in builds of forks, organizations can prevent these kinds of security breaches.
An example of the recommendation for “Azure DevOps pipelines should not have secrets available to builds of forks” is in Figure 1 below. This recommendation provides a clear description of the issue, detailed remediation steps, and a list of all the unhealthy and healthy Azure DevOps pipelines. Additionally, the recommendation also contains a severity level and mapping to the DevOps Threat Matrix tactics.

By clicking on the unhealthy resource, customers can gain more information on the Resource health blade, including the Azure DevOps Organization and Project and a direct link to the affected component.
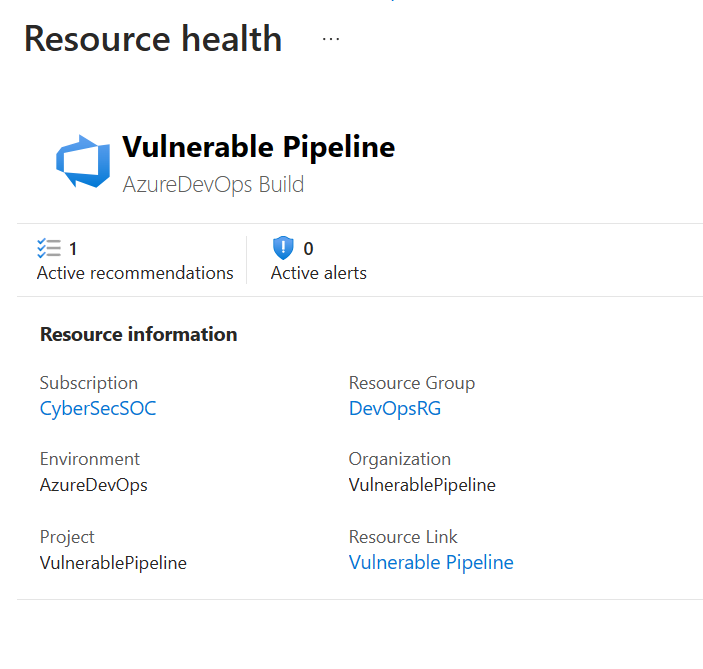
This information can also be found in the DevOps Security workbook in the Posture Management tab.
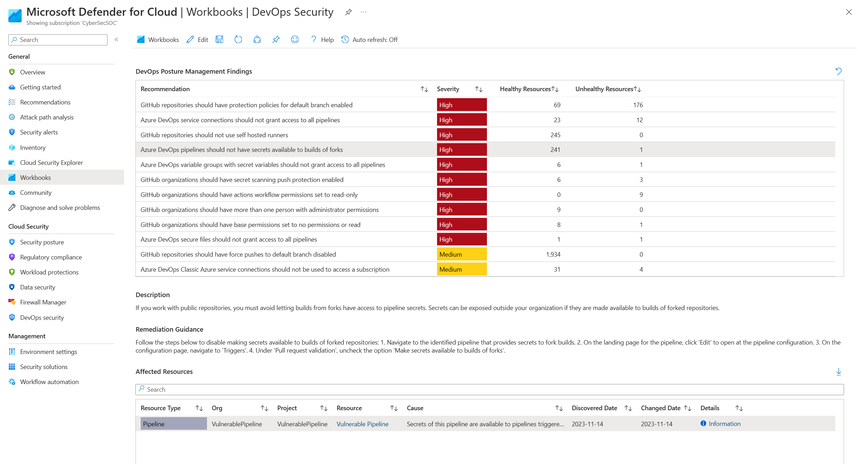
When implemented, these recommendations significantly strengthen the security posture of the source code environments used to develop cloud applications.
Service Principal Mapping
Enhancing the capabilities of posture management recommendations, Service Principal Mapping in Defender for Cloud connects CI/CD pipelines directly to cloud environments. This connection is crucial for providing visibility and control from code development all the way to cloud deployment.
CI/CD pipelines typically interact with cloud resources using a Service Principal (SPN) as their identity. However, this can create security risks, especially when SPNs are over-privileged or when pipelines, such as those in public Azure DevOps repositories, lack sufficient security controls. Such weaknesses can turn these pipelines into targets for malicious actors, who may exploit these weaknesses to gain unauthorized access to cloud resources. The consequences of these breaches can range from data leaks to unauthorized alterations of critical infrastructure, posing significant threats to organizational security.
Service Principal Mapping addresses this risk by offering visibility into the specific Azure resources accessible by each SPN. This creates a clear and comprehensive map of access points within the cloud environment, which is vital for organizations to accurately assess and manage the extent of cloud access privileges granted to their DevOps platforms. By exposing these access relationships and evaluating the risks associated with them, Defender for Cloud reduces the attack surface and enhances the security posture of applications from code to cloud.
To test this in your environment, first ensure you have a connector to Azure DevOps and/or GitHub in Defender for Cloud with Defender CSPM enabled, and then run the following queries:
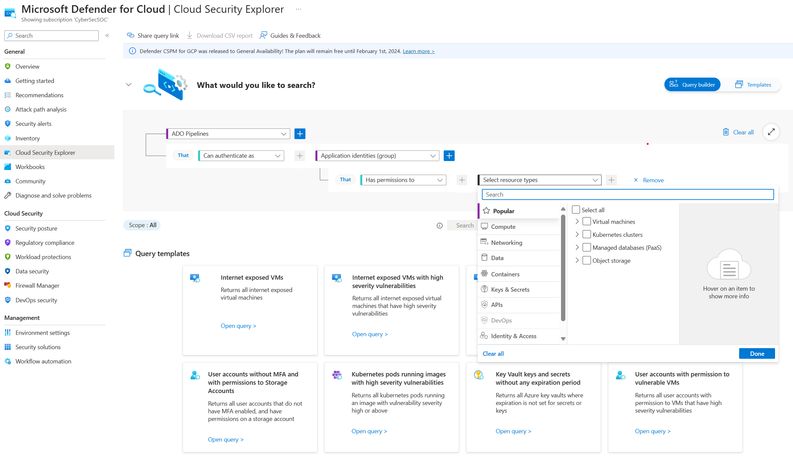
DevOps Attack Paths
By leveraging insights from the new recommendations and mapping capabilities, our Microsoft Security research team has released new attack path, highlighting the most critical risks within a customer’s environment.
As an example, we now have an attack path for a GitHub repository without branch protection rules that has permissions to connect to Azure resources. This means that if the repository were to be compromised, then an adversary would be able to modify and execute the GitHub workflow to compromise your Azure environment.

Conclusion
DevOps security in Defender for Cloud offers a comprehensive approach to securing the cloud-native application development lifecycle. This approach extends beyond just protecting individual DevOps components to secure the entire software development process, from the initial coding phase to the final deployment in the cloud. As technology evolves and new cybersecurity threats emerge, these capabilities assist in proactively strengthening the posture of applications, ensuring that organizations can safely navigate the complexities of cloud-native development.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.