- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Proactively secure your Google Cloud Resources with Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
In today's digital landscape, where over 90 percent of organizations have embraced multicloud1 solutions, security teams face the growing complexity of maintaining robust security controls and cloud security posture across multi-cloud environments. Microsoft Defender for Cloud offers protection for cloud infrastructure, applications, and data providing a single contextual view of cloud risks across Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP).
According to the Google Cloud Threat Horizons Report, credential theft accounted for over 60% of compromise factors and cloud misconfiguration accounted for 19% of compromise factors.
In this blog, I will walk through a few scenarios of misconfigured GCP resources and how Microsoft Defender for Cloud can help proactively identify misconfigurations and allow security teams prevent risks and remediate quickly.
Proactively secure your GCP resources
On 15 August 2023, Defender CSPM plan support for GCP resources was released in public preview. Customers now can leverage the power of Defender CSPM contextual cloud security graph and attack path analysis capabilities to proactively secure GCP resources. Learn more about the cloud security graph, attack path analysis, and the cloud security explorer.
To have this capability working you need first to enable Defender CSPM Plan on your GCP Connector. Please refer Connect your GCP project - Microsoft Defender for Cloud | Microsoft Learn
The use case scenarios discussed in this blog depict hypothetical situations to explore and understand how Defender CSPM can help protect your Google cloud resources.
Scenario 1:
Tailwind Traders is a well-established retailer with a strong online presence. They use Microsoft Azure as the primary cloud provider for their business applications and back-office operations. They have chosen Google Cloud Platform (GCP) to host their e-commerce website. Tailwind implements Microsoft Defender for Cloud across their entire cloud infrastructure, including Google Cloud and Azure.
Their ecommerce application hosted on Google Cloud Compute Engine VM instances. They have a specific VM instance, named "WebServer", that is exposed to the internet. “Webserver” instance is configured with a Google Cloud service account that has access to a critical GCP SQL database instance, which stores customer data, including personal information, payment details, and order histories. The service account uses application default credentials to access the SQL database.
Due to improper configuration and lack of regular security updates, this VM instance has several known vulnerabilities, such as outdated software packages and weak password policies.
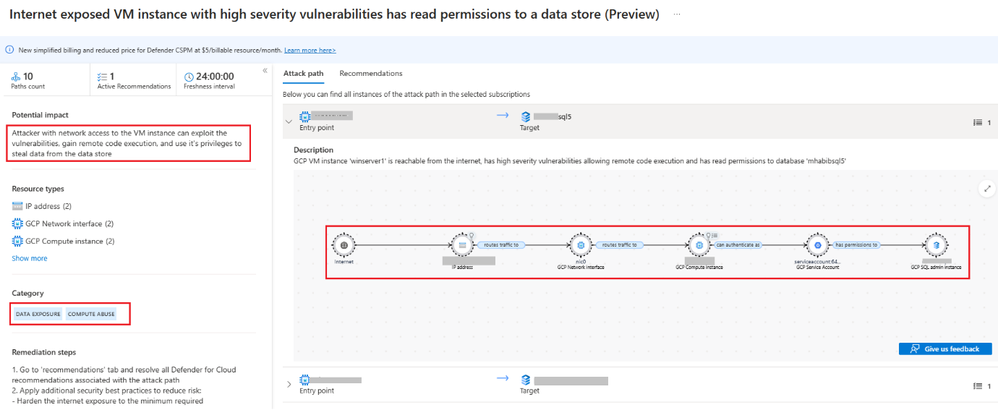
Defender CSPM identifies the security issue as an attack path, “Internet exposed VM instance with high severity vulnerabilities has read permissions to a data store (Preview)”
Security Risks:
The Attack path Analysis highlights the risk involved is “Data Exposure” and “Compute Abuse”.
Click on the VM Instance and Insights tab specifies the details of vulnerabilities and the VM Internet exposure. The VM's vulnerabilities, including outdated software and weak security settings, make it susceptible to exploitation by malicious actors. Attackers can potentially gain unauthorized access to the VM, compromising its data and functionality.
Click on the attack path ‘has permissions to’ understand the risk involved with service account associated with the VM. Since the VM has a GCP service account with access to the SQL database, if an attacker compromises the VM, they may also gain unauthorized access to sensitive customer data stored in the database.
