- Home
- Security, Compliance, and Identity
- Microsoft Defender External Attack Surface Management Blog
- Optimize insights and efficiency with latest Defender EASM features and generative AI integrations
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Discovering and prioritizing vulnerabilities that often arise as a result of known and unknown internet-exposed assets – which can emerge from shadow IT, the supply chain, and the shift of moving to the cloud, for example – is an essential practice our customers take to reduce external risk and stay secure.
Over the last six months, Microsoft Defender External Attack Surface Management (EASM) has released updates that help Defender EASM customers increase the speed to operationalize its findings. Now, vulnerability management teams are using labels to drive workflows and denote asset ownership, they are saving queries to quickly modify newly discovered assets, and they are combining it all with data connector exports to generate custom reports to help them see their security data holistically.
These new features that we’ve recently delivered make it easier for our customers to track inventory changes, see important asset findings in one place, connect data to supplement workflows, and has made managing assets and long-running tasks more efficient.
Additionally, we’re excited to announce that we’ve extended Defender EASM’s footprint into Microsoft Security Copilot with capabilities that enable Copilot users to learn more about their external attack surface exposures in context and at AI speeds.
Read on to learn more about the latest in Defender EASM.
Understand inventory changes over time
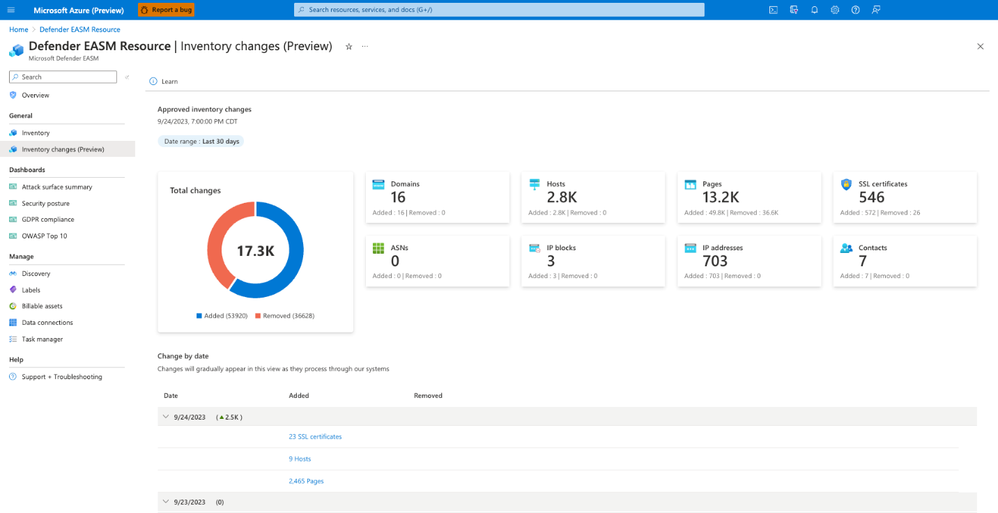
While Defender EASM has long provided detailed dashboards with information on vulnerabilities, misconfigurations, breakdowns of device types, and other useful analytics, these have primarily focused on point-in-time snapshot-style views. In October, we released a new dashboard that shows inventory changes in your attack surface. With the introduction of this dashboard, you can now see changes to the attack surface over time, as assets move in and out of the attack surface, whether automatically due to Microsoft’s ongoing scanning and enumeration, or due to manual curation in product, or even via API-based adjustments made via external integrations. In addition to a graphical overview of the changes over the selected time period (7 or 30 days), you can also see the change counts for each day in the last 30 days, both in the aggregate and for each individual asset type.
