- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Exposure Management: The Evolution of Vulnerability Management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Traditional Vulnerability Management
As security professionals, we’re tasked with the seemingly impossible job of staying one step ahead of attackers. This task is made more challenging by the constantly evolving threat landscape as well as the silos that exist within our businesses, security teams, and even our tooling. The technology and architecture required to support a modern enterprise has caused the attack surface to expand rapidly in recent years—this includes things like leveraging a hybrid cloud/on-premises architecture, enabling a fully remote workforce, and using a myriad of tools and technologies to support a single web application. Combined with a consistent increase in the amount of malicious activity from both organized crime groups and independent hackers, the odds have never been more stacked against security teams. For many defenders, security is a game of Whac-a-Mole; as soon as one issue is fixed, three more are identified.
Despite common attacks exploiting known vulnerabilities and often following well defined tactics, techniques, and procedures (TTPs), we still find it challenging to identify and prevent them within our organizations. Misconfigurations and vulnerabilities, even those that are well-known and have patches and fixes available, continue to be a common cause of successful breaches.
Our traditional approach to vulnerability management is falling short. This is in part due to its limited scope. Historically, we’ve focused on protecting what we know – looking for Common Vulnerabilities and Exposures (CVEs) across our endpoints, servers, and infrastructure. While this is a good start, it does not give us a holistic view of our digital estate, it lacks context, and assumes all resources are equal. With this approach, we only have insights into a small snapshot of our environment. We also need to account for risks within our code, network vulnerabilities, data access, resource misconfigurations, and identity over permissions.
Today, all these risks fall under the Vulnerability Management charter, and each introduces a new tool or set of tools designed to identify and remediate the risk. While it’s helpful to have specialized tools for each unique use case, the tools continue to operate in silos. The data itself is not integrated and the tools operate within separate portals. As a result, they continue to provide a fragmented view of our environment. This lack of integration means that despite having additional coverage, we do not have contextual security, making it hard to prioritize the most critical threats and our corresponding remediation efforts.
Continuous Threat and Exposure Management
The NIST Cybersecurity Framework helps us to break down cybersecurity into 5 domains: identify, protect, detect, respond, and recover. In recent years, we have seen organizations focus heavily and make significant investments into two of these domains— detection and response. Due to these investments, which include innovative technologies like artificial intelligence (AI) and advanced automation, these organizations have been able to achieve a much lower Mean Time to Detect (MTTD) than ever before, a key metric in evaluating their efficiency in responding to cyber incidents. Despite this, we continue to see the rates of successful breaches grow year-over-year.
Two of the areas that we have been investing heavily in over the years are Identify and Protect capabilities. Identify is just as important as any of the other stages of the framework. You cannot Protect, Detect, or Respond to threats against services of which you are unaware. The first stage in ensuring up-to-date services, proper configuration, and the right detection and response tools is ensuring you know the scope of your environment. While we can often protect what we know, it is much harder to protect the resources we do not know exist. This is especially important to keep top of mind because we’ve seen through our most recent research that 80-90% of successful ransomware compromises originated through unmanaged devices (Microsoft Digital Defense Report 2023 (MDDR) | Microsoft Security Insider). These devices run a higher risk of having unpatched remote code execution vulnerabilities and misconfigurations allowing RDP or SSH access. Without being able to identify these resources and their relationship to our organization, we are ill-equipped to protect against targeted attacks. We need to consider our entire exposure, including the areas not directly within our control.
Once we’ve identified the true scope of our exposure, the next stage of the cycle is to define protections. For years, we’ve used vulnerability management solutions, and we have used them as well as we can. Even with Vulnerability Management solutions in place, studies show only about 13% (Why does it take so long for security teams to remediate vulnerabilities? | SC Media (scmagazine.com...) of vulnerableness are remediated and the average time it takes to remediate these vulnerabilities is 271 days. Typically, organizations look at vulnerabilities from a criticality standpoint, starting with the most severe, working down from there. With this approach, we only focus on the individual CVEs, not the full impact of exploitation. Without contextual security, we are potentially focusing on the wrong vulnerabilities.
The Vulnerability Management industry is evolving from targeted vulnerability identification and remediation to a more holistic exposure management approach referred to by Gartner as Continuous Threat Exposure Management (CTEM). This represents a paradigm shift for vulnerability management from prioritizing based purely on the threat type and severity to focusing our remediation strategy on potential business impact. To do this effectively, we must recognize that there are significant variables to consider including our external attack surface, sensitive data exposure, and resource interconnectivity (attack paths).
CTEM is not just about vulnerability and posture management, it’s a process to help prioritize risk reduction based on business impact.
Microsoft’s Exposure Management Journey
Microsoft has always placed a high emphasis on helping customers understand their posture and has been on the Exposure Management journey for quite some time. One of the first features was a feature within our Defender for Identities solution called Identity Security Posture Management. This is a technology that helps organizations to discover and visualize identity vulnerabilities such as legacy protocols being used, dormant entities in sensitive groups, exposed credentials in clear text, and many others.