Remediation Steps:
To address the security risks associated with this scenario, security team should consider implementing the following mitigation strategies:
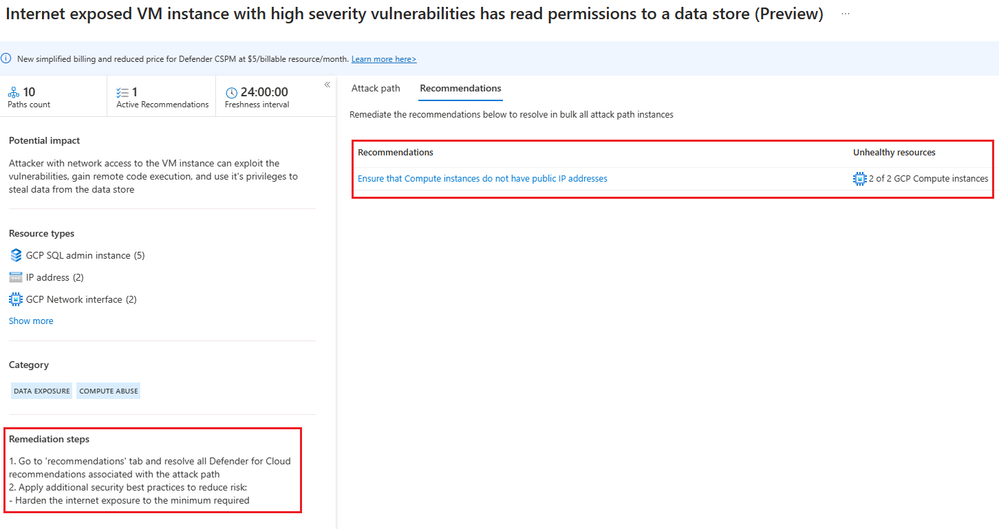
- Go to 'recommendations' tab and resolve all recommendations associated with the attack path.
- Regularly scan and patch the VM instance to address known vulnerabilities.
- Review and restrict the permissions granted to the GCP service account associated with the VM. Ensure it only has the necessary privileges to access the SQL database.
Scenario 2:
Lamna Healthcare Company implements the Fast Healthcare Interoperability Resources (FHIR) standard to achieve interoperability with healthcare systems and is hosted on Azure. Defender for Cloud is used to monitor and protect their FHIR systems, ensuring compliance and threat detection.
As part of their multicloud strategy, Lamna Healthcare decided to use Google Cloud to manage patient records, appointment scheduling, and billing. They have set up Cloud SQL database instances for storing patient data, and unfortunately, these instances use basic authentication (username and password) for access. Furthermore, due to misconfiguration, these instances have been left open to the internet.
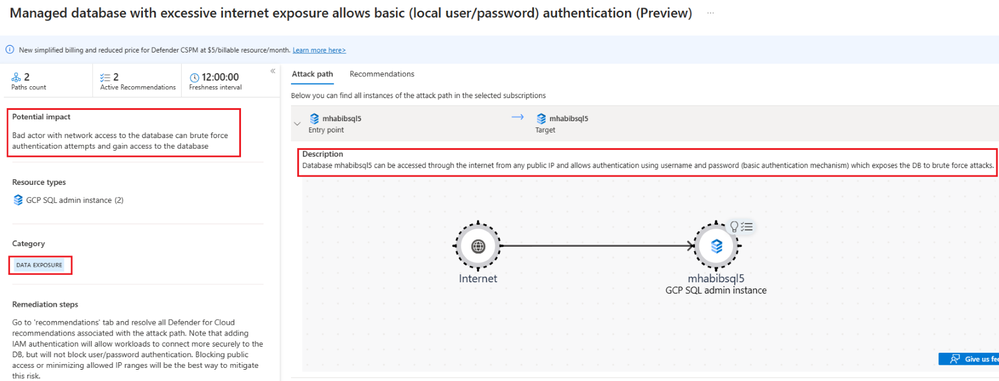
Lamna Healthcare Security Team connected their Google Cloud Environment to Defender for Cloud. Defender CSPM attack path analysis identifies the risk, as “Managed database with excessive internet exposure allows basic (local user/password) authentication (Preview)”.
Security Risks:
The Attack path Analysis highlights the risk involved is “Data Exposure”.