Inventory changes dashboard in Defender EASM
See asset vulnerabilities in one place
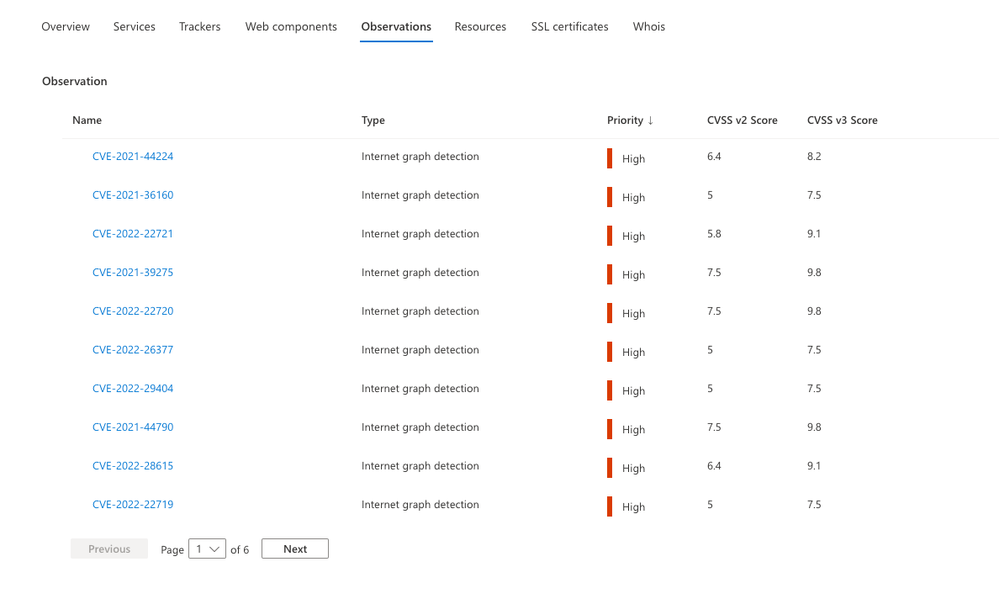
In Defender EASM we have two different detection methods used to identify software, services, and vulnerabilities on your external assets: insight detections authored by Microsoft’s security research team, and internet graph-based detections based on software and service components that Defender EASM can identify in your environment, allowing us to identify likely CVEs on assets. Our two different detection methods complement one another and are valuable in generating the most accurate coverage, however, analysts sometimes found it challenging to align the two together when inspecting assets, and complicated to identify which observations came from Microsoft research versus graph detection, or both methods combined.
In June, we introduced a new feature into the Defender EASM interface that helps unify asset detail data and showcases all high, medium, and low priority observations related to any given asset in a single tab, labeled “Observations”, on the asset details page. The new tab is helpful so you can see exactly which detection method the insights are coming from, whether that be from research, graph detection, or both. This new tab represents a significant step in unifying findings in the EASM interface so that analysts can understand all the security posture-relevant findings for an asset in a single place and make smart decisions about how best to proceed in terms of investigation or remediation steps. Analysts can also more clearly understand the breadth of Microsoft’s security knowledge regarding any given asset and feel confident that EASM is providing them with clear guidance as they evaluate ongoing deployment of security controls, whether direct or compensating.
Observations tab Defender EASM
Connect, organize, and take action on your data
This year, we’ve added many new capabilities and features in Defender EASM that make it easier for you to connect your external attack surface data to other Microsoft tools, as well as the ability to keep assets organized with labeling, bulk modification, and task management.
