- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Enhancing Defender CSPM across the application lifecycle
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Organizations are challenged with managing multicloud security due to the complexity of coordinating security measures across diverse cloud environments, each with its unique configurations and vulnerabilities. Visibility across cloud environments can be limited, making it challenging to effectively triage issues that arise. Additionally, ensuring consistent security policies and followed amidst a changing threat landscape can be daunting, especially when dealing with multiple providers.
To address these challenges, Cloud Security Posture Management (CSPM) solutions help security teams take on these challenges and strengthen their security posture by providing visibility across multicloud environments from development to runtime to predict and prevent cyberattacks.
Through Microsoft Defender for Cloud, a market-leading cloud-native application protection platform (CNAPP), Defender Cloud Security Posture Management (CSPM) offers cutting-edge capabilities that empower security administrators to understand security risks across their multicloud environment, cut through the noise to focus on critical issues, and take action to remediate and prevent future cyberattacks. Defender CSPM is powered by the cloud security graph and synthesizes security signals across data, DevOps, External Attack Surface Management (EASM), identity, and compliance – enabling security teams to find exploitable resource paths and mitigate risks faster.
To continue delivering on multicloud leadership, we're excited to share the general availability of Defender CSPM capabilities for Google Cloud Platform (GCP), extending its advanced agentless scanning, data-aware security posture, cloud security graph, and attack path analysis capabilities to GCP resources.
Additionally, Defender CSPM is raising the bar again to help security teams predict and prevent cyberattacks from code to cloud across cloud environments with new innovations.
Extend visibility with more contextual insights across the development lifecycle
We are excited to announce the integration of the capabilities of Permissions Management with Defender for Cloud is now available in public preview. Microsoft now delivers CIEM solutions with as part of CNAPP through Microsoft Defender for Cloud (CNAPP) and Microsoft Entra Permissions Management (CIEM). Integrating Permissions Management capabilities with Defender for Cloud strengthens the prevention of security breaches that can occur due to excessive permissions or misconfigurations in cloud environments. This enables teams to get basic permissions management insights through Defender CSPM, such as actionable recommendations for resolving permissions risks across Azure, AWS, and Google Cloud. Learn more about additional insights and remediation tools from Microsoft Entra Permissions Management, which require a license for Entra Permissions Management.
The integration also enriches attack path analysis, enabling teams to visualize how identity and access can be exploited by attackers to compromise your cloud resources. This integration brings you new recommendations to reduce identity-related risks for your cloud environment.
View new recommendations to prevent identity and permissions-related risks
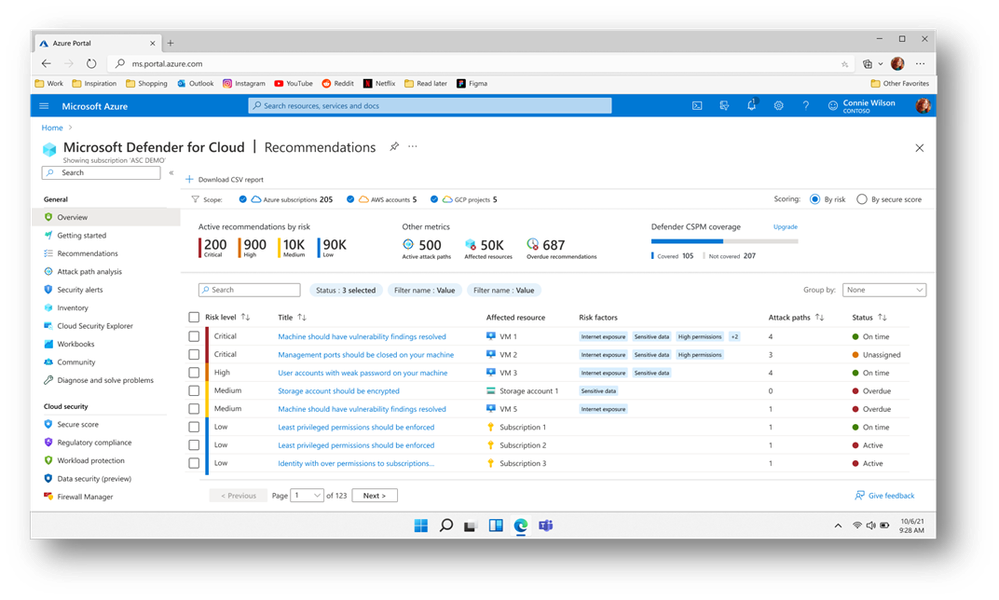
Adopt a risk-based approach to prioritize recommendations and enhance attack path analysis
Our goal is to empower security teams to swiftly address the most critical risks, overcome security issues fatigue, and remediate security issues based on the effective risk.