Basic authentication relies on simple username and password combinations, which are susceptible to brute-force attacks. Attackers can repeatedly attempt to guess or crack the credentials, potentially gaining unauthorized access to sensitive patient health records.
Open access to patient records can lead to serious breaches of privacy and violations of healthcare data protection regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States or similar laws in other countries.
Click on the SQL Instance provides more insights on the ports exposed to the Internet and Allows basic Authentication.
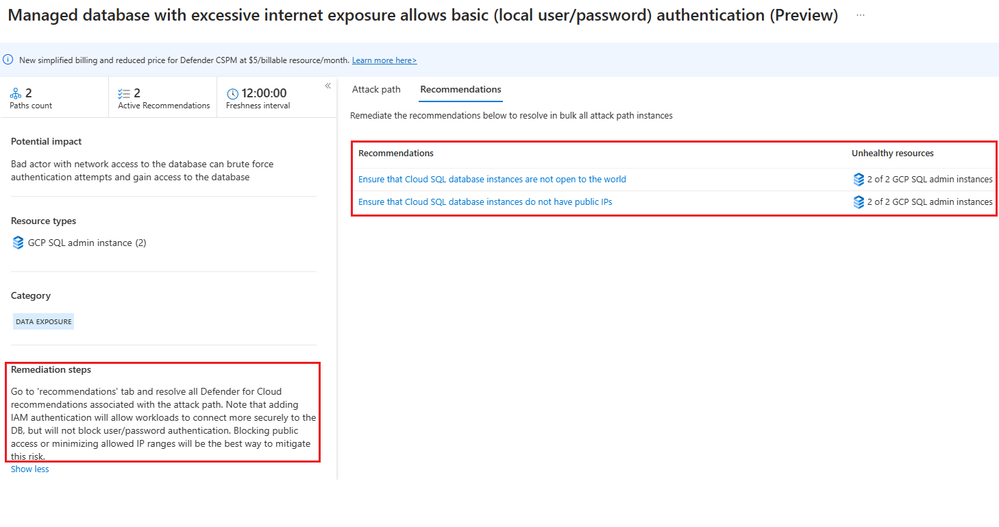
Remediation steps:
To address the security risks associated with Google Cloud SQL instance, security team should consider implementing the following mitigation strategies:
- Go to 'recommendations' tab and resolve all recommendations associated with the attack path.
Scenario 3:
Humongous Insurance is a leading health insurance company offering a wide range of healthcare coverage plans. The Insurance company relies on Microsoft Azure for critical backend services, particularly those related to compliance and customer data security.
The mobile app for policyholders, is hosted on Google Cloud. The sensitive patient medical records and financial data is encrypted using GCP's Key Management Service (KMS).
The company decided to use Defender for Cloud to enforce security policies, meet regulatory requirements, and ensure that Azure and GCP environments adheres to best practices.
Due to a configuration error by an inexperienced cloud administrator, the GCP Key Rings that contain encryption keys for securing patient data are inadvertently made publicly accessible.
Security Risks:
Anyone on the internet can access the key rings without any authentication or authorization.
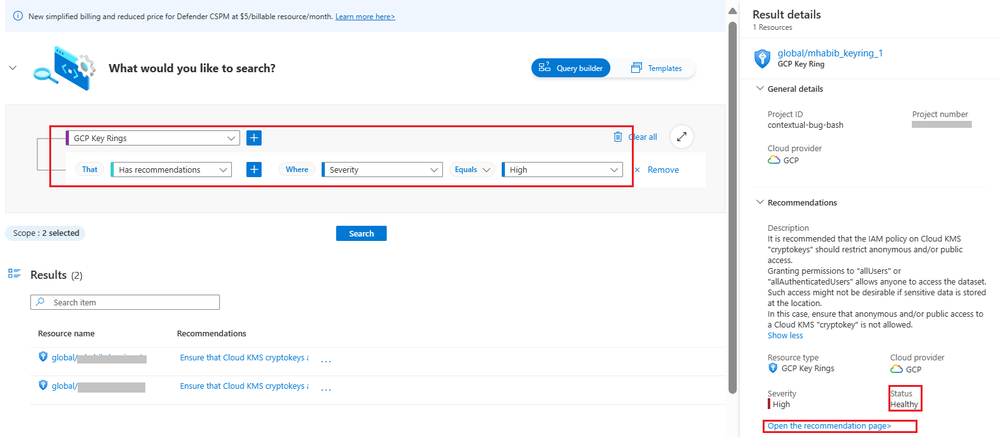
Security Administrator can use Cloud Security Explorer to query if the organizations Cryptographic keys are protected. Select “Keys & Secrets”, under Keys management services, select “GCP Key Rings” as shown below.