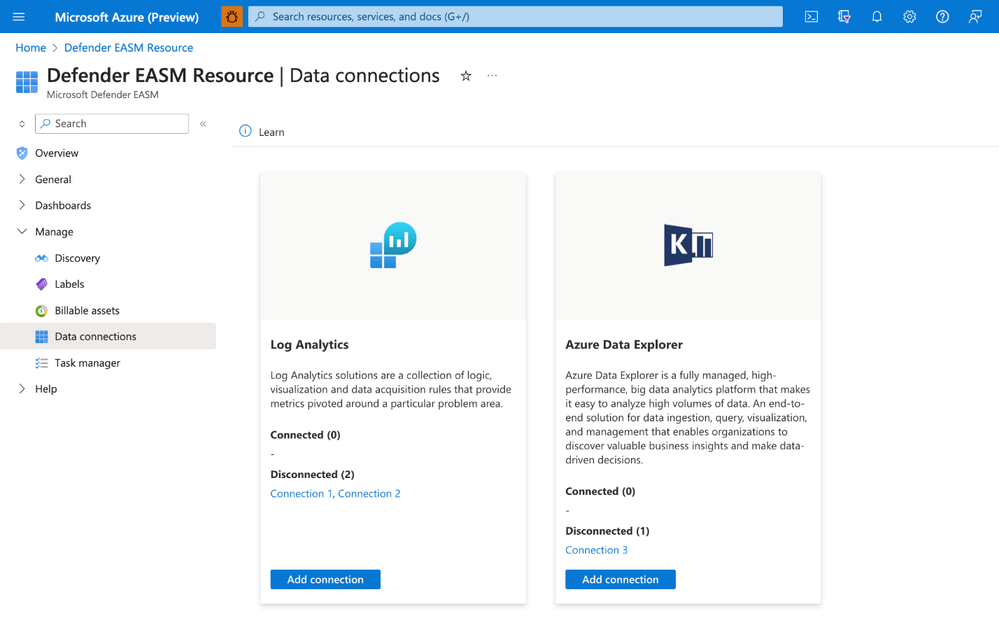
Created to supplement existing workflows, gain new insights, and automate data flow between tools, Defender EASM’s recent data connections feature is compatible with both Microsoft Log Analytics and Azure Data Explorer. The integration provides external attack surface data flow into your mission-critical systems, so you can get a holistic view of your data, enhance data visualizations, stay compliant, and effectively guard against vulnerabilities. Learn how to get started with data connections here.
Data connections in Defender EASM
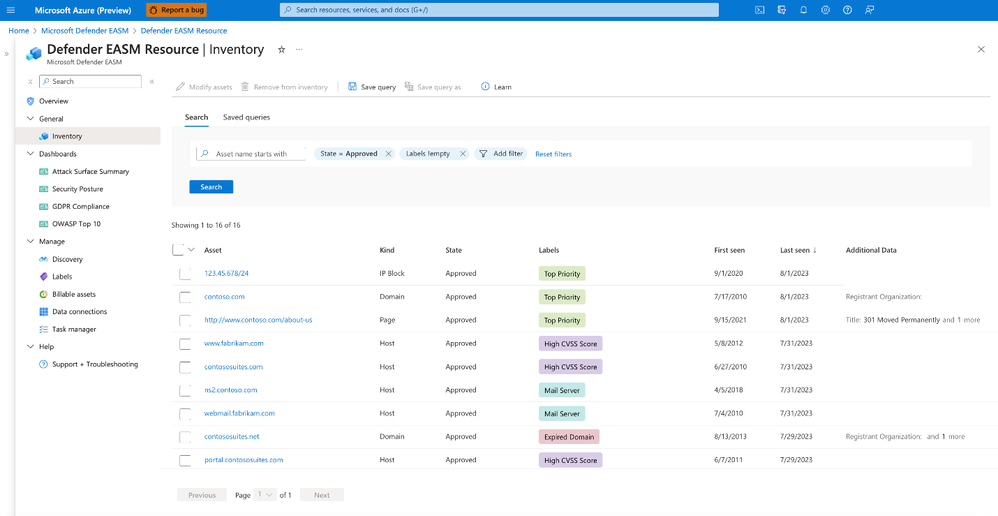
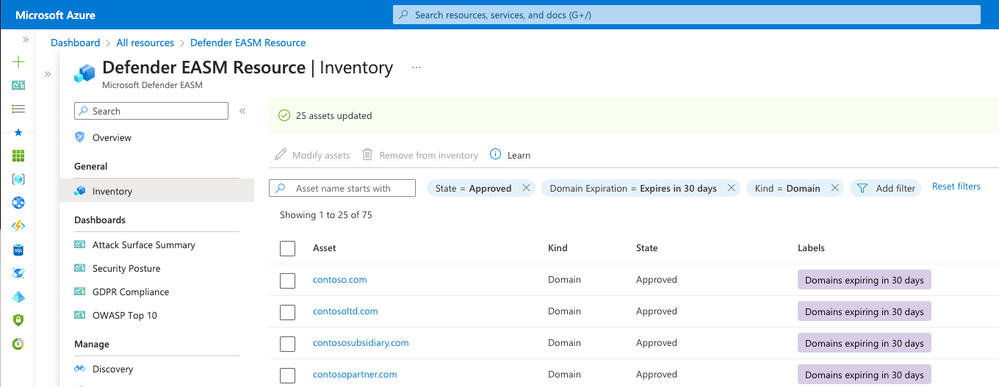
Organizing attack surface data – even after you’ve enabled a data connection – is important because it helps you apply business context to the asset at hand. For example, labeling assets is helpful to distinguish any assets that may have come in from a merger or acquisition, or those that require compliance monitoring, or when dealing with assets impacted by a specific vulnerability that requires mitigation. New this year, we’ve added the ability to apply any text label to a subset of assets – including within any asset export via the data connectors – so they can be grouped together to better operationalize your inventory.