We are happy to announce new risk prioritization capabilities in Defender CSPM. Defender CSPM goes beyond merely identifying security issues and takes a proactive role in assessing the risk of each issue in your organization, considering the exploitability and the potential business impact to your organization.
Our risk assessment engine takes into account essential risk factors when assessing the risk of a security issue, such as internet exposure, data sensitivity, lateral movement, potential attack paths that will be mitigated by resolving the issue, and more. This comprehensive approach ensures that you can focus on tackling the most urgent security concerns first, making your remediation efforts more efficient, and effective.
New Defender for Cloud experience prioritizes recommendations based on risk level
In addition, we are happy to introduce major enhancements to our attack path analysis capabilities. First, the attack path analysis is getting a fresh new engine, which uses a path-finding AI algorithm to improve attack path analysis capabilities dramatically. We will now detect many more attack paths, including complex and sophisticated attack patterns that attackers can use to breach your environment. We will also start detecting attack paths spanning across multiple cloud providers in your environment, for example starting at GCP and allowing attackers to move laterally to your AWS environment.
Enhanced attack path analysis now identifies sophisticated attack paths and includes risk level and maps to MITRE ATT&CK techniques.
In addition, we are introducing several additional enhancements to our attack path analysis, that were long anticipated by customers:
- Risk prioritization – Prioritized list of attack paths based on effective risk (taking exploitability and business impact into account)
- Enhanced remediation - Pinpointing the specific security issues that should be resolved to break the chain, distinguishing them from the ones that will only reduce risk.
- MITRE mapping – Mapping all attack paths to MITRE framework.
- Refreshed user experience – Refreshed experience with stronger capabilities: advanced filtering, search, and grouping of attack paths.
- Export – Export capabilities of attack paths to SIEM and data lakes (coming soon)
- Email notifications – Email notifications for new attack paths (coming soon)
Proactively flag risks in code and seamlessly 'fix left'
In today's ever-evolving cybersecurity landscape, securing assets from code to cloud is critical in ensuring the safety and integrity of your cloud-native applications.
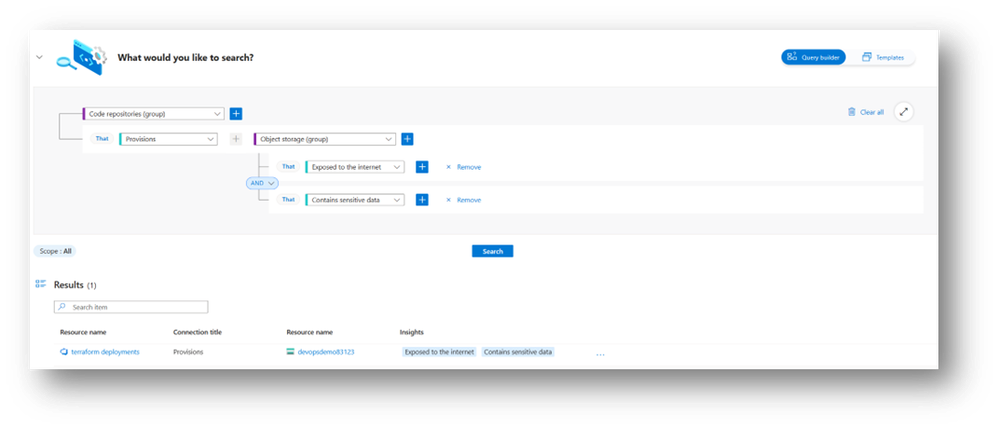
We are thrilled to announce two groundbreaking new capabilities: container image mapping and Infrastructure as Code (IaC) template mapping. With container image mapping, we empower you to gain real-time visibility into security posture of your containerized applications across the software development lifecycle, from your DevOps pipelines to the deployment of the images in registries. This feature not only enhances security but also streamlines compliance by tracking image vulnerabilities. Users can now query the Cloud Security Explorer to see the source code origin of their container images.