Select Recommendations with High Severity as shown below, and click on "search"
Remediation Steps:
Ensure the Status is "Healthy" for all the keys. If the status is "Unhelathy", open the recommendation page and implement Manual remediation steps or click on "Take Action" as shown below.
Scenario 4:
Contoso is a popular retail company with an online and physical store presence. The inventory management system is hosted on Azure and integrated with their suppliers' systems for seamless data exchange.
They use Google Cloud services to power its e-commerce platform. Contoso uses the Google Maps API key to power the store locator feature on their website and mobile app. The API key is integrated into their website and mobile app, allowing for real-time location-based services.
Contoso integrates Google Cloud Vision API into their mobile app to provide a visual search feature. Customers can take a photo of a product or upload an image, and the API identifies similar products from Contoso product catalog.
They have created several API keys for their GCP project to access various Google services, including Google Maps, Google Cloud Storage, Google Cloud Vision. However, due to oversight, these API keys have not been properly restricted to only the necessary APIs. Over time, Contoso has neglected to rotate these API keys regularly.
Contoso has a Security Audit in 3 months and their management want to Educate developers and administrators about the importance of securing API keys, restricting permissions, and adhering to security best practices. Contoso’s security team started using Defender for Cloud for a centralized security posture management across Azure and Google Cloud.
Security Risks:
- By not restricting API keys to specific APIs, API keys have overly broad permissions. This means that if one of these API keys is compromised, an attacker could potentially access and abuse multiple Google services, including those that are not required for the application's functionality.
- If an API key provides access to Google Cloud resources, an attacker could modify or delete critical resources, disrupting business operations and potentially causing data loss.
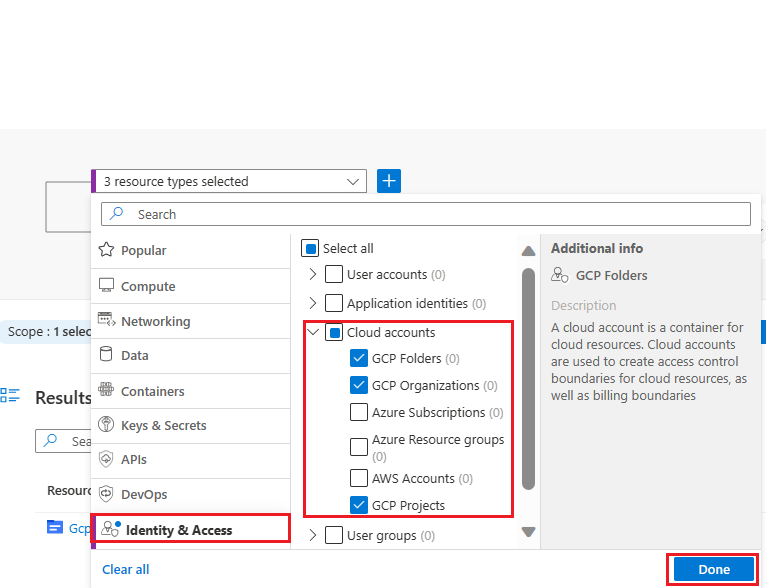
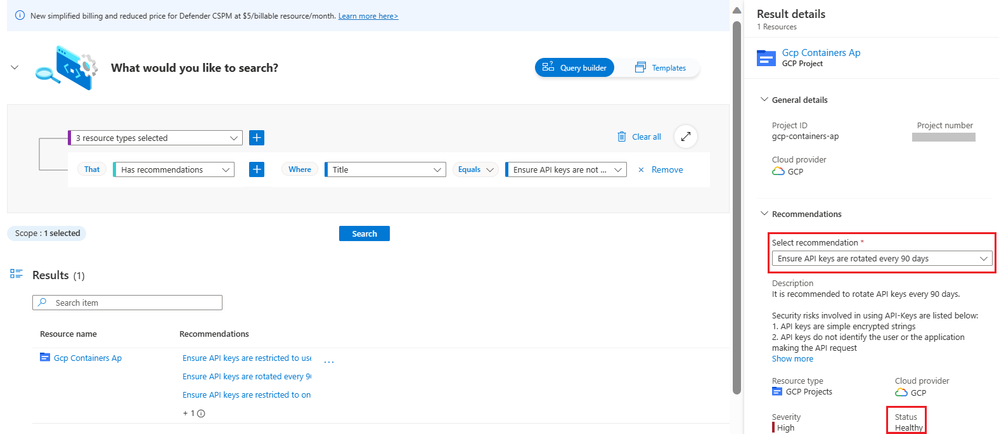
Contoso security team can proactively query their GCP Environment using the Cloud Security Explorer to identify the API misconfigurations. Under "Identity and Access", select "Cloud Accounts" and select "GCP Folders", "GCP Organizations", "GCP Projects" as shown below.