Asset labeling in Defender EASM
In addition to applying labels to better organize assets, assets can also be categorized to tell you what their role is within your organization. For example, if the asset is approved and owned, or dependent on a third party, or only retained in your inventory to be monitored. Now, you can change the state of your selected assets in bulk, saving you time in categorizing many assets at once.
Changing the state of your assets in bulk in Defender EASM
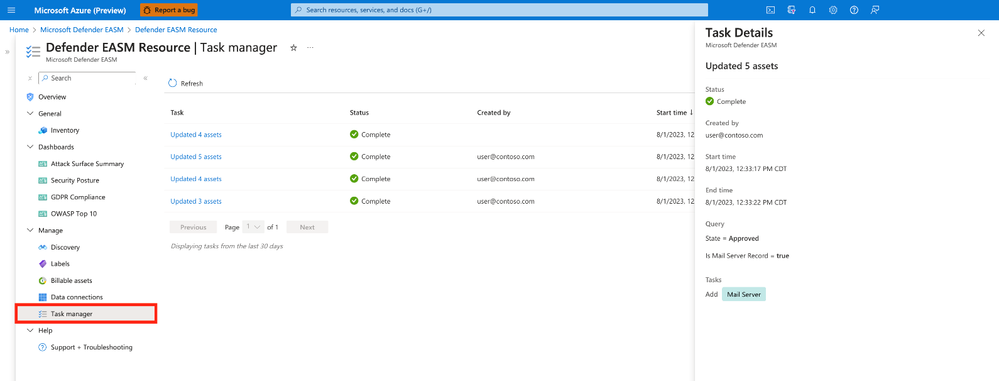
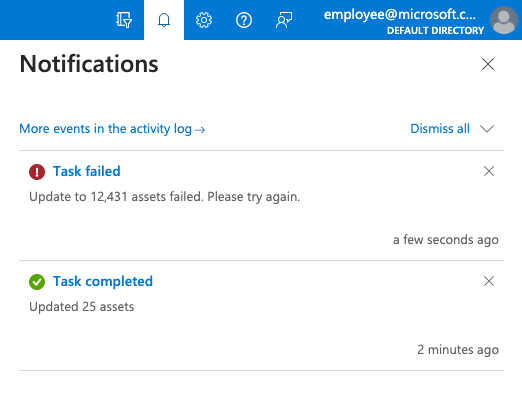
With the new ability to modify hundreds – or even thousands – of assets at a time, we’ve added a new “Task Manager” page to Defender EASM, making it possible to easily track the progress of tasks (like asset modification or downloading dashboard chart data) that may take a longer time to complete. Furthermore, you will also be notified via a pop-up about the progress of any relevant tasks that are running in the background – eliminating the need to check the status every so often and helping you stay focused on other priorities.