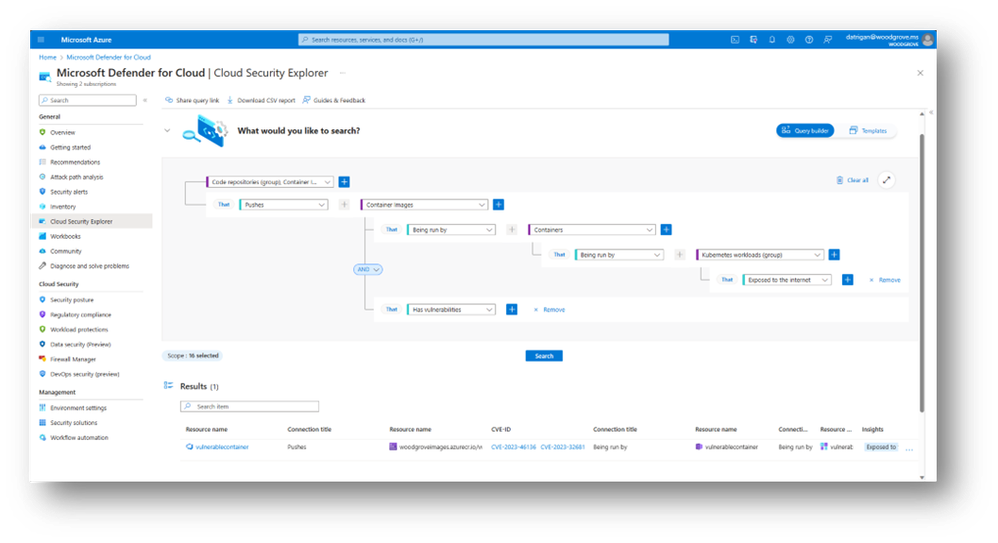
Additionally, IaC template mapping extends the same visibility and control to your infrastructure, allowing you to trace IaC templates from code repositories to the cloud resources they provisioned, bolstering your ability to enforce security policies and optimize resource configurations. With this capability, remediation becomes seamless, as security administrators can now track the origin of their unhealthy resources, allowing them to fix issues at the source, and avoid drifting from the desired configuration of the running resource.
Trace IaC templates from code repositories to the cloud resources they provisioned
Together, these capabilities represent a significant leap forward in your code to cloud journey, offering you the robust tools you need to fix-left the security of your cloud assets in a rapidly changing environment.
Lastly, we are excited to announce the general availability of Azure DevOps pull request (PR) annotations for Infrastructure-as-Code (IaC) misconfigurations. A single IaC misconfiguration can be propagated across hundreds of cloud resources, potentially compromising an entire cloud environment. Security administrators can enable PR annotations from Defender for Cloud to empower developers to fix security misconfigurations before they enter the production stage. Each annotation includes a description of the issue, a severity level, and remediation instructions to reduce to-to-remediation for developers that want to ship secure code quickly.
Defender CSPM continues to deliver innovative capabilities to help security teams stay ahead of risks from development to runtime.
Get started today - learn more about getting the most out of these innovations
View our latest Microsoft Mechanics video: Predict future security incidents! Cloud Security Posture Management with Microsoft Defender
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.