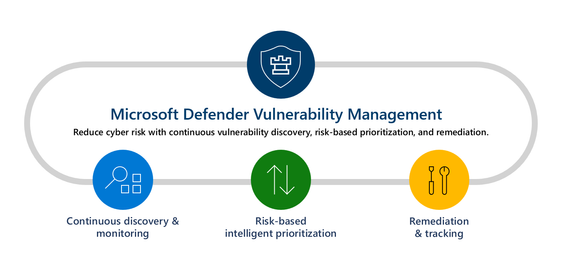
The next stage of the journey was the introduction of Microsoft Defender Vulnerability Management (MDVM). MDVM brought the capability to evaluate both first and third-party OS kernel vulnerabilities. Over the years we continued to build and expand our capabilities with the goal of being able to discover vulnerabilities from application to hardware. Some of these innovations include introducing security baselines, hardware and firmware assessments, digital certificates assessments, browser extension assessments, and even network share analysis.
Microsoft Defender Vulnerability Management was then extended from traditional client and server management to containerized applications. Using the MDVM engine, we now have the ability to run vulnerability scans against new images checked into container registries across Azure, AWS or GCP, and discovers running instances with vulnerabilities.
In August of 2021, Microsoft acquired RiskIQ, a cybersecurity company focused on Internet-scale data discovery, threat intelligence, and attack surface management. Leveraging the web-crawling infrastructure and datasets from RiskIQ, we released a new solution called Defender for External Attack Surface Management (Defender EASM). Defender EASM automatically discovers and monitors customers’ external attack surface and gives security teams visibility into potentially unknown resources and Internet assets, like shadow IT or improperly decommissioned UAT environments. Since EASM only leverages open-source data collection, it allows security teams to view their organization’s external attack surface the same way that an attacker would—if we can see it, so can they.
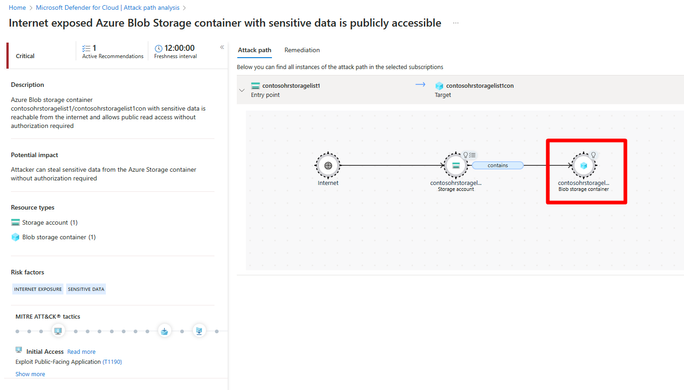
The next stage we started really helping organizations contextualize and prioritize their cloud vulnerabilities. We released Defender CSPM which natively integrates with Defender Vulnerability Management in both an agent and agentless approach for compute resources like servers and containers. Additionally, we include Data Aware Security Posture Management which add key capabilities including the ability to scan storage accounts and databases against sensitive data types like social security numbers, credit card numbers, and hundreds of additional. By correlating this information, we gave customers visibility to see where their assets and resources were at risk in context of potential impact or blast radius.
Shift-Left is a large part of our story as well. We started our source code security with GitHub Advanced Security (GHAS) that looks at dependency vulnerabilities (SCA), source code vulnerabilities (SAST) and discovers secrets in code. Recently we announced DevOps Security (part of Defender CSPM) to discover vulnerabilities in Infrastructure-as-Code and Container Image scanning. These new capabilities allow us to provide contextual security throughout the entire resource life cycle, from code to cloud.
Microsoft Security Exposure Management
The next step in our journey is to bring these insights together, within one platform. We’re doing this with Microsoft Security Exposure Management.
Microsoft Security Exposure Management is a new, unified posture management architecture that modernizes exposure management in the same way XDR modernized threat management. Rather than introducing a new tool, we are helping organizations centralize their vulnerability and posture management data feeds to provide contextual security, helping organizations understand their blast radius and visualize the impact of an exploited vulnerability.
Microsoft Security Exposure Management will help prioritize remediation strategies based on potential impact, complimenting the extended detection and response capabilities of Defender XDR, in the same unified portal as our XDR and SIEM solutions. This solution will centralize content from our existing vulnerability management, posture management, exposure management solutions, including:
- Microsoft Defender Vulnerability Management
- Microsoft Defender External Attack Surface Management
- Microsoft Defender for Cloud – Cloud Security Posture Management
- Microsoft Secure Score
- Microsoft Entra
- Microsoft Defender XDR
- Microsoft Defender for IoT (MDIoT)
- Microsoft Defender for Cloud Apps (MDA), including SaaS Security Posture Management (SSPM)
Microsoft Security Exposure Management is our solution to integrate all these current and future capabilities to address the CTEM need that many organizations require. The solution will also integrate with non-Microsoft exposure management solutions (such as Qualys, Wiz, and Okta) and ITSM systems (such as ServiceNow) to help centralize all customer information, regardless of source.
Through these integrations across both the Microsoft and non-Microsoft Security stack, we’re able to provide greater visibility and insights to security teams. Ultimately, we can’t protect what we don’t know— the most comprehensive security program in the world will fall short if they are only aware of a portion of their digital estate. In this era of security defined by the expanding and complex attack surface, visibility is key.
While we may work in silos today, attackers do not. The same vulnerabilities on different resources do not always pose the same risk, and security teams need to be armed with contextual insights from across their entire environment to effectively understand and prioritize. To do this, we need an architecture without silos, one where data, technology, and teams are seamlessly integrated and unified.
To learn more about Microsoft Security Exposure Management, please visit:
- Official Microsoft Security Exposure Management announcement
- Product website
- Video from Microsoft Mechanics
- Microsoft solution docs
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.