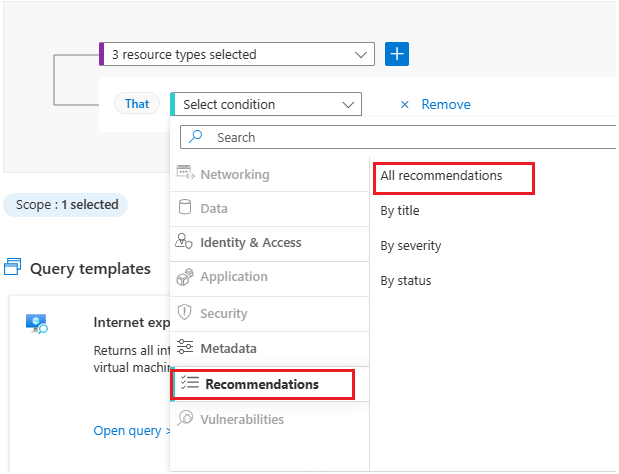
Select Recommendations -> All Recommendations
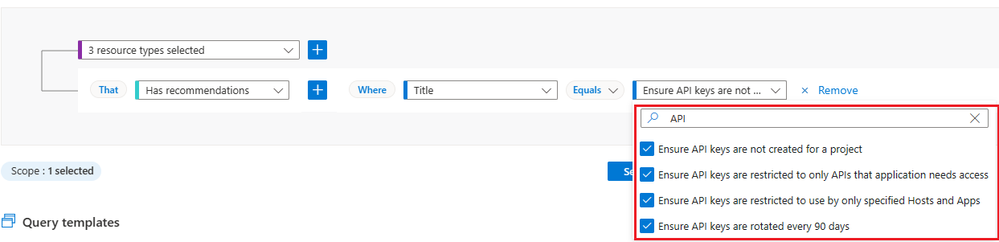
Select the Title Equals and in the search bar type 'API', and select the recommendations as shown below and click on "search".
Ensure each recommendation status is "Healthy".
Remediation Steps:
To address the security risks associated with unrestricted Google Cloud API keys, Contoso should consider implementing the following mitigation strategies:
- Review and restrict API keys to the specific Google APIs required for the application's functionality. Remove unnecessary API permissions.
- Rotate API keys on a regular basis to invalidate any potentially compromised keys and enhance security.
- Set up continuous monitoring and auditing to detect unusual API key activity or unauthorized access.
Conclusion
In this article you learned how to leverage Defender CSPM plan to enhance the security of your Google Cloud resources. Attack paths can change over time as your cloud environment evolves. Regularly monitor and remediate potential attack paths that malicious actors could use to exploit vulnerabilities in your Google cloud environment. By using attack path analysis as part of your overall security strategy in Google Cloud, you can take a proactive approach to risk mitigation, strengthen your defenses, and reduce the likelihood of security incidents.
Additional Resources
Please refer the resources below to learn more about these capabilities:
- Microsoft Defender for Cloud Security Posture Management
- Cloud security explorer and Attack path analysis (Video)
- Identify and remediate attack paths
- Reference list of attack paths and cloud security graph components
Reviewers
Yuri Diogenes, Principal PM Manager, CxE, Microsoft Defender for Cloud
Tal Rosler, Senior Program Manager, Microsoft Defender for Cloud
Lior Arviv, Senior Program Manager, Microsoft Defender for Cloud
*1 2023 State of the Cloud Report, Flexera.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.