Task manager page in Defender EASM
Notifications in Defender EASM
Learn more about organizing, modifying, and tracking your external attack surface data here.
Get a snapshot view of your external attack surface with generative AI
We are excited to announce our new Defender EASM capabilities within the Microsoft Security Copilot standalone experience, currently available in the Early Access Program. These capabilities enable your security teams to quickly gain derive insights into your (non-curated) external attack surface at AI speeds – without the need for prior configuration in Defender EASM.
The capabilities solve for three distinct needs:
- They help SOC teams understand their externally facing assets
- They help vulnerability managers understand particular CVEs of impact
- They help security teams know where to start prioritizing remediation efforts
Let’s dive into how you can use the capabilities to address each.
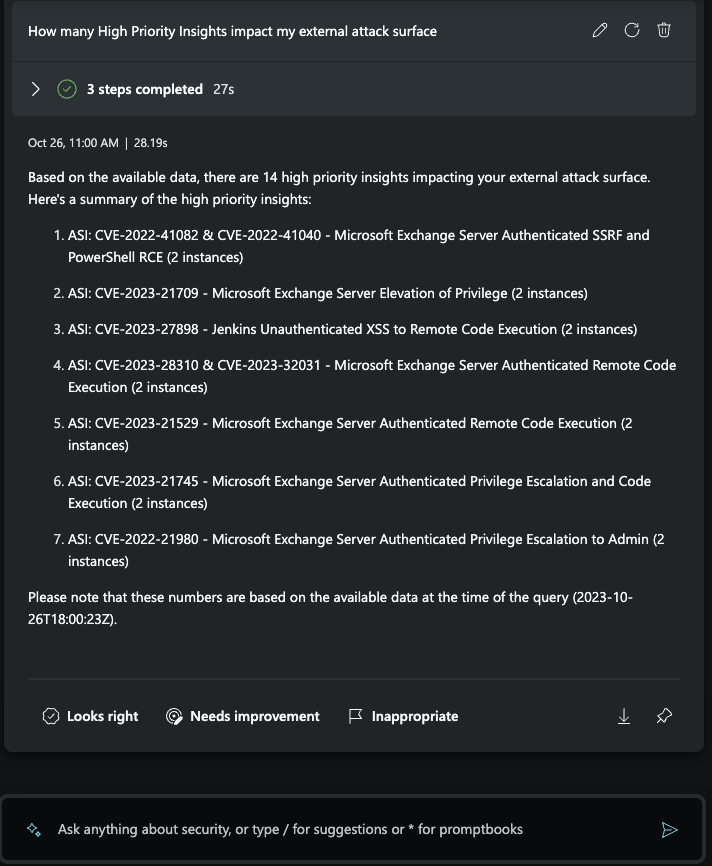
Understand your externally facing assets
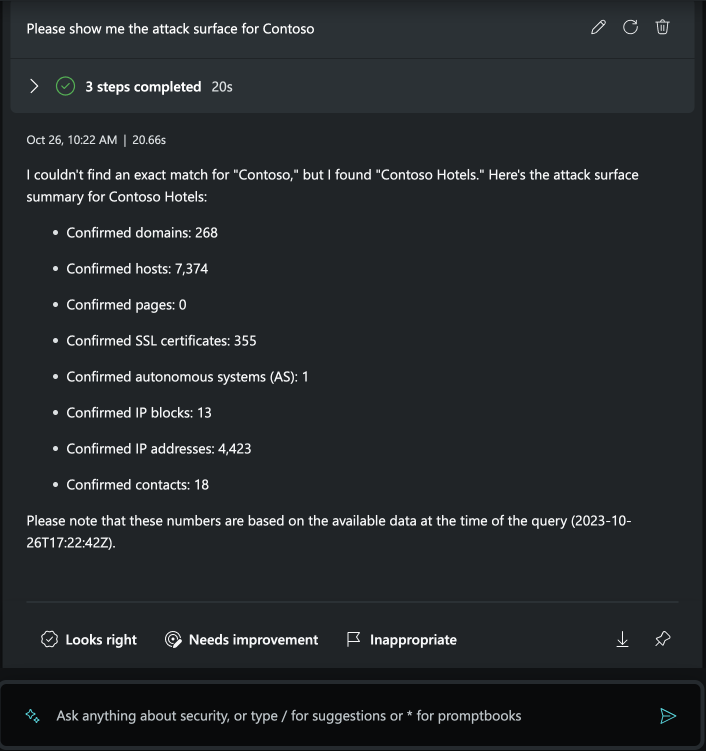
Understanding your digital footprint as threats emerge every day is critical in keeping your organization secure and compliant. The new set of Defender EASM capabilities in Security Copilot allow your organization’s SOC team to obtain a global snapshot view of the external attack surface, based on Microsoft’s pre-built library of external attack surfaces, by identifying externally facing assets exposed to the internet -- such as domains, hosts, and IP addresses – whether they are hosted on premise, in the cloud, or originating from a third party. You can also see how many high, medium, and low priority insights that may impact your organization are present, and quickly identify the assets they are tied to.
Use any of the following prompts in Security Copilot to understand your external attack surface:
- Please tell me my externally facing assets.
- Get the external attack surface for [my organization].
- What is the external attack surface for [my organization]?
- What are the externally facing assets for [my organization]?
- How many High Priority Insights impact my external attack surface?
- Get high priority attack surface insights for [my organization].
- Get low priority attack surface insights for [my organization].
- Does my organization have high severity vulnerabilities in the external attack surface?
- Are there any medium priority insights?
Understanding the external attack surface in Security Copilot’s standalone experience
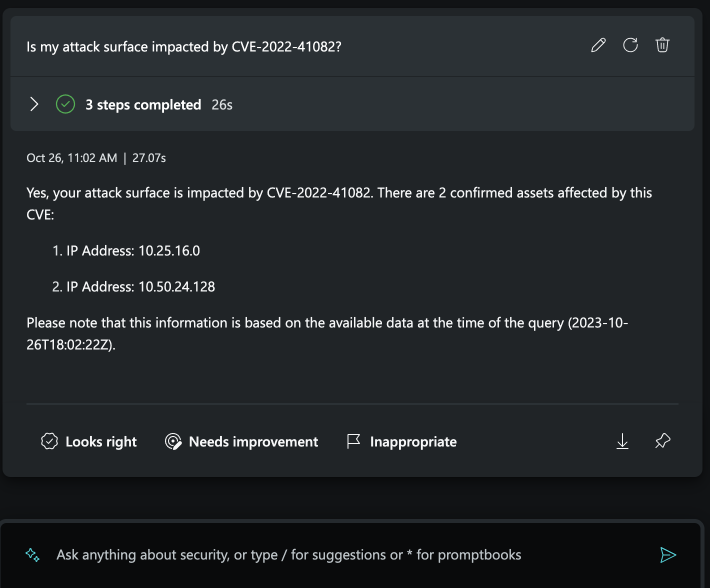
Understand particular CVEs of impact
After you’ve understood your attack surface composition, it’s imperative to investigate if there are high priority insights present so you can understand which assets are risky to your organization. Defender EASM capabilities do the digging for you, enabling you to quickly see high priority observations and significantly reduce the time it takes to research vulnerable assets.
Use the following prompts to understand if your organization is impacted by a particular CVE of interest and get visibility into vulnerable and critical high severity CVEs:
- Is my external attack surface impacted by [CVE ID]?
- Get assets affected by [CVE ID] for my organization.
- Which assets are affected by [CVE ID] for my organization?
- Is my external attack surface impacted by [CVE ID]?
- Are any assets impacted be [CVE ID] for [my organization]?
- Get assets affected by high severity CVSS’s in my attack surface.
- How many high priority insights impact my external attack surface?
- How many assets have critical CVSS’s for my organization?
- What assets are affected by CVSS for [my organization]?
- Are there assets with high CVSS scores for [my organization]?
Showcasing particular CVEs within the external attack surface in Security Copilot’s standalone experience
Asking about high priority insights in Security Copilot’s standalone experience
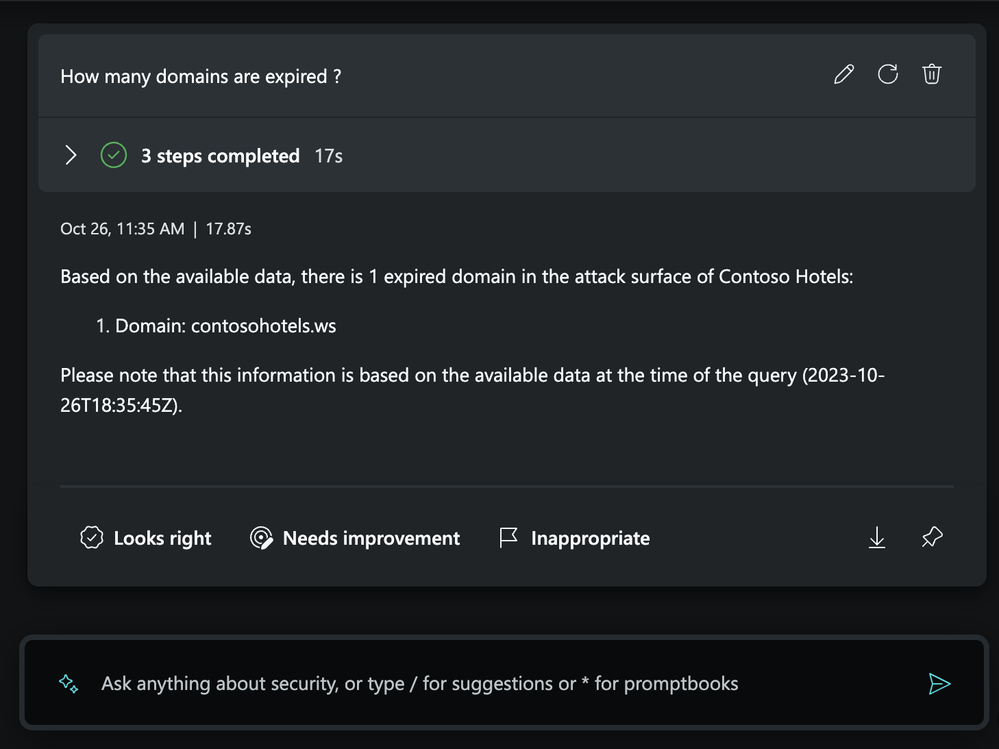
Understand how you should prioritize your remediation efforts
Once you’ve found the assets that need attention, Defender EASM capabilities will take it a step further and identify assets that need immediate attention by showing assets with critical and high CVSS scores, expired domains and SSL certificates, and any assets using SSL SHA1. This is helpful in reducing the time it takes you to determine which assets should be remediated first.
Use the following prompts to unlock which assets need your attention first:
- How many domains are expired in my organization’s attack surface?
- How many assets are using expired domains for my organization?
- How many SSL certificates are expired for my organization?
- How many assets are using expired SSL certificated for my organization?
- How many SSL SHA1 certificates are present for my organization?
- How many assets are using SSL SHA 1 for my organization?
Checking for expired domains in Security Copilot’s standalone experience
Defender EASM capabilities in Security Copilot make it easy for you to get a snapshot view of your external attack surface, without needing to create a Defender EASM workspace.
Interest in the Security Copilot Early Access Program has been high and space is still available. Reach out to your sales representative to get more details on early access program qualifications.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.